Computing in Isolation: Taking a look at Red Star Linux
The tale of Red Star is one of tracking, control and containment.
It’s hard to be a user of technology and have to pick a side of the fence to sit on. Apple over Android. Windows over Linux. Freeware over Payware. However, one operating system quietly stands out not only for its unique features but also for the intriguing geopolitical context in which it was developed. Enter Red Star Linux, an operating system born in the heart of North Korea, designed to provide its citizens with a distinct digital experience.
While most operating systems are products of international collaboration and technological evolution, Red Star Linux offers a glimpse into the controlled and isolated digital environment of North Korea. Developed under the guidance of the country’s government, this operating system presents a blend of functionality, ideology, and technological autonomy that sets it apart from its mainstream counterparts.
In this article, we embark on a journey to uncover the intriguing aspects of Red Star Linux. We’ll look into its origins, its unique features, and the broader implications it holds in the world of technology and geopolitics. From its user interface to its software ecosystem, Red Star Linux serves as a window into North Korea’s approach to technology, shedding light on how a closed society navigates the digital age. Join us as we explore the nuances, controversies, and curiosities that define the enigmatic Red Star Linux operating system.
What is It
Prior to using and developing Red Star North Korea used variants of western software, namely Red Hat Linux and older versions of Windows XP. Sensing the impending computer revolution and needing a way to bypass heavy western sanctions that were in place at the time, DPRK leadership subsequently started looking at ways to further ingrate technology into their society.
However due to the ideology of the DPRK, selection and implementation of suitable software would not be a one step process. This is because North Korea has a history of isolation and self sufficiency where possible, meaning that a heavy reliance on western software brought with it the opportunity of facing technological interruptions as well as surveillance.
Because of these many factors coming in to play, it seemed that the only solution available to leadership was the implementation and creation of their own software package, with all the features a dictatorship needed to keep an eye on their population.
The first steps toward this were taken in 1998, with the launch of Red Star OS, a Linux based operating system with a distinct Windows XP feel. Using KDE as it’s desktop environment, Red Star featured a text editor, email and office suites as well as a modified version of Firefox that is designed to work with the North Korean Intranet. However Red Star would lurk in the shadows for some time, taking until the late 2000’s for the first copy to be leaked to the western world.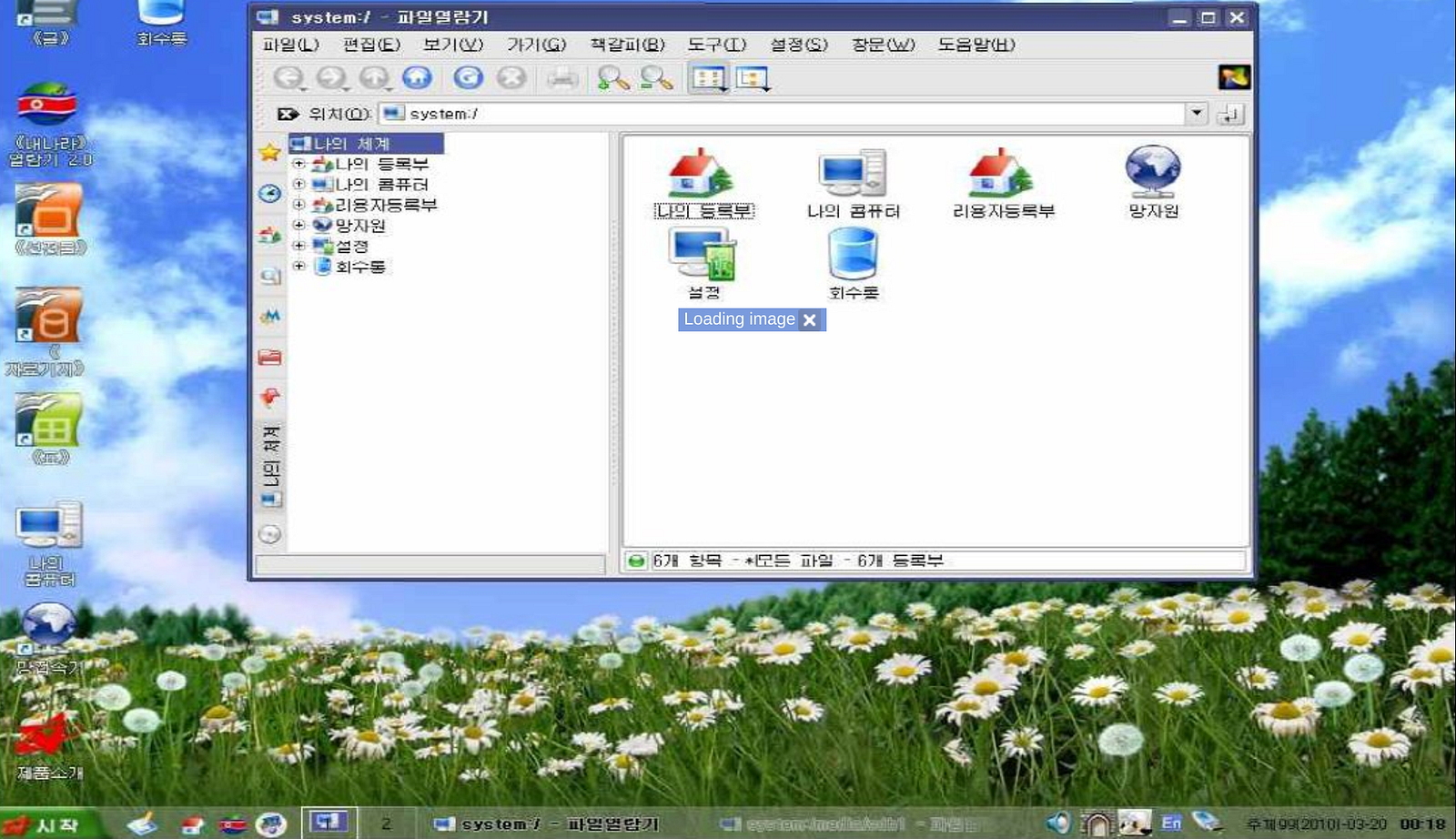 Red Star V1 desktop. Source: Wikipedia
Red Star V1 desktop. Source: Wikipedia
Let’s have a look at some of the features that make Red Star unique.
Requirements
Linux based, Red Star is an extremely efficient operating system with the early versions requiring just 3gb of disc space and 256mb of RAM. While the later versions are more resource intensive for the most part it remains a lightweight OS with good compatibility across devices found within North Korea.
Naenara
Based on Mozilla Firefox, Naenara is the people’s browser with one distinct twist. Rather than accessing the internet like you would to say, load Medium, Bulb or Publish0x, Naenara is more based on a country wide intranet that’s entirely localized to North Korea. Known as Kwangmyong, this intranet provides North Korea with the ability to be able to leverage technology for those that need it, and provides a way to securely and quickly exchange information across the country. This intranet also provides a heavily cultivated web portal that’s accessible to outside visitors. While it’s accessible world wide, we’ve chosen to not supply the address as NK servers have served malware to visitors in the past so you should exercise caution if you’re intending to look at some of these sites. 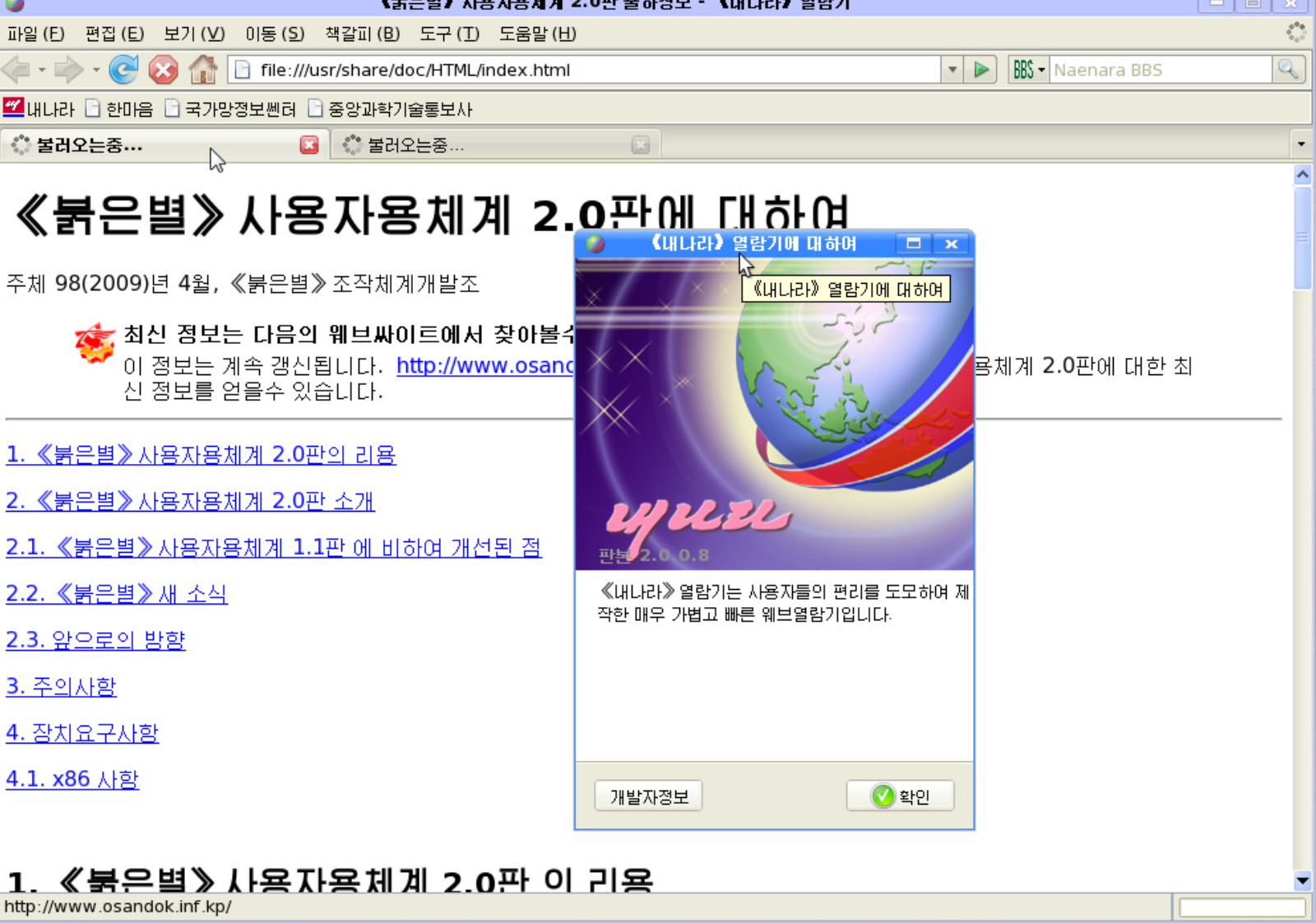 Naenara running in Redstar V1. Source: Wikipedia
Naenara running in Redstar V1. Source: Wikipedia
While people in country can access the actual internet the IP blocks allocated are extremely limited and seem to be limited to those fluent with technology and DPRK leadership which is what you’d typically expect to find when dealing with a dictatorship. One page that does receive regular traffic is the booking page for Air Koryo, the official North Korean airline.
When we last checked, travel from Vladivostok to Pyongyang was yours for the princely price of $230 USD. Just take your own food, because you probably don’t want to sample the Air Koryo mystery burger. 
 The Koryo burger. It looks much more appetizing from this angle. Source: Reddit
The Koryo burger. It looks much more appetizing from this angle. Source: Reddit
Censorship, Media Tagging & Propaganda
As you’d expect, looking into the kernel a little deeper shows some interesting additions to the software package. But to understand where we’re heading, firstly we need to understand the environment a little better.
Since the start, Korea has had a problem with foreign media. Used by South Korea and the west generally to spread information via this media, this became a bigger problem as the proliferation of computers increased across the country. To tackle this problem, Red Star has some interesting features around looking at media management in general.
To control the proliferation of USB flash drives, any device that is connected to the computer embeds it with an encrypted tag that allows government officials to track the movement of the media across the intranet. While explaining the system is probably outside the scope of a single article, what we can say is that it is that it uses these encrypted tags to identify users that may have shared media to people within their social circle. This helps track the movement of western propaganda through North Korea.
The system also uses various methods to prevent root access, with general users able to use, but not modify the local system and parts of the source code. Should a user interfere with a controlled file the machine simply resets. In some instances it may simply display an error message but any interfering with the firewall, anti virus or other key features will not only break your machine but will flag your attempt to officials. While this was eased in later versions, it’s still a prevalent feature for many users today.
Lastly the OS is rich with propaganda, with various images, quotes and ideologies presented to users throughout the experience.
Vulnerability
While later versions are unable to be sourced and therefore tested, the earlier version of Red Star remains available and has been heavily tested by internet researchers. During this testing, certain vulnerabilities were found that were unknown prior to the assessment. For instance the media tagging we mentioned earlier, applies to all files on the machine even if you haven’t opened them. Naenara also appears to be vulnerable to remote code execution via a well known Firefox vulnerability although it’s unknown how easy it is to exploit this vulnerability as it stands with the current software. However Red Star is significantly invasive to it’s users, providing monitoring capabilities and a way for Korean leadership to identify and track dissidents.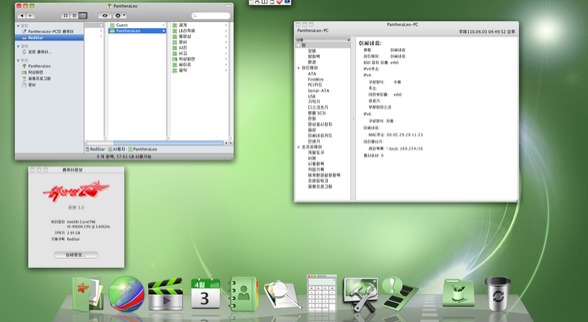 Desktop of RedStar V3.0 looking decidedly mac ish. Source: Wikipedia
Desktop of RedStar V3.0 looking decidedly mac ish. Source: Wikipedia
Other Variants
Like Windows and macOS, Red Star has gone through interesting developments over the years which we’ll share for you before we close the article out.
In the early days of Red Star development it was heavily influenced by Windows XP. However as the leadership of DPRK was passed from Kim Jong Ill to Kim Jong Un, we see the development of Red Star moving closer to a variant of macOS rather than any particular version of windows.
This is believed to be partly due to the fact that current leader Kim Jong Un, was educated in the western world and had a greater exposure to technology in general compared to leaders of the past. This means he took a more active role in steering the development of Red Star in a particular direction. This theory is supported by the fact that shortly after taking the leadership, Kim Jong Un was photographed using an Imac.
However later versions of Red Star, while still being locked down actually provide greater flexibility to it’s users with root access to the device actually obtainable in some instances. However less is known about these later versions due to the fact it usually takes some time for the distro to be leaked to the press. As it currently stands it’s believed that the software currently uses version 4, with further development expected into the future. Version 1 of the software is available via torrents for those who like to live dangerously. 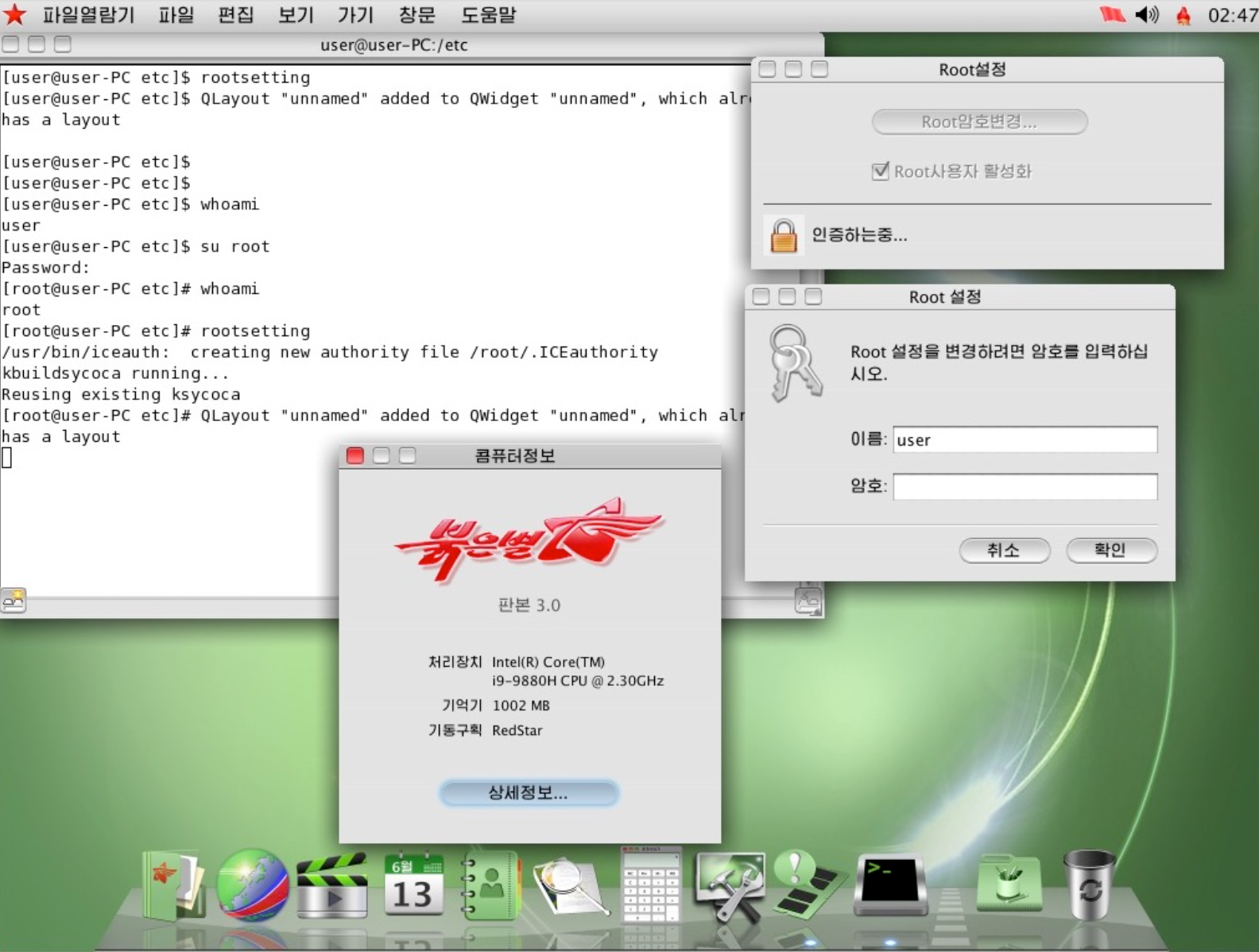 Red Star 3.0 with user root access. Source: Wikipedia.
Red Star 3.0 with user root access. Source: Wikipedia.
It’s worth pointing out that North Korea is by no means the only country to use it’s own operating system, with both China and Cuba also using and distributing software to it’s citizens. We’ll save the exploration of those for another day though.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our Telegram channel for exclusive updates or.
🐦 Follow us on Twitter
🔗 Articles we think you’ll like:
- OSINT Unleashed: 5 Essential Tools for Cyber Investigators
- Unleashing the Hunters: A History of Wild Weasels
✉️ Want more content like this? Sign up for email updates here