Radio Hackers: BlueBorne
If you aren’t a medium member, you can read with no paywall via substack
One of the fun things about dealing with RF-based protocols is the amount of research that can be carried out on various types of transmission modes. And while traditional cybersecurity usually keeps us confined within a localized network, RF-based systems can send data over distance meaning that for SIGINT and research purposes, there’s usually plenty to keep people amused. For black hats and state-based hackers though, this over-the-air transmission presents a unique exploitation opportunity.
In today’s article, we’ll be looking at the Bluetooth stack and exploring a noteworthy series of exploits that came to life in the late 2010s. While it was by no means the first Bluetooth exploit, it was one of the more notable ones.
The Background
Becoming popular in the mid-2000s, Bluetooth was the de facto standard for headsets, headphones and other multimedia devices. Originally used with mobile phones, it was so successful that it would eventually move into different fields being installed in all sorts of devices ranging from door locks and smart systems right through to solar regulators and other stand-alone systems.
Due to the nature of its design, Bluetooth was able to provide a stable, spread spectrum connection and provide acceptably good performance in high-traffic areas and it was this stability along with its ease of implementation that led to it becoming so prevalent in our day-to-day lives.
Like many systems though, the security standards would often be quite varied, due to firmware and device limitations. While some accessories provided a good default security configuration, many other systems would be lacking and it was these more vulnerable devices that the Blueborne exploits were looking for.
The Exploits
Blueborne would be unique in the world of cyber exploits due to the fact it wasn’t just one exploit, but rather a group of exploits that would go on to affect a large array of devices of different types, specs and operating systems. More importantly, the exploit was known to affect both major phone manufacturers AND both Linux and Windows meaning large parts of the consumer markets would end up being affected.
After careful analysis, 8 separate vulnerabilities were identified and deemed to be part of the overall Blueborne threat. Each vulnerability would also be given its own CVE.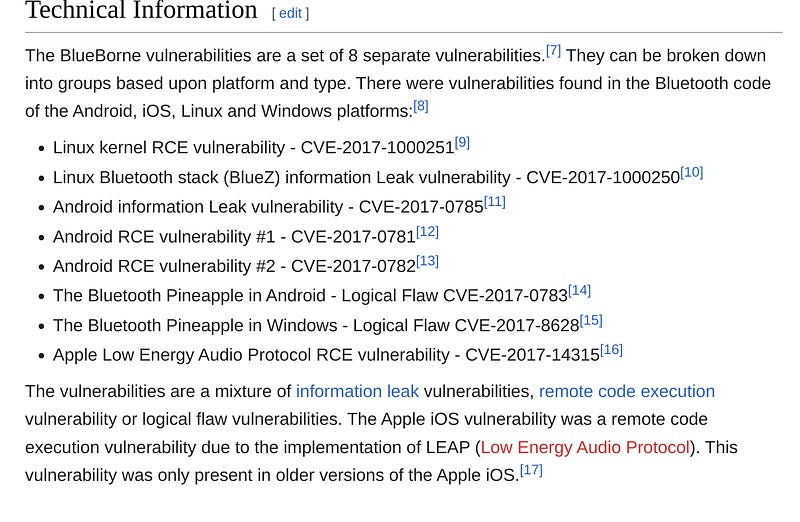
With the initial threat being identified by private research agency Armis, looking at the scope of the vulnerabilities proved to be vast as it was suggested that nearly every Bluetooth device manufactured could be vulnerable. Eventually, billions of devices were deemed to be at risk, and while manufacturers and security providers would eventually push updates to help patch these vulnerabilities, some cheaper or unsupported devices would simply be left as they were. 
Larger manufacturers and notable tech brands would simply bypass some of these issues by providing their own rectification strategies to help keep consumers safe. Google, for instance, would go on to provide a range of free tools and resources to identify and patch blue-borne vulnerabilities through the use of its Blueborne scanner. Interestingly enough the provider of this scanner would later be identified as Armis, the cybersecurity agency responsible for first shining light on the issues encountered by Blueborne.
The Fallout
As you’d expect, an exploit affecting billions of devices the world over would cause some controversy as people wondered exactly what in their world would end up being affected by the exploit. While this was a perfectly natural response in the aftermath of a problem, Blueborne would also go on to spark some rather interesting discussions in the tech world around a problem that remains both relevant and prevalent even today.
While the early days of the internet would use wireless methods like RF and satellite to establish local networks and the internet at large, these early systems would take time to evolve and develop and due to data storage methods at the time, often updates would be done using formats that were more secure. This meant that flash drives, DVDs and floppy disks were all part of this process.
However as technology evolved we’d eventually see “smart” or IOT devices grow in popularity and as part of this, the over-the-air method of pushing software updates and sending telemetry would also grow. This meant that the radio spectrum grew in both popularity and value as demand and usage would also increase.
It was this shift that would end up being responsible for sparking many discussions about how exactly we approach things like cybersecurity in embedded and OTA systems like vehicles, remote systems and other designs that would incorporate transmitting/receiving functions into their general design.
The Flipper Zero
It’s fair to say that while these discussions are occurring more there’s still a long way to go in dealing with this issue into the future. There are also ethical questions to ask around concepts such as this too. For instance, if your vehicle receives OTA updates, does this open up your vehicle problems should you void your manufacturer's warranty? This is just one such thing to consider but the reality is we could apply the same theory to many smart devices, opening up questions around intellectual property and consumer rights. 
It also might surprise you to see an innocuous hacking tool like the Flipper receive a mention in such an article but it deserves one, if for no other reason than it sparks discussion around the security of IOT devices and other lessor known protocols that are still widely used.
And while in some places it’s attracted a fair amount of controversy for being a “hacking tool” what it’s also done is spark new excitement around the spectrum and transmitting protocols in general, and encouraged more people to explore some of this for educational purposes.
While bad actors will always find a way, the fact is that tools like the flipper can be great educational tools in a controlled environment, and the extension of this is that we get a deeper understanding of some of the familiar protocols that we see and use everyday.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Rocket Engines
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates





































