Lights On, Hazards Off: Safely Navigating The Darkweb
It’s time to strip away the aura and look at Darkweb navigation for newbies.
This tutorial is provided for educational purposes only. Please remember that Darkweb research may be restricted in your location. Readers are encouraged to adhere to the laws governing their jurisdiction and behave ethically while conducting dark web research.
In our series on the Dark Web, we’ve looked at some of the history from the early days as well as some of the reasons that it came into being. And while it hosts a range of legitimate content, it also harbours a wide range of illicit activities.
For researchers though, the Dark Web provides a treasure trove of information that’s open to careful analysis. Through this, we can deepen our understanding of how we can protect the clear web as well as explore and monitor some of the more malicious activities that are present as well.
While private researchers will have to work within limitations to ensure they remain legal, you’ll find that for government investigators, this Dark Web work is an essential part of nation-state intelligence investigations.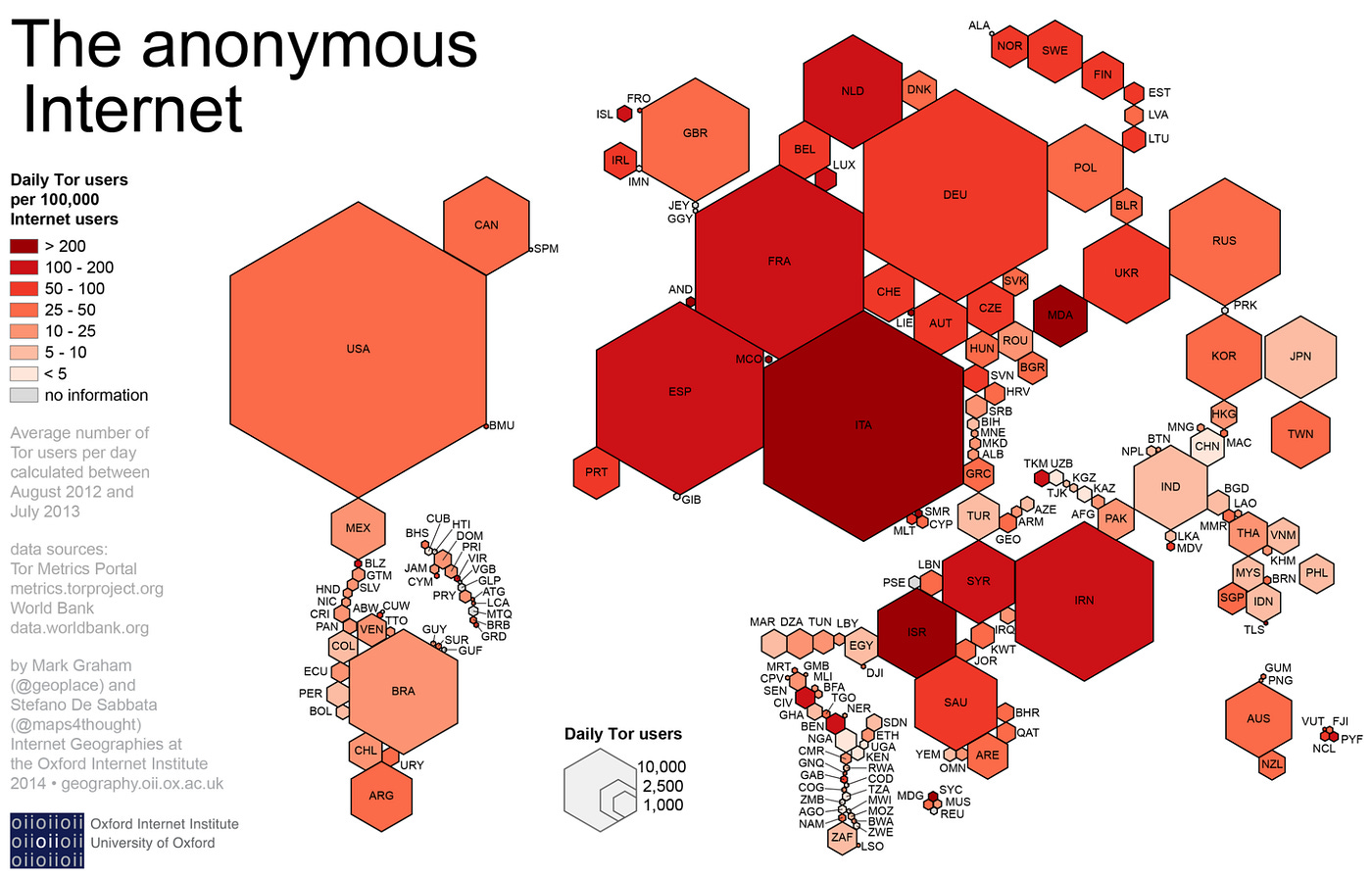
The dark web is a vast place that's more commonly known about in today's digital world.
For users, accessing the Dark Web safely requires understanding and utilizing tools like Tor (The Onion Router), which provides anonymity and privacy through its network. This tutorial aims to help guide beginners through the process of using Tor to access the Dark Web safely.
Understanding Tor
Tor is a free and open-source software that enables anonymous communication by directing internet traffic through a worldwide network of volunteer-operated servers. This network obscures a user’s location and usage from anyone conducting network surveillance or traffic analysis.
Tor works by encrypting and routing internet traffic through a series of randomly selected relays (or nodes) before reaching its destination. This process, known as onion routing, ensures that no single relay knows both the source and destination of the data, enhancing anonymity.
While Tor is much more heavily surveilled than in years gone by, it’s still an essential tool for privacy-focused communications. Legitimate users might find its encrypted communications useful
Accessing Tor
To access Tor we have a few options. Hardware-based or Virtual Machine.
Firstly, we can carry out a hardware installation, installing the necessary package on our everyday system. Like most software packages, this will require some basic software installation and configuration which you’ll need to be comfortable with.
The other option is to use a virtual machine or live USB system to create a temporary machine running an operating system that comes pre-configured with the Tor browser.
Both Kali Linux & Parrot OS come pre-configured with these packages, but if you’re really privacy-focused then you might find this an ideal time to check out TAILS OS, a completely privacy-focused live operating system. Running on a flash drive, TAILS uses the live OS principal to protect user data.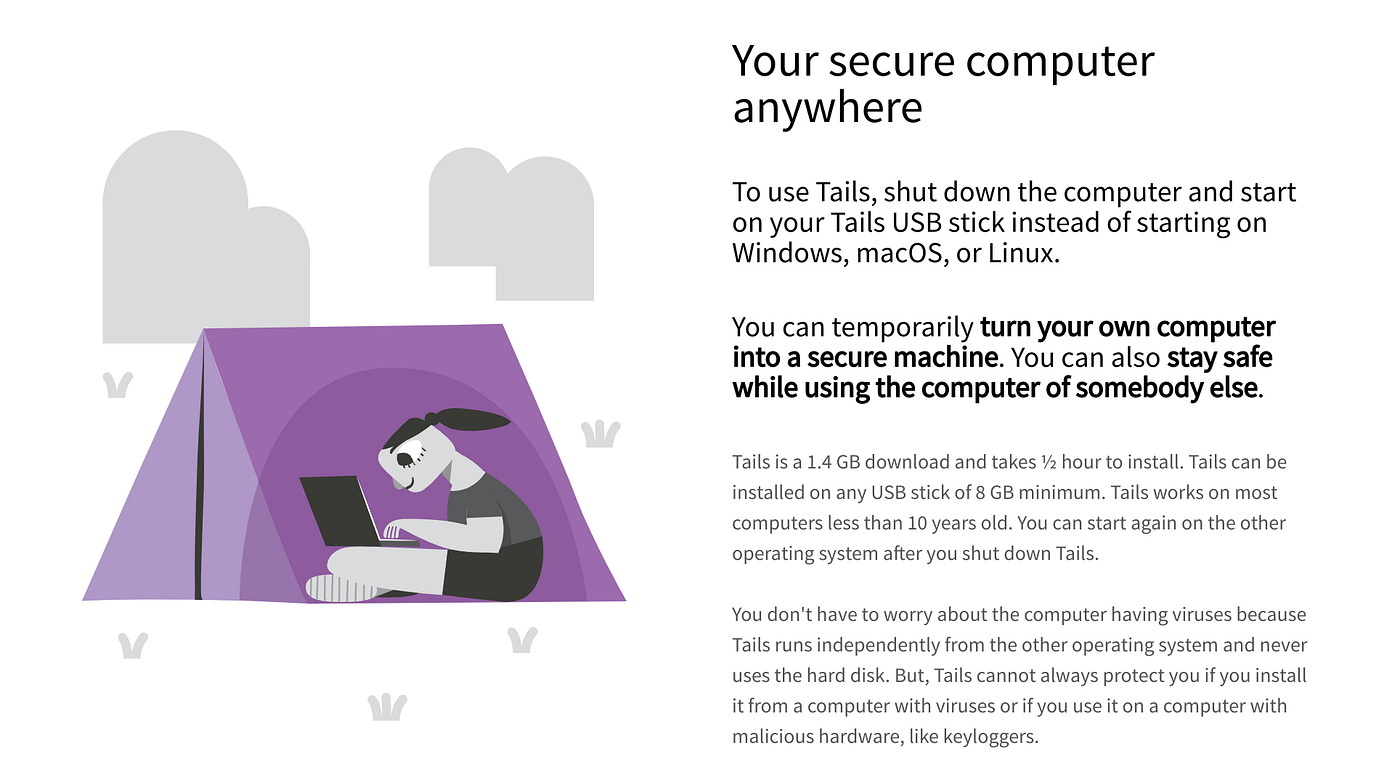
For today’s article, we’ll talk about a bare metal system installation, the quickest and easiest way to get started.
Installation
To install Tor on a bare metal machine, we’ll first visit the official Tor Project website.
There, download the Tor Browser bundle for your operating system — like Windows, macOS, or Linux.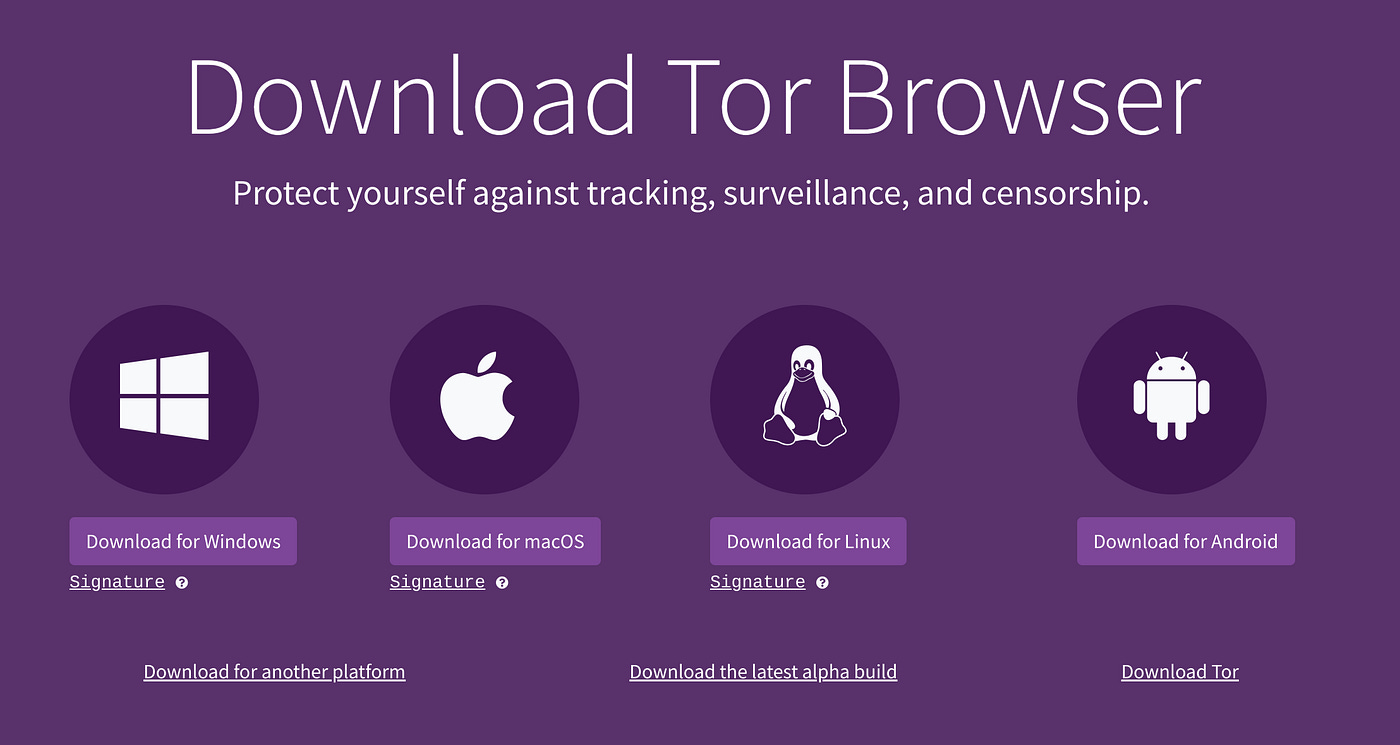
Before we install our software, we’ll need to check the cryptographic signature to ensure we’re getting the official version. This can often be the trickiest step for newcomers, but you’ll find instructions for your operating system easily accessible on the Tor Website.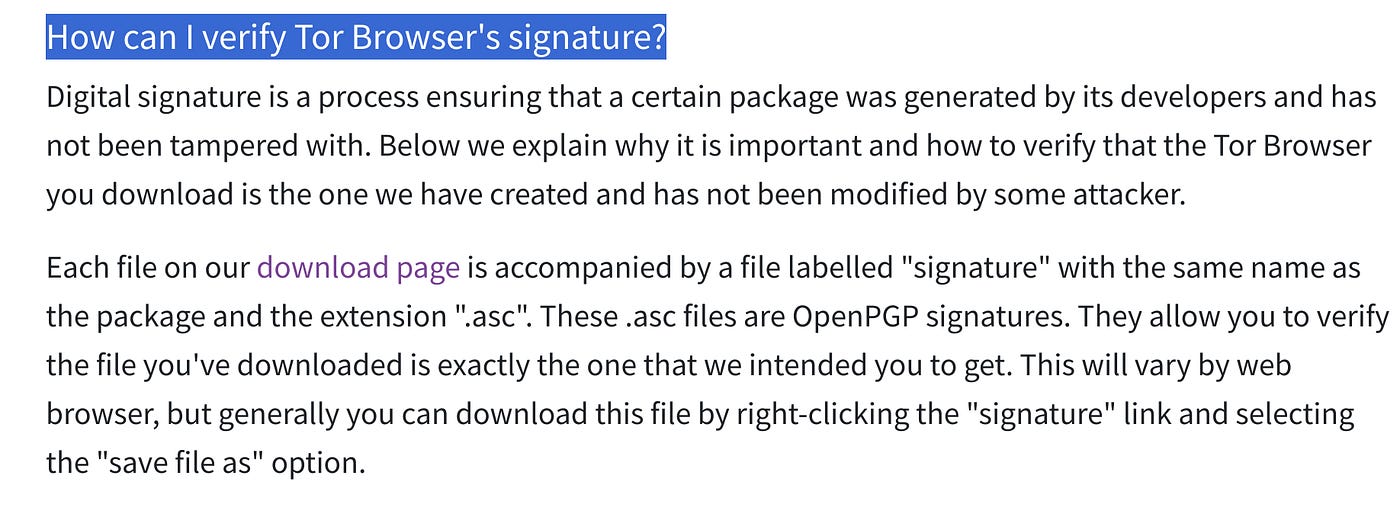
