$560,000 was stolen from crypto wallet,do these 6 things to reduce the risk of theft
From the bull market to the bear market, in addition to accepting the current market situation of the spot value shrinking by two-thirds or even falling by 90%, what is even more uncomfortable is that the wallet is stolen.
In the second half of 2023, as the bear market deepens, hackers become more active, more and more wallets are stolen, and many people lose money overnight.
According to incomplete statistics from my community, on September 6th, a group of friends was stolen for 210,000 usdt; on October 23, a group of friends was stolen for 230,000 usdt; on October 25, a group of friends was stolen for 2,000 usdt; on November 7 , a group of friends had another 16,000 usdt stolen; on November 14, a group of friends had another 110,000 usdt stolen; I didn’t see the others, and there are countless others whose losses have not been disclosed.
A rough calculation shows that these five friends lost more than $560,000.
These are just the experiences of a few wallets among players in my community. Other communities, other players, and even other projects are attacked by hackers from time to time, often losing hundreds of millions of dollars.
Last week, Poloniex project was hacked for US$126 million. Sun wanted to provide a 5% white hat bounty for the hacker to return it voluntarily, but did not receive a reply from the hacker.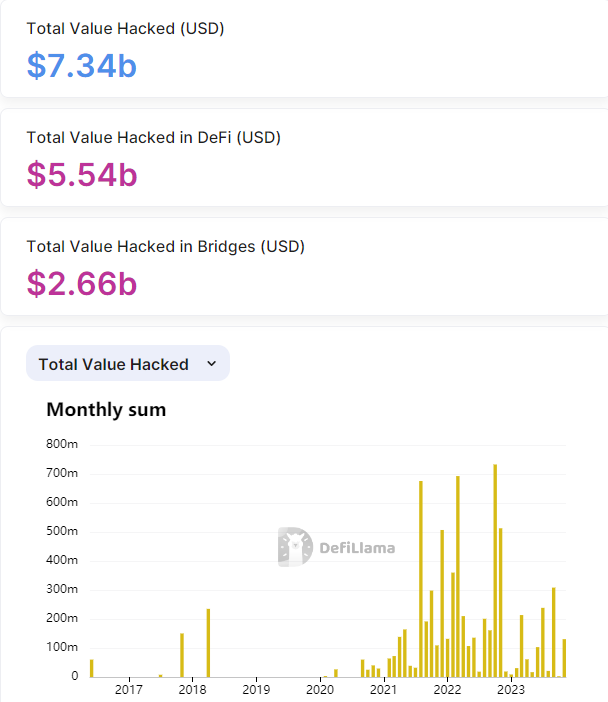 A total of US$7.34 billion will be hacked on the chain in 2023
A total of US$7.34 billion will be hacked on the chain in 2023
The decentralized technical characteristics of blockchain free players from the constraints and rules of centralization, but it also brings the other side of the double-edged sword;
As long as you get the wallet mnemonic or find a loophole, you can easily take away the wallet assets. Without a customer service center, there is no way to intercept or recover them.
Ordinary players take the spot, keep an eye on the contract, interact, and earn bands. The accumulated balance will be reset to zero once the wallet is stolen.
Several players had their on-chain wallets stolen. They used the wallets for a period of time after downloading them, but one day the balance was inexplicably transferred away and the wallets returned to zero.
There is no interaction with these wallets and no additional authorization. The wallets were also downloaded from the official website, but I don’t know at which point the mnemonic phrase was leaked.
Searching for the hacker’s wallet address, there are still large transfers from other wallets, but there is nothing we can do. We don’t know who the owner is behind the wallet, and we don’t know the private key and mnemonic phrase of the hacker’s wallet, so we can’t do anything.
If the assets on the chain are stolen, the alarm may not be accepted. The response you get is that the assets are virtual assets and you are responsible for your own profits and losses, and no assistance will be provided. If your wallet is stolen, you have to suffer huge pain and loss silently, with no room for recovery. On-chain wallets are trackable but anonymous
On-chain wallets are trackable but anonymous
There are thresholds for using digital wallets. You can only try to prevent problems before they occur, make full preparations, and try to protect every step.
① Download from the official website wallet
There are hundreds of wallets on the market, and some projects also have dedicated operating wallets. According to the wallet usage needs, choose a wallet that saves the keys locally and has an open source code.
When I interact with projects, I mainly uses metamask, or use wallet plug-ins recommended by the project side to interact; Bitpie is used to store encrypted assets.
At present, it is relatively rare to see theft of these two wallets in the group and on social media. The development team of metamask is from abroad, and bitpie should be developed by a domestic team.
Other wallets such as OKX, Coinbase, and Trust have exchange backgrounds, and less negative news is heard, and more people use them.
Generally download through the official website, do not obtain the official website through search; do not click on the official website or download link that others actively share with you. Numerous web3 wallets
Numerous web3 wallets
②Physical recording mnemonic phrase
The mnemonic phrase must not be copied and pasted into notepad, or screenshots saved in photo albums/computers/favorites. Each copy or screenshot increases the risk of leaking the mnemonic phrase.
All applications on the mobile phone may scan the user’s pasteboard. As long as it is copied once, it may be saved and uploaded to the corresponding database, and the mnemonic phrase has been leaked.
Manually copy the mnemonic words and keep them properly. Record them in a notebook. Store and back up multiple notebooks separately. Don’t just copy it on a piece of paper, because you may not be able to find it next time.
It’s troublesome but also convenient for hackers. When it was stolen, I don’t know which accident caused it. Keep the wallet mnemonic phrase properly. If it is lost or damaged, no one will be able to open the wallet, and the assets inside will be permanently locked, and you will regret it.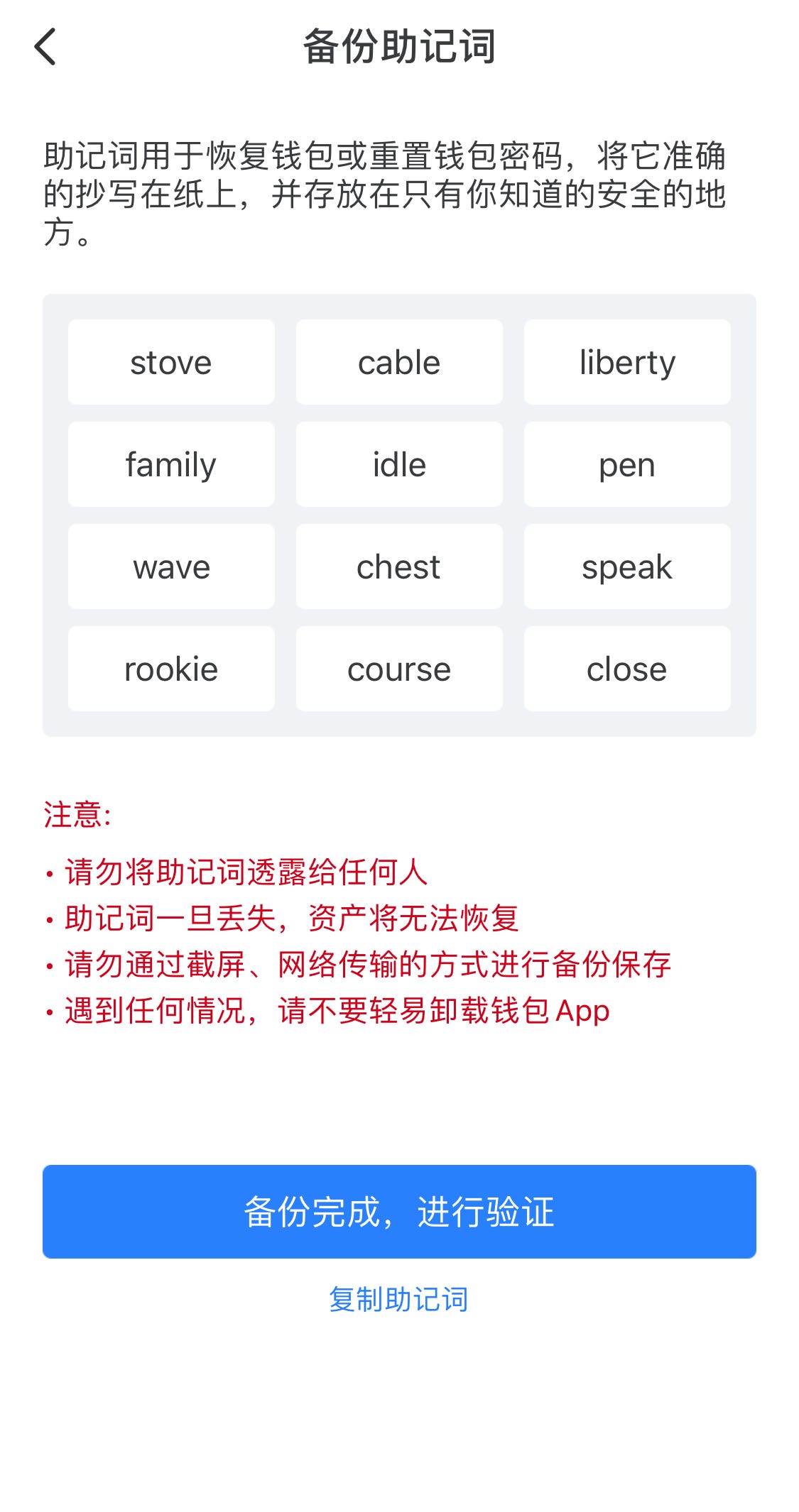 Copy mnemonics
Copy mnemonics
③Avoid leakage of mnemonic phrases
The friend mentioned earlier thought he downloaded the wallet from the official website, and the wallet was not logged into any other projects. The mobile phone environment was also very clean, but it was still stolen. Some people also suspected that it was a problem with the wallet development team itself.
Has the mnemonic phrase been recorded in the background and monitored when creating the wallet? When there is a large amount of money coming in, the assets are stolen? Of course there is no evidence for this.
Another friend has a partner and a girlfriend. Is it possible that the wallet mnemonic was leaked, causing the assets to be transferred away? It’s possible, but there’s no way to prove it.
Or the wallet mnemonic phrase is recorded in the mobile phone, or the screenshot is saved in the photo album, and it is scanned. It is possible.
Some malicious apps deliberately monitor user wallets, scan mnemonic phrases, upload them to the database, and monitor them in real time. Once the wallet contains a large amount, it will be transferred away. The mnemonic phrase is leaked, the wallet is not under control, and assets are stolen.
④ Operate contract authorization carefully
There are also some wallets that log in to certain projects for contract interaction. Some smart contracts themselves have risky vulnerabilities, which are designed to steal wallets. Once the wallet is authorized to log in, the wallet initiative is authorized to others, and others can operate it.
If it is a wallet that saves a large balance, do not do any authorization and only use the transfer in or out function to avoid any authorization risks.
If it is a wallet that specializes in airdrop interaction, you should also pay attention when authorizing certain projects and confirm that it is an official link before proceeding further. If you authorize some phishing sites, the wallet will also be stolen.
Do not trust the download links or project links provided by the community. It is possible that the account will be stolen after logging in and authorized; or the mnemonic phrase will be leaked and the wallet will no longer be safe.
You can check the authorization status at revoke.cash and cancel possible risky links. Hacking incidents are increasing
Hacking incidents are increasing
⑤Hardware wallet
You can also use hardware wallets for large amounts of assets, which is relatively safer.
The hardware wallet generates the mnemonic phrase offline, and the mnemonic phrase must also be properly stored. The hardware wallet does not require an Internet connection to use it. It can be connected to Bluetooth. After operation, it will not be connected to the Internet without any authorization, which is relatively safer.
Currently, common hardware wallets on the market, such as Ledger, OneKey, trezor, etc., also need to be purchased through the official website. They are similar to USB flash drives and do not interact with the Internet and are relatively safer.
⑥Don’t trust any TG official communication group
All tg links may be risky, and all those who send you private messages are basically scammers.
If you are pulled into some tg official communication groups and actively reply to questions. If you are stolen and still actively deal with it, you are probably a scammer.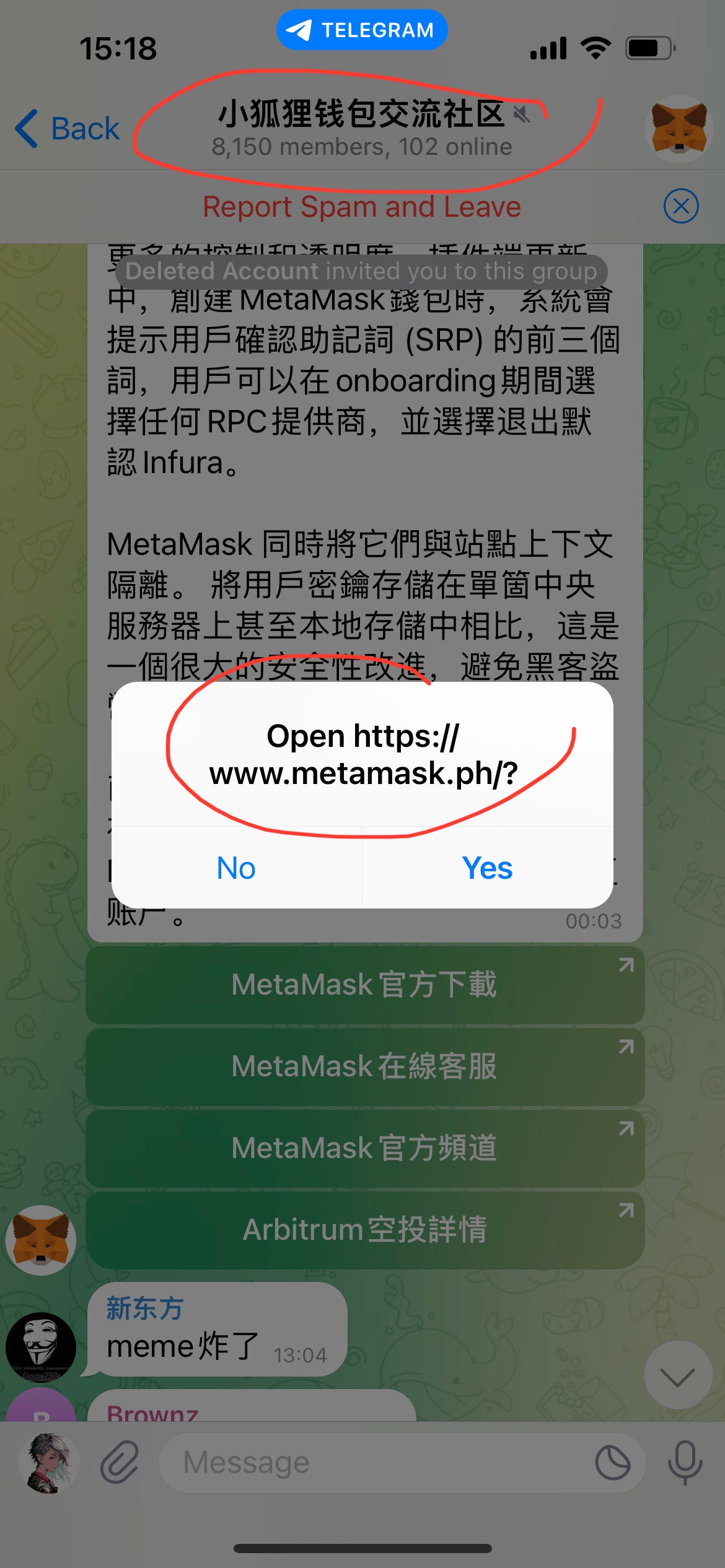 Phishing official website of fake official communication group
Phishing official website of fake official communication group
Of course, if you can’t do the above, you can also choose to place it on the leading exchange. Every operation on the exchange requires multiple verifications such as email, mobile phone verification code, Google authenticator, etc., which is relatively safe.
The only risk that needs to be guarded against is whether the exchange will go bankrupt or run away, because once the website cannot be accessed, the assets will not be under your control and you will not be able to withdraw them. A centralized platform can directly freeze user accounts and assets, and there is nothing you can do about it.
There are certain risks in any method. Face the risks and try to reduce the risks in every link. Every time you are lazy, you may have to pay high tuition fees, which can easily cost thousands or tens of thousands of dollars.
There will be no prompts for each risky operation. Once it occurs, it cannot be undone, causing permanent losses.
The crypto market is full of opportunities, and each opportunity hides corresponding risks; every time you take it seriously, it is possible to reduce a huge loss.
The above is just my personal opinion, no investment advice. I am CryptoLola, and I am paying attention to the encryption market and web3.
1
Hacker
Cryptocurrency
Btc
1
 Follow
Follow
Written by CryptoLola
1K Followers
·
Writer for
Coinmonks
I am a content creator, a self-media. I mainly focus on NFTs, Metaverse, Blockchain, etc.
More from CryptoLola and Coinmonks

 CryptoLola
CryptoLola
in
Coinmonks
How to optimize the Gitcoin passport score to above 17?
I did a thrivecoin task some time ago, completed 4 tasks in the first phase, and received 10 OPs, about $15;
5 min read
·
Jul 20, 2023
21
2
 Shantanu Gupta
Shantanu Gupta
in
Coinmonks
Which Crypto Will Explode in 2024? Here Are Some Of MyTop Picks.
As we approach the end of the year, investors worldwide are gearing up for the anticipated bull run in the crypto market, eyeing the next…
4 min read
·
Dec 19, 2023
726
4
 Velvet.Capital
Velvet.Capital
in
Coinmonks
🚨Velvet.Capital Token Distribution (Airdrop)🚨
🚨 Airdrop Alert🚨: DeFi Asset Management Done right! Everything you need to know for Velvet.Capital’s Token Distribution & Airdrop!
4 min read
·
Dec 30, 2022
40K
1063
 CryptoLola
CryptoLola
in
Coinmonks
The first BRC20 ORDI increased by 1428 times
In the past few days, the BRC20 track has become popular again.
6 min read
·
Nov 8, 2023
3
Recommended from Medium

 Brandon Duff, The Boring Passive Income Dad
Brandon Duff, The Boring Passive Income Dad
Crypto Challenge: $10 Into $100 In 24 Hours — Step by Step Guide
Brandon The Boring Passive Income Dad
·
4 min read
·
6 days ago
240
 Michel Marchand
Michel Marchand
in
Coinmonks
The Bull Is Back? Top 10 Cryptos to Buy on Coinbase in 2024
well . . . I’M back, shouldn’t that be enough?
21 min read
·
Dec 31, 2023
418
8
Lists

 Modern Marketing52 stories
Modern Marketing52 stories
·
371
saves
 Generative AI Recommended Reading52 stories
Generative AI Recommended Reading52 stories
·
627
saves 0xAnn
0xAnn
in
Crypto 24/7
Making Money Scalping Crypto
“Why do you work 9–5 when crypto trading is basically free money?”
·
7 min read
·
Jan 10
491
10
 Prodigy Sniper Bot
Prodigy Sniper Bot
What is a Crypto Sniper Bot and how to snipe in crypto ?
The ultimate guide to understand what is a Sniper bot and how to use it.
15 min read
·
Dec 22, 2023
22
 CryptoHunters100X.com
CryptoHunters100X.com
Crypto Hunters 100x Q4 Review
10 min read
·
Jan 3
103
 Mike Coldman
Mike Coldman
Top 4 Crypto Gems Set to Explode in 2024 !
Unlock the Secret Strategies of Elite Investors and Transform Your Portfolio Overnight !
·
5 min read
·
Jan 8
171
3



![[LIVE] Engage2Earn: auspol follower rush](https://cdn.bulbapp.io/frontend/images/c1a761de-5ce9-4e9b-b5b3-dc009e60bfa8/1)







![[ℕ𝕖𝕧𝕖𝕣] 𝕊𝕖𝕝𝕝 𝕐𝕠𝕦𝕣 𝔹𝕚𝕥𝕔𝕠𝕚𝕟 - And Now What.... Pray To The God Of Hopium?](https://cdn.bulbapp.io/frontend/images/79e7827b-c644-4853-b048-a9601a8a8da7/1)





















