Securing The Internet of Things
Smart devices promise great convenience, but at what cost?
There’s been no hiding the fact that there’s a distinct passion with regard to embedded systems in our past. Embedded systems have provided endless learning into cybersecurity, vulnerabilities, and the importance of securing embedded systems. And while we took a browse at the importance of securing embedded systems in earlier articles, what we haven’t looked at much is Internet of Things (IOT) devices and why it’s so important to secure them properly.
We’ll also be looking at some of the risks that occur when this hasn’t happened and look at some of the general privacy risks that can occur during normal operation. Today's article focuses on technology, telemetry, and smart devices phoning home.All manner of devices now come with connectivity. Source: Pexels.com
Badly Secured Devices
“Vulnerable” has become a bit of a catchphrase in recent years. Plenty of analysts will correctly deduce that many of these smart devices can come with some pretty broad security issues. For the average consumer though, this means little, and it’s even worse when you consider that often people receive the same warnings across multiple devices. The phone is vulnerable. Windows is vulnerable. The washing machine will hack your passwords. Trust nothing!
The reality is, that to the average consumer, these warnings tend to mean little unless we security researchers take the time to explain why this is so, and what can be done to rectify it. And, rather than using big words that nobody understands, we need to break them down into chunks that our clients and colleagues can easily understand. This is….no small task for anybody who is trying to figure out exactly how to achieve this.
Privacy Considerations
The first thing to consider is how some of these devices can affect our privacy, and in certain circumstances even change the threat level under which we operate. Badly secured or openly vulnerable devices leave a network open to compromise at the least and large amounts of unrequested traffic as well.
We can and should, secure these devices better however doing so comes with little benefit unless we can impart exactly why it is important to do so.
For Instance. We as security researchers know that a specific device, is going to use a particular format on a particular port to phone home. We can then check and secure this vulnerability to secure the device. We also know that often, password management on embedded devices is absolutely shocking in some cases. Admin/admin for user name and password anybody?
If we are unable to explain exactly why this is bad practice then are we able to expect mitigation strategies to naturally follow? Like anything, having an explanation, justification, and rectification strategy for your issues will go a long way in receiving assistance with rectifying the issue.
The Role Of Researchers
For many researchers, experimenting and playing with cybersecurity and pen testing comes naturally. Tinkerers will always tinker, and as such we end up with the Hacker Community, the contributions of which have provided many essential fixes over the years.
However, when we apply this knowledge to smart devices, we begin to see that a cumulative effort is needed to bring standardization to the forefront. Thus, carrying out pen testing and security assessments on smart devices is an important step toward understanding how we secure devices appropriately. After all, it’s impossible to secure something correctly without having an assessment to help us understand what might be vulnerable.
While this work isn’t as glamorous as traditional pen testing or red teaming scenarios it’s still a vitally important component of keeping smart devices secure. To help sell this point, we’ll reference the superb work done by Twitter user Haxrob in assessing the security status of a pretty common and very cheap, Bluetooth battery unit.
To save you from reading the entire thread, we’ll point out that it didn’t take long to find out that the device was sending all sorts of information back to its home servers. Worse still, the Play Store and Apple Store listed the offending app as not sending private data, a distinction that is misleading at best and outright fraudulent at worst.
The fact is, that private researchers like this have broad experiences to offer with regard to securing and assessing devices such as this, and when we see such work we should support it wherever possible. This could be by something as simple as exposure, or it could mean putting your learning cap on and pen-testing devices of your own choice. The “doing” of something can make for incredibly productive learning in the right circumstances.
Get Out And Do
So if you’ve got an interest in Bug Bounty or have been experimenting with learning to hack or playing with embedded systems the only thing left to do is to encourage you to use your inquisitive mind and get your hands dirty with some of these things.
Whatever shape that looks like is up to you. It could be starting with a security assessment in your home environment, or it could be looking at devices in your possession and wondering if they are worthy of a security assessment. If they are connected to the internet, chances are they probably are worthy.
If you need some final motivation before the end of the article to help convince you of the viability of this kind of thing then we’ll put forward this recent post from social media as supporting evidence.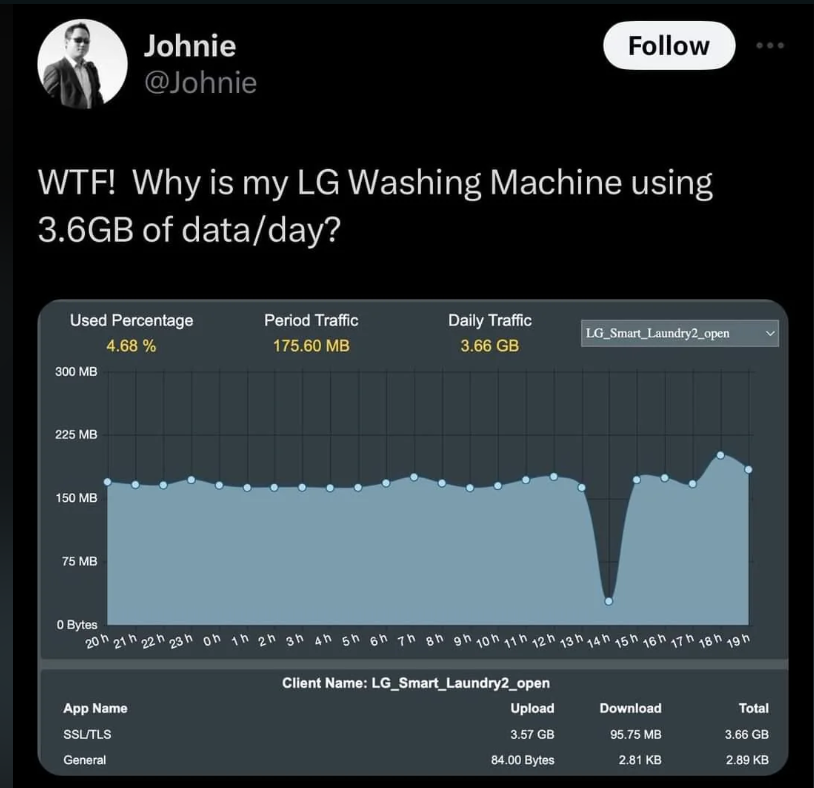 So what is this washing machine doing anyway?. Source: Wikipedia
So what is this washing machine doing anyway?. Source: Wikipedia
Purporting to show an LG washing machine, the screen capture displays a large amount of network traffic travelling through the device. So what exactly is this traffic you might wonder? Is it telemetry data, that's boring and uncompressed? Or is the washer a piece in a zombie botnet, putting in work sending traffic to assist with denial-of-service attacks? Or is it simply badly configured and vulnerable, waiting to be added to a botnet or taken over? The fact is, that regardless of your talent the only way to figure these questions out, is to fire up your computer and start monitoring some traffic and carrying out assessments. If nothing else, we’ll gain some rather functional practical skills by doing so, and we might just collect an answer or two along the way.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Software Defined Radio & Radio Hacking
- OSINT Unleashed: 5 Essential Tools for Cyber Investigators
✉️ Want more content like this? Sign up for email updates here