Stray Emissions: Van Eck Phreaking
If you aren’t a medium member, you can read with no paywall via substack
If you’re of the older persuasion you probably remember a time when the world was a much different place. Videos and eventually, DVDs would be the way we consumed media, and while mobile phones have been around for more than a while now, they weren’t as pervasive as they are in today's modern world.
While the methods varied, connectivity was still important. In the days before Slack, Teams, and Facebook, much of this connectivity was provided by hardwired services. For the legal and medical professions, this would mostly mean fax machines and pagers, while the rest of the world would use landline telephones. The usage of these services would often be subject to exploitation and would lead to a whole generation of hackers. However, due to the differences between networked computers and telephone exchanges, we wouldn’t call them hackers like we would today. We’d call them “phreakers”. Spawning a whole subculture of their own, phreakers would use DTMF tones to give them access to the world.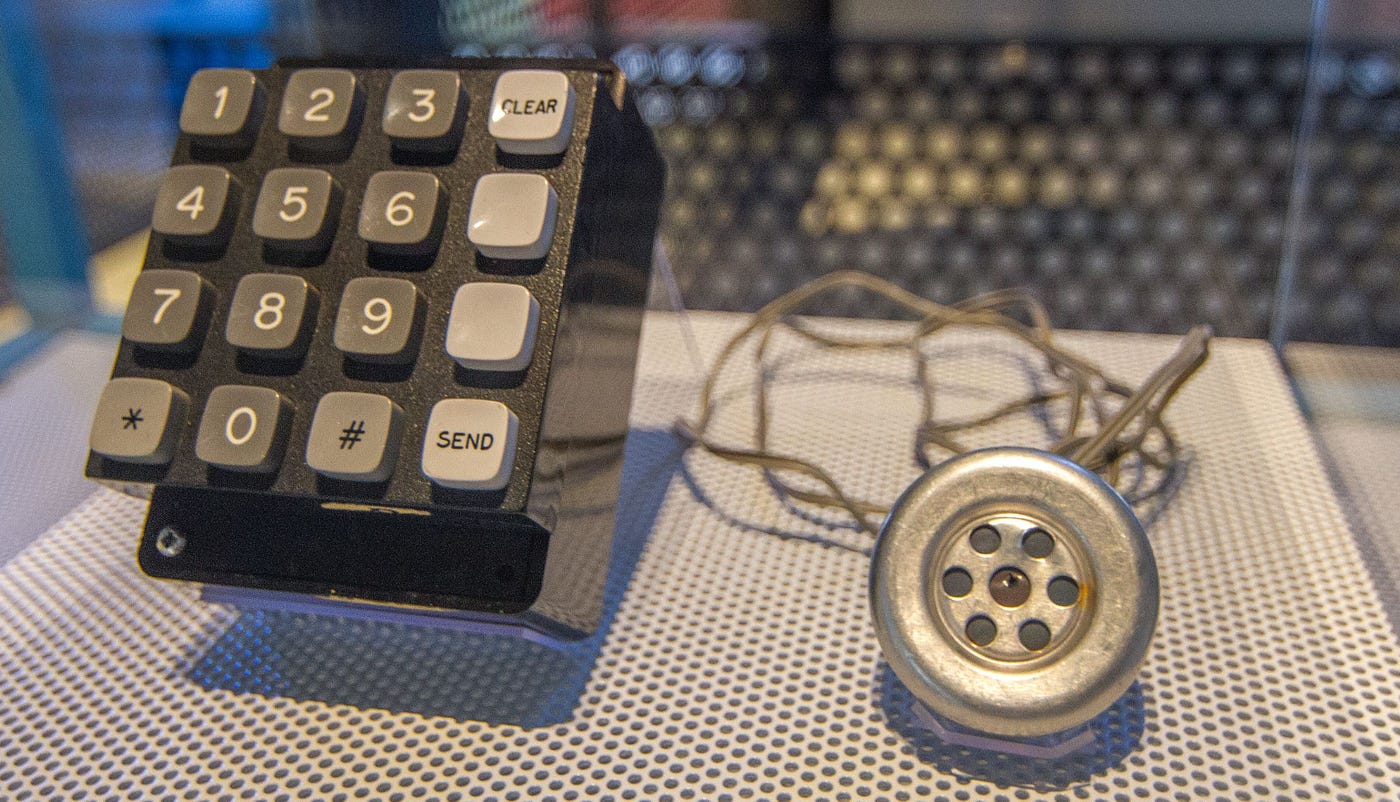
So-called “Blue Boxes” were a big part of the early scene. Source: Wikipedia
In today’s article, we’re going to take a look at a phreaking technique that applies to the modern world. Known as Van Eck Phreaking, it’s an interesting tale that could have been pulled straight from a spy movie. Let’s check it out!
WTF Is Phreaking?
As phone systems moved from the early manual systems to automated services, researchers in the 60s discovered that replicating the 2600mhz tone that helped make the system work would grant access to systems that were usually secured. By carrying out experimentation and gathering data to understand how the system worked, early phreakers would eventually be able to exploit analogue systems in a number of ways.
In fact, one of the hackers we’ve discussed in this blog at length before first came to fame as a phreaker. Kevin Mitnick, known to many in the world of infosec played a large role in understanding how many of these systems were able to be exploited. While he’d later serve time for some of these exploits, his later pursuits through his private security firm would eventually be his legacy, providing consulting advice and expert experience to help secure systems from the inside.
Kevin’s legacy would be one of a phreaker turned white hat. Source: Wikipedia
As technology evolved to include mobile phones and eventually mobile connectivity, the phrase “phreaker” would slowly start to morph. Rather than disappear entirely, it took on an expansion in its meaning. Eventually, “phreakers” would be known for experimenting with, and exploiting RF-based systems rather than just telephone systems, and it’s one of these exploits that’s the focus of today's article.
Van Eck Phreaking
If you’ve followed the Radio Hackers publication you’ve probably already learnt that when something emits a signal, then more often than not, the signal is probably able to be detected by someone else. While we can use obfuscation strategies like encryption and low probability of intercept (LPI) formats, the reality is that in the real world, these strategies more often than not are simply not applied.
Because of this, stray data emissions became a focus quite early. Starting as the sole domain of state-based actors, like many other forms of hacking eventually this research would move into the civilian domain. It might surprise you to learn that much of this work started in the 80s, well before the start of even the dot com bomb.
One of the most interesting papers focusing on this topic at the time was the research done by Wim Van Eck. His work would focus on detecting stray emissions from audio-visual sources, like computer monitors and then using these emissions to replicate the signal and therefore, the data shown on the display.
While state-based actors were aware of and had researched such techniques, at the time, they believed it to be beyond the technical capabilities of civilian actors. Unfortunately, while this was probably true just a decade earlier, Van Eck’s research would destroy this theory outright, as Van Eck was able to intercept and reproduce the signal using nothing more than a normal television set and about $20.00 worth of specialised hardware.
