How To Recognize Ledger Scams - Three Phishing Attempts Explored
In this post, we will explore three Ledger phishing scams so you can learn how to recognize them easily:
- First Phishing Scam: The victim's details are for sale on the dark web. One scammer who purchased the victim's details has organized a rather credible spear phishing attack.
- Second Phishing Scam: In this second case, it gives the impression that the scammers are still learning the basics, so their scam is rather basic with a very low probability of success.
- Thirst Phishing Scam: The scammers have put effort into creating a credible phishing website that, when doing our research, was not yet flagged as malicious.
Recognizing 99% of phishing scams is quite straightforward if you know what to look for.
So, we hope that by the end of this post, you have learned how to stay clear from most phishing attacks.
First Ledger Scam - We Know Who You Are
In this first Ledger phishing scam, the victim receives a phishing email stating that urgent action is required to ensure that the victim's Ledger account remains safe and available.
The email mentions the victim's name, surname, and phone number, which makes it more credible and highly increases the probability that an unsuspected victim falls for this scam.
This first Ledger Scam is an example of a Spear Phishing Scam.
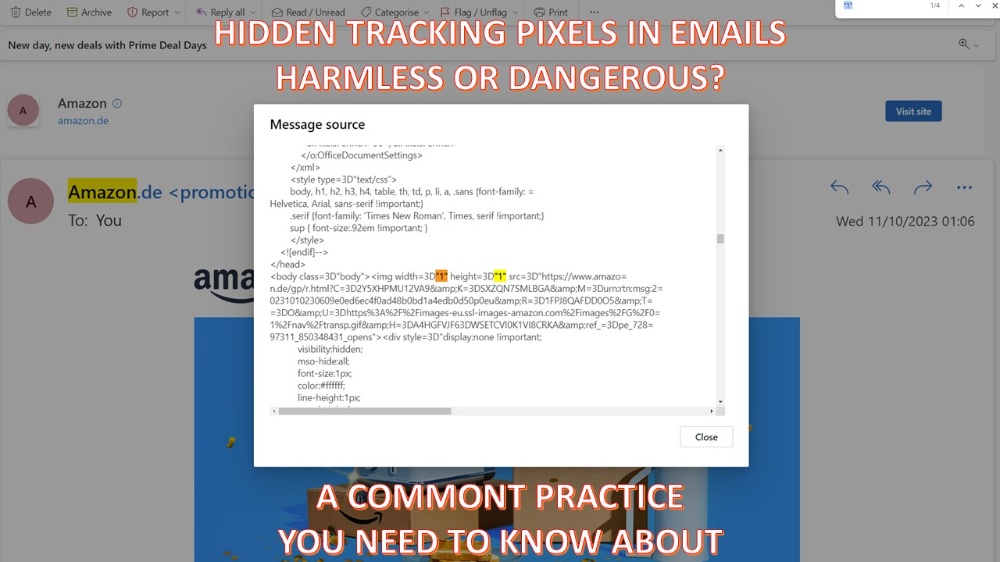
Nobody should open a phishing email because most of those emails contain invisible tracking pixels that will notify the scammer and provide valuable information about the victim.
Or, even worse, opening a phishing email can be a step towards a sophisticated Man-in-the-middle (MitM) attack.
But anyone can have a bad day, and you may accidentally open a phishing email. Just note that this action, opening a phishing email, will have consequences even if you don't click over any malicious link or attachment.
The sender of this first phishing email is 'lmsalertsATacquiroleadsDOTcom', a domain (acquiroleadsDOTcom) unrelated to Ledger.
A legitimate email from Ledger will be sent from the domain ledger.com
Like the email from the example below.
Or the email from the example in the picture below, sent by a legitimate Ledger subdomain (news.ledger.com.
Subdomains are a way to organize and structure websites, and they are created by adding a prefix (such as "news") to the main domain (in this case, "ledger.com"). So, "news.ledger.com" is a subdomain of "ledger.com.
An email from an unrelated domain, in this case from acquiroleadsDOTcom, should already be a clear indication that this is a phishing email, and anyone should close the email at this point, send it to the trash bin, and report it.
Like we have done in this example.
You don't need to open phishing emails to learn about them. Let us do it to show you what they look like and how they convince their victims to take actions that will be detrimental to them.
Most phishing emails use amygdala hijack to induce panic and an irrational response from the victim.
The amygdala is a part of the brain that processes emotions, particularly the generation of strong emotional responses like fear.
An "amygdala hijack" occurs when the amygdala takes over and triggers a strong emotional reaction, often overriding logical or rational thinking.
Phishing emails often use tactics to induce panic or a sense of urgency to trick individuals into taking immediate action without considering the potential risks.
You should never click over any email attachments unless you are 100% sure that the email and attachments are legitimate.
But to show you what happens when you accidentally click on a malicious link, we have opened the phishing email attachment. That, in this case, is a URL to a phishing page.
On this page, the scammer does request the victim to confirm identity, and for that, the following personal information is mentioned: name, surname, email address, and home address.
You will ask yourself: How come the scammer has that much of the victim's personal information?
Well, this happens because data breaches are quite common, and some years ago, many Ledger customers were victims of one such data leak.
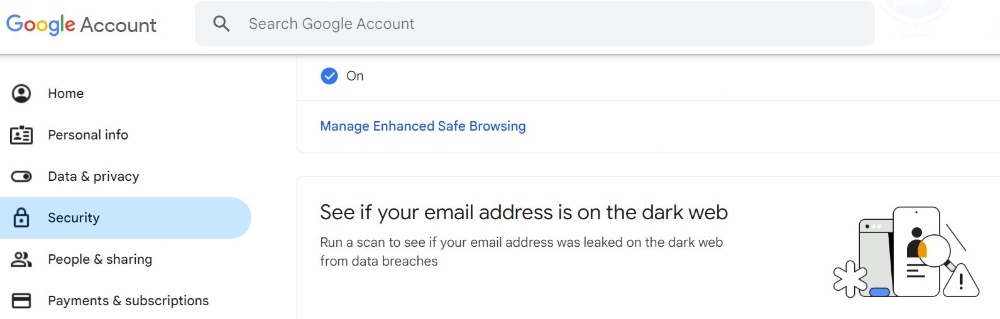
If you have a Google account, you can easily find out if your account has been leaked to the dark web.
Alternatively, you can use 'have i been pwned?' to check if your email address is in a data breach.
Returning to our First Ledger Scam, the scammer asks the victim to confirm the device model.
Once confirmed, the scammer requests the victim to provide the wallet seed phrase.
Cryptocurrency scammers are nearly always after the victim's cryptocurrency wallet seed phrase. Because this is by far the easiest and most profitable target.
Second Ledger Scam - Scammer Still Learning
The second Ledger scam is far less well organized than the first one, but it is still worth reviewing.
Once again, most phishing scams are easily identified by looking at the sender's email address. In this case, tradestarDOTcomDOTbr has clearly nothing to do with Ledger, so this email can clearly labelled as phishing.
Still, we want to remark that in some rare cases, the scammer takes the time to create a domain name nearly visually identically, which can be very difficult to spot.
This is called Unicode domain phishing.
Unicode domain phishing involves using characters from different scripts to create deceptive domain names that resemble legitimate ones. Attackers exploit visual similarities to trick users into visiting malicious sites and disclosing sensitive information. This is often done through Punycode encoding.
You may be thinking: If the phishing attacks get so sophisticated, how can I differentiate legitimate from malicious domains or URLs?
Your most important tool is your security and safety knowledge and experience. However, some online applications can be used to complement your knowledge.
More on that at the end of this post.
In any case, in this second phishing email, there is a link to a phishing website that the scammers claim our colleague needs to visit to perform a security upgrade.
We have clicked on the link to study how this phishing attack works. Straight away, we received an alert from Chrome warning us that the website we were trying to access was malicious.
We know that and are taking precautions, so we have proceeded despite the warning.
Still, this is a poorly organized scam, and the phishing website is missing the SSL certificate, so even if a victim ignores all the signs and warnings, nothing will happen due to the website's unavailability.
While this looks like a relatively harmless phishing attack, please be careful not to open phishing emails to check what is on them.
Instead, use educational content to learn what to do if you accidentally click on a phishing email or link.
Third Ledger Scam - Flying Under The Radar
The third scam is more sophisticated than the second but may not be as well organized as the first scam.
As with the other two scams, this email also proceeds from a domain (intrentino.com) that has nothing to do with Ledger.
Once again, it only takes a brief look at the email sender domain to identify most phishing emails.
In this phishing scam, we are asked to click over a link to visit a phishing website (nanochecker.com) and perform a security update on our ledger device.
On this occasion, we were not warned that we were about to visit a phishing website. This is an excellent lesson to refrain from over-rely on external sources to identify phishing websites and to develop our security and safety awareness.
Once again, and this is a similarity to nearly all crypto wallet scams, we are asked to provide our wallet seed phrase.
Of course, we will not do it, but we click over 'continue' anyway. Then, the phishing website directs us to the legitimate Ledger website, and the scam is over for the victim.
While the victim is trying to figure out what is happening, the scammer will recover the victim's wallet using the seed phrase and clean the victim's account.
If you ever come across a phishing website that your browser has not yet identified as such, please report it to the 'Google Report Phishing Page.'
If you do so, you have done a good deed and maybe saved a fellow Cryptoverse user from losing valuable crypto assets.
Before we finish, consider using free online tools to analyze suspicious domains or URLs. Like the one from the picture below, Virus Total has flagged nanocheckerDOTcom as malicious.
It takes only a few seconds to navigate to the tool and input the domain or URL you want to analyze.
Thanks for reading until the end. We have made a video about this topic.
No need to watch it if you have no time. But if you still have some minutes to spare, the video contains some extra details for the second and third scams.
All our videos can be found on the Crypto Safety First YouTube Channel.
Please consider subscribing to our channel to support a fellow Bulb app content creator. Appreciated. Thanks.
_____________________________________________________________________________________________
Congratulations on completing this 5-minute digital safety power-up.
We hope this 5 minutes read was worth the time and that you have learned some valuable information.