Twisted Tweets & Bots Unleashed
Exploring an interesting evolution in the information space.
If you aren’t a medium member, you can read with no paywall via substack
This article deals with malware and malicious links. All relevant tweets are screen captures rather than embedded, to minimize the risk of spreading malware. Browse safely!
In this previous article, we started to explore how the spread of disinformation has become easier, using ChatGPT and API-based access to quickly and easily empower bots with the means to engage automatically on their own.
While this was an interesting topic, one thing that we didn’t mention was that this was by no means a one-and-done piece. So, we’ll continue to explore this issue on social media and where relevant (and interesting), write it up as an analysis. So, welcome to part two of this series where we jump into the pit of disinfo known as X/Twitter and try to get our hands dirty. Today though, we won’t just be looking at disinformation though. There’s also real-life malware and phishing caught out in the wild. Let’s go!
Information Warfare
While the concept of disinformation isn't exactly new, it’s fair to say that in the modern world, with modern tools it’s now far more relevant than it once was. And while we won’t point fingers, the fact is that some countries are more well-known for spreading disinformation than others. It also just so happens that one of these countries happens to be in wartime mode. This means that controlling the information space is a hugely important part of a modern conflict and that much can be gained by processing and disseminating as needed.
As you’d imagine, during times of war, this is pretty important generally speaking. But during times of intense pressure or stress, it becomes even more important. The fog of war is real and controlling the narrative and flow of information could be the difference that makes or breaks a kinetic action.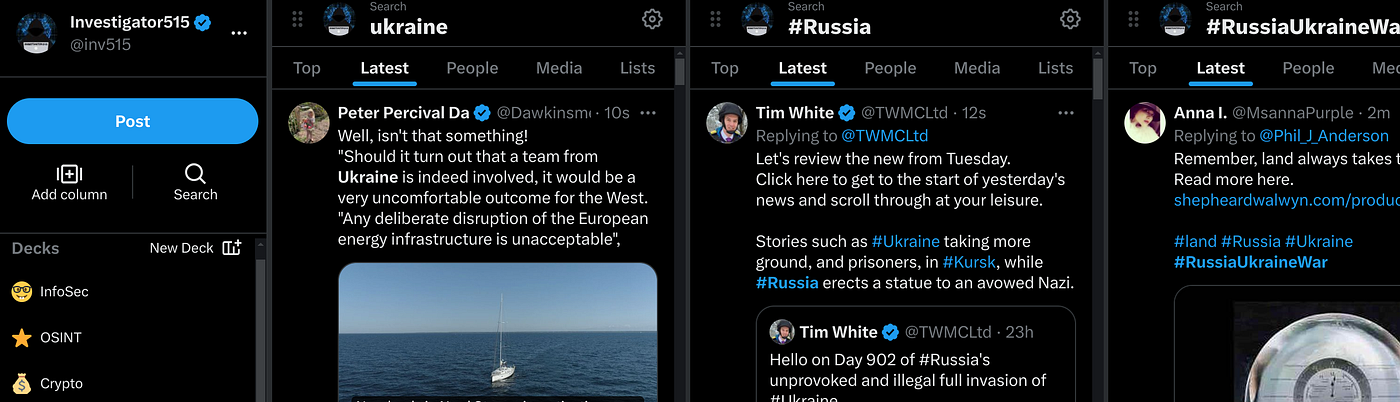 Deck view and other tools show us large amounts of data and trends in real-time. It’s a great tool during breaking events and critical incidents. Source: Author.
Deck view and other tools show us large amounts of data and trends in real-time. It’s a great tool during breaking events and critical incidents. Source: Author.
We saw an example of this recently when Ukraine moved forward into Kursk, taking the initiative on the battleground and upending the current dynamic. While the details of the offensive are outside the scope of this article, one thing that is worth discussing is the attempt we saw in regard to controlling that narrative. It’s worth mentioning though that this was no small effort. As the activity unfolded, exploring hashtags via the deck view showed multiple posts occurring every second at its peak. This isn’t a one-off attempt at a cyber attack. This isn’t even information warfare. It’s a straight-up pit of malware, trying to catch out journalists, analysts and members of the general population. We also call it a cyberattack.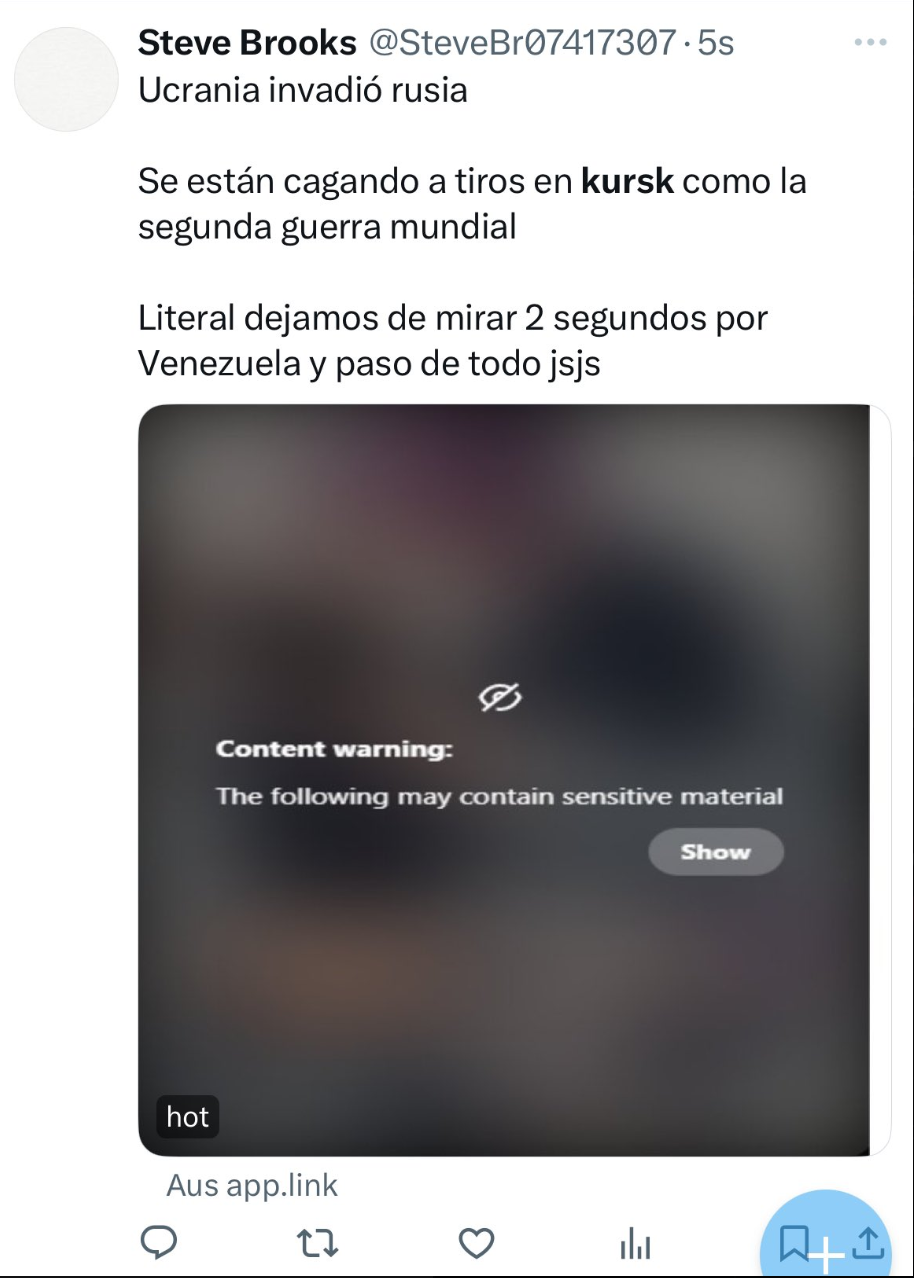 An example of our sketchy tweet. Source: X/Twitter
An example of our sketchy tweet. Source: X/Twitter
The Offending Tweets
While the accounts spreading the offending tweets were too numerous to identify, there were distinct patterns that helped tie accounts together making the identification process easier. Correct analysis would still need to be done for full verification, but we could use pattern analysis and other strategies to help identify bad actors in real-time. In case you’ve missed some of these markers in the earlier article, we’ll cover them for you now.
- Username: Usually a combination of Words/Numbers
2. Profile Picture: Missing or AI-Generated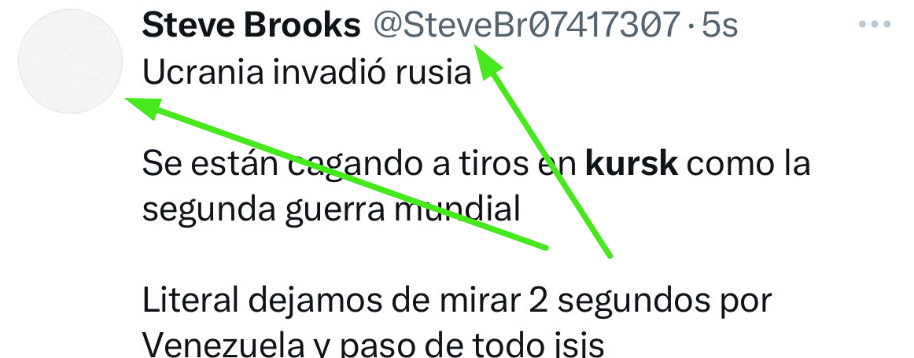 Name/Number & No profile picture. Source: X / Twitter
Name/Number & No profile picture. Source: X / Twitter
3. Sensitive Content Warning: To help hide the malicious link
4. Link Attached: To redirect you to the malicious site.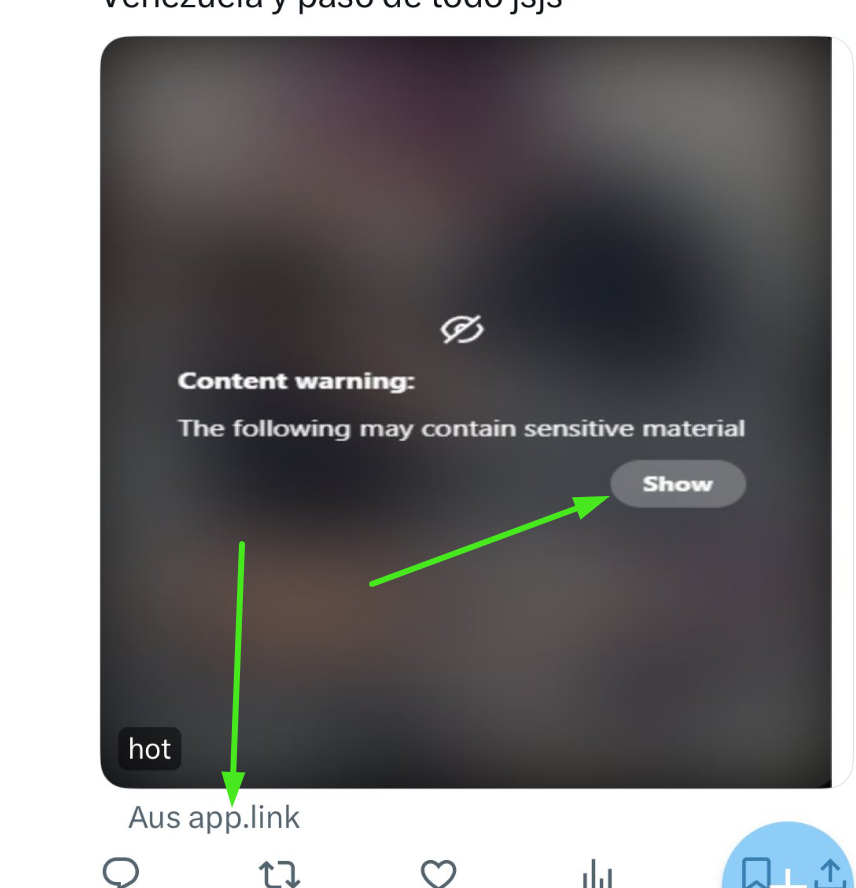 As well as sensitive content warnings and third-party links. Source: X/Twitter
As well as sensitive content warnings and third-party links. Source: X/Twitter
This time though. We got pretty lucky, as putting the link into VirusTotal would end up giving a heap of actionable intelligence.
The Malicious Domain
While the link would use a number of techniques for obfuscation purposes, including a link shortener as we all know, there’s no hiding from the internet. This means we have an actionable domain to research now as well.Here’s the whois information of our malicious domain along with some additional data,
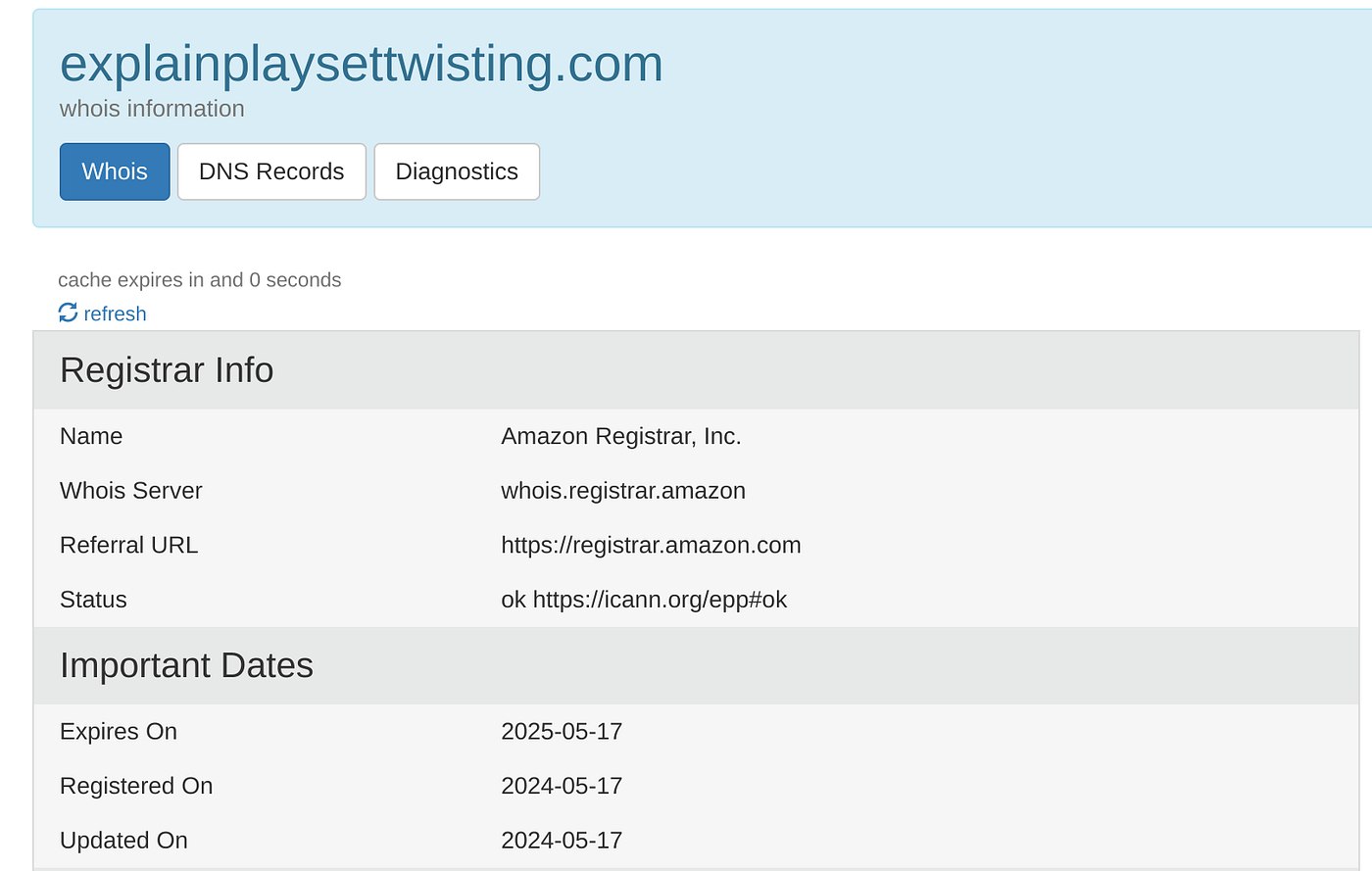
Complete with available DNS records. Eagle-eyed users may have noticed some actionable information from the whois data — can you see what it is?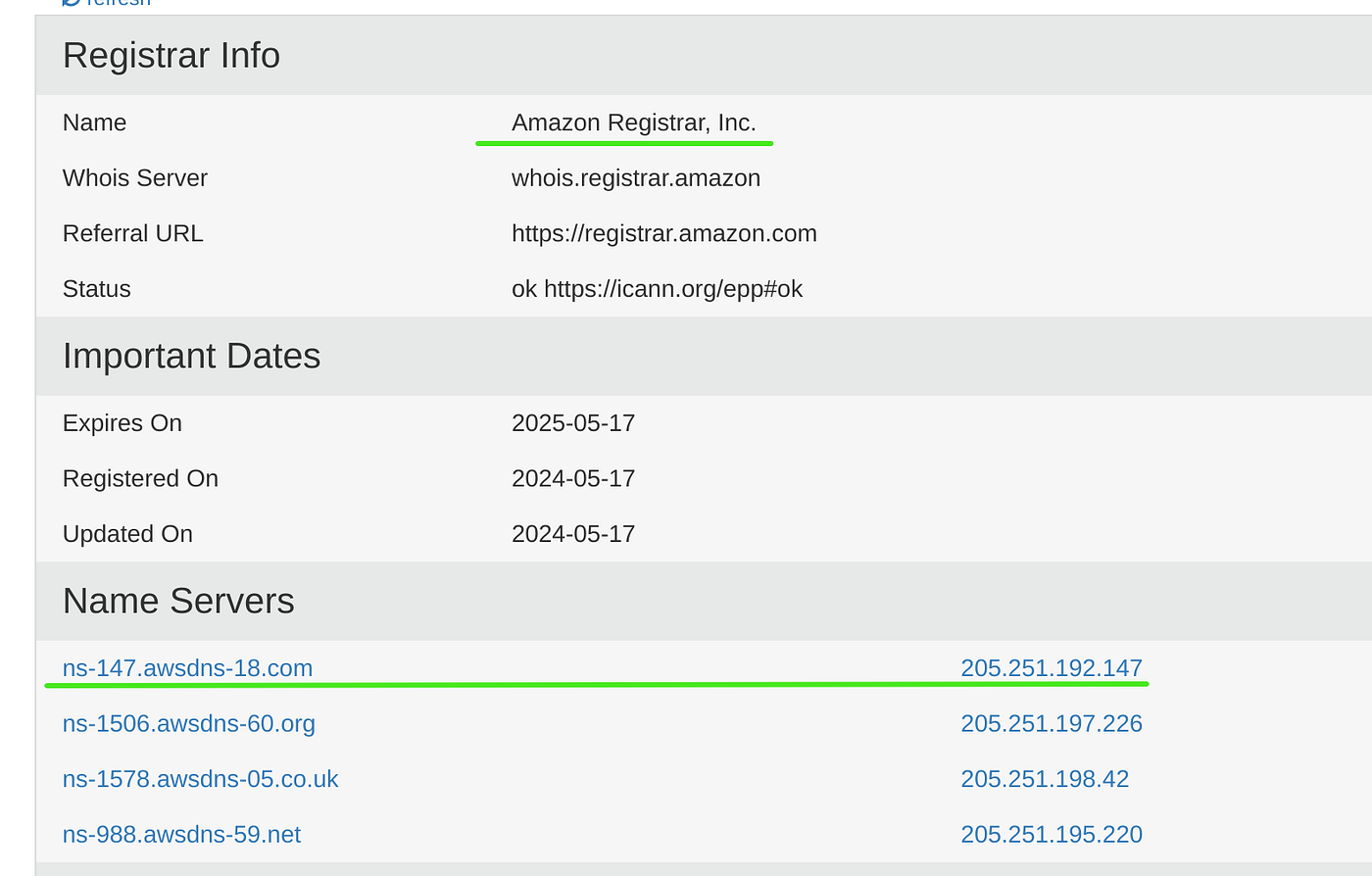
If you noticed that our bad domain was being hosted by Amazon’s AWS cloud then you’re spot on the money. This means we can report it for breaching the AWS terms of service, and have better odds of taking it out via an X/Twitter report, which doesn’t really seem to be answered much these days. What’s up with that?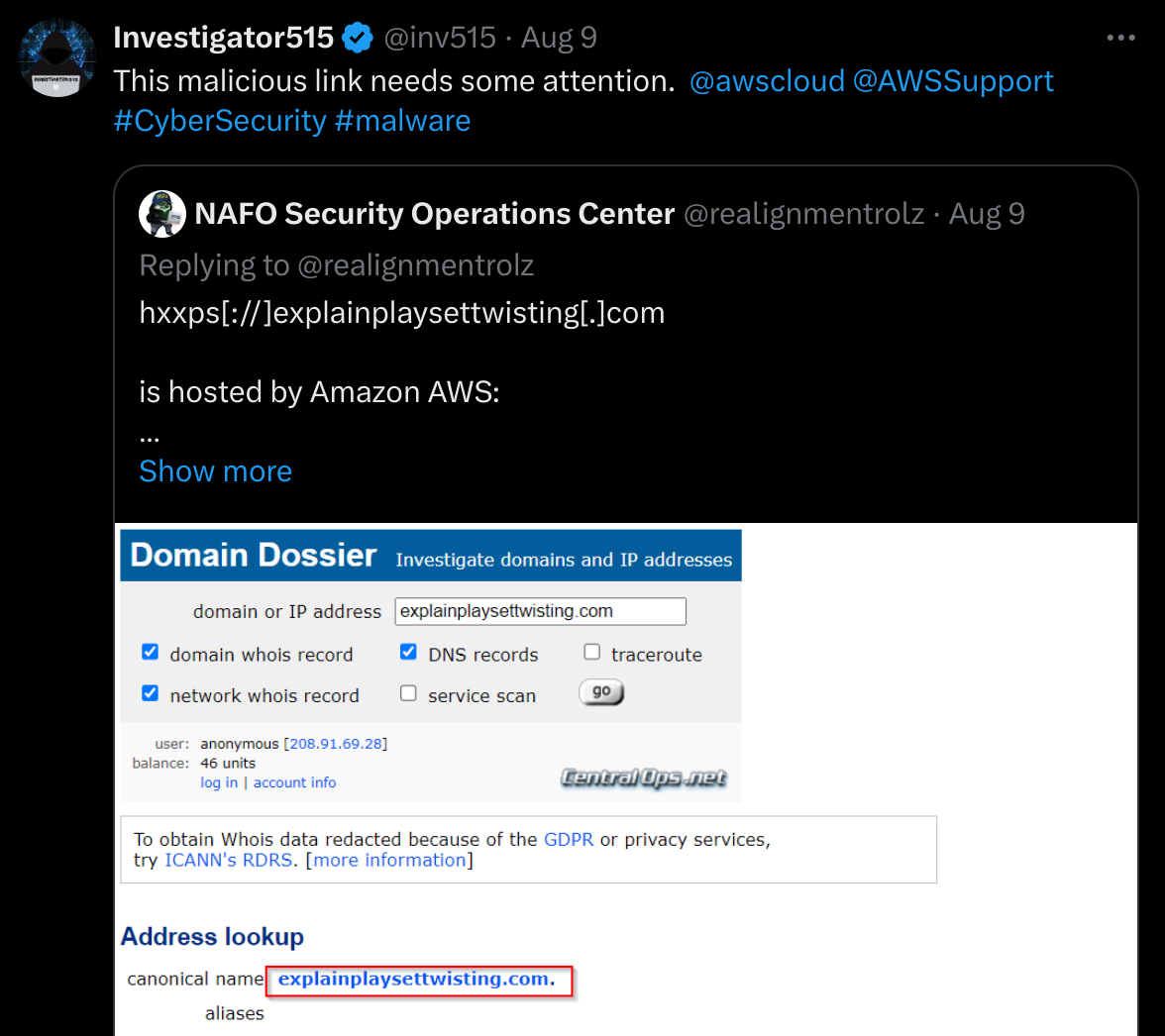
For credit where credit is due, AWS was prompt in responding to the query and providing rectification strategies for getting the complaint to the right people. X on the other hand? Yeah, you know how that turned out.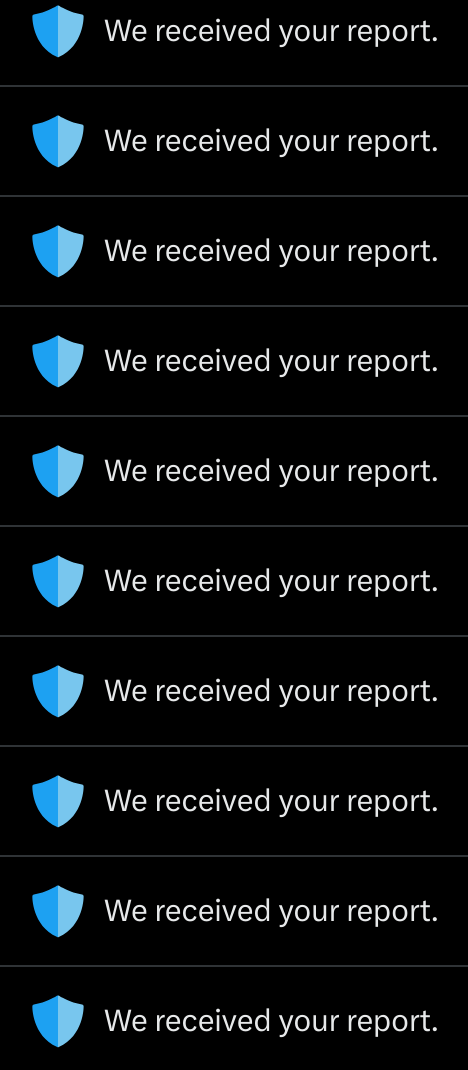
Summary
While this was a pretty basic analysis it is worth mentioning that for some reason, the malware we looked at in today's article didn’t seem to do too much when it was run in a sandbox. In fact, it appeared to be distinctly mobile-flavoured, ignoring laptops and PCs.
However, we’d need to look much deeper into how it works to ascertain that for certain.
What we can do as a result of this though, is spark a discussion about privacy and consider how this might affect our day-to-day browsing habits or general cyber hygiene. Many in the crypto space, have learnt to become aware of encountering malicious links or malware on sites just like this but the reality is that for many users, encountering this type of thing while browsing for news or using a “trusted” app is a relatively new thing. Particularly at the levels we’re currently seeing.
The reality is that like modern warfare, cyber defenders have to get lucky every time, while cyber attackers have to get lucky just once to be successful. Incidents such as these are great reminders to us all to use good cyber hygiene and be vigilant when consuming social media.
In fact, you could even say that even cyber professionals could use a reminder of the importance of this every once in a while as well. We are all human after all.
Thanks To
Teamwork makes the dream work and fighting disinformation would be a losing battle if we did it alone. So, a quick shout out to the following accounts on X / Twitter that helped provide information that was valuable in compiling this blog post.
Pekka Kallioniemi: Author of Vatnik Soup
NAFO Operations Center: Domain Research
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Rocket Engines
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates