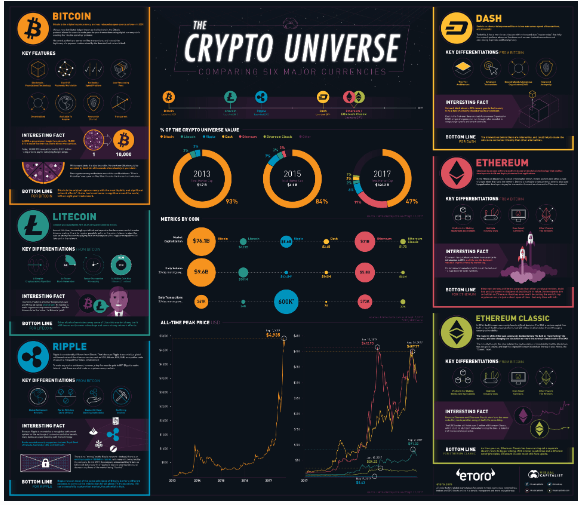
5 Computer Viruses From the Early Days of the Internet
It took a while for bad actors to come on to the scene.
While malware and other scams are all but accepted as part of the modern world, it hasn’t always been this way. In the early days of the internet, before smartphones proliferated it was a much calmer place. However it was only a matter of time before we started to see governments, cyber criminals and intelligence agencies begin to leverage computer viruses for their own means. In this article, we’re going to take a quick walk through of some interesting computer viruses that we’ve had to deal with over the years. We’ll look at malware, worms and other interesting attacks and with the motivations for said viruses ranging from everything to free internet to disassembling a nation states nuclear program, it’s safe to say today will be an interesting walk through the history books.
5. Melissa (1999, United States)
Melissa was unique for the time, as in the early days the internet was still considered to be a reasonably unknown place in regards to the risk of carrying a virus. With floppy discs still the rage and the CD ROM still in it’s early days, the earlier viruses of the time could do significant damage simply due to the fact that the way they spread and propagated was unsual.
Designed in Florida by David L Smith, and named after an exotic dancer, Melissa’s origin was in a Word Document that was posted to the Usenet Forum under the guise of passwords for pornographic material. Once opened, the virus would select up to 50 users from the machines address book and send infected correspondence directly to them. This meant that Melissa spread rapidly, causing chaos in a world already trying to deal with the perceived issues due to Y2K.
Despite using a stolen AOL account for the upload, Smith was captured due to metadata within the document less than a week after the outbreak and provided assistance to the FBI, leading to a reduced sentence. The Melissa outbreak was estimated to have caused up to 70 million dollars damage. 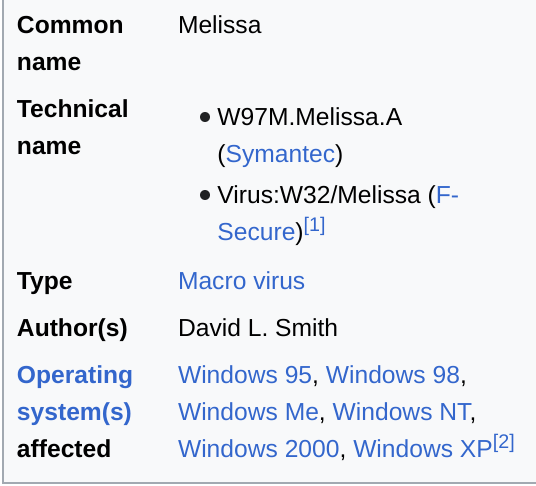 Wiki Extract for Melissa. Source: Wiki
Wiki Extract for Melissa. Source: Wiki
4. Anna Kournikova (2001, Netherlands)
Coming a few years after Melissa, the Anna Kournikova virus was named due to the fact it had a picture of the famous tennis star. Created in just a few hours by 20 yo student Jan De Wit, the virus was a simple worm written in visual basic. This virus was notable as it was created by a visual basic worm generater, a piece of software obtained on the same day that the was released. Whilst it’s important to note that this virus didn’t corrupt data like many of the viruses prior, it was notable for it’s impact on email systems and servers, which struggled with capacity during the peak of the spread.
