Hidden Trackers: 5 Ways Your Technology Betrays You
Let’s talk about Steganography, Fingerprinting & File Metadata
In recent weeks, we’ve started to explore some of the ways to help reduce your digital footprint. For the most part, this covers invasive things like app privacy as well as the typical overreach that we see applied to some social media platforms.
However, while computers can be great, it can be difficult to understand some of the other ways that you can be tracked via technology.
And, like most historical topics, there are more than a few interesting stories that accompany the history of these subjects.
Let’s take a look!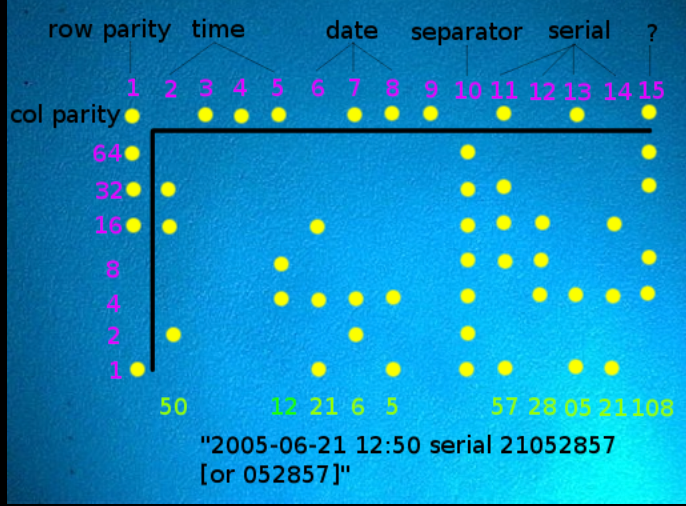 Printer Steganography was originally identified by the EFF back in the early 2000s. Source: Wikipedia.
Printer Steganography was originally identified by the EFF back in the early 2000s. Source: Wikipedia.
Printer Steganography
More commonly referred to as Machine Identification Code or alternately, tracking dots printer steganography has long been used to identify documents, whistleblowers and devices used in criminal activities.
While it varies according to the history of the technology as well as the device used, typically, printer dots are small, embedded pieces of information that are often small enough to be nearly invisible to the naked eye. Acting as a watermark of sorts, the dots contain information that can help identify print jobs. This usually includes a serial number, time and date information and the model of the printer.
Interesting Fact: In 2017, printer steganography discussions went mainstream after allegations were made that an NSA translator involved in a data leak was identified via these methods. When the matter went to court, the role of printer steganography became even more blurred. It’s an interesting read if you have the time.
 Rader would be identified due to metadata police obtained from his correspondence. He will never be released. Source: Wikipedia.
Rader would be identified due to metadata police obtained from his correspondence. He will never be released. Source: Wikipedia.
File Metadata
While we often discuss metadata in the context of mobile phones or devices, the fact is that metadata is present in much of the media we create and use. This can range from simple metadata in a Word document that contains creation date, machine info and usernames, as well as more complex metadata in photos or videos that can contain GPS information and even more detailed device information.
Forensically though, metadata isn’t infallible. It can be examined, modified or even removed entirely. In the early days of social media, metadata was often not removed from pictures when they were uploaded. This led to some interesting OSINT investigations.
Interesting Fact: Denis Rader, who was charged with murder after being identified as the BTK killer has some interesting tales to tell about metadata. He was identified after a floppy disc (remember those?) he sent to police contained a word document that held enough identifiable metadata to single him out and link him to the killings.
 Well known in privacy circles, TOR comes with some caveats. Source: Wikipedia.
Well known in privacy circles, TOR comes with some caveats. Source: Wikipedia.
Browser Fingerprinting
While electronic fingerprinting is a lot more well-known these days, it’s a lot more relevant when you consider its usage with things like Tor. While clear net tracking will often track system time, type and even time zones, the scale of this has increased over the years.
Now, you’ll also have your screen resolution and additional hardware identified, as well as any browser extensions you might have installed. These fingerprinting methods are usually carried out automatically with no user intervention required, and profiling is used to help create a unique, trackable profile of your machine.
The Electronic Frontier Foundation (EFF) has some great resources to help understand this tool. It even includes resources for testing your fingerprint!
Interesting Fact: Tor Browser comes with a default browser resolution that aims to help thwart fingerprinting attempts. Changing the size of the browser also changes your unique footprint, making it easier to identify your machine.
 Originally used in media protection, watermarking popularity took off during the age of the influencer. Source: Wikipedia
Originally used in media protection, watermarking popularity took off during the age of the influencer. Source: Wikipedia
Media Watermarking
Able to be applied to media in audio, photographic and video form, watermarking was originally used as part of a suite of tools designed to aid in copyright protection. As the era of social and electronic media evolved, it would eventually grow in popularity due to its use as a media tracking and referencing tool. Now, it’s everywhere.
The watermarking methods used vary according to the circumstances of use. The most common method would be the graphical watermarks that are applied to things like stock photo images, while more elaborate, software-based watermarks may be used to encode audio clips or digital media.
Interesting Fact: As mapping techniques evolved, Trap Streets or Paper Towns existed for cartographic purposes. These were pieces of false information inserted into existing cartographic features purely for copyright purposes. In 2011, Google would accuse Bing of plaigerising it’s maps, which was revealed when a trap street was included in Bing’s map repository.
 Bluetooth in particular, can be used for device tracking purposes.
Bluetooth in particular, can be used for device tracking purposes.
Device Logging & Telemetry
As electronics evolved, they became smaller, more convenient and more user-friendly. As the internet grew with time, so did the number of ancillary devices that were connected to it.
While this would include stand-alone devices like fridges, washing machines and air conditioners, it would also evolve to include all manner of personal devices including things like smartwatches.
Fully fledged personal devices like these are often computers in their own right, having the ability to log location information, device information and other trackable data. These devices are incredibly popular, but there’s no denying they come with a unique privacy risk that under the right circumstances, can be exploited.
Interesting Fact: Often, these devices can be analysed for data using open-source techniques. Strava, a popular fitness app has been used for intelligence purposes on more than one occasion. It caused controversy in 2018 when open-source analysts identified a number of sensitive military locations in places like Iraq, Afghanistan and Syria. It was Strava’s heat map that would betray these secrets, by revealing patrol information and base locations thanks to their logging features.
A Word About Aggregation
When we talk about privacy-related issues, a big defence that many companies turn to is the concept of data anonymisation for privacy purposes. Essentially, they are saying that applying strategies that remove personal identifying information is enough to protect your data from misuse. While this might have been true, in the age of AI and social media, this simply doesn't stack up.
In the past, analysts would often look at single sources of data, such as a picture or a file. Now, analysts can use raw computing power to analyse entire datasets, including breach data and then apply strategies to de-anonymise some of this data. We’ll look at this more in a later article, but for now, here’s a good example of how this works on a basic level.
A single location snapshot gives a short but not particularly detailed picture of your life at a single point in time. However, thousands of these snapshots allow people and companies the ability to track your life, including where you work, when you work and what you might do in your personal time.
To make it even more interesting though, we can then apply strategies like MAC address tracking to add another layer to this dataset and by doing so, we can now get a picture of electronic devices (and the people who carry them) that you might be associated with. Pretty cool if you’re a nerd, or a company looking to sell data. Not so cool if you like your privacy.
Before We Go.. What About Paranoia
There’s no denying that paranoia or fears about privacy concerns can often become a hot topic of discussion. In fact, in some instances, this is directly used as a tool to downplay the seriousness of claims that contravene the general expectation of privacy. And it’s fair to say that some people hold some unrealistic views about how prolific this data collection might be.
State-backed surveillance programs are a thing, and in countries with human rights issues or authoritarian governments, this is more often than not a legitimate concern.
However, a fundamental concept that is often overlooked is the fact that, like everything in life, data has an inherent value even if we can’t see it. It’s called the data economy, and it’s a growing business year-on-year.
So, does this mean James Bond is spying on you? Probably not, unless you’re an international person of mystery yourself. Does it mean that open-source analysts are wizards who can find out any secret? Sadly, not usually.
The truth is likely to be much more mundane, but despite this, remember that your privacy is still worth protecting. Companies make big money off it.
It’s a lot harder to regain freedom once you’ve lost it.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Space Shuttles
- Shodan: A Map of the Internet
✉️ Want more content like this? Sign up for email updates






























































