Understanding Cyber Attacks: Types and Strategies for Protection

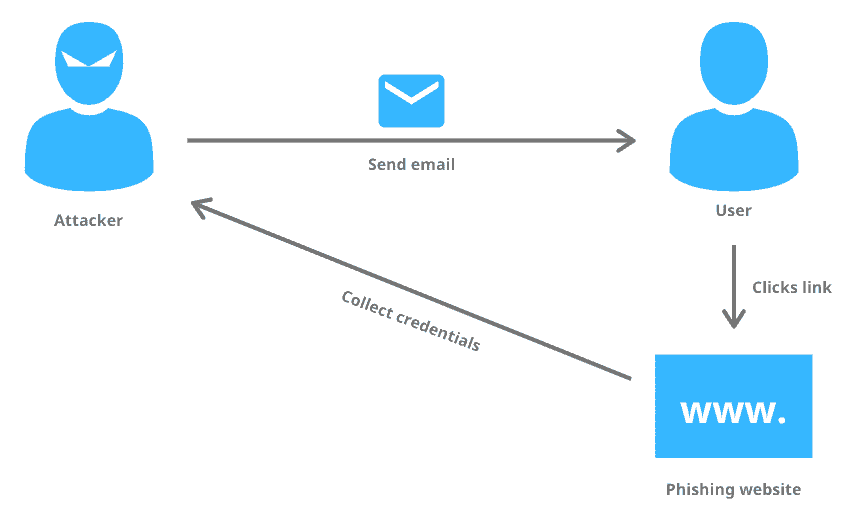
- Phishing Attacks: Phishing is one of the most prevalent forms of cyber attack. It involves the use of deceptive emails, messages, or websites to trick individuals into revealing sensitive information such as login credentials, financial data, or personal details. These attacks often mimic legitimate entities, such as banks or government agencies, to gain trust. Vigilance and education are key defenses against phishing attacks. Users should be cautious of unsolicited emails or messages and verify the authenticity of websites before entering sensitive information.
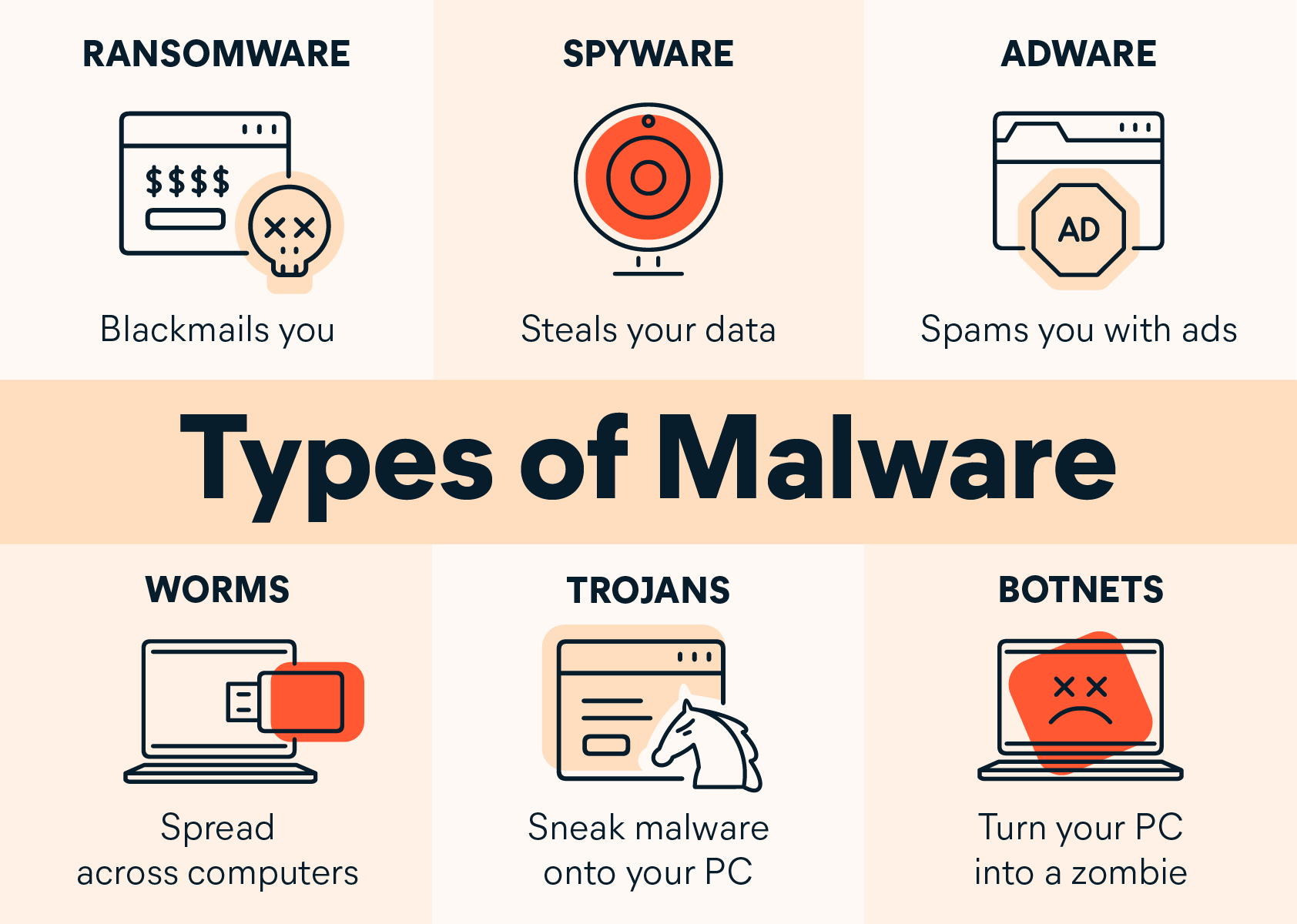
- Malware: Malware, short for malicious software, encompasses a variety of harmful programs designed to infiltrate and damage computers or networks. Common types of malware include viruses, worms, Trojans, and ransomware. Viruses attach themselves to legitimate programs and replicate when the program is executed. Worms spread independently across networks, exploiting vulnerabilities to infect other systems. Trojans disguise themselves as harmless programs to trick users into installing them, granting cybercriminals unauthorized access to their systems. Ransomware encrypts files or locks users out of their systems until a ransom is paid. To mitigate the risk of malware attacks, organizations and individuals should regularly update their antivirus software, exercise caution when downloading files or clicking links, and maintain secure backups of important data.
- Denial-of-Service (DoS) Attacks: DoS attacks aim to disrupt the normal functioning of a network or website by overwhelming it with a flood of traffic. This prevents legitimate users from accessing the services provided by the target.
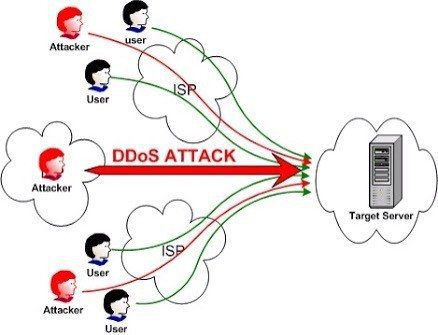
- Distributed Denial-of-Service (DDoS) attacks, a variant of DoS attacks, involve multiple compromised devices, collectively known as a botnet, orchestrating the attack. Defending against DoS attacks requires implementing robust network security measures, such as firewalls and intrusion detection systems, to filter out malicious traffic and maintain service availability.

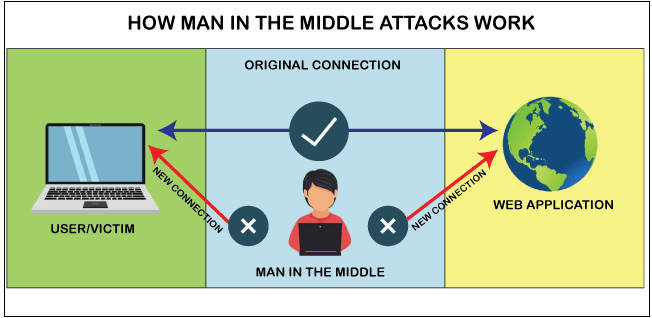
- Man-in-the-Middle (MitM) Attacks: MitM attacks occur when a cybercriminal intercepts and potentially alters communication between two parties without their knowledge. This allows the attacker to eavesdrop on sensitive information or manipulate the data exchanged between the victims. Common methods used in MitM attacks include session hijacking, where the attacker assumes control of an ongoing session between two parties, and DNS spoofing, where the attacker redirects network traffic to a malicious server. Employing encryption protocols, such as HTTPS, and using virtual private networks (VPNs) can help mitigate the risk of MitM attacks by securing communication channels.
- SQL Injection: SQL injection attacks target websites or web applications that utilize a backend database to store and retrieve information. By exploiting vulnerabilities in the application's input fields, attackers can inject malicious SQL commands into the database, enabling them to retrieve, modify, or delete sensitive data. To prevent SQL injection attacks, developers should implement parameterized queries and input validation techniques to sanitize user input and mitigate the risk of unauthorized database access.

As cyber threats continue to evolve, staying informed and implementing proactive security measures are paramount. By understanding the different types of cyber attacks and adopting best practices for protection, individuals and organizations can minimize their susceptibility to cybercrime and safeguard their digital assets. If you have any questions or would like to share your experiences with cyber attacks and security measures, feel free to comment below. Your insights and contributions are valuable in fostering a safer digital environment for all.
References:
- Cisco. (n.d.). "Phishing: What You Need to Know." Retrieved from https://www.cisco.com/c/en/us/products/security/email-security/phishing.html
- Symantec. (n.d.). "Types of Malware: Explained." Retrieved from https://www.symantec.com/blogs/threat-intelligence/types-malware-explained
- Cloudflare. (n.d.). "What is a DDoS Attack?" Retrieved from https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
- OWASP. (n.d.). "Man-in-the-Middle Attack (MitM)." Retrieved from https://owasp.org/www-community/attacks/Man-in-the-Middle_Attack
- PortSwigger. (n.d.). "SQL Injection." Retrieved from https://portswigger.net/web-security/sql-injection