While Melissa creator David Smith provided advice to the authorities on this virus, Jan De Wit was eventually caught after handing himself in, confessing that he did not expect the virus to spread in the way in which it did.
After being charged with the offense of spreading data with the intent to cause damage, De Wit was later offered a job by the government within the Netherlands. The Anna Kournikova worm was estimated to cause around $166,000 USD in damages.
3. Code Red (2001, Philipines)
Code Red was an interesting bug first detected in the very early 2000’s. Adopting it’s name from the Mountain Dew drink the programmers were consuming when it was discovered, Code Red was a worm that took advantage of a simple buffer overflow attack giving remote code execution opportunities on many machines.
Code Red was interesting as it ran to schedule, looking to complete several objectives as the worm unfolded. Date Controlled, the Code Red worm worked to the following schedule.
Day 1–19: Opportunities for spread among uninfected machines.
Day 20–27: Denial of Service attacks on several IP addresses, including one that was linked to the White House.
Day 28–EOM: Dormant.
Leaving a message on infected machines that read “Welcome to worm.com, Hacked by Chinese!” the infection peaked on the 19th of July 2001 when over 359,000 machines were estimated to be infected. While this is a small number compared to the damage modern viruses can do, it’s important to remember that this was in the pre smart phone era when the internet was a far smaller place.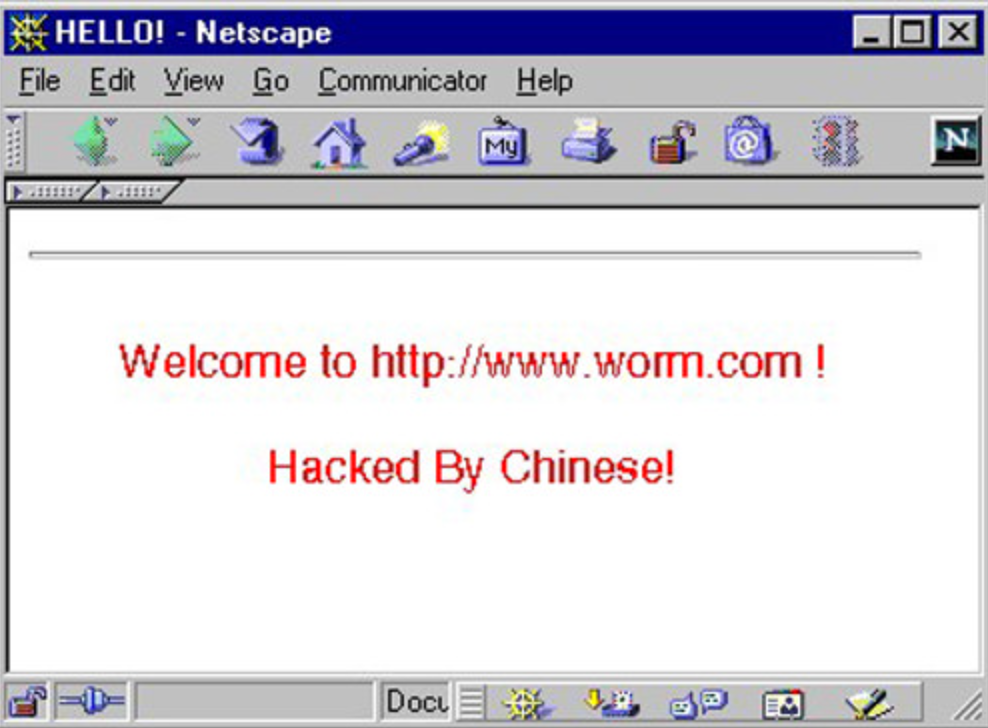 Code Red was simple and devastatingly effective. Source: Wiki
Code Red was simple and devastatingly effective. Source: Wiki
2. Michelangelo (1991, Australia)
Michelangelo was a particularly old version of virus, originally designed to infected DOS based operating systems.
Operating at the BIOS level, Michelangelo was unique due to the fact it did not engage the operating system, and like others we’ve referenced in this article, operated around time constraints.
On March 6th, the virus would start to corrupt hard drive sectors, overwriting the values with nulls. Due to the fact the virus would spend large periods of time dormant, it meant that infections could potentially last years before detection.
Despite being given the name Michelangelo and March 6th the artist’s birthday, the virus had no reference to Michelangelo within it’s code and it’s generally accepted that these are merely coincidences and that there is no real link between the two.
Michelangelo makes our interesting list due to the fact that in 1992 a number of computer manufacturers had shipped components and systems pre infected with the virus, causing a large amount of concern among security specialists. Despite the fact an infected system had the potential to last years in the right conditions, the damage done by the virus was relatively low, and by the late 90’s cases were no longer seen in the wild.
1. I LOVE YOU (2000, Philipines)
Also known as the Love Bug, number 1 on our list is the late 2000 computer worm known as the ILOVEYOU worm.
Yet another piece that was written in Visual Basic, the worm came to mainstream attention in early 2000 when it was observed to be spread in the Philippines. Written by 24 yo Onel De Guzman to steal passwords to obtain free internet, the worm proliferated after geographic restrictions were removed causing a rapid spread through computer systems world wide.
Coming after the hype of the millennium bug, and not too long after the Melissa Virus, ILOVEYOU caused massive amounts of damage during spread, mostly due to how it was configured.
Once infected and after damaging files within the local machine, the code copied itself into all addresses in the Microsoft Address Book, allowing the worm to spread prolifically in a short period of time. At the peak of the infection, it was estimated that at least 10% of computer systems worldwide had been affected, causing over 5 billion dollars worth of damage over the period of the infection. At one point things were so bad that large multi national corporations were pulling entire systems off line in the hopes of arresting the spread with minimal damage.
De Guzman, who was identified by police in May 2000 was eventually charged for the virus. However due to laws lagging behind the progression of technology, he was released with out charge later in the year.
In one last twist to the case, in July 2000, Philippine legislators passed the Republic Act 8792 in response to the Love Bug. Known as the e commerce law, it prohibited the writing and spreading of malware in the Philippines, bringing the laws up to date with the technology of the time. 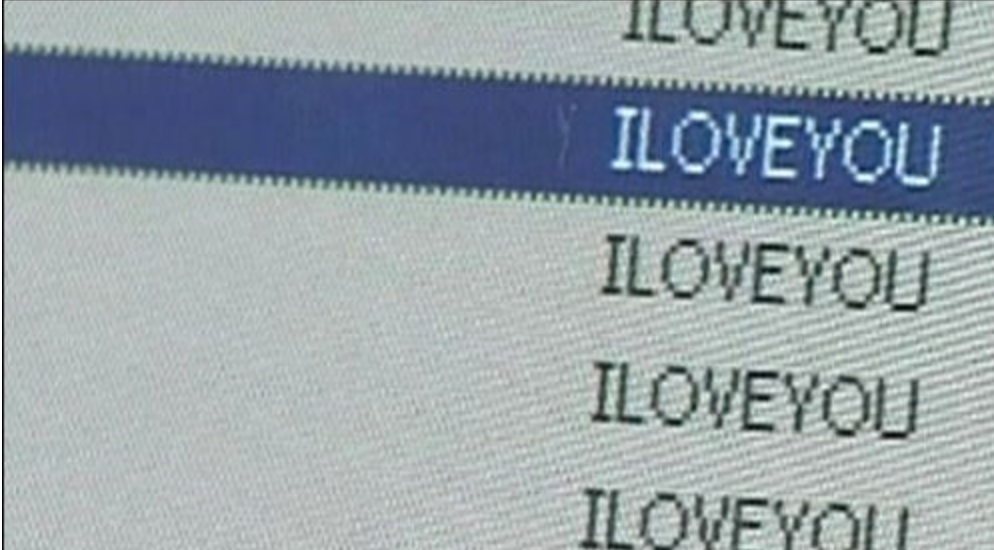 The Love Bug proliferated fast enough to cause extensive damage. Source: Wiki
The Love Bug proliferated fast enough to cause extensive damage. Source: Wiki
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our Telegram channel for exclusive updates or.
🐦 Follow us on Twitter
🔗 Articles we think you’ll like:
- OSINT Unleashed: 5 Essential Tools for Cyber Investigators
- What the Tech?! GPS Technology
✉️ Want more content like this? Sign up for email updates here