Hive Ransomware: A Cyber Threat That You Should Be Aware Of
In the ever-evolving landscape of cyber threats, ransomware stands out as one of the most pervasive and damaging forms of malware. Among the myriad strains of ransomware, the Hive ransomware has gained notoriety for its sophisticated tactics and widespread impact on organizations worldwide. In this article, we delve into the intricacies of the Hive ransomware, exploring its origins, mechanisms of action, and the devastating consequences it inflicts upon its victims.
Origins and Evolution
The origins and evolution of the Hive ransomware offer a glimpse into the shadowy underworld of cybercrime. Like a malevolent entity emerging from the depths of the dark web, Hive first surfaced in June 2021, its nefarious capabilities gradually unfolding as it evolved over time. With each iteration, Hive has morphed into a more formidable adversary, honing its tactics and evading detection with increasing sophistication.
The name "Hive" itself conjures imagery of a sinister network, akin to a hive of bees, where infected computers serve as interconnected nodes under the command of cybercriminal overlords. This symbolism reflects the coordinated and decentralized nature of the ransomware operation, where a swarm of compromised systems collaborates to carry out attacks on unsuspecting victims.
As Hive continues to evolve, its impact reverberates across the digital landscape, leaving a trail of destruction in its wake. From small businesses to multinational corporations, no entity is immune to its insidious reach. Understanding the origins and evolution of Hive ransomware is essential in combating this ever-present threat and fortifying our defenses against future incursions into the digital realm.
Mechanisms of Attack
The mechanisms of attack employed by Hive ransomware are as diverse as they are cunning, designed to infiltrate and immobilize the digital assets of its victims with ruthless efficiency. Through a combination of sophisticated tactics and malicious ingenuity, Hive navigates its way into unsuspecting systems, leaving devastation in its wake.
One of Hive's primary tactics involves exploiting vulnerabilities in software systems, capitalizing on weaknesses and loopholes to gain unauthorized access. Whether it's outdated software or unpatched security flaws, no system is immune to Hive's relentless probing for entry points.
In addition to software vulnerabilities, Hive ransomware leverages social engineering techniques, such as phishing emails, to deceive unsuspecting users into unwittingly downloading malicious attachments. Crafted with deceptive precision, these emails masquerade as legitimate correspondence, luring victims into opening attachments or clicking on links that unleash the ransomware onto their systems.
For those who dare to resist, Hive employs brute force attacks, relentlessly hammering away at network defenses until they crumble under the onslaught. With brute force, Hive seeks to exploit weak or default passwords, exploiting human error and lax security protocols to gain unfettered access to sensitive data and systems.
Once inside a victim's system, Hive moves with ruthless precision, swiftly encrypting files using advanced encryption algorithms. These algorithms, often military-grade in nature, render files inaccessible to their rightful owners, effectively holding them hostage until the ransom demands are met.
The speed and efficiency with which Hive executes its attacks leave victims reeling, grappling with the sudden loss of access to critical data and systems. As organizations scramble to contain the damage, Hive's grip tightens, leaving a trail of devastation in its wake. Understanding the multifaceted nature of Hive's attack methods is crucial in fortifying defenses and mitigating the risk of falling prey to this relentless adversary.
Ransom Demand and Payment
Once the insidious grip of Hive ransomware has encrypted the files of its victims, a chilling message emerges: the ransom demand. Like a digital extortionist, Hive promptly displays a ransom note, serving as a grim harbinger of the ordeal that awaits the victim. This note, often striking fear into the hearts of those who encounter it, delivers the grim news that their precious files have been irreversibly encrypted, effectively held hostage by the malicious software.
The ransom note, meticulously crafted by the cybercriminals behind Hive, leaves no room for ambiguity. It succinctly informs the victim of the dire situation at hand, detailing the encryption of their files and providing explicit instructions on how to navigate the treacherous path towards potential salvation. These instructions typically include the steps necessary to make payment in exchange for the elusive decryption key, the sole means of liberating their files from Hive's relentless grasp.
Payment, the currency of desperation in the world of ransomware, is demanded in cryptocurrency, often the likes of Bitcoin or Ethereum. This choice of currency serves a dual purpose for the perpetrators: it ensures a degree of anonymity, shielding their identities from law enforcement scrutiny, while also providing a convenient and untraceable means of transacting across borders. For victims thrust into the heart of this digital nightmare, the prospect of navigating the complexities of cryptocurrency transactions adds an additional layer of confusion and anxiety to an already fraught situation.
Time is of the essence in the twisted world of Hive ransomware, and victims are often presented with a deadline by which to meet the ransom demands. Failure to comply with these demands carries dire consequences, with the threat of permanent data loss looming ominously overhead. The specter of irrevocable destruction serves as a potent motivator, compelling victims to weigh the risks and make the gut-wrenching decision to either capitulate to the demands of their digital captors or face the unthinkable loss of their invaluable data.