The real status quo change wasn’t in the cheap hardware though. Its real problem was that Van Eck had pulled this off over distances measuring hundreds of meters, causing a real problem for the military. The security dynamic was changing. Because of this, the US government would add EMR research to an existing program called TEMPEST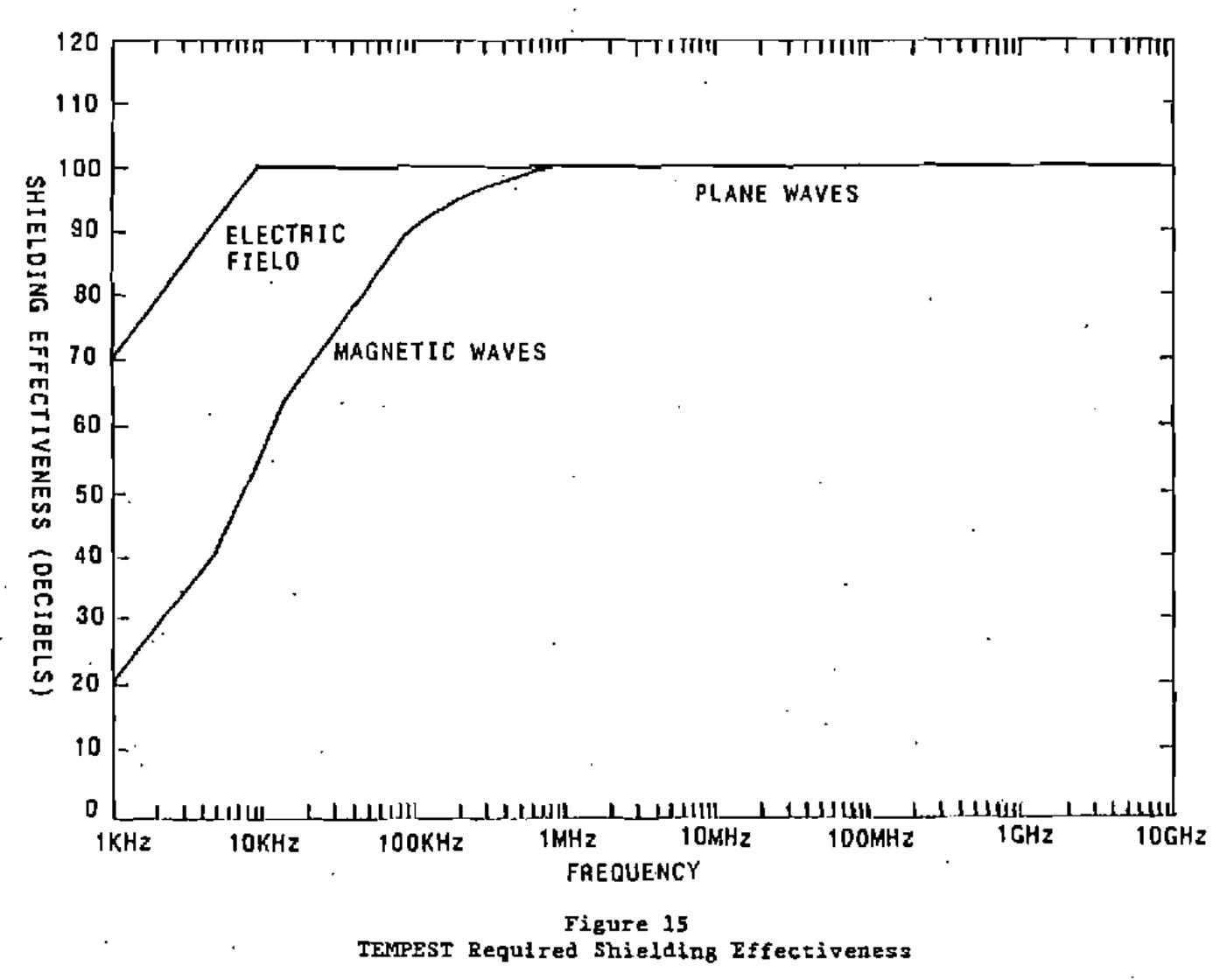
Tempest would urgently identify the need for new shielding standards. Source: Wikipedia.
In the Modern World
TEMPEST wasn’t a new project though. It was simply an add-on to a project that started in the late 1940s. Studying ways to protect their own emissions while attempting to exploit the emissions of others, TEMPEST conducted large-scale research into the issue. Much of this research would be shared with other Western governments, and they’d eventually expand to include standard operating procedures and protocols that were designed to specifically protect against this kind of issue.
A lot of this research became even more relevant in the modern world, as computers would eventually evolve to become an even larger part of our day-to-day working life meaning an active and ongoing defence was needed.
