Why Say Goodbye to Web2
Web2 has come a long way over Web1 in allowing the user to interactively control her website. B. Social Media Platforms - Admittedly, this has significant drawbacks.
The most prominent of these is its level of centralization. You have some control, but things get a little sketchy when it comes to how much control you have over your data.
Centralized Web2 powerhouses such as Google and Meta extract and store data, ostensibly to improve the platform's services. In most, if not all, of these apps and websites, you must consent to the collection of your personal information.
Web2 privacy and security concerns
Once you give up control of your personal information, these companies use it for everything from tracking your online activity and serving you personalized ads to collecting contact information. There is a possibility. Contact information is often sold to third parties without your knowledge. They also fall prey to security breaches that target centralized servers.
User data breaches have made headlines for years, including the Facebook and Cambridge Analytica data breaches that allegedly impacted the outcome of the 2016 US presidential election. Cambridge Analytica, an analytics firm allegedly associated with Donald Trump's presidential team, allegedly used leaked Facebook user data to advance its political campaign at the time. In 2018, Google discovered personal data leaks from Google+ users. The first of his two disclosed data breaches, which affected about half a million users, reportedly went unnoticed for years before being discovered. These incidents led to the shutdown of Google+ in 2019.
2019 was also the year Yahoo agreed to pay nearly $120 million to users affected by what it called "the largest data breach in history." Between 2013 and 2016, 3 billion Yahoo users had their identities stolen and put up for sale on the dark web.
Most recently, Twitter's former security chief-turned-whistleblower Peiter "Mudge" Zatko announced in August 2022 that he would threaten the social media giant with security measures that would put users' personal information at risk. I claimed there was a problem. Retention of personal data data from deleted accounts. Twitter disputed the allegations.
These are just a few examples of serious user data breaches faced by technology companies due to weaknesses in Web2's centralized security.
What about web3
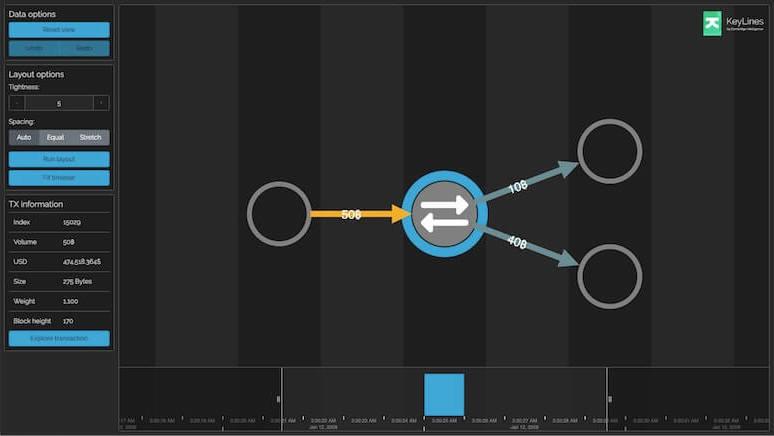
Alluding to what you read a little earlier in this article, the key takeaway of Web3 is its decentralized or blockchain format, which inherently has greater security- and privacy-preserving capabilities than a centralized system.
This is because, unlike a centralized system where one party could assume control of what happens to everyone’s data, a decentralized one works on the basis of distributed or collective authorit
In other words, no individual or single group can hijack the controls. The power is collectively held by everyone in the syste
Web3’s privacy and security advanta
Adding to the benefits of a distributed ledger, data which has been uploaded to a blockchain is recorded immutably — and therefore highly resistant to tampering
User data can also be kept secure and private more effectively with potent cryptographic security measures such as hashes, proof protocols and threshold signature
Thus there is a far lower risk of the data stored on a decentralized system being manipulated or stolen by bad actors, as compared to a centralized one.s..gem.y.
References
[1] <Analog>, '<Why You Should Care About Web3 — and Loosen Your Grip on Web2>' (online, <2022>) <https://medium.com/@analogtime/why-you-should-care-about-web3-and-loosen-your-grip-on-web2-7a18bc6d5376>.
[2] BULB, 'Write to Earn. Read to Earn' (online, 2022) <https://www.bulbapp.io/>