Historical Hacks: The RSA SecurID Breach (2011)
That one time when two-factor authentication was targeted.
If you aren’t a medium member, you can read with no paywall via substack
When you’re at the incident response stage of assessing a cyber attack, it can often be a pretty dynamic situation. Assessing this properly can be a make-or-break part of mitigating damaged systems and ensuring that minimal damage has occurred.
One part of the process entails looking at protocols and solutions to help maintain security and prevent an incident from reoccurring. This usually entails the addition of extra steps, like 2FA or even things like hardware-based tokens to increase the complexity required for a successful attack.
But what happens in a world where these “extra steps” become part of the targeting chain and end up being a point of compromise on their own? In today’s historical hack, we’ll be going back to 2011 to cover the data breach that struck RSA Electronics and their SecurID protocol. This was yet another state-backed attack, and the subsequent breach had many large companies questioning just exactly how secure their processes were. Worse still, the steps taken by RSA to mitigate the attack did little to calm their users.
What Is SecurID?
Servicing a large range of both commercial and government clients, SecurID provided easy-to-implement two-factor authentication services that were based on the AES-128 encryption format.
Using the familiar to many RSA “dongle” to provide the code, SecurID captured a large part of the market with up to 70% of 2FA services provided by the company. Because of this, the company was highly regarded by many and by the time of the attack had more than a decade's experience in providing 2FA services with little in the way of incidents.
Unfortunately, in 2011 all of this was set to change.
The Incident
In many hacks, accurate details can often become murky. Companies and even people can often go into damage control and dealing with the PR of any given incident is an essential part of recovering to the business as usual phase. This means that often, you’ll have to dig deep to find accurate information and cross-check most things to ensure you’re maintaining some form of historical accuracy. This hack was no different, however, there are a few things that we are able to clearly ascertain.
The hack originally came to light in March 2011 when RSA announced that they had been the victims of a reasonably sophisticated cyber attack that had led to a compromise of the systems that help administer the SecurID 2FA service. Reading that you’d think we’d be talking about a sophisticated, nation-state-type attack like Stuxnet, where little could be done in terms of prevention or mitigation.
Unfortunately, though, this was only half true. While the attack was suspected of having the backing of a state-based actor (although details remain murky), the actual exploit that was carried out was pretty simple considering the damage it caused. The threat actors used a well-crafted phishing email to entice RSA employees to click on a malicious link. Once this was done, the Poison Ivy remote access trojan (RAT) was installed on the system, granting the attacker access to RSA’s servers.
While the financial damage as a result of the attack was in the tens of millions, the real damage done was to the image of MFA security strategies, exposing lax attitudes towards cybersecurity.
The Fallout
Eventually, RSA did release further information about the attack. However after the release of this information, for many, there were still plenty of questions about what happened and more importantly who had perpetrated the attack. Which is in fact, quite an interesting question.
Several of the historical hacks that have been covered in previous articles have included state-based attacks by threat actors like the Russian Federation and North Korea, and we’ve also explored why some of these attacks have occurred. It might surprise you to learn though that it’s believed that this incident was the responsibility of a different country entirely. Investigations carried out in the aftermath of another 2011 attack (Nitro Attacks) also showed usage of the Poison Ivy RAT, and a virtual Command & Control server for this was located within the continental United States.
The user for this server however was based in China, and while further investigations were carried out, US authorities were never able to directly ascertain confirmation of the individual’s involvement in the attack. To this day there are still questions around who exactly ordered the attacks.
Eventually, RSA would provide replacement tokens and live security monitoring to its affected users as an additional mitigation strategy. Despite this, the company maintained its claim that its end users were not greatly affected.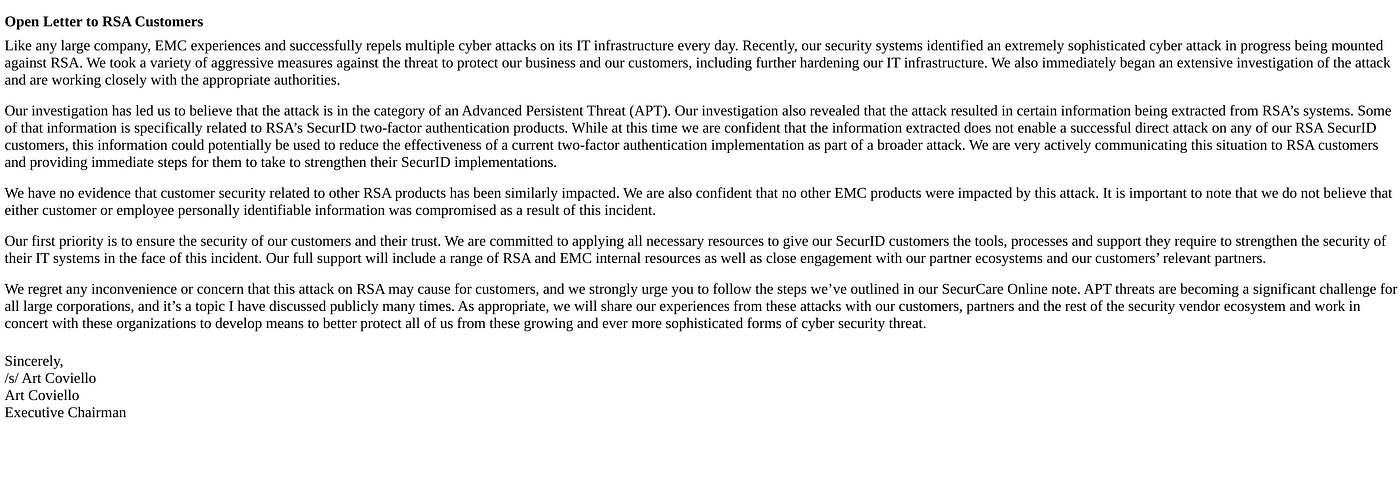
In Closing
It’s fair to say that this attack helped change attitudes around security and cyberspace in general. For a long time, the concept of security by obscurity was most certainly a thing and it took far longer than it should have for many to see this approach as both unrealistic and unsafe.
However, it wasn’t just the compromise of the data that would allow analysts to draw this conclusion. At the time, attitudes around the internet, and security in general, were also pretty lax, and the evolution of social media through the same period would lay the foundations for big data. Eventually, this would take humanity straight to the cutting edge, which meant that cyber was now a domain for state actors, and information warfare could apply new strategies to help leverage big data techniques to help shape the narrative.
When we apply some of these lessons to today's world, it’s not hard to see that not only do some of these problems remain, but in some instances they have gotten worse. With the evolution of artificial intelligence adding another layer of complexity to the issue one thing remains certain. It sure is an interesting time to work in cyber or information security.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Rocket Engines
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates