Information Risk Management: Safeguarding Your Organization's Valuable Assets
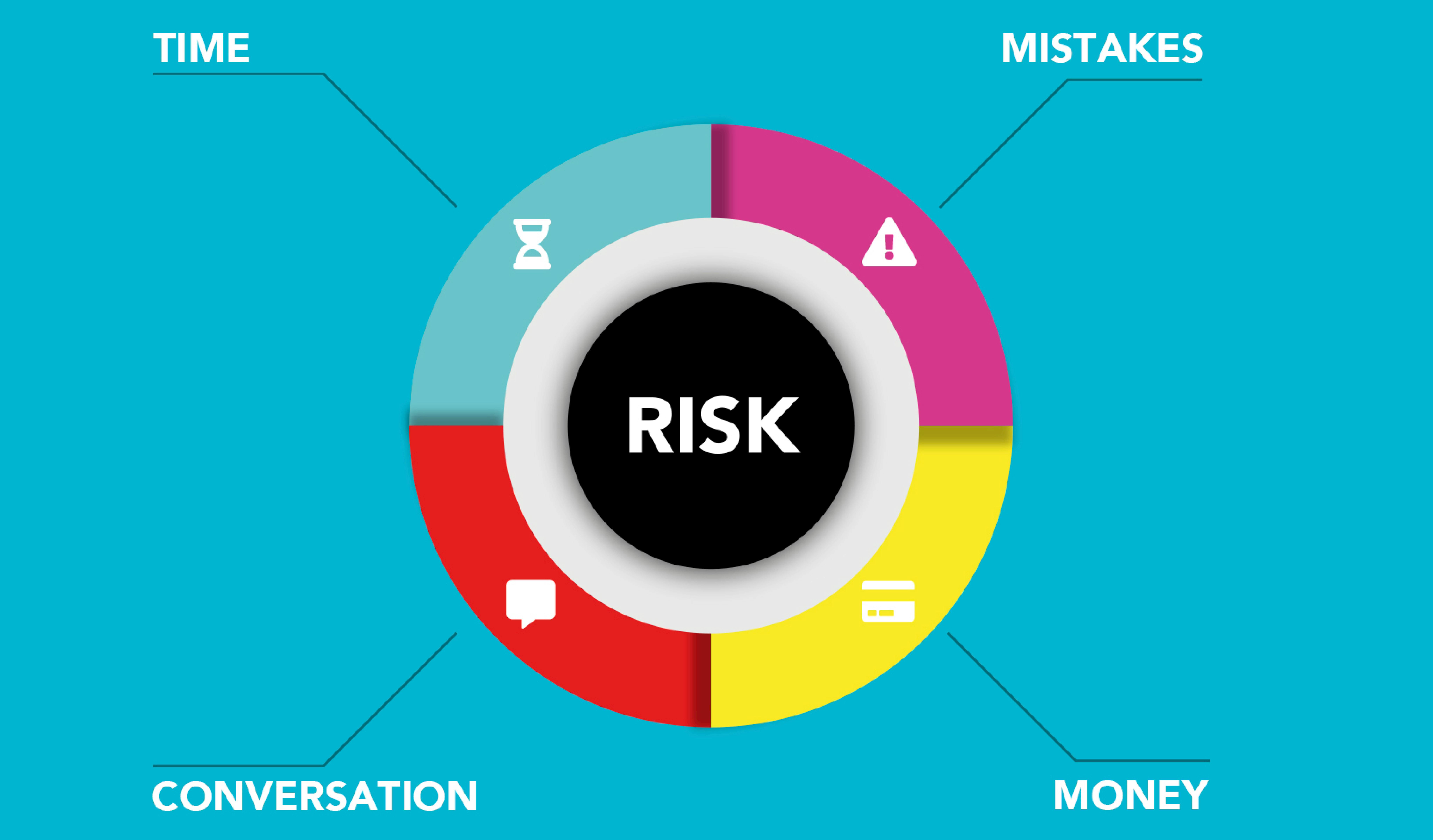
Image Source: Pexels
In today's digital era, where information is the lifeblood of businesses, the importance of information risk management cannot be overstated. Companies are constantly grappling with the challenge of protecting their sensitive data from cyber threats, regulatory non-compliance, and other potential risks. At [Brand], we understand the critical role that information risk management plays in safeguarding your organization's reputation and ensuring business continuity. Our expert team is dedicated to helping you identify, assess, and mitigate the risks associated with your valuable information assets.
What is Information Risk Management?
Information risk management is the process of identifying, assessing, and mitigating risks to an organization's information assets. It involves evaluating the potential impact of risks and implementing strategies to minimize them. By effectively managing information risks, organizations can protect their data, maintain regulatory compliance, and safeguard their reputation.
Importance of Information Risk Management
The importance of information risk management cannot be emphasized enough in today's interconnected world. Organizations face numerous threats to their sensitive data, including cyberattacks, data breaches, and insider threats. The consequences of these risks can be severe, ranging from financial losses to damage to brand reputation. By implementing robust information risk management practices, organizations can stay ahead of potential threats and minimize their impact on the business.
Common Types of Information Risks
Information risks come in various forms, and understanding the different types is crucial for effective risk management. Some common types of information risks include:
- Cybersecurity Risks: These risks include unauthorized access, malware infections, phishing attacks, and other cyber threats that can compromise the confidentiality, integrity, and availability of information.
- Data Privacy Risks: With the increasing focus on data privacy regulations, organizations must address risks related to the collection, storage, and processing of personal data. Failure to comply with privacy regulations can result in significant penalties and damage to an organization's reputation.
- Operational Risks: Operational risks encompass risks arising from internal processes, human errors, system failures, and other operational factors. These risks can disrupt business operations and lead to data loss or unauthorized access.
- Compliance Risks: Regulatory non-compliance can have serious consequences for organizations. Failure to comply with industry-specific regulations or data protection laws can result in legal penalties, reputational damage, and loss of customer trust.
Steps in the Information Risk Management Process
Effective information risk management involves a systematic approach to identify, assess, and mitigate risks. The following steps outline the information risk management process:
1. Identifying and Assessing Information Risks
The first step in the information risk management process is to identify and assess potential risks. This involves conducting a comprehensive assessment of the organization's information assets, systems, and processes. By understanding the vulnerabilities and threats, organizations can prioritize their risk management efforts.
2. Mitigating and Controlling Information Risks
Once the risks have been identified and assessed, organizations need to implement measures to mitigate and control the risks. This may involve implementing technical controls, such as firewalls and encryption, as well as implementing policies and procedures to govern the use and protection of information assets.
3. Implementing Information Risk Management Policies and Procedures
To ensure consistent and effective risk management, organizations should establish clear policies and procedures. These policies and procedures should outline the responsibilities of employees, define acceptable use of information assets, and provide guidelines for incident response and reporting.
4. Training and Educating Employees on Information Risk Management
Employees play a crucial role in information risk management. It is essential to provide comprehensive training and education to employees on the importance of information security, their responsibilities, and best practices for protecting sensitive data. Regular training sessions and awareness campaigns can help create a culture of security within the organization.
5. Monitoring and Evaluating Information Risk Management Efforts
Information risk management is an ongoing process that requires continuous monitoring and evaluation. Regular audits and risk assessments can help identify any emerging risks or gaps in the risk management strategy. By monitoring and evaluating information risk management efforts, organizations can adapt and improve their approach to stay ahead of evolving threats.
Conclusion: The Role of Information Risk Management in Protecting Businesses and Their Data
In today's digital landscape, information risk management is an essential aspect of protecting businesses and their valuable data. By implementing effective risk management strategies, organizations can minimize the impact of potential threats, maintain regulatory compliance, and safeguard their reputation. At [Brand], we recognize the importance of information risk management and offer comprehensive solutions to help organizations navigate the complex world of information security effectively.
As technology continues to advance and new risks emerge, organizations must stay vigilant and proactive in managing information risks. By partnering with [Brand], you can ensure that your organization is equipped with the expertise and tools necessary to protect your valuable information assets and maintain a secure environment for your business to thrive.
Contact us today to learn more about our information risk management services and how we can help safeguard your organization against the ever-evolving landscape of information risks.
Note: The above article is for informational purposes only and should not be considered as legal or professional advice. Organizations should consult with legal and cybersecurity professionals to develop a tailored information risk management strategy.




























































