Historical Hacks: Operation Aurora
In previous articles, we’ve made the point that in the early days, a lot of notable cybersecurity events weren’t exactly what we’d call malicious. While they’d certainly be damaging in terms of lost productivity or downtime, often these attacks were the result of research or curiosity gone wrong.
Over time though, we’d start to see cyberattacks or more specifically, cyberwarfare become more and more relevant to state-based actors. In today's historical hack, we’ll be taking a look at one of these more noteworthy events by exploring and analysing Operation Aurora.
Accepted at this point as the result of a state-backed operation, Aurora would breach a large amount of data and force professionals to rethink strategies to identify and contain advanced persistent threat groups (APTs). Let’s check it out!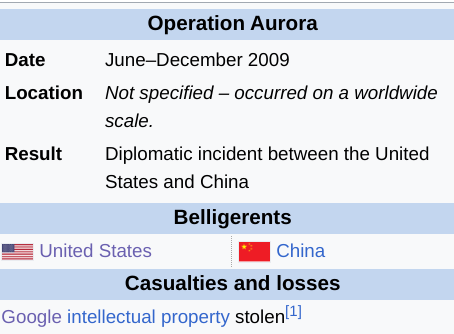 Aurora would be discovered in 2009, with the loss of a large amount of intellectual property. Source: Wikipedia.
Aurora would be discovered in 2009, with the loss of a large amount of intellectual property. Source: Wikipedia.
Background
While the acceptance of China as a near-peer power is common in today's world, it’s reasonable to say that this wasn’t always the case. Over time though, we’ve seen the evolution of a number of different aspects regarding military power, soft power and a willingness to pursue geopolitical ambitions via various means.
As an extension of this, we’ve seen changes in both the military resources and strategies applied by the PRC. With the early 2000s being a rough time for Chinese aviators, a steady stream of funding and expansion has seen new, high-tech assets fielded in the past two decades. The J-20 provided China with it’s first, indigenous stealth aircraft. Source: Wikipedia.
The J-20 provided China with it’s first, indigenous stealth aircraft. Source: Wikipedia.
However, it’s not just military and kinetic assets that have evolved through this timeframe. Like many states, China too has given resources to both offensive and information operations that are to be conducted in the cyber domain.
Often, these events are subtle, taking a significant period of time to be discovered. At other times, they are extremely overt. The Type 055 Destroyer would signal a shift in Chinese naval evolution as well. Source: Wikipedia.
The Type 055 Destroyer would signal a shift in Chinese naval evolution as well. Source: Wikipedia.
Advanced Persistent Threats
If you’ve spent any time working in cyber or researching cyber incidents of technology, you’ve probably already heard of APT groups. If you haven’t though, it’s worth breaking down exactly what this means.
Typically, in the purview of state-based actors, APTs have the means, funding, and persistence to act as a significant threat over an extended duration of time. In English, what this means is that APTs will be highly motivated, well-resourced and know exactly what they are looking for. They’ll also have the skills to carry out a few things needed for a successful long-term hack. The first is persistence, meaning that the threat actor has the ability to stick around far longer than the average script kiddie.
The second is lateral movement. This essentially refers to the ability of an attacker to move across and through a network. This is important, as it means that where the attacker starts, is typically not where they’ll end up.
These factors combined with others mean that APT Groups have the ability to cause significant damage when needed.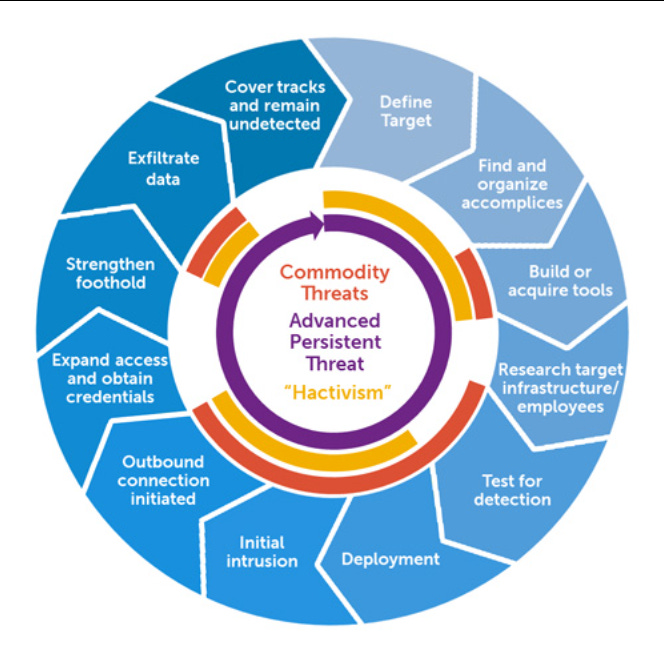
The Hack
Understandably when we consider these factors it’s no surprise to learn that the attack was vast. So vast in fact, that multiple well-known companies were revealed to have been struck by the attackers in some way.
Which companies you might ask? Northrop Grumman, Adobe, Google, Symantec, Dow Chemicals and Morgan Stanley, just to name a few.
While the attacks would vary according to the target and the type of intelligence offered, it’s no lie to say that these attacks were well-motivated, well-planned and well-executed.
Carried out by a group known as the “Elderwood Group”, rather than leverage social engineering techniques, this group would use a number of Zero-Day exploits to help gain access to and exploit systems.
Once access was gained, the group would use a “Watering Hole” strategy that would help to identify further machines of interest to exploit.
Notably, once the attack was analyzed, Internet Explorer was identified as the weak link. This would signal the start of end days for Microsoft’s already struggling browser.
The Fall Out
As you’d imagine, a cyberattack that targeted both government and commercial platforms would lead to a significant amount of fallout when discovered and this attack would be no different.
Like many cyber attacks though, it would take some time to identify what had occurred, who had done it and exactly what had been lost. With many of these companies having large, well-resourced cybersecurity divisions, incident response teams would be hard at work identifying useful information and mitigating the fallout.
During this discovery phase, a number of relevant and interesting pieces would be uncovered. Aurora, for instance, wasn’t just a randomized name of an operation. It would be identified as part of a file path during the investigation, eventually being applied as the name of the operation.
Even more controversially, Microsoft would eventually issue a press release stating that they knew about the vulnerabilities that were exploited as well. Not a great look for one of the world's premier software companies.
The most fallout would come from a large company that we know all too well though. The Big G (Google).
Suffering a significant loss of intellectual property as well as having a large amount of data breached, Google responded by threatening to withdraw its overseas operations from mainland China.
In the following years to come, Google would explore the attacks in even more detail by releasing a short, multi-part series on the attacks and their fallout.
Consequences
As you’d imagine, in these types of circumstances there can be a significant lack of overall information as both governments and companies deal with the matter of saving face in the aftermath. This event would be no different however there are still a few interesting takeaways that we can deduce from the situation.
While the Chinese government would never officially admit to the attack, the incident would still strain US-China relations. It would also shine a light on Cybersecurity as a national security problem, rather than simply something to be dealt with by companies.
Because of this, Aurora would influence how we see cybersecurity in a significant way. New funding would be provided and new cybersecurity postures were assessed and implemented in an attempt to gain an improved security footing.
Interestingly enough, in today's world, it seems like we’ve forgotten some of those hard lessons that were learnt in the early days. For many, cybersecurity divisions are still seen as “nice to have” rather than the essential divisions that they are.
It takes just one critical event to change history, and those who forget the mistakes of the past, are often bound to repeat them.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Space Shuttle
- Shodan: A Map of the Internet
✉️ Want more content like this? Sign up for email updates