This cryptographic information uses PGP cryptography to ensure the integrity of the downloaded file. The file is signed by the Tor developers when updated, so confirming this signature matches will confirm that you’re dealing with the correct software package.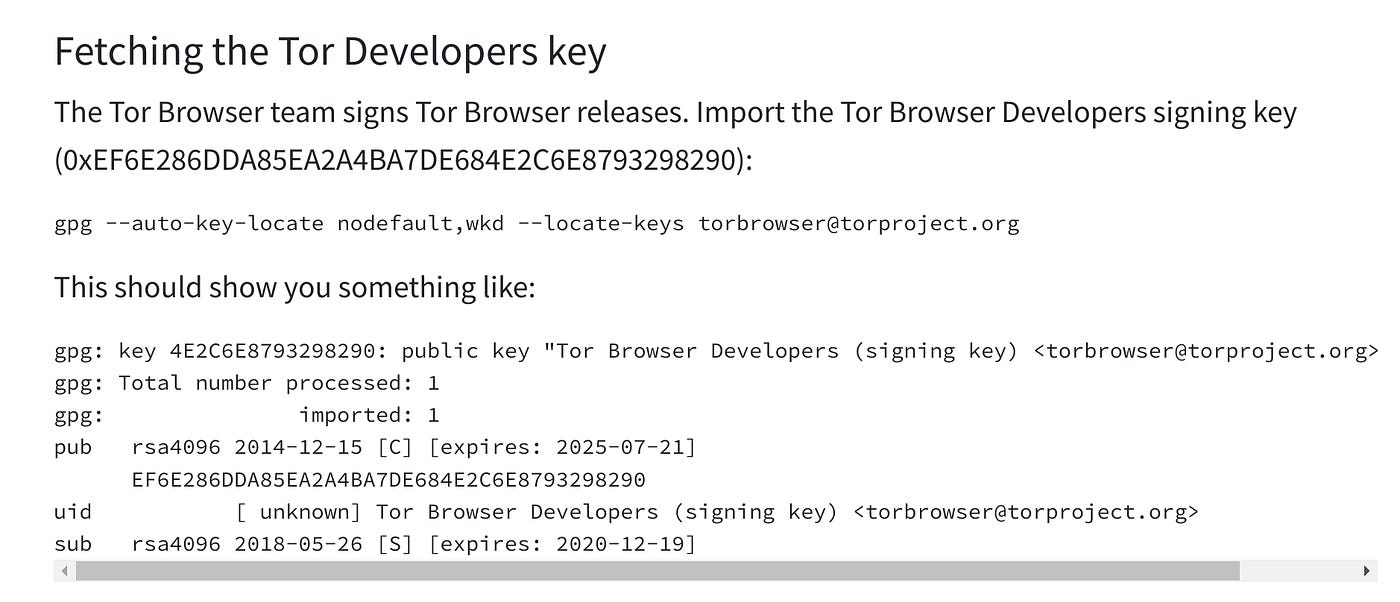
After installation, launch the Tor Browser, and it will automatically connect to the Tor network
How To Navigate
While you’ll use Tor in ways that are similar to your traditional browser, one notable variation is that Dark Web websites use “.onion” domains instead of traditional domain extensions like .com or .org.
These addresses are not accessible through regular browsers and will require Tor to access them. Dark Web URLs are typically a string of random characters followed by “.onion”. And, unlike normal websites, there is no “Whois” data for Tor.
Because of this, as well as the lack of indexing by search engines, finding Dark Web links can be challenging. However, various online communities, forums, and directories curate lists of Dark Web websites. While no links will be provided in today’s article, you can often find some of this information easily accessible on the clear web.
Once you’ve found some Dark Web websites, simply enter its .onion URL into the Tor Browser’s address bar and press Enter. The browser will connect to the Tor network and route your traffic through relays, providing anonymity and encryption.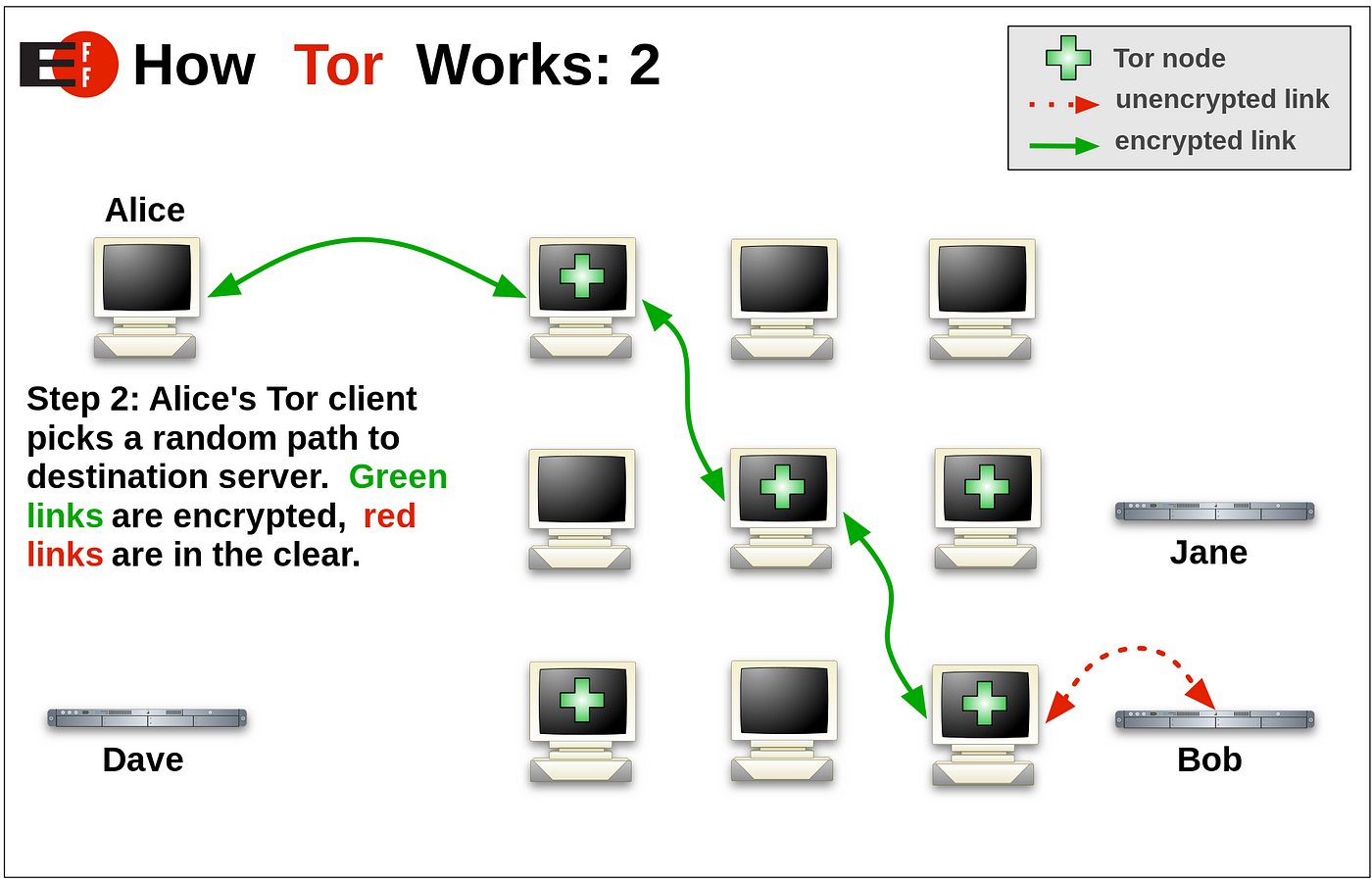
Ending Sessions
When you’re finished browsing the Dark Web or need to exit Tor, simply close the Tor Browser window like you would with any other program.
Tor Browser automatically clears your browsing history, cookies, and other data to maintain privacy.
Each time you use Tor, your browsing session is also isolated from previous sessions.
However, it's usually wise to consider any lingering security or privacy concerns before starting a new session.
Safely accessing the Dark Web with Tor helps deepen your understanding of the tools and practices that enhance anonymity, security, and privacy, and while it won’t be for everyone, learning how to leverage these tools can be a fun way to broaden your skillset.
However one important point. While the Tor project aims to provide security and anonymity, it’s worth remembering that over the years it’s also become a government playground. So, if you’re accessing services via Tor, expect analysis. Lots and lots of analysis.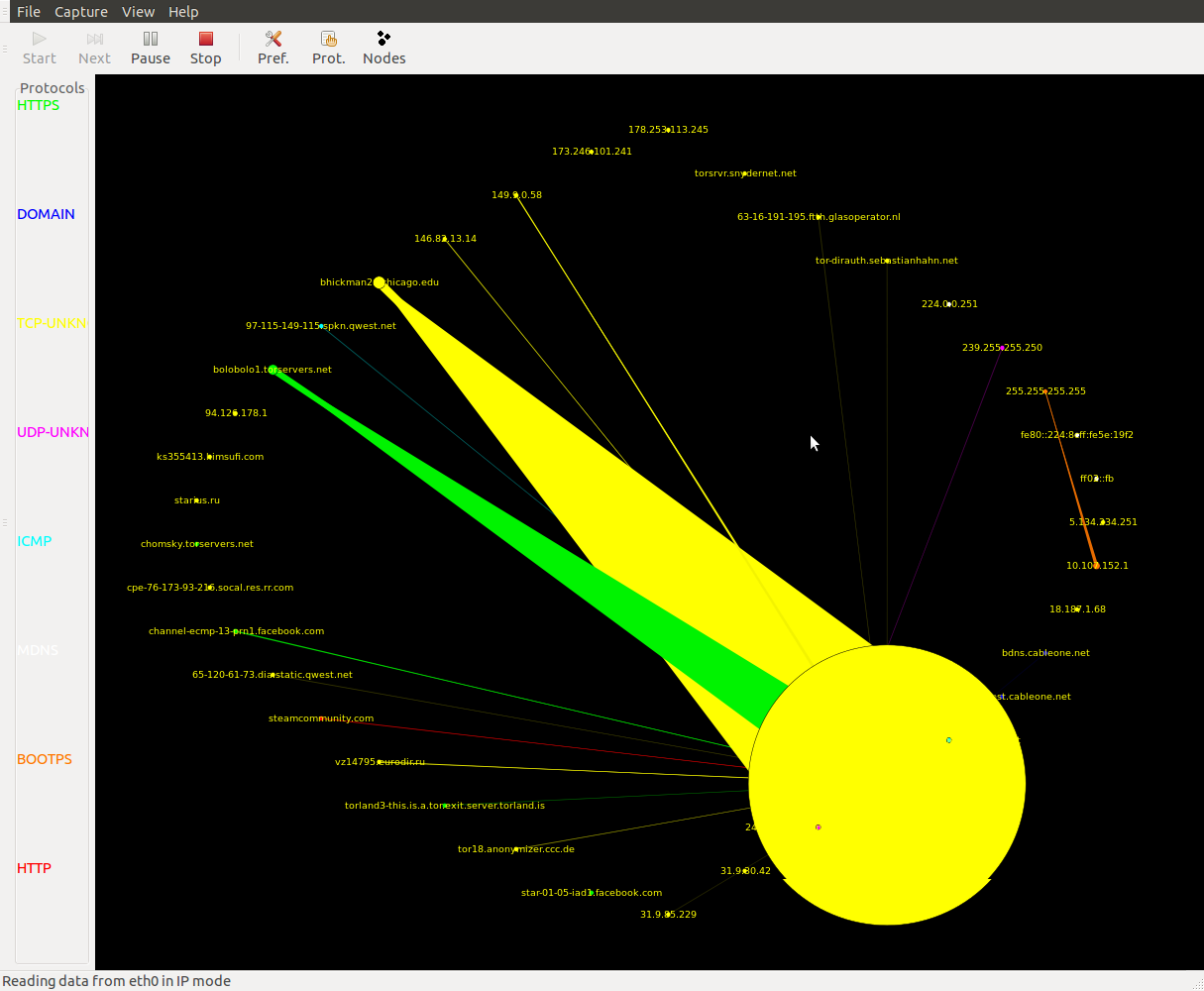
Tips For Staying Safe
While the Dark Web can be a bit of a sketchy place, some smart habits will help increase your chance of staying safe.
First and foremost, be cautious of the websites you visit on the Dark Web, as some may host illegal or malicious content. And, like the clear web, we should also avoid clicking on suspicious links or providing personal information.
It’s also essential to keep your Tor Browser up to date, as updates often include security patches that protect against emerging threats. Additionally, disabling JavaScript in your browser settings can help to mitigate potential security risks associated with malicious scripts.
As a researcher, we won't be purchasing content on Tor, but if someone decides that they want to do that, then we should understand that that will also change the risk profile as well.
There is no single silver bullet approach to online security, but a multi-layered approach toward security will usually increase your chances of avoiding problems.
Beware The Content
Despite the obvious risks and signs, many are still surprised to realise that the Dark Web can be a bit of a sinister place, with all manner of advertisements, content and services being advertised. Because of this, individuals will have to apply their own risk management strategies to their online behaviour.
Depending on where you live, even accessing dark web services or running a node may be illegal or land you in hot water, so it’s wise to understand the rules that govern your location and look into mitigating these risks beforehand so you understand what you’re getting yourself into.
It’s also worth mentioning that even if you aren’t seeing illegal content, you may still be exposed to disturbing material inadvertently by simply going about your business, so understanding some of this stuff contextually is a good idea before you get started.
Should you need more material to help you get started along the way, you’ll find a huge array of additional material to get you started via the Tor Project.
Happy Darkweb surfing!
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Software Defined Radio & Radio Hacking Pt 1
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates