Historical Hacks: Heartbleed 2014
The internet in its modern form, requires heavy encryption to enable it to function in the way in which we’ve come to expect. Banking, shopping and messaging all use various levels of encryption to protect transactions and user data.
To make this happen easily, we rely on software to implement these different forms of encryption and for the most part, this simply runs in the background allowing us to go about our normal lives. As you might imagine though, if this encryption was to be exploited, we’d be in for a pretty rough time.
Today's historical hack explores that exact scenario. The 2014 Heartbleed bug would exploit the OpenSSL library to great effect.
The Background
With https being the normal status quo, it’s almost hard to believe that there was a time where this wasn’t the case. While there were still cyber threats present, it was a different time regarding threat actors, profiles and attack techniques.
Over time, we’d gradually see better security and encryption being implemented. On the software side, encryption libraries played a key part in making that happen. Able to be easily implemented, it provided a way for developers to easily code secure apps and software.
Like most software packages and libraries, some of this code would be vulnerable and it was these vulnerabilities that Heartbleed looked to exploit.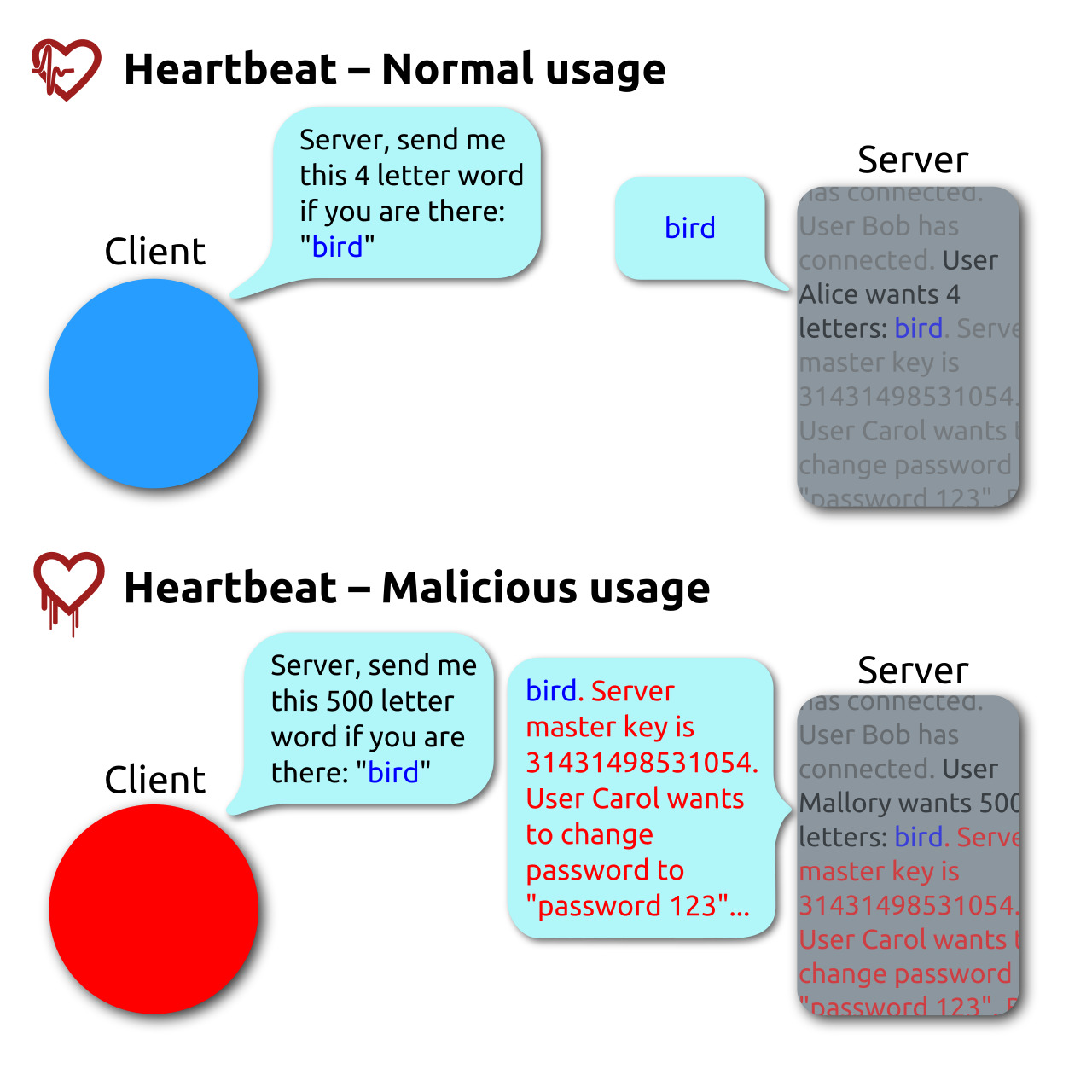
The Hack
While most articles that we’ve written up have focused on a single event, this vulnerability would be different for quite a few reasons.
Firstly, it’s important to clarify that Heartbleed was most certainly not a one-off incident or event. It was the infection of thousands of machines worldwide over a sustained and significant timeframe.
It was that timeframe that would make Heartbleed such a controversial attack. As investigators reviewed logs and dealt with the aftermath of exploited machines, it was revealed that Heartbleed had first been found in the wild in 2012, a full 2 years earlier.
At its core though, the attack was simple as it was ingenious. Given that the OpenSSL library used a “heartbeat” to ensure that a connection remained valid, no validation checking on the input meant that a simple buffer over-read would allow the hackers to exfiltrate data from the machine.
While the vulnerability was patched on the same day it was released, the damage had already been done.
The Discovery
In a nod to proactive security programs around the world, Heartbleed was originally discovered by Google employees who were doing a routine audit of the library.
They were auditing the Heartbeat process itself and noticed that the previously mentioned lack of validation on inputs would allow for excess information to be leaked. The total amount of data able to be taken was relatively small (64kb), but this would be enough to breach passwords and other sensitive information.
A second company, Codenomican, would also be involved in the disclosure, having also found evidence of the bug at around the same time that the Google team was doing its own research.
The breach would be privately disclosed to the OpenSSL team on the 1st of April, 2014. Ultimately, it would be a researcher at Synopsis Software who would name the Heartbleed bug and create the bleeding heart logo that would become the visual trademark of the attack.
The Lessons
OpenSSL worked quickly to mitigate the effects of the vulnerability, getting a patch issued within a few days of its discovery. However, Heartbleed would shine light on a problem that still exists today, namely, the fundamental lack of urgency around patching vulnerable code.
This was amplified by the fact that around the time of exploitation nearly a full 20% of the internet’s infrastructure was running on machines that were considered vulnerable to heartbleed attacks. While this was a staggeringly high number of machines, the frustrating problem was that over three years later in 2017, over 180,000 machines were still running unpatched on the internet. The times might change, but the problems don't.
There’s More Though
In the aftermath, there were some interesting claims made regarding knowledge of the vulnerability. It would be Bloomberg News that would ask questions of the US’s National Security Agency, which would focus on their knowledge of the vulnerability amid persistent rumours that they knew yet chose to cover it up for their own purposes.
These claims gained enough traction in the media that eventually, the United States Government would be forced to comment on the issue. This would come in the form of a public statement that would focus on clarifying their position on Zero-day vulnerabilities.
Researchers would eventually point out that failing to secure software vulnerabilities for the purposes of surveillance would be bad policy that would come with its own long-term cost.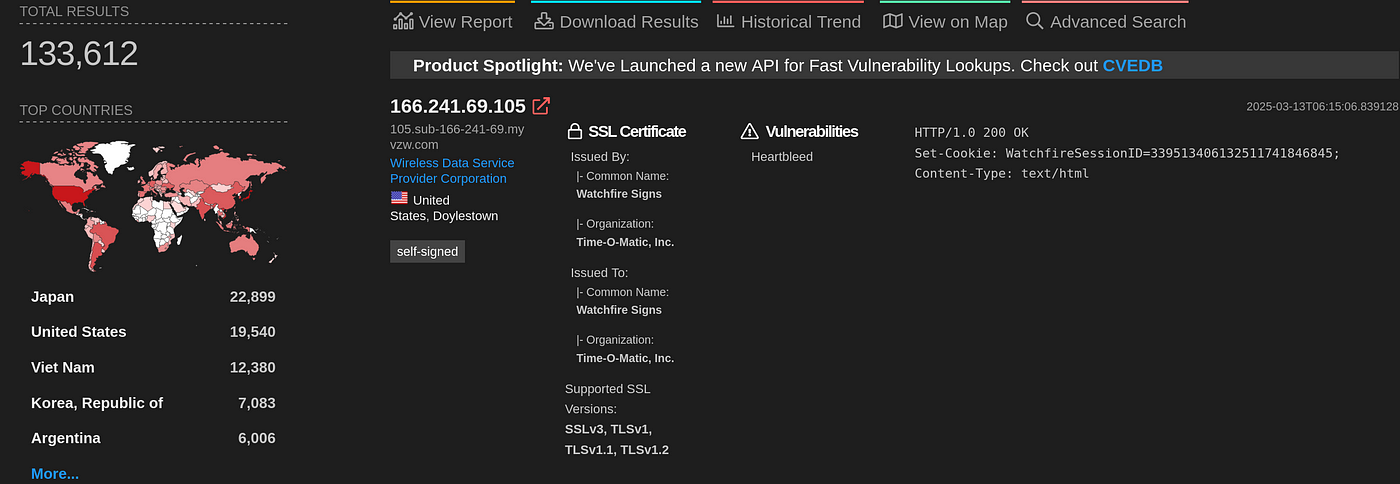
The government's usage of Zero-day exploits continues to this day, and a quick look at Shodan still shows plenty of machines running unpatched software.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Space Shuttles
- Shodan: A Map of the Internet
✉️ Want more content like this? Sign up for email updates


























































