Difference between public key and private key
Difference between public key and private key
A private key, also known as a secret key, is a variable in cryptography that is used with an algorithm to encrypt and decrypt data. Secret keys should only be shared with the key's generator or parties authorized to decrypt the data.
In this article, we are going to discuss public key, private key and the difference between them. Private keys and public keys both terms are commonly used for encryption and decryption. So, it is very important to know about both keys and the difference between them.
Public key
It is an encryption technique that uses a pair of keys (public and private key) for secure data communication. In the pair of keys, the public key is for encrypting the plain text to convert it into ciphertext, and the private key is used for decrypting the ciphertext to read the message.
The private key is given to the receiver while the public key is provided to the public. Public Key Cryptography is also known as asymmetric cryptography.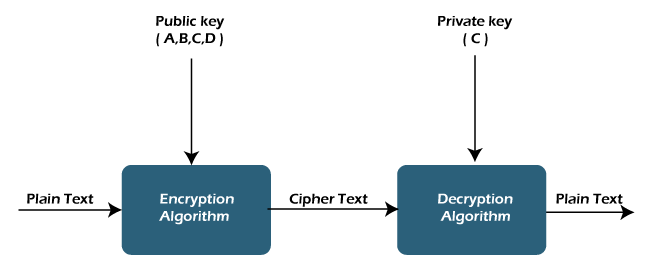 The public key can be shared without compromising the security of the private one. All asymmetric key pairs are unique, so a message encrypted with a public key can only be read by the person who has the corresponding private key. The keys in the pair have much longer than those used in symmetric cryptography. So, it is hard to decipher the private key from its public counterpart. Many of us, heard about RSA, which is the most common algorithm for asymmetric encryption in use today.
The public key can be shared without compromising the security of the private one. All asymmetric key pairs are unique, so a message encrypted with a public key can only be read by the person who has the corresponding private key. The keys in the pair have much longer than those used in symmetric cryptography. So, it is hard to decipher the private key from its public counterpart. Many of us, heard about RSA, which is the most common algorithm for asymmetric encryption in use today.
Public-key encryption is slower than secret-key encryption. In secret key encryption, a single shared key is used to encrypt and decrypt the message, while in public-key encryption, different two keys are used, both related to each other by a complex mathematical process. Therefore, we can say that encryption and decryption take more time in public-key encryption.
Applications of public key
The applications of public key are -
- Public key cryptography can be used to encrypt Emails to keep their content confidential.
- Asymmetric cryptography or public-key cryptography is also used in Secure socket layer (SSL) protocol to make secure connections to websites.
- Public key is also used in Blockchain and cryptography technology. For example, a pair of keys is generated, while setting up a new cryptocurrency wallet.
- It can be used to create a digital signature in the Operating System software such as Ubuntu, Red Hat Linux packages distribution, etc.
Private Key
In private key, the same key (or secret key) is used by both the parties, i.e., the sender and receiver, for Encryption/Decryption technique.
The sender uses the secret key and encryption algorithm for encryption, whereas for decryption, the receiver uses this key and decryption algorithm. In Secret Key Encryption/Decryption technique, the algorithm used for encryption is the inverse of the algorithm used for decryption. It means that if the combination of addition and multiplication is used in the encryption algorithm, then the decryption algorithm will use the combination of subtraction and division.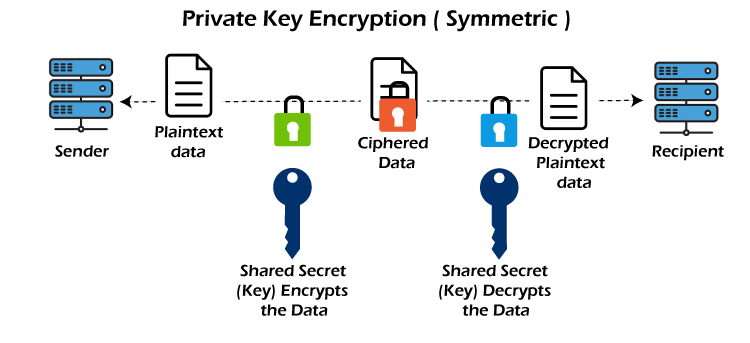 The secret key encryption algorithm is also known as symmetric encryption algorithm because the same secret key is used in bidirectional communication. The mechanism of private key is faster than the mechanism of public-key cryptography. The reason for this is that the size of the key is small.
The secret key encryption algorithm is also known as symmetric encryption algorithm because the same secret key is used in bidirectional communication. The mechanism of private key is faster than the mechanism of public-key cryptography. The reason for this is that the size of the key is small.
Public key v/s Private key
 That's about the description of both public and private keys. Now, let's see the comparison chart between both keys. We are comparing both keys based on some characteristics.
That's about the description of both public and private keys. Now, let's see the comparison chart between both keys. We are comparing both keys based on some characteristics.
On the basis ofPublic keyPrivate keyDefinitionIt is defined as the technique that uses two different keys for encryption and decryption.It is defined as the technique that uses a single shared key (secret key) to encrypt and decrypt the message.Known asIt is also called as Asymmetric key encryption.It is also called as symmetric key encryption. It is because the same secret key is used in bidirectional communication.
Efficiency :It is inefficient as this technique is used only for short messages.It is efficient as this technique is recommended for large amounts of text.
Speed :It is slower as it uses two different keys; both keys are related to each other through the complicated mathematical process.It is faster as it uses a single key for encryption and decryption.
Secret: It is free to use.Apart from the sender and receiver, the private key is kept secret and not public to anyone.
Purpose: The main purpose of the public key algorithm is to share the keys securely.The main purpose of the secret key algorithm is to transmit the bulk data.
Loss of key: There is a less possibility of key loss, as the key held publicly.There is a possibility of losing the key that renders the system void.
What are the benefits and limitations of Public Keys?
Benefits:
Public key cryptography promises a lot of security benefits in an open network like blockchain. The three most important aspects, as well as the benefits of using public-key cryptography as the security method, are; Confidentiality, Integrity, and Authenticity.
1. Confidentiality: Blockchain assures confidentiality of the data that we are sharing by using a pair of keys. The public and private keys that are linked to each other make sure that the data or information that we are sending is kept secret from others. It maintains confidentiality by encrypting the data using a public key and decrypting it on the other end using its corresponding private key.
2. Integrity: By encrypting the data, public-key cryptography also maintains the data’s integrity. The information is only accessible to the sender and the receiver due to end encryption. As a result, one may be confident that the data is complete and that no one has tampered with it in the interim.
3. Authenticity: The user’s authenticity is another crucial component and a big benefit of public-key encryption. Some can’t impersonate themselves because it uses digital signatures in every transaction. As a result, each node on the blockchain network may be certain that the sender is a genuine member of the network. This is how blockchain establishes user trust.
Limitations:
There are a few drawbacks to public-key cryptography, just as there are to everything else.
- Speed:
Many secret-key encryption methods are substantially quicker than any public-key encryption method currently available. To achieve the best of both worlds, public-key cryptography can be combined with secret-key cryptography. To acquire both the security advantages of public-key systems and the speed advantages of secret-key systems, the optimum method for encryption is to combine public- and secret-key systems.
The ability of mathematical techniques to encrypt and decrypt data or messages is restricted to specific data sizes. When there is a big amount of data to encrypt, the algorithm takes a long time.
This slows down the encryption process and necessitates more processing resources.
2. Security:
If someone gains access to the secret private key or exposes it to the network by accident. All of the information encrypted with that private key will fall into the wrong hands. Once the private key is exposed, the data cannot be restored or re-encrypted.
3. IIf a node loses its private key, its data will be stuck indefinitely, and it will no longer be able to make transactions from the same public address. The data encrypted by its private key will be inaccessible to such a node.
What are the benefits and limitations of Private Keys?
Benefits:
- Private keys are much faster and easier to implement. To encrypt or decode a file, the system uses a single, reversible mathematical equation. As a result, symmetric encryption uses fewer computer resources than symmetric encryption.
- Encrypted data can be transferred across a link using private keys, even if there is a chance that the data will be intercepted. The chances of data being decrypted are nil because no key is transmitted with it.
- A private key employs password authentication to verify the receiver’s identity, and communication can only be decrypted by a system that has the secret key.
Limitations:
- To send the key, it uses insecure methods of communication. Allowing third parties access to the key that unlocks the data is dangerous. This method cannot ensure the message’s origin or legitimacy, and it may cause issues if there is a disagreement or uncertainty.
- It is required to generate and manage numerous private keys if a user wants to separate data or cash into groups. Too many keys are inconvenient, and a new shared key with each new party could be dangerous.
- It is not possible to provide digital signatures that cannot be revoked.