The Principles of Cryptology: Safeguarding Information in the Digital Age
Introduction:
Cryptology, the study of securing information through cryptography and cryptanalysis, plays a pivotal role in ensuring the confidentiality, integrity, and authenticity of data in the digital era. As technology advances, the need for robust cryptographic principles becomes increasingly crucial to protect sensitive information from unauthorized access and malicious activities. In this comprehensive article, we will delve into the fundamental principles of cryptology, exploring its core concepts and applications.
Cryptography: The Art of Concealing Information
Cryptography, a key component of cryptology, is the practice of transforming information into an unintelligible form, making it secure from unauthorized access. The primary objective is to enable secure communication and data storage. Several foundational principles underpin cryptography:
a. Encryption: The process of converting plaintext (readable data) into ciphertext (unreadable data) using algorithms. Encryption ensures that even if unauthorized individuals gain access to the data, they cannot comprehend its meaning without the appropriate decryption key.
b. Decryption: The reverse process of encryption, where ciphertext is converted back to plaintext using the decryption key. Decryption is performed by authorized parties to access the original information.
c. Key Management: The secure generation, distribution, and storage of cryptographic keys are critical to the effectiveness of cryptographic systems. Keys serve as the basis for both encryption and decryption processes.
Key Principles in Cryptographic Algorithms:
a. Symmetric Cryptography: In this approach, a single key is used for both encryption and decryption. Algorithms like Advanced Encryption Standard (AES) employ symmetric cryptography, offering efficient and fast data protection.
b. Asymmetric Cryptography: Also known as public-key cryptography, this method involves a pair of keys – public and private. Data encrypted with one key can only be decrypted with the other. Asymmetric cryptography addresses key distribution challenges and facilitates secure communication.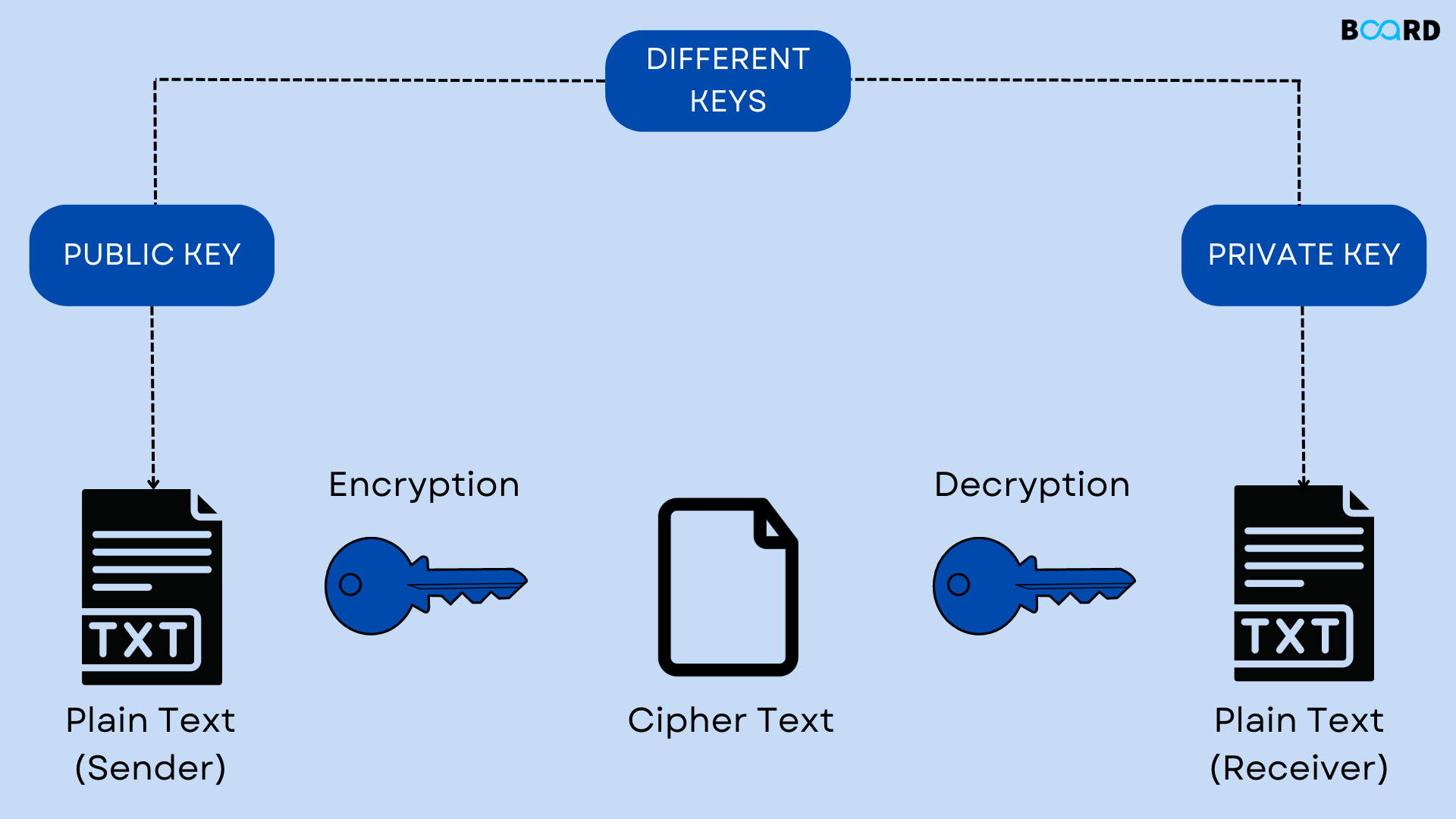 c. Hash Functions: These are one-way mathematical functions that generate a fixed-size output (hash) from variable-size input. Hash functions are integral for ensuring data integrity and creating digital signatures.
c. Hash Functions: These are one-way mathematical functions that generate a fixed-size output (hash) from variable-size input. Hash functions are integral for ensuring data integrity and creating digital signatures.
Cryptanalysis: Unraveling the Secrets
Cryptanalysis, the counterpart to cryptography, involves analyzing and breaking cryptographic systems. While cryptographers strive to create robust algorithms, cryptanalysts seek vulnerabilities and weaknesses in these systems. Common techniques include: a. Brute Force Attacks: Attempting all possible keys until the correct one is found. Strong key lengths and complexity help mitigate the risk of brute force attacks.
a. Brute Force Attacks: Attempting all possible keys until the correct one is found. Strong key lengths and complexity help mitigate the risk of brute force attacks.
b. Frequency Analysis: Examining the frequency of characters in ciphertext to deduce patterns and potentially reveal the original message.
c. Differential Cryptanalysis: Analyzing the differences between pairs of plaintext-ciphertext to uncover weaknesses in the encryption algorithm.
Practical Applications of Cryptology:
- a. Secure Communication: Cryptology ensures the confidentiality of sensitive information during transmission over networks, safeguarding against eavesdropping and interception.
- b. Data Integrity: Cryptographic hash functions are employed to verify the integrity of transmitted or stored data, protecting against tampering and corruption.
- c. Digital Signatures: Asymmetric cryptography enables the creation of digital signatures, providing a means to authenticate the origin and integrity of digital messages or documents.
Blockchain technology has a wide range of applications across various industries due to its decentralized, transparent, and secure nature. Some key usage areas of blockchain include:
Cryptocurrencies:
- Bitcoin (BTC): Blockchain's initial application was as the underlying technology for Bitcoin, a decentralized digital currency.
- Altcoins: Many other cryptocurrencies (e.g., Ethereum, Ripple, Litecoin) utilize blockchain for secure and transparent transactions.
Smart Contracts:
- Blockchain platforms like Ethereum allow the creation of smart contracts, self-executing contracts with the terms directly written into code. They automate and enforce the execution of contractual agreements, reducing the need for intermediaries.
Supply Chain Management:
- Blockchain can improve transparency and traceability in supply chains. It allows stakeholders to track the production, shipment, and delivery of products in real-time, reducing fraud and errors.
Identity Management:
- Blockchain can be used for secure and decentralized identity management. Individuals have more control over their personal information, and it reduces the risk of identity theft.
Voting Systems:
- Blockchain can enhance the integrity of voting systems by providing a tamper-resistant and transparent ledger. It helps prevent fraud and ensures the accuracy of election results.
Financial Services:
- Cross-Border Payments: Blockchain can streamline cross-border transactions by providing a more efficient and cost-effective alternative to traditional banking systems.
- Smart Contracts in Finance: Smart contracts are used in financial applications, such as lending, insurance, and derivatives, to automate processes and reduce the need for intermediaries.
Healthcare:
- Blockchain can improve the security and interoperability of healthcare data. Patients can have more control over their medical records, and healthcare providers can access accurate and up-to-date information.
Real Estate:
- Blockchain simplifies property transactions by providing a transparent and immutable record of ownership. It reduces the need for intermediaries, making the process more efficient.
Intellectual Property and Royalties:
- Artists and content creators can use blockchain to manage intellectual property rights and receive fair compensation through transparent and automated royalty systems.
Energy Trading:
- Blockchain facilitates peer-to-peer energy trading in decentralized energy systems. Consumers can directly buy and sell excess energy without the need for intermediaries.
Legal and Notary Services:
- Blockchain can be used to create transparent and tamper-proof records in legal and notary services, reducing the risk of fraud and disputes.
Gaming:
- Blockchain is used in gaming to provide secure and transparent in-game transactions, ownership of virtual assets, and provably fair gaming experiences.
These are just a few examples, and the potential applications of blockchain technology continue to expand as the technology matures and new use cases are explored.
Conclusion:
In conclusion, the principles of cryptology form the cornerstone of modern information security. By understanding and implementing robust cryptographic techniques, individuals and organizations can navigate the digital landscape with confidence, ensuring the protection of sensitive data against evolving threats. As technology continues to advance, the role of cryptology in securing our digital future remains more critical than ever.




































