In the harrowing realm of Hive ransomware, the ransom demand is the culmination of a meticulously orchestrated campaign of digital extortion. It represents the final, desperate plea for salvation from victims ensnared in the clutches of this malicious software. As organizations and individuals grapple with the devastating fallout of ransomware attacks, the ransom demand serves as a sobering reminder of the high stakes involved in confronting the ever-present threat of cybercrime.
Global Impact
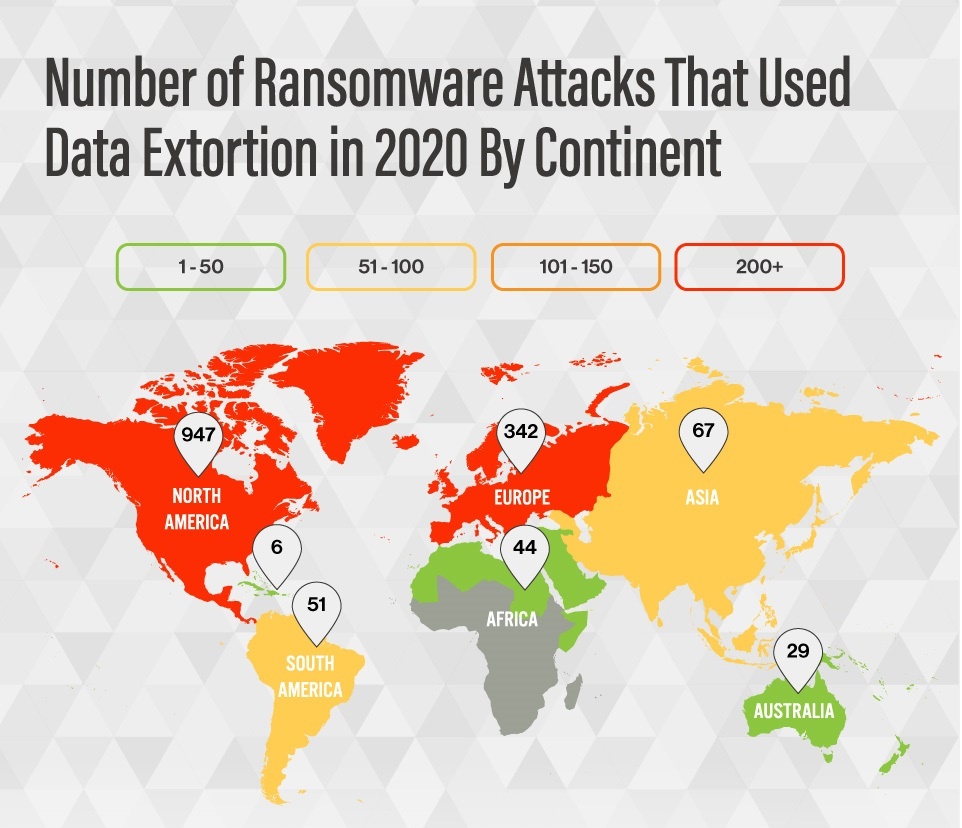
The pervasive reach of Hive ransomware transcends geographical boundaries, leaving a trail of devastation that reverberates across the global landscape. From bustling metropolises to remote corners of the world, no sector remains untouched by the indiscriminate wrath of this malicious software.
The impact of Hive ransomware extends far beyond the confines of individual organizations, casting a dark shadow over entire sectors vital to the functioning of modern society.
Healthcare, the bastion of wellness and healing, finds itself under siege as hospitals and
medical facilities fall victim to Hive's insidious attacks. In the midst of the COVID-19 pandemic, these assaults on healthcare infrastructure strike a particularly poignant chord, exacerbating an already dire situation by compromising patient care and diverting precious resources away from the frontline battle against the virus.
The financial sector, a cornerstone of economic stability, also bears the brunt of Hive's onslaught, as banks and financial institutions grapple with the fallout of ransomware attacks.
The disruption of financial services not only inflicts immediate financial losses but also undermines consumer confidence and erodes trust in the integrity of the financial system.
Government entities, entrusted with safeguarding the welfare of their citizens, are not immune to the reach of Hive ransomware. From local municipalities to federal agencies, the disruption of government operations poses a threat to public safety and national security, casting doubt on the ability of governments to fulfill their fundamental duties in the face of cyber threats.
Critical infrastructure, the backbone of modern civilization, stands vulnerable to the whims of Hive ransomware. Power grids, water treatment facilities, transportation networks—these essential systems are the lifeblood of society, yet they are increasingly susceptible to cyber attacks that have the potential to bring entire nations to their knees.
The global impact of Hive ransomware is not confined to a single country or region but spans across continents, affecting institutions in over 80 countries. The resulting financial losses and operational disruptions are staggering, with billions of dollars lost and countless hours of productivity squandered in the wake of these attacks.
As the world grapples with the ever-present threat of ransomware, it is imperative that governments, organizations, and individuals come together in a united front against this insidious scourge. Only through collaboration, vigilance, and proactive measures can we hope to mitigate the global impact of Hive ransomware and safeguard the digital infrastructure upon which our interconnected world relies.
Government Response and Law Enforcement Efforts
In the face of the escalating menace posed by Hive ransomware and its ilk, governments and law enforcement agencies have mounted a concerted response to combat cybercrime on a global scale. Recognizing the urgent need to confront this pervasive threat, authorities have intensified their efforts to identify, apprehend, and dismantle the criminal networks responsible for perpetrating ransomware attacks.
The U.S. Department of State's recent announcement of a $10 MILLION-DOLLAR reward for information leading to the apprehension of individuals involved in Hive ransomware activities underscores the gravity of the situation and the government's unwavering commitment to holding cybercriminals accountable for their actions. This substantial incentive serves as a powerful motivator for individuals with knowledge of Hive's operations to come forward and assist law enforcement in their efforts to disrupt and dismantle the ransomware infrastructure.
In addition to offering monetary rewards, governments have engaged in coordinated law enforcement operations aimed at disrupting ransomware networks and apprehending key perpetrators. These operations, conducted in collaboration with international partners, leverage sophisticated investigative techniques and intelligence-sharing mechanisms to target the infrastructure and individuals responsible for orchestrating ransomware attacks.
Through a combination of legal measures, technological capabilities, and international cooperation, law enforcement agencies have made significant strides in combating the scourge of ransomware. From seizing servers and infrastructure used by ransomware operators to making high-profile arrests and prosecutions, these efforts send a clear message that cybercriminals will be pursued relentlessly and brought to justice for their crimes.
However, the fight against ransomware is an ongoing battle that requires continued vigilance and collaboration among governments, law enforcement agencies, the private sector, and cybersecurity experts. As ransomware attacks continue to evolve in sophistication and scale, it is imperative that authorities remain proactive in adapting their strategies and capabilities to effectively combat this ever-evolving threat.
By bolstering cybersecurity defenses, enhancing information sharing and coordination, and holding cybercriminals accountable for their actions, governments and law enforcement agencies can mitigate the impact of ransomware and safeguard the digital infrastructure upon which our society depends. Together, we can turn the tide against Hive ransomware and ensure a safer, more secure cyberspace for all.
Mitigation Strategies
Mitigating the threat posed by Hive ransomware demands a comprehensive strategy that addresses both technical vulnerabilities and human factors. Organizations must adopt a multifaceted approach, incorporating proactive measures to fortify their defenses and minimize the risk of falling victim to ransomware attacks.
A crucial aspect of mitigation involves maintaining up-to-date software and security patches. By regularly updating systems and applications, organizations can address known vulnerabilities that cybercriminals often exploit to infiltrate networks and deploy ransomware. This proactive approach reduces the attack surface and strengthens the overall resilience of the organization's digital infrastructure against emerging threats.
Robust email security protocols play a pivotal role in thwarting phishing attacks, one of the primary vectors through which Hive ransomware gains entry into organizations. Implementing advanced email filtering mechanisms, spam detection algorithms, and sender authentication protocols can help identify and block malicious emails before they reach users' inboxes.
Additionally, educating employees about the telltale signs of phishing attempts and providing guidance on how to respond can empower them to exercise caution and vigilance when interacting with email communications.
Cybersecurity awareness training is another essential component of mitigation efforts. By equipping employees with the knowledge and skills necessary to recognize and respond to potential threats, organizations can significantly reduce the likelihood of successful ransomware attacks. Training sessions should cover topics such as identifying phishing emails, practicing good password hygiene, and exercising caution when downloading or opening attachments from unknown sources. Additionally, conducting regular simulated phishing exercises can help reinforce awareness and ensure that employees remain vigilant in their cybersecurity practices.
Implementing a robust incident response plan is essential for minimizing the impact of a ransomware attack in the event that preventive measures fail. Organizations should develop detailed procedures for detecting, containing, and recovering from ransomware incidents, including protocols for isolating infected systems, restoring data from backups, and communicating with stakeholders. Regularly testing and updating the incident response plan ensures that the organization is well-prepared to respond effectively to ransomware attacks and mitigate their impact on operations.
In essence, mitigating the threat of Hive ransomware requires a proactive and holistic approach that addresses technical vulnerabilities, strengthens email security defenses, raises employee awareness, and establishes robust incident response capabilities. By implementing these mitigation strategies, organizations can reduce their susceptibility to ransomware attacks and minimize the potential damage inflicted by cybercriminals.
Conclusion
The Hive ransomware represents a formidable challenge to cybersecurity professionals and organizations alike, posing a significant risk to data integrity, financial stability, and operational continuity. By understanding the mechanisms of attack employed by ransomware strains like Hive and implementing proactive mitigation strategies, organizations can better protect themselves against this ever-evolving threat. Collaboration between government agencies, law enforcement, and the private sector is essential in the ongoing fight against ransomware, ensuring a safer and more secure digital environment for all.














































![[LIVE] Engage2Earn: McEwen boost for Rob Mitchell](https://cdn.bulbapp.io/frontend/images/c798d46f-d3b8-4a66-bf48-7e1ef50b4338/1)




