Artificial Sleuths: Google Dorking
Using artificial intelligence to help improve your dorking skills.
In previous articles, we’ve looked at some easy strategies to get you started with Google “dorking”. If you’re new to this type of thing though, you might find it a little difficult to remember or be uncertain of where you might like to try and apply your new skillset. In the second article of our AI-powered OSINT series, we’re taking a look at using AI to help us get across Google dorking. Let’s go!
Start Your (Search) Engines!
This previous article has some more detailed info, but essentially, Dorking allows us to use certain strings and phrases to help leverage the Google search engine to uncover interesting information. Used by both good and bad guys, Dorking can be particularly useful in the recon phase, where you’re looking to build a picture or uncover information linked to specific targets.
Some people have been paid good money for uncovering confidential information that was incorrectly indexed through open bug bounty programs. So, if you’re a bounty hunter, it’s quite possible to dork your way to rewards just by knowing what to search for and where to look. More on that later though.
DorkGPT
In the first article, we discussed how custom-configured AI models can be extremely useful, allowing you to find and analyse information in a specific “role” that’s optimised for that task. DorkGPT is a great example of this. While we could use the OG ChatGPT to help us, DorkGPT should give us much better results, as it’s configured as a pro searcher from the outset.
You’ll find the interface simple to use and quite familiar, as it’s powered by the same OpenAI engine that is used for ChatGPT under the hood. More of these cybersecurity-focused AI-agents are becoming available, but you’ll achieve the best results by adding your own “wrapper” that is configured for your own purposes.
If you’re a pro, it’ll configure your search string off your text-based input. If you’re a beginner, you might want to look at keeping a Chat GPT window open so you can have the output broken down for you.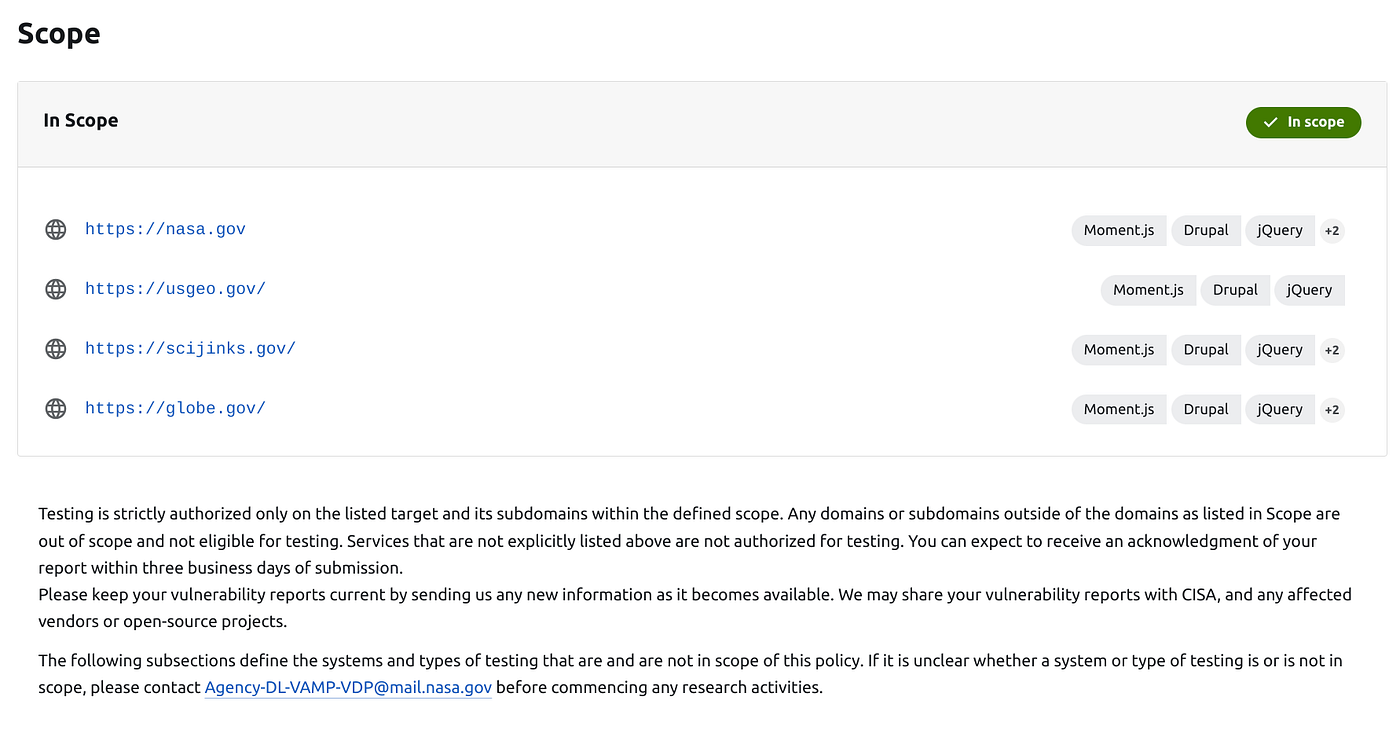 “Hacking” NASA can be as simple as finding misconfigured files. Source: bugcrowd.com
“Hacking” NASA can be as simple as finding misconfigured files. Source: bugcrowd.com
Interesting Files
Sometimes you might just want to dork your way through your own web history however, at other times you might want to try your luck and see what you can find.
If you’re looking to try your hand at bug bounty, then you’ll want to uncover sensitive or misconfigured files to have the best chance of a payout. To ensure you’re staying legal, you’ll need to join one of the programs to find out your rules of engagement. Bugcrowd is good for beginners.
While the scope can be pretty broad, ideally we’ll be looking for files that contain sensitive credentials, databases or backups and configuration files like .conf or .env.
It just so happens that NASA has an active bug bounty program, so we can use our search strings to target that. We can use the Dork to generate a string with this prompt
.env .conf .sql files on the nasa.gov domain
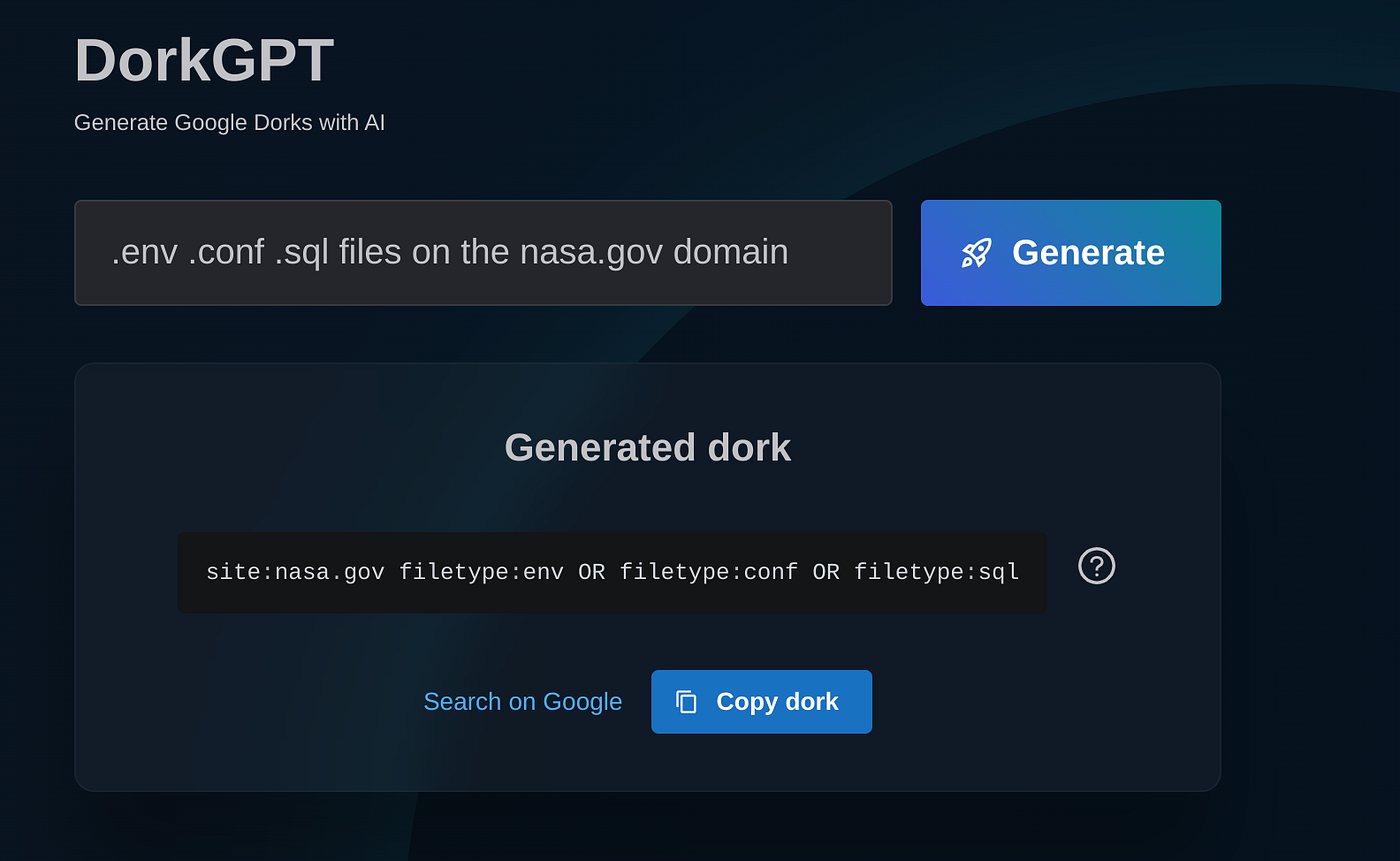 DorkGPT is super useful if you’re confused about search strings. Source: DorkGPT
DorkGPT is super useful if you’re confused about search strings. Source: DorkGPT
The best results come from unique and specific strings, but for the purposes of the article, we’ll try using a combined search instead. We can see that the Dork returns with the following string.
site:nasa.gov filetype:env OR filetype:conf OR filetype:sql
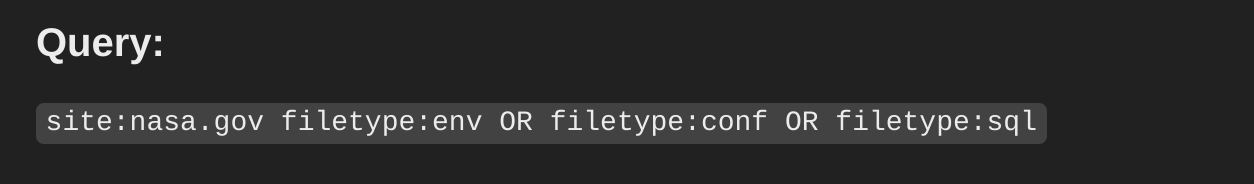
Breaking this down is simple. The “site:” flag allows us to restrict the search to the nasa.gov domain, allowing us to stay in-scope. The “filetype:” flag allows us to restrict our search to a specific filetype. While the “OR” flag allows us to search with multiple factors. Too easy! Our search results look a little different now. Source: Google.com
Our search results look a little different now. Source: Google.com
Search Strings
Running our string through Google gives us plenty to search through. At this point, you should be across how to create and explore a Dork of your own, but if you’re after a little more inspiration, here are a few search strings that you might also find fun to play with.
This one should help uncover login pages
site:example.com intitle:"login" OR intitle:"admin" OR inurl:"login"
While this one should look for old backup files
site:example.com filetype:sql OR filetype:bak
And this one is useful for searching public directories that might be misconfigured
site:example.com inurl:"/backup/" OR inurl:"/old/" OR inurl:"/temp/"
Don’t Forget Your Ethics
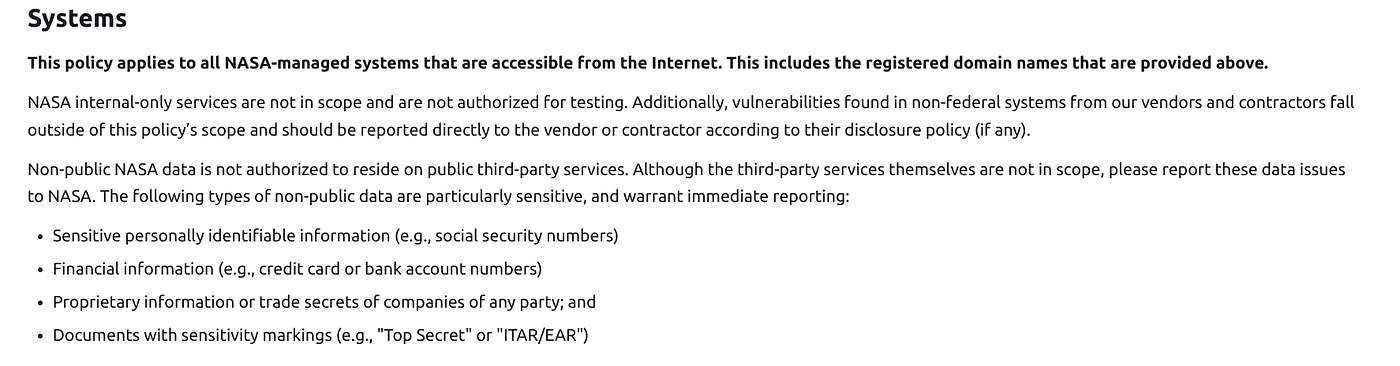
Bug Bounty programs can be great for learners as it gives you an open environment in which you can test your skills in a way that won’t see the local police knocking on your door. NASA in particular, offers a concept called “Safe Harbour” where research carried out in good faith will not land you in hot water should you make an error or face problems.
However, it’s worth mentioning that this comes with some strict limitations, which tend to focus on things like Personal & Financial information and information that might be subject to ITAR or Top Secret ratings. These also warrant immediate reporting (which typically means a bounty payout for your good self).
If you do uncover sensitive files, you should take appropriate action to ensure data on your end is properly secured while the issue is resolved. While you’d like to think that most companies have their cyber affairs in order, the reality is that there are still plenty of things in the wild that shouldn’t be. So, persistent dorkers can have some good fun while getting paid for it.
Dorking is the best and easiest way to upgrade your Google-Fu to pro level. Are you going to give it a shot?
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Space Shuttles
- Shodan: A Map of the Internet
✉️ Want more content like this? Sign up for email updates






















































