Unraveling the Layers: Exploring the Significance of Layer 2 in Networking Technologies
Introduction
In the dynamic realm of networking, Layer 2 stands as a fundamental cornerstone, playing a pivotal role in the seamless exchange of information. As an integral component within the OSI model, Layer 2, also known as the Data Link Layer, undertakes the crucial task of ensuring reliable communication between devices. This introductory exploration aims to shed light on the significance of Layer 2 in the networking landscape, providing an overview of its functions, its place within the OSI model, and the essential role it plays in establishing robust connectivity. From Ethernet protocols that form the bedrock of data transmission to advanced technologies like Virtual LANs (VLANs) and the intricate world of switching, this article will delve into the multifaceted layers of Layer 2, unraveling its complexities and unveiling its importance in fostering efficient and secure network communication.
The OSI Model: Placing Layer 2 in Context
The OSI model, a conceptual framework for understanding network functionality, is instrumental in dissecting the intricate layers that facilitate seamless communication. In this context, Layer 2, known as the Data Link Layer, assumes a specific and crucial role within the broader framework. The OSI model consists of seven layers, each delineating a specific set of functions and responsibilities. As we focus our lens on Layer 2, it occupies a pivotal position above the Physical Layer and below the Network Layer. This layer primarily deals with framing, addressing, and error detection, serving as a bridge between the physical transmission medium and the network protocols above. By placing Layer 2 in the broader context of the OSI model, we gain a comprehensive understanding of its purpose and significance in the layered architecture, setting the stage for a deeper exploration of its functionalities and contributions to network communication.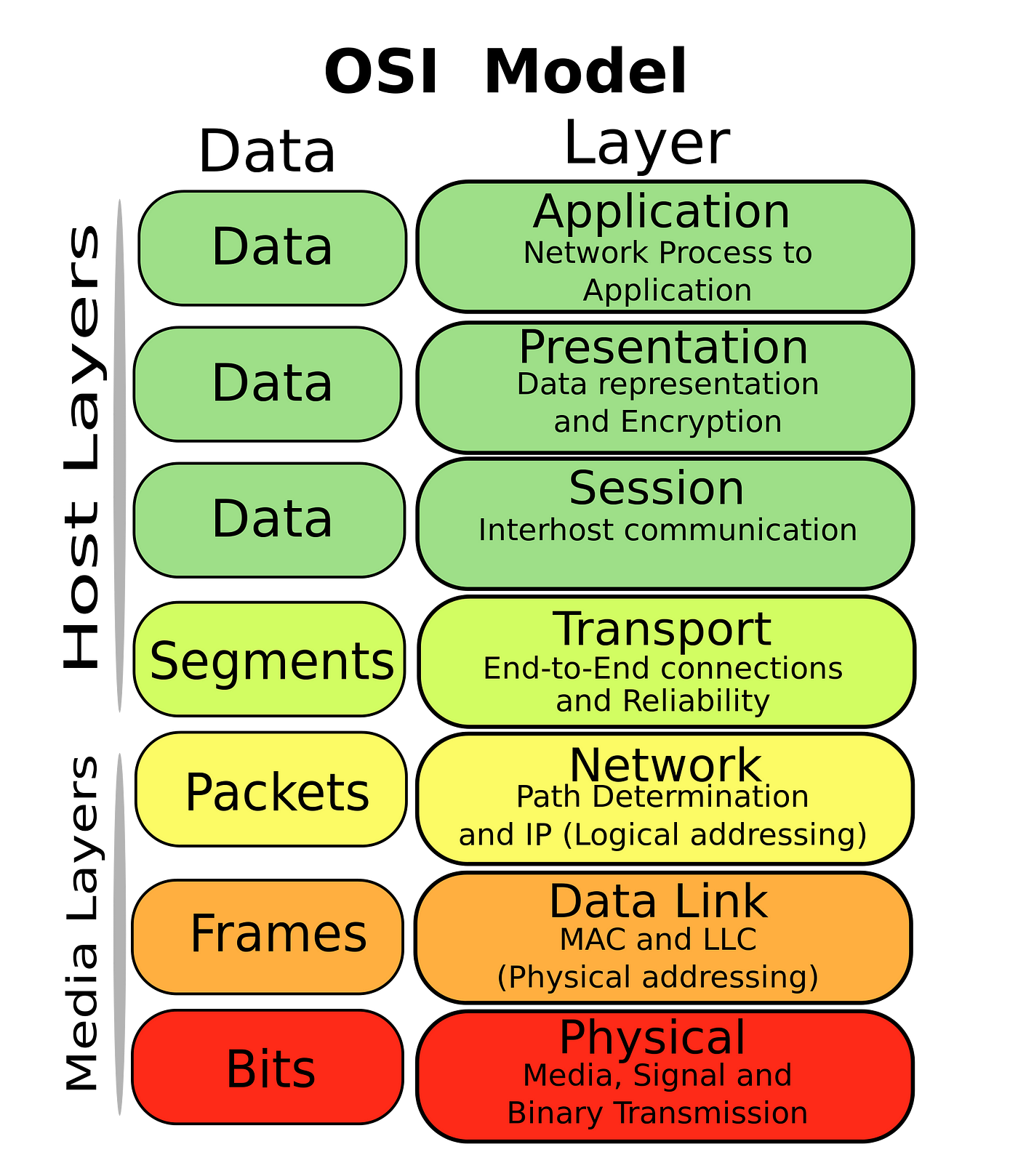
Data Link Layer: Bridging Communication
The Data Link Layer, residing at the second level of the OSI model, serves as a crucial intermediary in the journey of data across a network. Essentially, this layer can be likened to a bridge that facilitates communication between devices connected to the same network. One of its primary responsibilities is to package raw bits from the physical layer into discrete frames, adding necessary information such as source and destination addresses. Through this process of framing, the Data Link Layer ensures that data is organized and formatted for efficient transmission.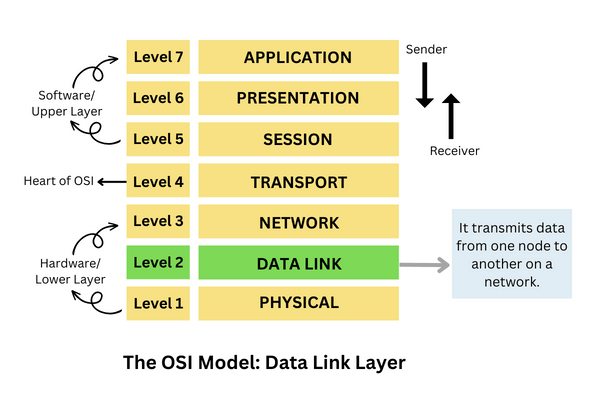 Moreover, the Data Link Layer is instrumental in detecting and correcting errors that may occur during data transmission. By incorporating mechanisms for error checking, such as cyclic redundancy check (CRC), it enhances the reliability of communication by identifying and addressing any discrepancies in the received data.
Moreover, the Data Link Layer is instrumental in detecting and correcting errors that may occur during data transmission. By incorporating mechanisms for error checking, such as cyclic redundancy check (CRC), it enhances the reliability of communication by identifying and addressing any discrepancies in the received data.
In essence, the Data Link Layer not only acts as a bridge between the Physical Layer and higher-level network protocols but also plays a pivotal role in organizing, securing, and validating the data as it traverses the network. As we delve deeper into the intricacies of this layer, its significance in establishing a robust and error-resilient communication environment becomes increasingly evident.
Ethernet Protocols: Foundation of Layer 2 Connectivity
Ethernet protocols stand as the foundational building blocks of Layer 2 connectivity, forming the backbone of modern networking. Ethernet, introduced decades ago, has evolved into a family of protocols that define the rules and standards for transmitting data over local area networks (LANs). At the heart of Layer 2, these protocols govern the way devices share the network medium, manage collisions, and communicate seamlessly.
Ethernet protocols encompass various standards, such as IEEE 802.3, each specifying the intricacies of data framing, addressing, and access control. The widespread adoption of Ethernet has not only standardized the physical and data link layers of network communication but has also contributed to the global interoperability of diverse networking devices. The ubiquity of Ethernet in both wired and wireless environments highlights its adaptability and enduring relevance. As we explore the intricacies of Layer 2 connectivity, understanding the nuances of Ethernet protocols becomes essential to grasp the mechanisms that enable devices to communicate effectively within a network. This section will delve into the diverse facets of Ethernet, examining its protocols and their roles in establishing a robust and efficient Layer 2 connectivity framework.
The ubiquity of Ethernet in both wired and wireless environments highlights its adaptability and enduring relevance. As we explore the intricacies of Layer 2 connectivity, understanding the nuances of Ethernet protocols becomes essential to grasp the mechanisms that enable devices to communicate effectively within a network. This section will delve into the diverse facets of Ethernet, examining its protocols and their roles in establishing a robust and efficient Layer 2 connectivity framework.
Switching Technologies: Enhancing Layer 2 Efficiency
Switching technologies play a pivotal role in enhancing the efficiency of Layer 2 connectivity within modern networks. Unlike traditional hubs that broadcast data to all connected devices, switches operate at a higher layer of the OSI model, intelligently forwarding data only to the intended recipient. This targeted approach significantly reduces network congestion, enhances overall performance, and ensures a more efficient use of available bandwidth.
At its core, a network switch operates as a traffic cop, directing data traffic based on MAC addresses. As data frames arrive at the switch, it examines the destination MAC address, allowing the switch to make informed decisions on where to forward the information. This process not only optimizes data flow but also minimizes unnecessary traffic, contributing to a more streamlined and responsive network. The advent of Layer 2 switching technologies has ushered in advancements such as VLANs (Virtual LANs) and improved collision domain segmentation, further refining the efficiency of network communication. VLANs, for instance, enable the logical segmentation of networks within a physical infrastructure, providing enhanced security and flexibility.
The advent of Layer 2 switching technologies has ushered in advancements such as VLANs (Virtual LANs) and improved collision domain segmentation, further refining the efficiency of network communication. VLANs, for instance, enable the logical segmentation of networks within a physical infrastructure, providing enhanced security and flexibility.
In essence, switching technologies serve as a cornerstone in enhancing Layer 2 efficiency, promoting intelligent and targeted data transmission within networks. As we delve deeper into the realm of Layer 2, understanding the mechanisms behind these technologies becomes paramount to grasp the intricacies of efficient and responsive network communication.
Challenges and Solutions in Layer 2 Security
Layer 2 security presents a complex landscape with its own set of challenges and demands, requiring careful consideration to fortify networks against potential threats. One of the primary concerns in Layer 2 security is the vulnerability to various attacks, such as MAC address spoofing and ARP (Address Resolution Protocol) spoofing. These attacks can lead to unauthorized access, network disruptions, or even data interception.
Additionally, the inherent trust within the same broadcast domain in Layer 2 networks poses a challenge. Devices within the same broadcast domain can communicate directly, but this also means that security measures must be implemented to prevent unauthorized access and eavesdropping. Without adequate safeguards, a malicious actor could potentially gain unauthorized access to sensitive information. To counter these challenges, various security solutions have been developed. Implementation of features like port security, which restricts the number of MAC addresses allowed on a switch port, helps mitigate the risks associated with MAC address spoofing. Secure VLAN configurations and the use of Private VLANs (PVLANs) add an extra layer of protection by isolating traffic within specific VLANs.
To counter these challenges, various security solutions have been developed. Implementation of features like port security, which restricts the number of MAC addresses allowed on a switch port, helps mitigate the risks associated with MAC address spoofing. Secure VLAN configurations and the use of Private VLANs (PVLANs) add an extra layer of protection by isolating traffic within specific VLANs.
Furthermore, the adoption of encryption protocols at Layer 2, such as MACsec (Media Access Control Security), ensures that data remains confidential during transmission within the local network. Regular monitoring, intrusion detection systems, and network segmentation are also essential components of a robust Layer 2 security strategy.
The Future of Layer 2: Navigating the Digital Era
The future of Layer 2 unfolds against the backdrop of an ever-evolving digital era, where connectivity and communication continue to redefine the landscape of networking technologies. As we look ahead, several trends and innovations are poised to shape the trajectory of Layer 2 and contribute to a more dynamic and efficient network ecosystem.
One notable aspect is the integration of Layer 2 technologies with emerging paradigms such as Software-Defined Networking (SDN). SDN offers a programmable and centralized approach to network management, allowing for greater flexibility, automation, and adaptability. This synergy between Layer 2 and SDN holds the promise of more agile and responsive networks that can swiftly adapt to the evolving demands of diverse applications and services.
Moreover, the advent of 5G and the Internet of Things (IoT) introduces new dimensions to Layer 2 connectivity. The growing number of connected devices and the need for low-latency communication emphasize the importance of Layer 2 in facilitating seamless and reliable connectivity for a multitude of devices.
My Other Articles
Exploring the World of GameFi and its Impact on the Future of Gaming
Exploring the World of Binance: A Comprehensive Overview
Understanding Layer 1 Blockchain
Stablecoins: Safe Havens in the Crypto Market
Central Bank Digital Currencies