Find Out How Invisible Tracking Pixels Invade Your Privacy
You need to know that it is standard practice to use invisible tracking pixels in emails.
And, also, you need to be aware that most probably every day you receive many emails that contain tracking pixels.
Tracking Pixels: To What Extent Is Your Privacy Invaded?
Sometimes the invisible pixels are used for relatively harmless purposes, like tracking the success of marketing campaigns.
As an example, below there is a relatively harmless email from Amazon Prime Deal Days, that contains 4 hidden tracking pixels.
Big companies, like Amazon, disclose in their term and conditions that they use tracking pixels.
So upon accepting the terms and conditions (that mostly nobody read), they can legally make use of tracking pixels in their communications.
As Amazon describes it in their 'Security and Privacy' disclaimer: "We use cookies, pixels, IP addresses and other technologies (collectively, "advertising technologies"), which enable us to understand the effectiveness of the interest-based ads we show you by measuring what ads are clicked or viewed, and to provide you with more useful and relevant ads. For example, we use cookies or other information such as IP address to limit the number of times you are shown the same ad."
But invisible pixels in emails can be used by hackers and scammers for malicious intentions.
Every time that you open a phishing email, you are giving away precious information: Information is collected by the tracking pixels, and through a third-party service the information is processed and made available to people or organizations with malicious intentions.
That information is collected without your consent and will be used to organize sophisticated scams or hacks against you.
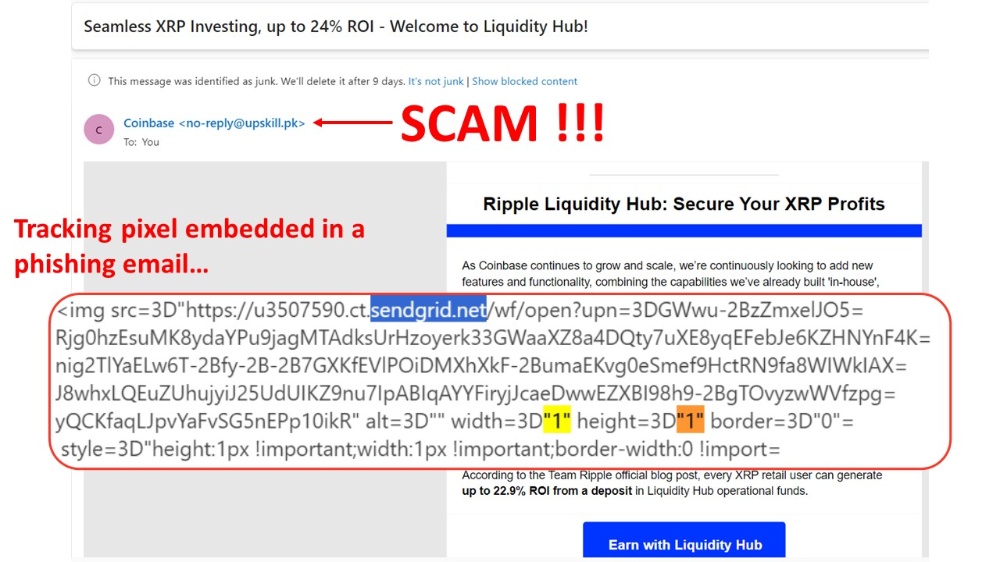
As an example, below there is a screenshot from a phishing email trying to convince us that it has been issued by Coinbase.
Once the email has been opened, and even if we don't fall for the scam and we don't click on the link, at the very least the scammer will receive information that can be used or sold to the best bidder.
The tracking pixel embedded into this email is reporting information to sendgrid.net.
Sendgrid.net is just a cloud-based SMTP provider and not a hacker or scammer's website. But it is used by spammers to collect sensitive information.
Sengrind, like many other email marketing companies, is just a tool that can be used for good or bad. And, in this case, the scammers are using it for nefarious purposes.
What Type of Information Do Tracking Pixels Collect?
Tracking pixels embedded in emails can collect the following information:
- The type of device used by you, the email recipient. (desktop or mobile)
- The type of operating system used by you, including mobile OS
- Activities performed during the session
- Screen resolution
- The email client used by you, the email recipient (browser, mail program, etc.)
- Your IP address
- What time did you open the email
Every time that you open a suspicious email, assume that it contains tracking pixels.
Even if you are curious, you should not open suspicious emails. You may think that you are safe as long as you don't click on any link, but by now you know that this is not the case.
At the very least, the scammers will know that you have opened the email, and they will keep sending you more phishing emails, in the hope that eventually you will follow for one.
How To Find Tracking Pixels in Emails
First of all, and once again, never open suspicious emails. Assume that all of them have tracking pixels.
- If the suspicious emails are in your email spam account, just leave them there without interacting with them.
- If the suspicious emails are in your inbox or focus accounts, create a rule to send them by default to the spam account.
But if you want to know if any email contains tracking pixels:
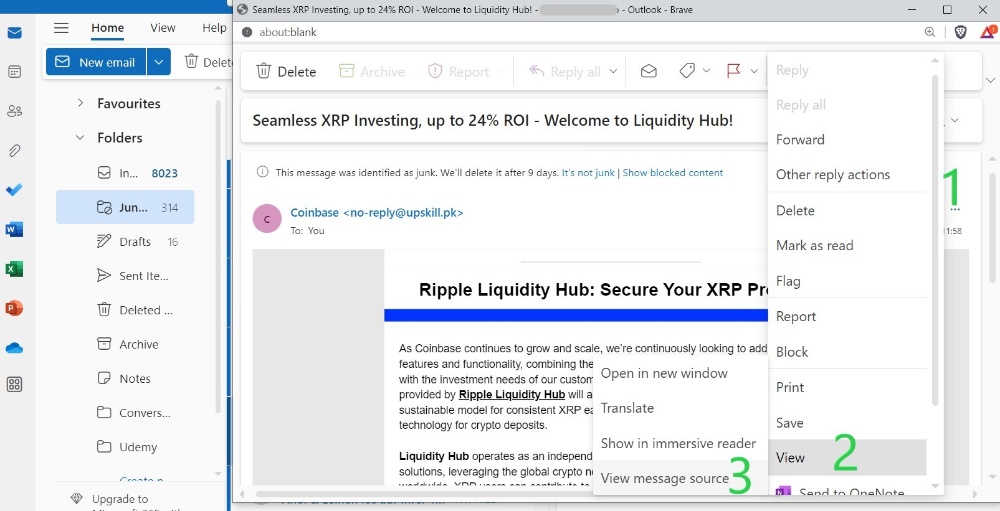
- Open the email
- Extend the options menu. As support, the picture below is a screenshot from an Outlook account: the options menu is the three dots (...) below the green number 1. The options menu will be visible upon clicking over the three dots.
- Find the 'View message source' menu and open it.
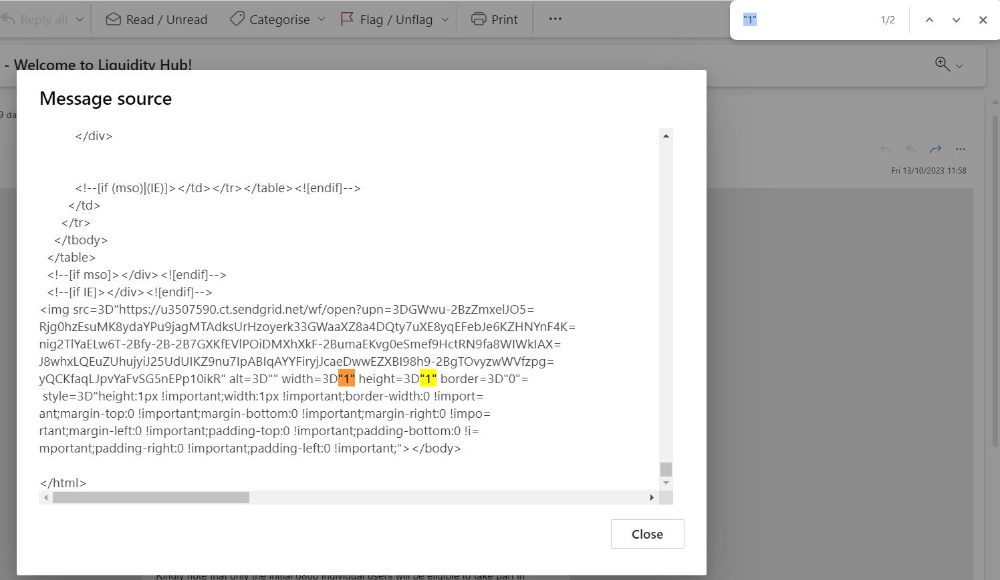
- Once the 'Message source' window is displayed, press Ctrl+F and search for "1"
Every width=3D"1" height=3D"1" you find is a tracking pixel.
_____________________________________________________________________________________________
Congratulations on completing this 5-minute digital safety power-up.
We hope this short article has helped increase your crypto safety knowledge and awareness, and the 5 minutes read was worth the time.
If you want to learn more, we have written a more extensive 'Find Out How Hidden Tracking Emails Are Used In Emails' article that may be of interest.
_____________________________________________________________________________________________
Article originally published at Publish0x




















![[LIVE] Engage2Earn: Veterans Affairs Labor repairs](https://cdn.bulbapp.io/frontend/images/1cbacfad-83d7-45aa-8b66-bde121dd44af/1)

























