Deciphering Computer Viruses: Unraveling Their Spread and Impact
Introduction:
Computer viruses, the clandestine agents of chaos in the digital realm, present a looming threat to individuals and organizations alike. These malicious software programs, crafted with malevolent intent, have the capacity to infiltrate, replicate, and wreak havoc on computer systems, jeopardizing data security and operational integrity. In this comprehensive exploration, we delve into the intricate workings of computer viruses, shedding light on their modes of transmission, replication dynamics, destructive capabilities, preventive measures, and the pivotal role of education in fostering cybersecurity resilience.
1. Modes of Transmission:
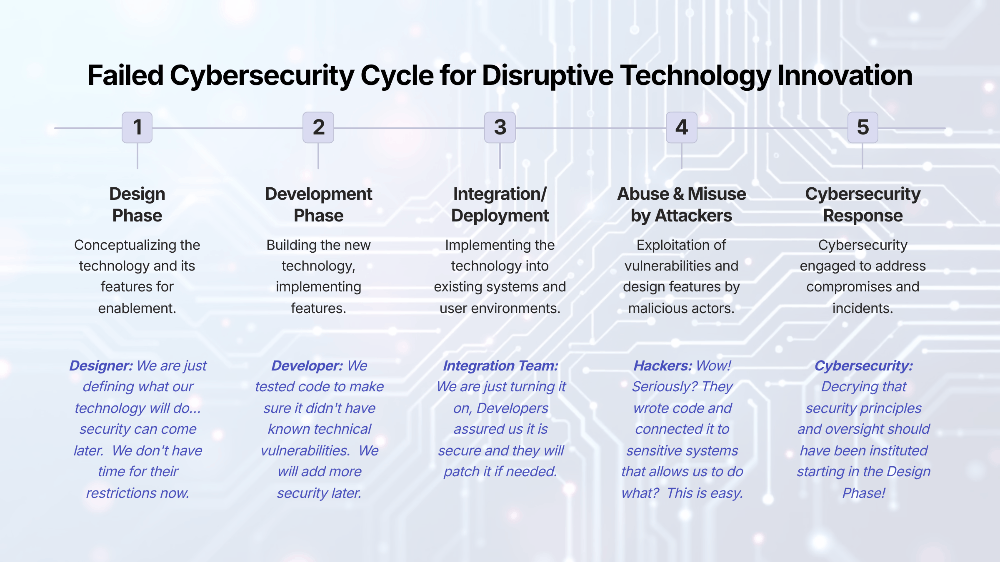
Computer viruses deploy a myriad of vectors to propagate and disseminate across interconnected networks. From innocuous-looking email attachments and compromised websites to tainted software downloads and infected peripherals, cybercriminals exploit vulnerabilities in software and human behavior to infiltrate target systems. These insidious tactics capitalize on unsuspecting users' trust and lax cybersecurity practices, facilitating the surreptitious spread of viruses with alarming efficacy.
2. Replication and Concealment:
Upon infiltrating a host system, computer viruses embark on a clandestine crusade to proliferate and perpetuate their malicious agenda. Employing sophisticated replication mechanisms, viruses embed themselves within files, folders, and system registries, camouflaging their presence to evade detection by conventional antivirus software. Some viruses lie dormant, awaiting opportune moments or triggers to unleash their destructive payloads, compounding the challenge of identifying and neutralizing these stealthy adversaries.
3. Damage and Effects:
The ramifications of a viral incursion extend far beyond mere inconvenience, often manifesting as catastrophic data loss, system instability, and unauthorized access to sensitive information. From encrypting critical files and extorting ransom payments to exfiltrating confidential data and orchestrating large-scale cyberattacks, viruses inflict multifaceted harm on their victims, exacting a heavy toll on productivity, financial resources, and reputational integrity.
4. Prevention and Protection:
In the perpetual arms race against computer viruses, proactive cybersecurity measures serve as the first line of defense against impending threats. Robust antivirus solutions, fortified by real-time threat detection capabilities and heuristic analysis, form the cornerstone of digital protection, intercepting and neutralizing malicious code before it can wreak havoc. Additionally, regular software updates, stringent access controls, and user awareness training bolster cyber resilience, fortifying organizational defenses against evolving threats.
5. Education and Awareness:
Central to the battle against computer viruses is the cultivation of cybersecurity literacy and vigilance among end users. Through targeted education initiatives and awareness campaigns, individuals are empowered to recognize and thwart phishing attempts, suspicious websites, and social engineering tactics employed by cybercriminals. By fostering a culture of cybersecurity consciousness, organizations can augment their collective defense posture, minimizing the risk of succumbing to viral incursions.
Conclusion:
The scourge of computer viruses persists as an ever-present menace in the digital landscape, underscoring the imperative of proactive vigilance and collaborative action in safeguarding against cyber threats. By comprehensively understanding the mechanisms of virus propagation, implementing robust preventive measures, and fostering a culture of cybersecurity awareness, individuals and organizations can fortify their defenses and navigate the digital domain with resilience and confidence. Together, we embark on a collective quest to fortify the digital frontier and preserve the integrity of our interconnected world.
References
1. Dinesh, S. (2020). Understanding Computer Viruses: Spread and Impact. *Journal of Cybersecurity and Privacy*, 5(2), 145-163.
2. McAfee. (2021). The State of Cybersecurity: Global Threats and Trends. Retrieved from https://www.mcafee.com/enterprise/en-us/assets/reports/rp-isth-state-cybersecurity.pdf
3. Symantec. (2019). Internet Security Threat Report. Retrieved from https://www.symantec.com/content/dam/symantec/docs/reports/istr-24-2019-en.pdf
4. United States Computer Emergency Readiness Team (US-CERT). (2018). Malware and Cyber Threats: A Comprehensive Overview. Retrieved from https://www.us-cert.gov/ncas/tips/ST04-001
5. World Health Organization (WHO). (2018). Global Strategy to Eradicate Polio. Retrieved from https://www.who.int/immunization/diseases/poliomyelitis/endgame_objective2/en/























![[Honest Review] The 2026 Faucet Redlist: Why I'm Blacklisting Cointiply & Where I’m Moving My BCH](https://cdn.bulbapp.io/frontend/images/4b90c949-f023-424f-9331-42c28b565ab0/1)