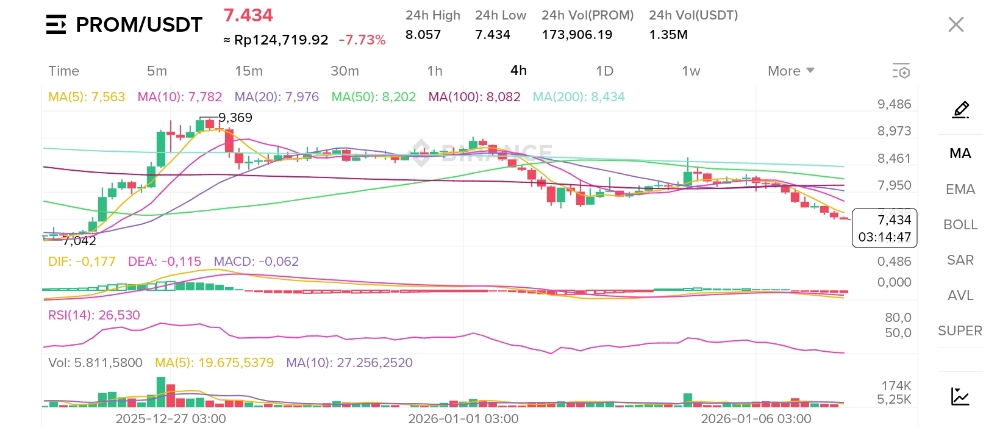
AI attacks🤖
Artificial intelligence (AI) is undoubtedly changing the world as we know it. However, although this developing technology has many benefits, artificial intelligence also brings the possibility of cyber attacks. Bad actors can use AI to increase the effectiveness of existing threats and create new attack vectors. To stay one step ahead, businesses need to consider how to protect their systems against various AI attacks.
What is an artificial intelligence attack?
Bad actors can manipulate an AI system deployed by the organization to serve a malicious purpose. This attack occurs when a bad actor finds limitations in a machine learning (ML) model and exploits them. Threat actors can also use AI to direct offensive attack technologies. They use AI to automatically generate higher volumes of attacks or exploit vulnerabilities themselves, making it harder for organizations to protect themselves. Shawn Henry, chief security officer at an American cybersecurity company, explained that cybercriminals can use artificial intelligence to penetrate cybersecurity defenses, spread misinformation, or infiltrate corporate networks.
According to the expert, the US government relies on artificial intelligence more than ever and uses it as a workforce in various institutions. 27 departments of the US federal government use AI-powered systems In Texas, more than a third of state agencies have delegated basic tasks to AI, including answering people's questions about unemployment benefits. Ohio, Utah and other states are also using AI technology. As artificial intelligence is favored in many areas of government and public services, experts fear that systems may fall victim to loss of control over the technology or privacy breaches. In October, FBI director Chris Wray warned that artificial intelligence was in danger of taking low-level cybercriminals to the next level.
rapid injection
Evade attacks
Training data poisoning (AI poisoning attacks)
Armed models Data privacy attacks
Model denial of service (Sponge attacks)
model theft
A malicious actor accomplishes this attack by strategically inserting prompts into a large language model (LLM) that leverages prompt-based learning. They use these strategic prompts to make the model perform malicious actions. Evade attacks Evasion attacks fool ML models by changing the input to the system. Rather than interfering with the AI, these attacks interfere with incoming data to intentionally cause a system error or evade defensive measures. For example, changing the appearance of a stop sign could theoretically persuade a self-driving car's AI algorithm to ignore the sign or read it as something else (a turn sign, etc.). Training data poisoning (AI poisoning attacks) This type of attack manipulates the training set used by the AI model to produce false outputs, such as biases or misinformation. A poisoning attack often targets AI models that leverage user data as part of their training sets.