Hackers For Hire: Exploring Bug Bounty Programs
Bug Bounty programs can be a great way to test your skills without breaking the law.
The Background:
We started our writing journey by wanting to make technology less technical, providing tutorials, resources and breakdowns that were easy to understand and implement. Along the way, there’s been projects and explorations around technology and open source intelligence, as well as strategies around implementing them into your workflow.
One thing we haven’t done though, is talked about ways to apply these skills for financial gain. Open source intelligence and cyber security are both fields where new ideas and innovation are important, leading to new ways of doing different jobs and new vulnerabilities that are to be patched before exploitation.
We’ve talked about HacktheBox and TryHackMe before in previous articles, explaining how they are great resources for people that work in IT. You don’t even have to be a master hacker to appreciate these resources either, as they’ll also provide information about open source intelligence, developing good cyber hygiene habits and other useful topics as well.
However the issue with resources such as these is that beyond a point, they can provide a stale environment for skills development, often varying greatly from how you’ll apply your skills practically in the read world during a pentest or red team engagement. As we’ve stressed previously though, performing real world engagements without approval is, in most parts of the world illegal.
So your lab skills are polished, you’re ready for your first real world engagement yet you’ve got no where to go?? Read on, we have a solution.
The Program:
If you’re relatively new to the game, it might surprise you to learn that there’s places where you can compromise machines, perform exploits and even hack government systems without landing yourself a prison holiday. It’s known as Bug Bounty, or Bug hunting and it’s a real world application of cyber security skills that’s an essential part of providing security to real world applications and infrastructure. 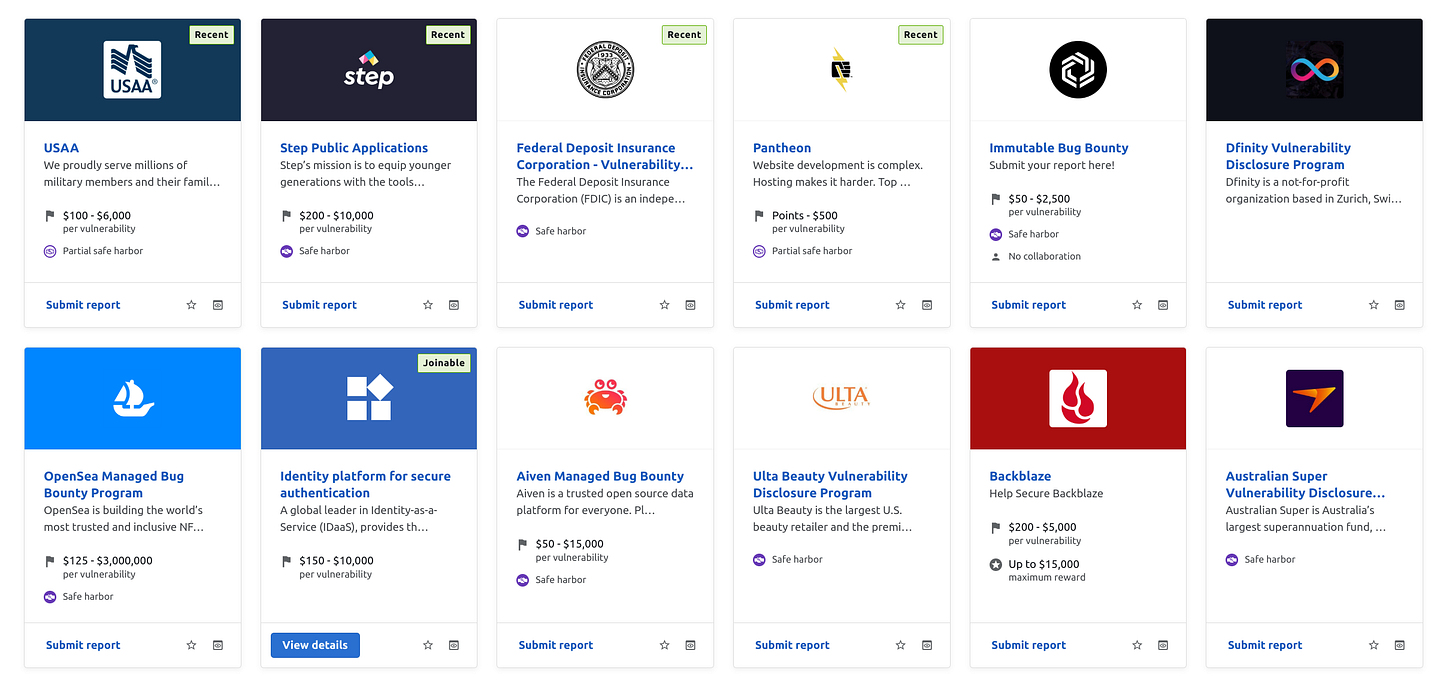 Just some of the programs available at the moment. Source: Bugcrowd.com
Just some of the programs available at the moment. Source: Bugcrowd.com
Bug Bounties had their start before the proliferation of the internet, with the first program put together by Hunter and Ready, with bugs reported in the Versatile Real Time Executive system giving the reporter a chance to win a Volkswagen Beetle. In today’s world though, programs give reporters the chance to earn cash, as well as industry cred by finding and reporting exploits. 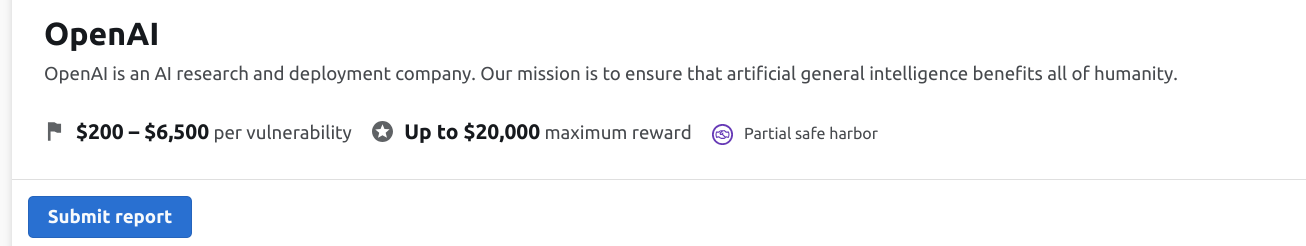 Good Bounty hunters are in hot demand. Check out those rewards. Source: bugcrowd.com
Good Bounty hunters are in hot demand. Check out those rewards. Source: bugcrowd.com
Typically, companies would put together their Bug Bounty program and come up with a “scope of assets” that required testing along with “rules of engagement” that defined what was legal under their program. This would be applied and a user that was able to successfully find a bug would report and be paid out. It’s a nod to the real world utility that hackers, cybersecurity analysts and industry specialists have in providing a unique perspective in how to secure and compromise a system. It’s essential to understand your rules of engagement before operating. Source: bugcrowd.com
It’s essential to understand your rules of engagement before operating. Source: bugcrowd.com
You’re probably thinking at this point that this sounds great and wondering what the catch is? Or perhaps you’re thinking that bug bounty covers larger issues and your technical skills might not be enough to get involved and have a shot. Well, in this instance you might be surprised to learn that bug bounty programs will pay anything in scope and that in terms of technical skills, even beginners have the option of getting involved.
This is because many bugs found are often low priority and not particularly difficult to find. In this scenario, the best chance you have of finding one is applying your skills in the real world and getting to searching. Even beginner OSINT analysts can get on board, check out the Google Hacking Database to learn more.  Analysts, arise! GHDB has good resources. Source: exploit-db.com
Analysts, arise! GHDB has good resources. Source: exploit-db.com
Getting Involved:
If you’ve heard enough and you want to get involved, then you’re at the right place in the article. To get onboard, you’ll need to join some of the project managers and register as a researcher. No need to be shy here, loyalty does not apply. Join all of them if you chose, it’s a good way to stay ahead of the latest developments and releases in the bug bounty sector. It’s also a pretty good place to network and most programs typically have resources available to make things easier for new hunters. This means you can also continue to develop your skills along the way.
Join the team and become a Ninja via the Bugcrowd Program, then
Jump on board and register with HackerOne
and lastly, sign up for YesWeHack.
Bug Bounty is a great way to continue and expand your learning journey while making a living along the way. While it’s not for everyone, the fact that it provides a chance to indulge in real world security while providing learning resources means that for many, it’s a quick way to apply and develop your cybersecurity skills in a tangible way.
Lastly, if you’re a new hunter then here’s two pro tips for getting started.
Firstly, try focusing on just a few aspects of hunting while you refine and develop your technique. This gives you the best chance of uncovering a bug while figuring out how it all works. It also reduces the chance of being overwhelmed while you develop your workflow. A good understanding of the OWASP Top 10 and some patience will take you a long way.
And secondly, look for projects that provide “Safe Harbors” to hunters. This typically means that any mistakes or problems encountered during hunting will not be pursued if done in good faith, ie as part of the program. It’s an additional safety net that provides newcomers with additional protections while they are carrying out their research.
Good Luck, and Happy Hunting!
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our Telegram channel for exclusive updates or.
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Software Defined Radio & Radio Hacking
- OSINT Unleashed: 5 Essential Tools for Cyber Investigators
✉️ Want more content like this? Sign up for email updates here