Who Are You: Email Aliasing
Reduce your vulnerability to spam by protecting your primary email address.
If you aren’t a medium member, you can read with no paywall via substack
If you’re a long-term reader, you’ll probably recall that we’ve taken a look at the concept of email aliasing in earlier articles. Using tools like temp mail, we’re able to generate email addresses as well as send and receive correspondence via the command line.
While these can be great tools to have for the beginner analyst, it’s more than fair to say that if you aren’t a Linux user or aren’t partial to using the command line, then it’s hard to bring these tools into everyday use.
But what if we could implement these using tools we already have without having to radically modify our workflow, making it easier to protect our primary address? In today’s article, we’ll be taking a walk through some of the options available to help solve this problem quickly and easily.
The Goals
While many people still choose to use either a Desktop or Laptop system as their primary device, for some people mobile devices are where it’s at for accessing the internet. So, any system we consider must provide options for mobile users, meaning that we’ll need to look at options available to both Android and Apple users.
We’ll also need it to be easy to implement and reliable without being overwhelming. And while 3rd party software can be considered as an alternative, the best outcome is probably going to come from using tools from either Apple or Google. This is due to its ease of integration and user-friendly approach. Both companies have gone to great lengths to make their devices more accessible as they’ve matured.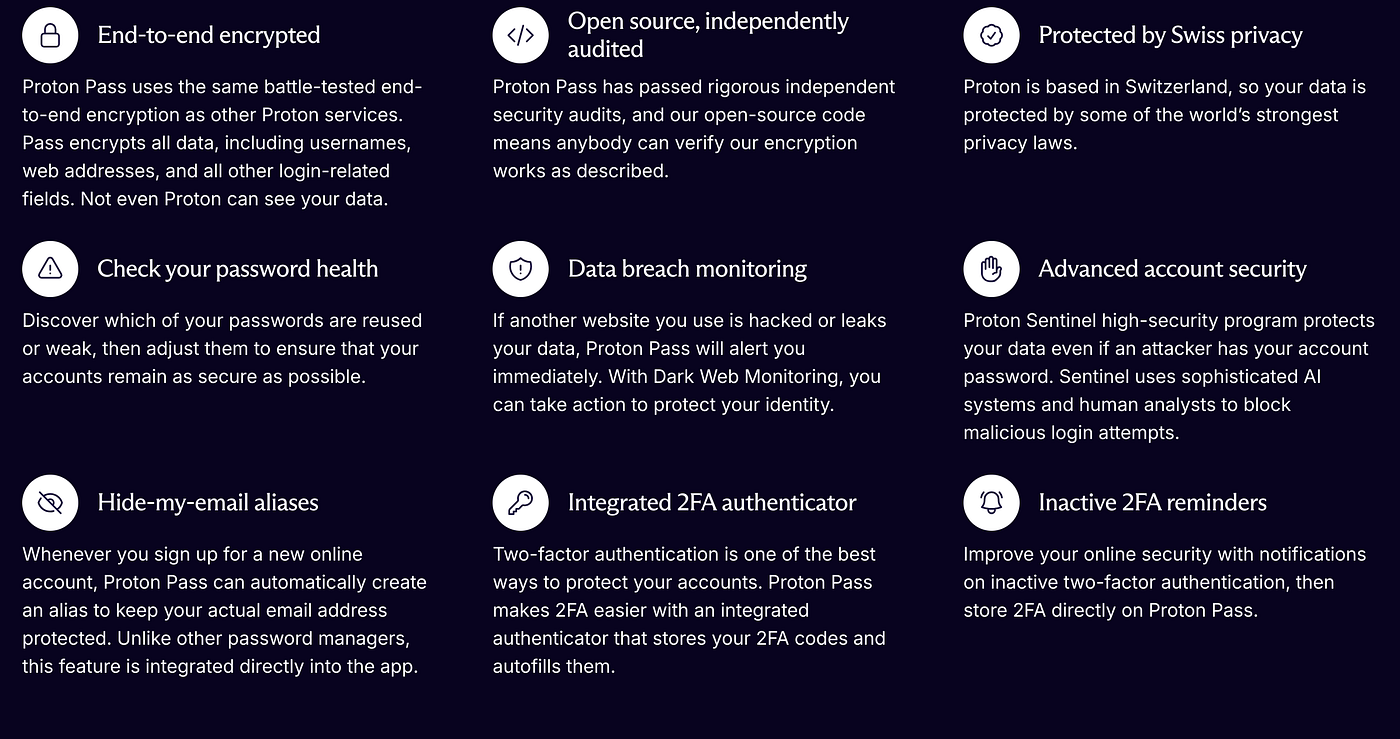
3rd Party Options
For the purposes of this article, we’re considering that most users will opt towards using the default alternatives. If you’d like to stray from this path though, Proton Pass is probably one of the best places to get started.
With both free and paid tiers, Pass allows you to generate alias addresses, apply 2FA strategies to your online accounts and provide strong, unique passwords that you’re able to use.
While the free tier does come with some limitations around the number of available addresses, it can still be a good option for those who might have a more nuanced approach to managing their privacy.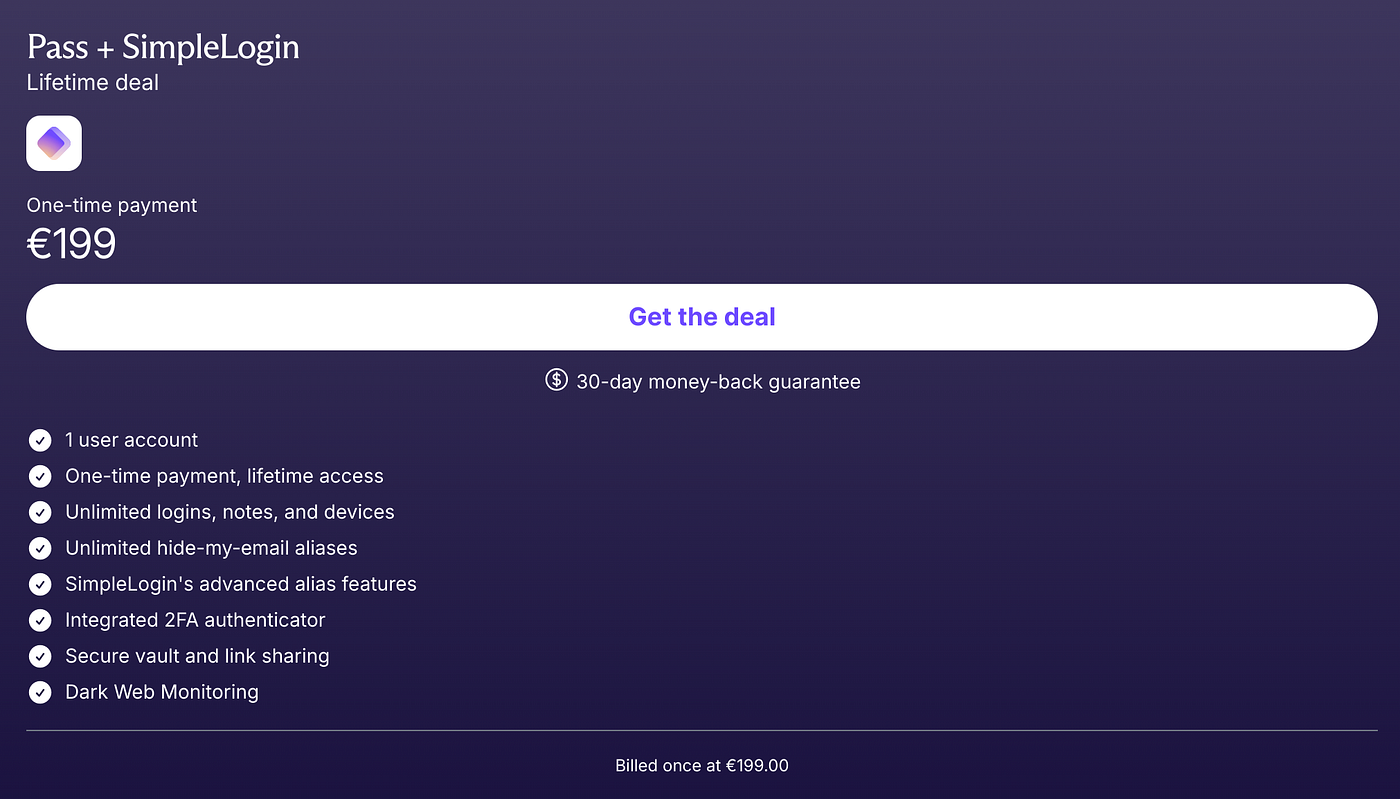 While the product typically relies on an annual or monthly subscription, Proton occasionally has a sale where you can purchase lifetime access for a one-off fee.
While the product typically relies on an annual or monthly subscription, Proton occasionally has a sale where you can purchase lifetime access for a one-off fee.
Default Hardening
It’s not hugely controversial to say that our current security postures tend to look pretty different compared to a few years ago and mobile devices are no different. Regardless of your team, both manufacturers have continued to add features that aim to protect user privacy and harden the device's overall security posture. Considerations around privacy and ease of use have played a large role in making this happen. This includes things like Apple’s Keychain and full disk encryption on Android devices.
What does this mean exactly? It’s pretty simple really. Now, Gmail users can use Google aliasing strategies, while iPhone users can use the Apple processes. While Apple goes to great lengths to ensure their product integrates into the default iPhone configuration, learned experience shows that Gmail users are less aware of their options.
Let's look at how we can make this work with our existing systems.
Gmail Plus Addressing
To make our alias address, we’re going to use a pretty cool feature that’s built directly into Gmail. It’s called plus addressing, and while it can sound complex overall, it’s pretty easy to use.
Effectively, you can add a “+” sign followed by any keyword or string after your Gmail username but before the “@” symbol. For instance, if your email is username@gmail.com, you could create aliases like username+work@gmail.com or username+newsletters@gmail.com.
Emails sent to these aliases will still arrive in your main inbox like any other email would. This technique can be pretty helpful for organizing your emails or for signing up for services where you want to track how your email address is used.
One other thing. Gmail also ignores all dots in the username part of the address, so user.name@gmail.com would also go to username@gmail.com, providing another option for aliasing an address that will go directly to your main account.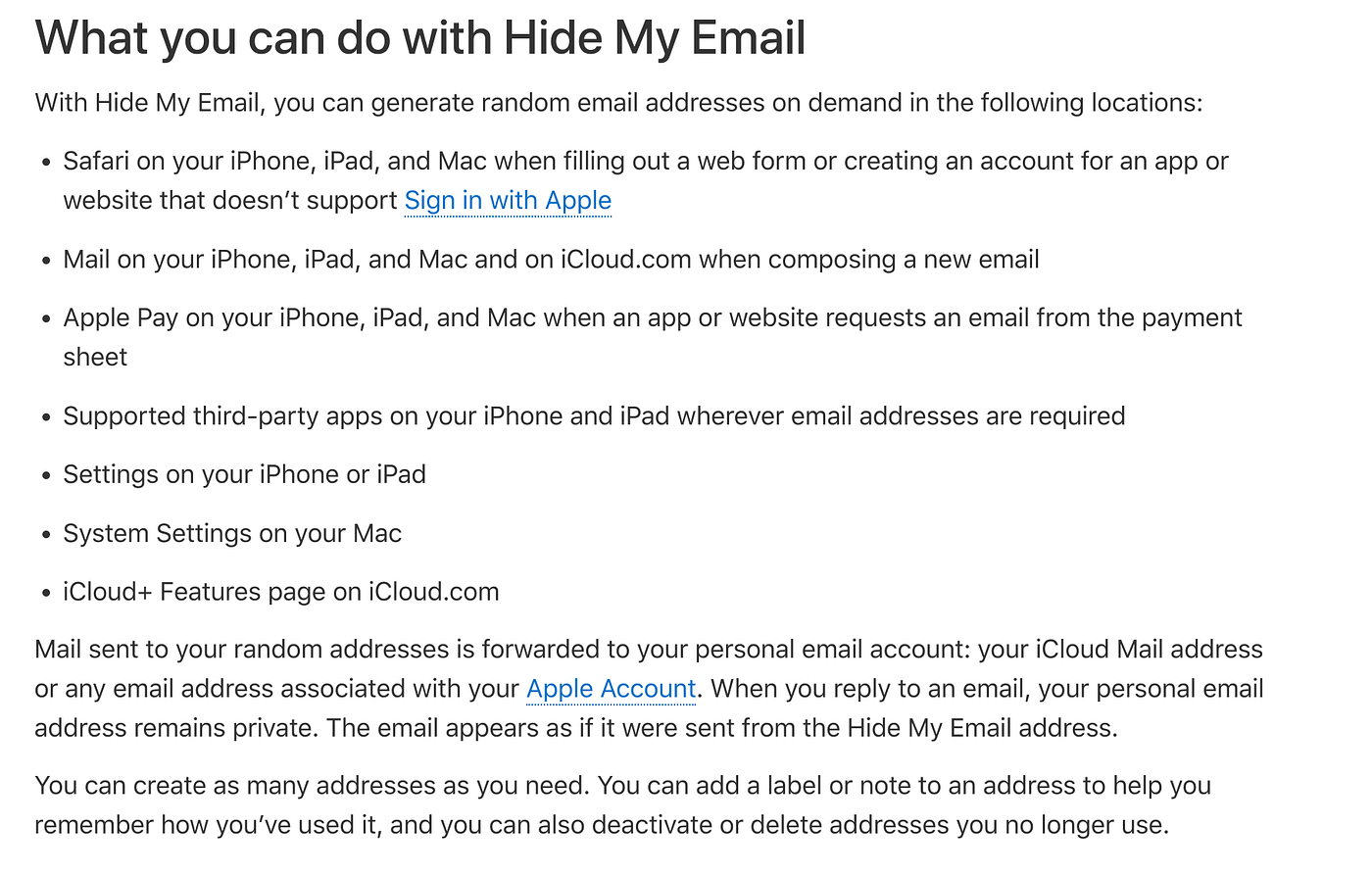
Apple’s Hide My
While Gmail requires you to use plus addressing, Apple has taken away much of the labour behind this process, with their “Hide My” feature integrated directly into iOS software. So, if you’re an iPhone user and you aren’t using this, changing that requires little effort and the best bit is that it integrates with Macbook devices as well. The downside is that to get the full functionality, you’ll need an iCloud + account. Once you’re set up though, you’ll find it as well featured as any of the other paid products. You’ll also be able to share the subscription with other users within your circle.
The configuration will vary slightly according to your system, so to get the best information for your device, follow the official Apple recommendations via this link.
If you need additional information, you might also find the support page to be helpful.
In Closing
It’s easy to look at privacy strategies and think there’s little value in taking steps to manage your online footprint. Some might also argue that there’s little point in doing so given that strategies already exist to deanonymise your data.
The reality though, is that personal information does have a commercial value and can be analysed and onsold to data brokers and other vendors. It’s not just this angle we need to consider though. From a cybersecurity perspective, breach data allows bad actors to up their fraud game by using leaked information for password spraying attacks and social engineering strategies.
Unfortunately, lacklustre responses to cyber incidents over the years have gone on to show us that there’s little incentive for companies to take control of the issue by providing tangible strategies to improve their overall posture. So for now, we get the bare minimum.
This means that if we value privacy, we now have to take matters into our own hands.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Rocket Engines
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates



































































