Up Your Search: Dorking For Beginners
The best things start from simple foundations and OSINT is no different.
We strive to provide informative articles, however, it is important for users to ensure their research is both ethical and responsible. Additionally, it is your responsibility to ensure you’re compliant with all applicable laws and regulations for your region. The information provided in this article is intended for educational purposes only.
For a lot of people, once we get past a certain point it’s easy to forget the concept of walking before you run. Translating this from an infosec perspective means that while there are plenty of cool tools available to help us do our job, there are also plenty of fundamental skills that are important to grasp as well.
In today's article, we’re going to explore a technique known as Dorking. While we’ve all used Google to find targets of interest or maybe even an ex-associate or romantic partner, Google has far more OSINT potential than a lot of people realise. Understanding how these work from an analysis perspective means that we can look at ways of either automating them or adding them to our workflow.
If you’ve ever claimed to someone that your Google-fu is on point, then this article might just be for you.
What is Dorking
Essentially, Dorking involves using advanced search strings to identify and uncover information that typically wouldn’t be found via standard search queries. While it’s a reasonably simple concept to understand, it’s easy to overlook a few things in the simplicity of the statement.
The key is in the concept of uncovering information that wouldn’t typically be found by normal search queries and it’s this concept that shines in Dorking. When you consider something like Shodan, which can give us tools to identify machines on the internet or a network, Dorking allows us to uncover data using a similar concept.
For many large companies, despite having active cybersecurity and IT departments there is still a wide array of mis or badly configured systems that make it online for whatever reason. They bring with them intellectual property, personal identifying information and other sensitive data that has value to bad actors. The Google Hacking Database has plenty of useful information. Source: exploit-db.com
The Google Hacking Database has plenty of useful information. Source: exploit-db.com
If you’re new to this, it’s often hard to grasp that simply searching for information can be so damaging in certain circumstances, but in today's world, many cybersecurity incidents and data breaches remind us of this fact. It’s so common in fact, that there’s even a Google Hacking Database. Check it out if you want to really up your skills.
Search Strings
While the sky (or your imagination) can be the limit with this type of thing, for the most part simply remembering a few basic concepts will take you a long way in uncovering information.
The first is the “in url” concept. Using this string paired with a search target allows us to results linked to a specific domain. This can be front-facing or backend architecture depending on the way the target is configured.
inurl:admin ourosinttarget.com
So the above string would search for pages where “admin” is part of the target URL ourosinttarget.com potentially leading us to login pages or administrative interfaces.
We can also use dorking to search for file types that might be of interest.
filetype:pdf site:ourosinttarget.com
This string would return us PDF documents linked to our target website. What would happen if we searched with a string like “confidential” instead?
We can also target the text within a website. So, if we’re looking for a specific phrase or piece of information somewhere, then we can narrow it down using this
intext:"example phrase" site:ourosinttarget.com
In some instances, cache histories can often be found as well.
cache: ourosinttarget.com
For the most part, these are just starting points and expanding on them can be as simple or as complex as you’d like. There’s plenty of information available to help expand on this including a large range of useful tutorials that work for all competency levels.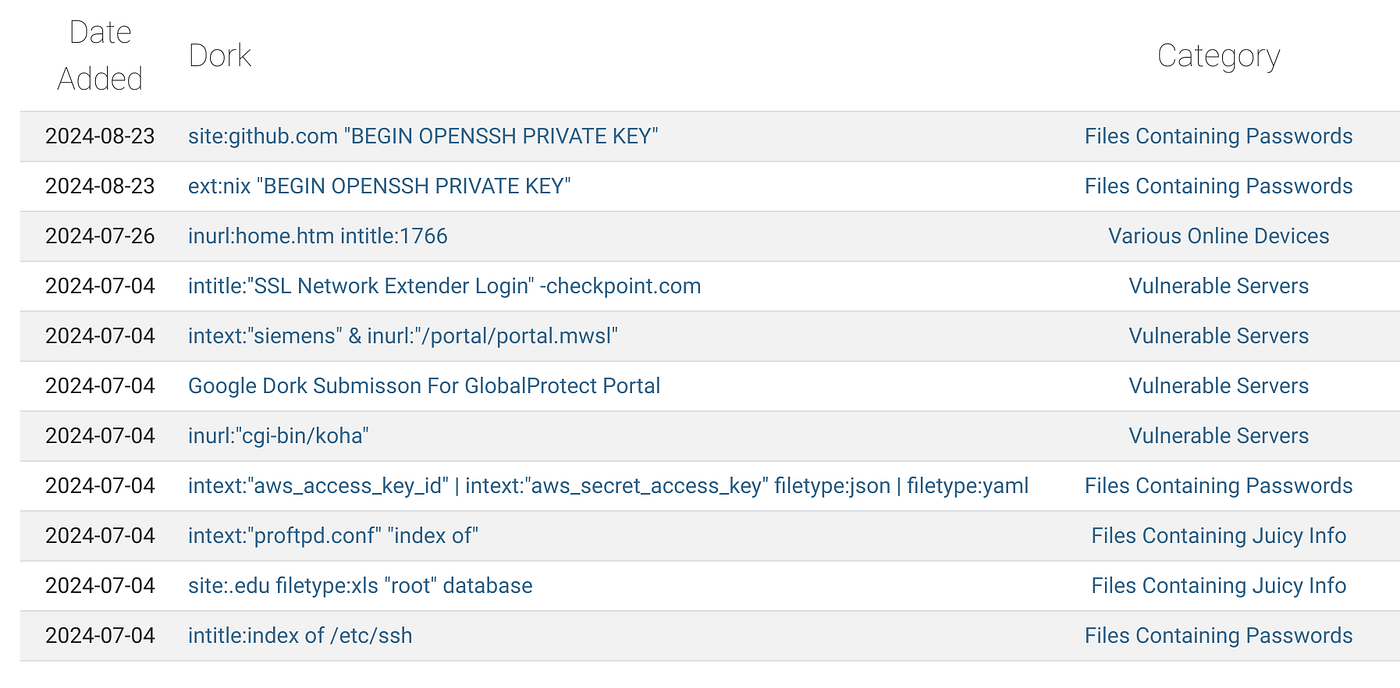 Your imagination is the limit. Source: exploit-db.com
Your imagination is the limit. Source: exploit-db.com
In Closing
While we’ve mostly focused on data in this article, there’s plenty of information to help identify systems and machines as well. This has value from both Blue & Red team perspectives as Blue teamers can find systems and information that require securing before they are exploited. Red teamers, on the other hand, can use the same information for exploitation purposes. Particularly if the machine is unpatched or vulnerable to specific CVEs.
Probably the best example we’ve seen of this in recent years came with the onset of the current full-scale invasion of Ukraine by Russian forces. One large group of cybersecurity specialists would use things like dorking to help identify vulnerable Ukrainian systems so they could be appropriately secured. While another would do the exact same to Russian systems before passing the information along so it could be exploited by Ukrainian forces.
The battle for both cyberspace and privacy has gone through some rapid developments since the integration and development of AI-based systems.
Despite this though, strategies like Dorking remind us that investing time into foundational investigative skills like good search and data analysis, leaves us much better placed to deal with some of the big data concepts that we’ll uncover in the real world.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Rocket Engines
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates