Analysis: Probe Requests & Your Privacy (Pt 1)
In our connected world, where Wi-Fi and Bluetooth have become a ubiquitous part of our daily activities, we often overlook or fail to understand the privacy implications of the devices we carry on our person. Considering those devices have the ability to broadcast our voice, our location and lots of other personal information, we’re of the opinion that this should be given more than a cursory thought. Hopefully, these articles will promote discussion around essential topics such as these.
In part one of this analysis, we’ll be looking into the details of Wi-Fi and Bluetooth probe requests, shining light on potential privacy risks that often go unnoticed. We’ll also look at how savvy hackers and OSINT analysts might be able to leverage this information to their advantage. In part two of this article, we’ll take the theory into the field and test its efficacy in the real world.
The Digital Handshake: Probe Requests
If you’re one of the folks who aren’t sure how Wi-Fi actually works, then fear not, we are here to help and explain!
Both Bluetooth & Wi-Fi-enabled devices regularly broadcast something called probe requests. These requests are seeking familiar networks in their vicinity to connect to automatically, for the sake of convenience. These requests contain information like the device’s unique MAC address and the SSID of the networks it’s attempting to connect to.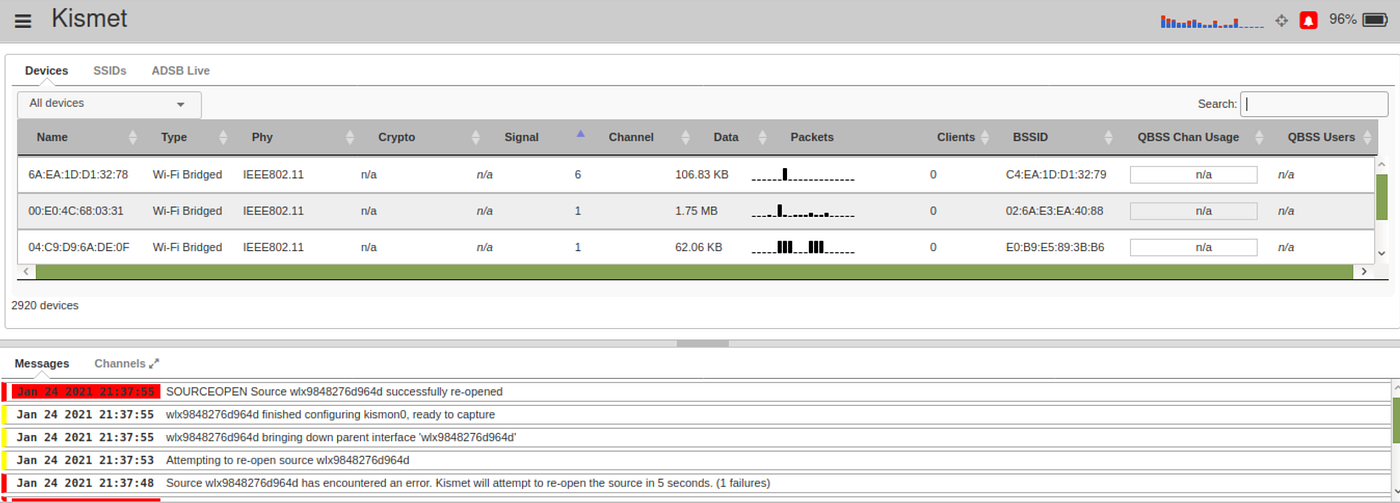 Kismet is a great to for wireless detection, but can we take that a few steps further? Source: Wikipedia
Kismet is a great to for wireless detection, but can we take that a few steps further? Source: Wikipedia
While this process is essential for seamless connectivity, it also unveils potential privacy challenges. One of the questions that we asked prior to compiling this article was “Could these probe requests be tracked?”. And, if they could be tracked, what effect could this have on a user's privacy as they go about their day?
In the earlier days, investigators of all sorts would often use GPS tracking devices to keep track of an important target. Is it now plausible that we can track someone without a GPS tracker using a device they carry and charge themselves? That’s exactly what we want to find out.
Understanding MAC Addresses
The MAC address, a device’s digital fingerprint, is exposed in probe requests. Although MAC addresses aren’t directly tied to personal identities, they can be exploited for tracking and profiling and there are databases online that collate and store Mac address information for OSINT purposes. One of those sites is WiGLE.
Have a look at WiGLE and see if you can find your own SSID or Mac address on the map.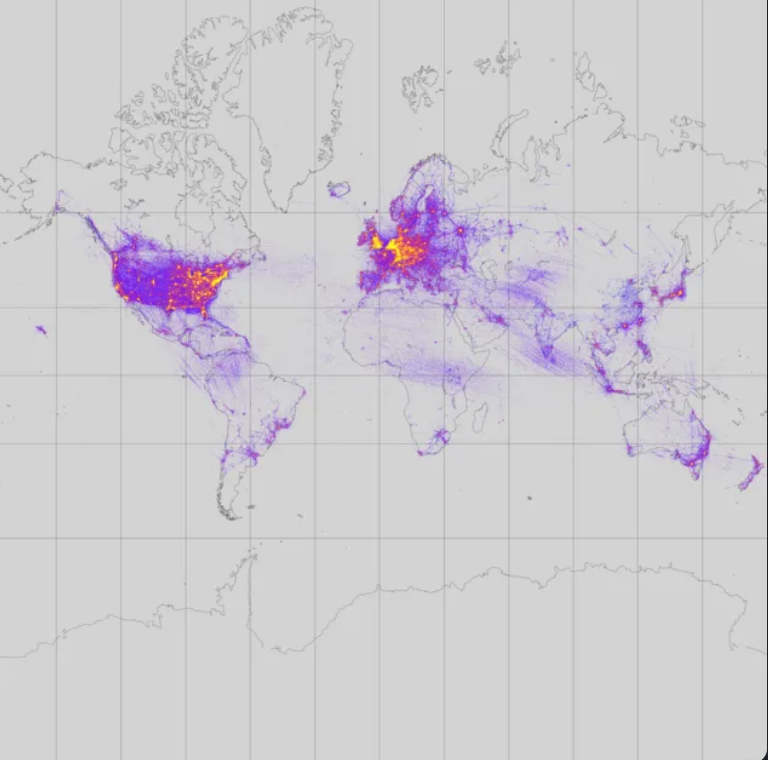 WIGLE is a diamond in the rough. If you’re an analyst, be sure it’s on your list. Source: wigle.net
WIGLE is a diamond in the rough. If you’re an analyst, be sure it’s on your list. Source: wigle.net
Often, manufacturers will use MAC randomisation in an attempt to maintain privacy. However, this doesn’t always work and fingerprinting strategies will often offset the benefits of this policy by looking for other accompanying ways to identify users and devices. While it will add a layer of complexity to targeting a specific device, we can offset this by tracking with a bit of patience and some handy experience.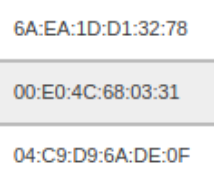 MAC addresses can look confusing but are pretty easy to decode. Source: Author
MAC addresses can look confusing but are pretty easy to decode. Source: Author
Mac addresses also follow a standard format and as such, you’ll find decoders that will allow you to find a specific device manufacturer and in some instances even a model number. Check out a super easy Mac address decoder via AllDataFeeds
Limitations and Problems
While plausibly, we can track someone off probe requests what we’ll need to look at is how we can do this in a built-up area and what the limitations are around accuracy and distance. The radio noise floor, number of devices in a given area and signal strength are all factors that will play into determining how successful this approach will end up being.
We’ll also need to ensure we have the hardware to adequately cover both 2.4 & 5ghz wifi bands, as well as a GPS module to help ascertain distance as well as bearing and location.
Lastly, for efficiency purposes, we also need to look at how we can script this to work effectively. While we can use Python for this, for this exercise we’ll be using a simple bash script that can be run in a terminal with a simple text output. By piping the output into e-speak or similar programs, we can write a script that will provide audible alerts when our device is detected. We don’t need a GUI to get things done!
An Ethical Experiment
While we are of course, cyber researchers, in the OSINT world there’s a thin line between carrying out ethical research and stalking somebody. So when conducting experiments such as these, it’s typically a good idea to start with clear boundaries, use your own devices and consider the ethical limitations that might come with performing open-source research in this fashion.
For this experiment, to understand the real-world implications of these probe requests, I’ll be conducting ethical research on my own devices and using people who are willing victims. Sorry, test subjects.
Lastly, we should remember, that it’s illegal to pentest, hack or assess networks without permission from the owner. Keep things legal and make sure your white hat stays on. Your conscience can stay guilt-free and your body can stay out of jail.
Beyond Wi-Fi: Bluetooth Probe Requests
It is also worth mentioning that Wi-Fi is not the sole player in the probe request game. Bluetooth-enabled devices also engage in similar interactions. This allows analysts to detect and use these packets in the course of their research, similar to the experiment we conducted with Wi-Fi devices.
While exploring this is outside the scope of today's article, we’ll be covering this topic in a future article, using the ultra-cool Flipper Zero. While the Flipper isn’t the be-all and end-all of radio hacking, it’s great for beginners to use during the learning phase, and you can expect to see a lot more of it in use in some of our upcoming articles. The flipper is definitely an addition to the cool tools kit. Source: Wikipedia.
The flipper is definitely an addition to the cool tools kit. Source: Wikipedia.
Closing Thoughts
So with that, the stage is set, the devices are charged and the script is written! Our experiment is ready to be conducted. In part two of this article, we’ll put our new script into play and use it to detect our devices. Will this be an excellent alternative to GPS or RFID-based tracking devices, or will it be a washout and fail to provide us with the information that we need? Either way, it’s going to be one fun experiment, so stick around for next month to see what we can find.
Lastly, don’t forget that if you’re a radio nerd, you can find all our Radio-related hacking articles in our Radio Hackers publication.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Signals From Space: The International Space Station
- Ukraine OSINT: Strava Strikes Again
✉️ Want more content like this? Sign up for email updates