The Raspberry Spy: Running Kali on the Zero W
The Pi Zero is perfect for some Portable InfoSec.
Infosec can be a great hobby or part time study field. It’s also pretty awesome as a career. However developing skills safely and legally can be tricky, and off the shelf tools while often effective can be expensive, particularly if you’re just beginning or looking to see if its the field for you.
However the development of single board computers have made it easier for experimentation and development purposes. While they aren’t always the best option they can be a brilliant tool for beginners or developing a configuration that isn’t linked to your primary computer.
The limitation of an SD card operating system over an emmc based system can actually be useful in this situation, allowing a number of configurations to be run quickly and easily, with changing your set up no harder than simply swapping out your SD Card.
The development of the Raspberry Pi specifically has been an interesting journey, with ongoing future planning and a significant increase in specs as each new Pi version is released. While the Pi 1 had limited processing power, no WiFi and just 500mb of RAM, the current Pi 4 runs a 1.5ghz processor with onboard WiFi, Bluetooth and up to 8 gigabytes of RAM. We also see the Pi Zero series with a smaller footprint and less power consumption while still having the onboard WiFi and Bluetooth of its full sized big brother.
Software and the OS
While the original Raspbian software was initially the go to version for the Pi, time has evolved to now give us many useful disc images that can be used according to your topic of interest. With disc images for Software Defined Radio, Pentesting / Infosec and OSINT able to be sourced with just a few easy clicks configuring the Pi to run a distro of your choosing is now painless and easy to set up.
While we don’t recommend using Kali or a similar distro for daily driving purposes it can be useful having a pre configured platform available for use as the generic version of Kali comes with many useful tools for those studying cybersecurity or carrying out OSINT investigations. While spinning up a VM is definitely a good option we tend to like the portability of the Pi as it means we can use it out and about or even fly it on a drone should it be warranted.
Today we’ll focus on installing Kali on the Pi Zero. This is because’ll be using the Zero for future infosec articles focusing on Kismet and a number of the open source based search tools that are included in the Stock Kali configuration. If you don’t currently have a Zero Board and would like to purchase one you can find one on Amazon here
Downloading the Disc Image
The good availability of software we mentioned above means that its now super easy to get our hands on an image suitable for our board. We do however need to take some precautions to ensure we are getting a secure version of the image which we’ll talk you through. First head to the Kali website located here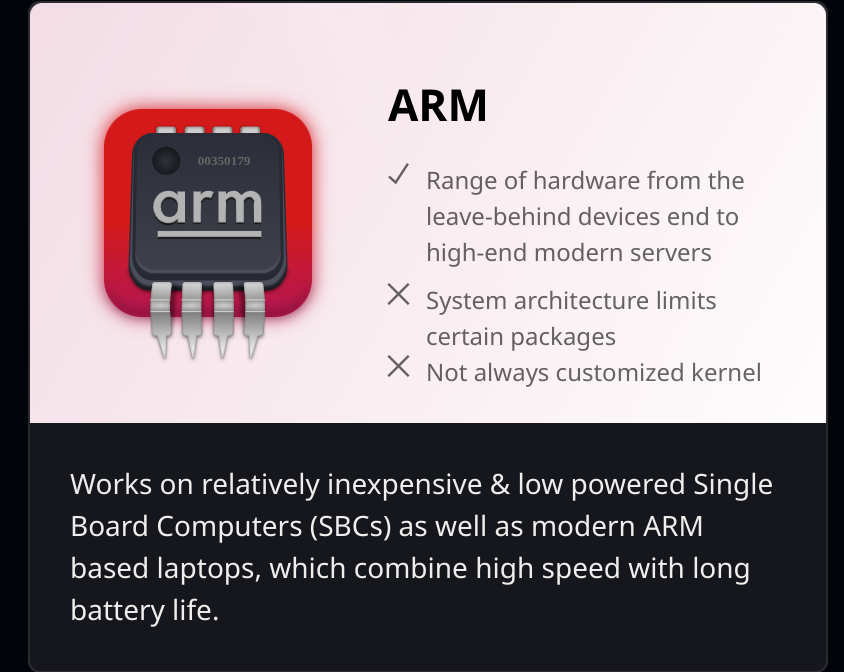 We want the ARM version for Single Board Computers
We want the ARM version for Single Board Computers
We’ll need to select the version for ARM systems focusing on single board computers. We can see our Pi Zero Version easily available.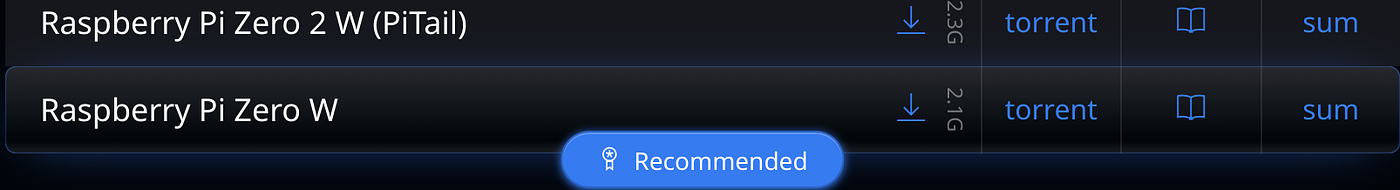
After we’ve downloaded the image we’ll need to check the integrity of the file to ensure its not compromised in anyway or that we haven’t downloaded our version from a bad site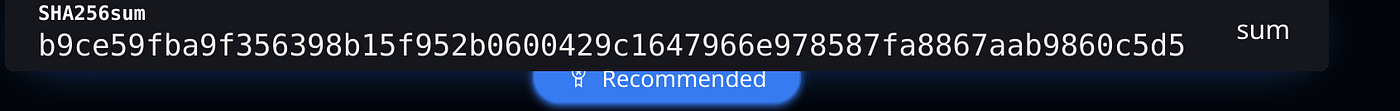 SHA256 SUM for our file download
SHA256 SUM for our file download
We can do this by looking at the checksum in the downloaded file and comparing that with the record that’s stored on the website. While the steps for doing this will vary according to your operating system if you’re already a linux user you can find this easily in the terminal by using the following command.
sha256sum <file_path>
Flashing the Image
Assuming your checksum matches, we can move on with flashing the SD card. We’ll use Balena Etcher to configure ours. Balena Etcher is quick to setup and use.
Balena Etcher is quick to setup and use.
Use etcher to flash your verified Kali Disc Image to your micro SD Card you’re planning to use in the Pi.
If you’re having issues with this part and you’d like to purchase a ready to go card then contact us in the comments and we can arrange one for you.
Booting and Loading
Once Balena finishes flashing your SD card you can now remove it and put it in the Pi so it’s ready to boot. However once you’ve booted it you’ll need to modify some settings to ensure it’s secure. You can modify the config file to automatically detect and login to your WiFi network, or you can use an external monitor with the usual peripherals to configure it offline. We’ll be doing a follow up article soon to show how to properly secure one of these machines after setup. This will include how to login via ssh using a key, which is far more secure than a password. If you’re seeing this screen, you’re seeing your new Kali-PI is configured correctly.
If you’re seeing this screen, you’re seeing your new Kali-PI is configured correctly.
If you’re seeing a screen similar to the one above then congratulations! You’ve taken the first steps towards configuring your Kali-Pi or as we like to call it, the Raspberry Spy.
One you’ve reached this step you can now login and start having a look around at some of the default packages available for use. You’ll see some familiar OSINT based tools in there, like Sherlock, TheHarvester and one of our favorite tools, Kismet Wireless.
In our later articles we’ll show you how to secure the Pi and use some of these tools effectively for Investigative Purposes.
If you’re studying infosec and you’d like access to a large range of free resources that will allow you to learn in a safe environment, then we’d recommend new users take a look at tryhackme.com for a large variety of study material. You can sign up for a tryhackme membership with our link and recieve cash back on a premium membership.
If you’d like to find our latest articles for free then you can find them on publish0x where you’ll be paid in crypto for reading and writing blogs. Join publish0x via our link here
If you’re a telegram user you can receive updates on our own channel here
Lastly if you’d like to make our day you can send us coffee here