While much of the defence would focus on using shielding and better build quality to help rectify some of the risks, new policies were also put in place to deal with the human factors around securing intelligence as well. We still see the legacy of this in the modern intelligence world, as things like EMR secure rooms (Anechoic Chambers) would evolve directly from data sourced through TEMPEST.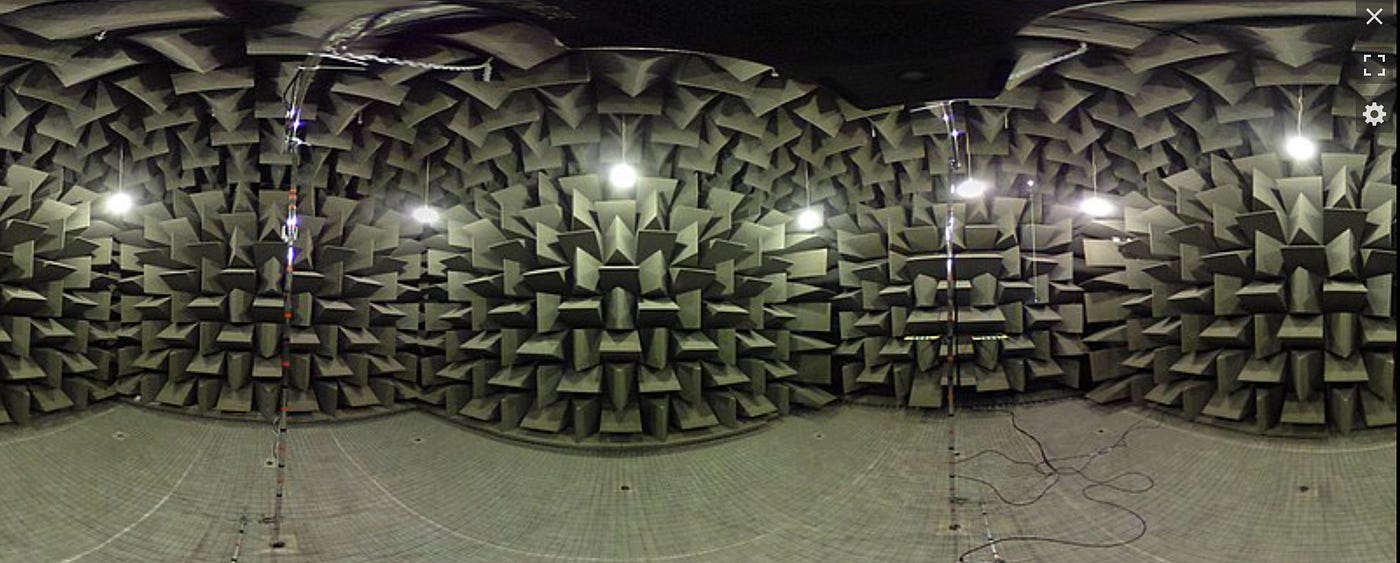
Anechoic chambers would be used to provide secure spaces by preventing all emissions, not just stray ones. Source: Wikipedia
By the time the social media era hit, Hollywood had latched on to the subject and Van Eck style phreaking would enter the public eye via its appearance in a number of popular television series. Both Numb3rs & Spooks would reference it in various ways during episodes, with it being a key part of the plot.
Do I Need To Worry?
While it’s a lofty exploit that can sound concerning, the reality is that unless you are a state-based actor or an individual up to some serious naughty, most people simply won’t have to worry themselves with attack vectors such as these.
Firstly, the evolution of TEMPEST and its data sharing means that while in modern systems, Van Eck can still be possible, generally speaking, modern systems have much better protection against things like stray emissions due to improved build quality. While it hasn’t solved the problem outright, it does make for a more marginal signal. And just like the radio in your car, sometimes marginal signals can be difficult to hear correctly.
Along with improved shielding, we’ve also seen an improvement in how the data was transmitted between devices. The later stages of TEMPEST would entail using filters to remove certain parts of the signal that weren’t needed, making it harder to replicate the signal from that vector as well.
For most people though, the best defence will be that they simply won’t be on the radar for those that are capable of performing such an attack. While corporate and government workers should have proper security policies governing their interactions to minimize attack vectors, the average worker who doesn’t deal with classified information and doesn’t hold a company phone has little to concern themselves with.
We’ll be exploring more of these obscure exploits in further issues of Radio Hackers as we look deeper into how to protect the RF spectrum from airborne (RF-based) attacks.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Rocket Engines
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates