TTK about Secure Hub Patterns for Application Gateway.
As we all know that secured virtual hub can be used to filter traffic between virtual networks (V2V), virtual networks to branch offices vice-versa(B2V) and traffic to the Internet from VNET/Branch(B2I/V2I). Today, in this blog post we are going to discuss about ways to secure traffic between application gateway along with its back-end pools via secure hub.
There are two specific design patterns in this scenario, depending on whether the application gateway and backend pools are in the same VNet, or different VNets.
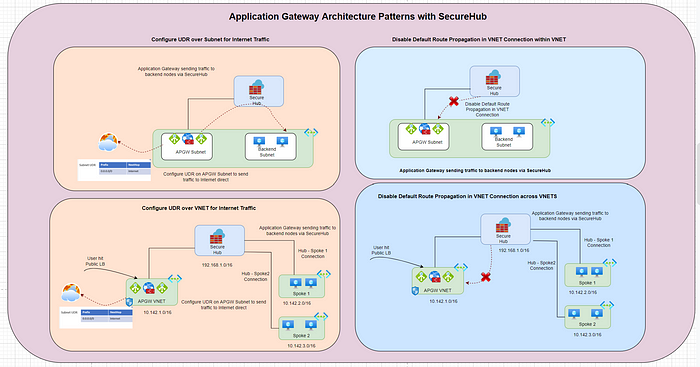 Photo by Author ©
Photo by Author ©
Scenario 1: The application gateway and backend pools are in different virtual networks peered to a Virtual WAN hub.
Scenario 2: The application gateway and backend pools are in the same virtual network peered to a Virtual WAN hub (separate subnets).
Now, we are going to discuss 2 approaches to implement each scenario along with Pros and Con’s.
Disable Default Route Propagation in VNET Connection
Create UDR in Application Gateway Subnet
Disable Default Route Propagation in VNET Connection
Disable default route propagation to a VNET connection only if the default route is already learned by the Virtual WAN hub as a result of deploying a firewall in the hub or any another connected site has forced tunneling enabled as this default route does not originate in the Virtual WAN hub.
Traverse, to VWAN → Virtual Network Connection → Select APGW VNET Connection → Disable Default Route propagation.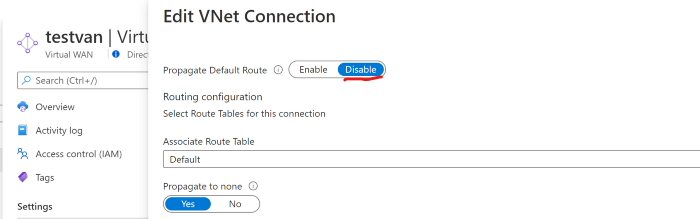 Photo by Author ©Disable Default Route Propagation in VNET Connection
Photo by Author ©Disable Default Route Propagation in VNET Connection
Once, you save the configuration you will notice that VNET connection Internet Traffic changed to Unsecured, and no default Route from secure will be learnt by VNET Connection and Internet Traffic will leave from the VNET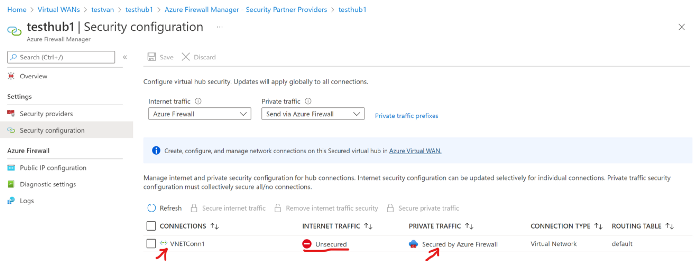 Photo by Author ©Secure Hub Pattern for Scenario-1
Photo by Author ©Secure Hub Pattern for Scenario-1
You can verify these settings by traversing to NIC of any VM deployed in that VNET and verify 0.0.0.0/0 is pointing directly to Internet instead of traversing via FW.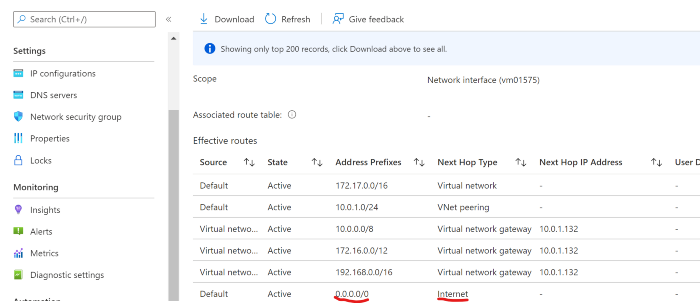 Photo by Author © Effective Route of APGW NIC
Photo by Author © Effective Route of APGW NIC
Drawback in doing this approach, as this configuration is applied over the VNET connection all the subnets will not receive the default Route which means that Traffic would not be going via firewall instead its leaving internet directly from VNET. This is preferred only when there centralized DMZ VNET which will host only Load balancers/Application Gateway with no other workloads underneath.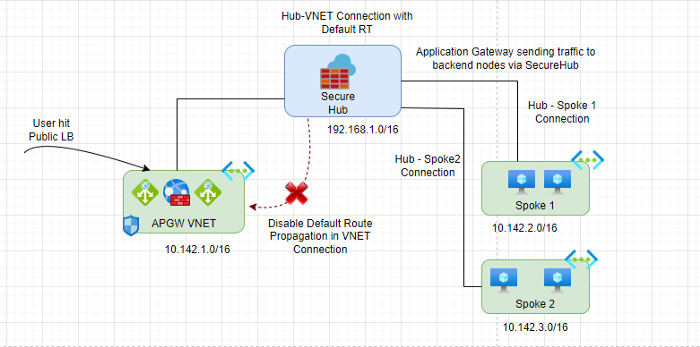 Photo by Author ©Scenario1- The application gateway and backend pools are in different virtual networks peered to a Secure Virtual WAN hub (Approach 1).
Photo by Author ©Scenario1- The application gateway and backend pools are in different virtual networks peered to a Secure Virtual WAN hub (Approach 1). Photo by Author (C)Scenario2- The application gateway and backend pools are in same virtual network peered to a Secure Virtual WAN hub (Approach 1).
Photo by Author (C)Scenario2- The application gateway and backend pools are in same virtual network peered to a Secure Virtual WAN hub (Approach 1).
Create UDR in Application Gateway Subnet
Another approach is to create UDR route to Internet attached to Application Gateway subnet so that traffic will route to Intenet directly from the subnet instead of traversing to SecureHub Firewall which will cause assymetric routing of packet transmission.
Now, go to Subnet which hosts application gateway and add below routes where 0.0.0.0/0 is directly pointed to Internet where as backend Pool traffic pointed to Azure Firewall.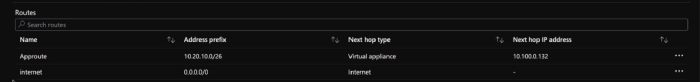 Photo by Author © Routes on Application Gateway Subnet
Photo by Author © Routes on Application Gateway Subnet
Similarly, for the back-end pool Subnet add a route to receive incoming traffic via FW. Photo by Author ©Routes on Spoke Subnet
Photo by Author ©Routes on Spoke Subnet
Even, after adding UDR you still see the policy settings intact because here we are overriding the default propagated Route by UDR in Subnet.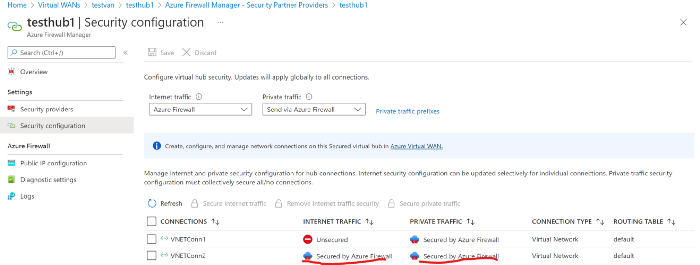 Photo by author © Secured Hub Policy Settings for Scenario-2
Photo by author © Secured Hub Policy Settings for Scenario-2
In the below screenshot, you can see the route 0.0.0.0/0 coming from SecureHub goes invalid and UDR is active.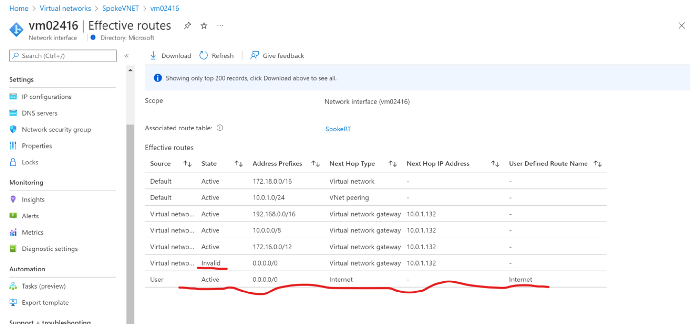 Photo by Author © Verify Effective Routes after adding UDR
Photo by Author © Verify Effective Routes after adding UDR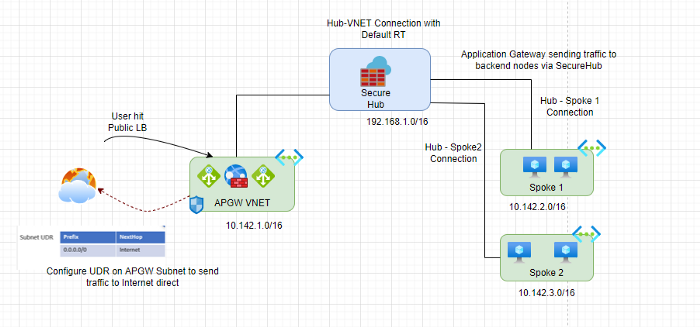 Photo by Author © Scenario1- The application gateway and backend pools are in different virtual networks peered to a Secure Virtual WAN hub (Approach 2).
Photo by Author © Scenario1- The application gateway and backend pools are in different virtual networks peered to a Secure Virtual WAN hub (Approach 2).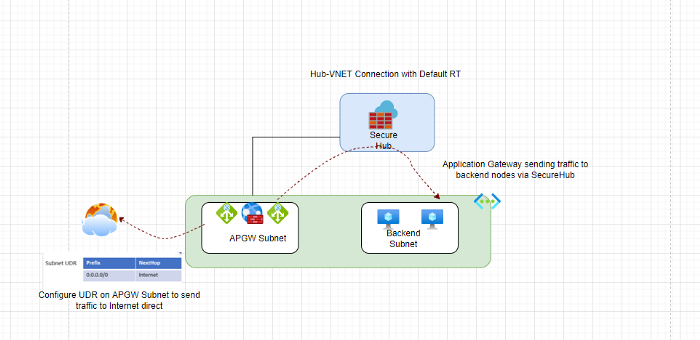 Photo by Author © Scenario2- The application gateway and backend pools are in different virtual networks peered to a Secure Virtual WAN hub (Approach 2).
Photo by Author © Scenario2- The application gateway and backend pools are in different virtual networks peered to a Secure Virtual WAN hub (Approach 2).
Drawback in this approach is basically if we delete UDR in the subnet it will break the control plane traffic to Application Gateway and will encounter issues. This is mostly preferred as it’s isolating the internet traffic only to subnet and remaining workloads still remain intact with SecureHub.
Now, let’s understand after configuring above 2 ways how can we validate backend traffic traversed via Azure Firewall, by looking at the logs.
Traverse to VWAN → Select Hub → Firewall Configuration → Security Partner Configuration→ Logs → Run Network Log Data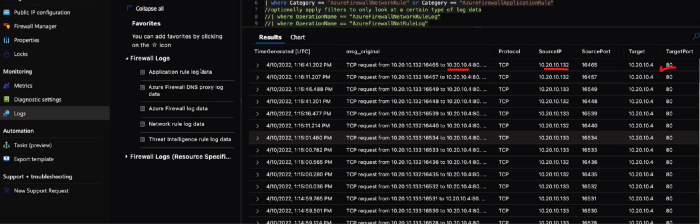 Photo by Author © Azure FW Network Logs
Photo by Author © Azure FW Network Logs
References:
I'm writing on medium, you can find my articles here: TTK about Secure Hub Patterns for Application Gateway. | by Musunuru Sharmila | Jul, 2022 | Medium
If you find the post enjoyable, please consider leaving us a positive review to help the author out.!! Thank you for time :)