LayerZero V2 — Simplified
In the ever-evolving blockchain ecosystem, one challenge persists: blockchains can’t communicate directly. Each operates like its own island, isolated and disconnected. If I had a penny for every time someone said that… Bridges and cross-chain protocols have tried to fill the gap, but they’re often centralized, complex, and limiting. Enter LayerZero — a protocol that breaks down these walls, creating an open highway for information and assets to flow freely across blockchains.
LayerZero is often compared to TCP/IP, the communication protocol powering the Internet, positioning itself as a universal translator that allows different blockchains to communicate securely and trustlessly. Imagine using your assets and applications across multiple blockchains as easily as sending an email across the Internet. This is the future LayerZero envisions, with the potential to revolutionize DeFi, NFTs, and beyond.
The Future — Omnichain Interoperability
At its core, LayerZero is all about achieving unified data and information sharing across different blockchains — an ambitious level of interoperability.
But why is that important?
From a user’s perspective, interacting with multiple chains can be a headache. Think about it: users are expected to navigate different blockchains, handle various gas tokens, and juggle features and latencies. It’s complex, and the more blockchains they interact with, the more cumbersome the experience becomes.
From a developer’s perspective, the challenge is just as daunting. Tapping into the unique strengths of multiple blockchains to build seamless apps requires weaving together different systems, each with its own set of complexities. Abstracting all of this into a smooth user experience isn’t easy.
And then there’s the question of composability. A protocol on one chain might not easily translate to another. For DeFi and Web3 apps to scale, these need to work fluidly across chains rather than remain fragmented. With over 100 million blockchain users expected in the coming years, creating a seamless user experience is crucial, and omnichain interoperability is essential to achieving it.
So, What Is LayerZero doing?
LayerZero is a leading omnichain interoperability protocol. At its core, it’s a generic messaging primitive — a framework that enables seamless communication between smart contracts on different blockchains. By allowing arbitrary contract invocation across chains, LayerZero eliminates the boundaries that once kept blockchains isolated, empowering developers to create truly omnichain applications.
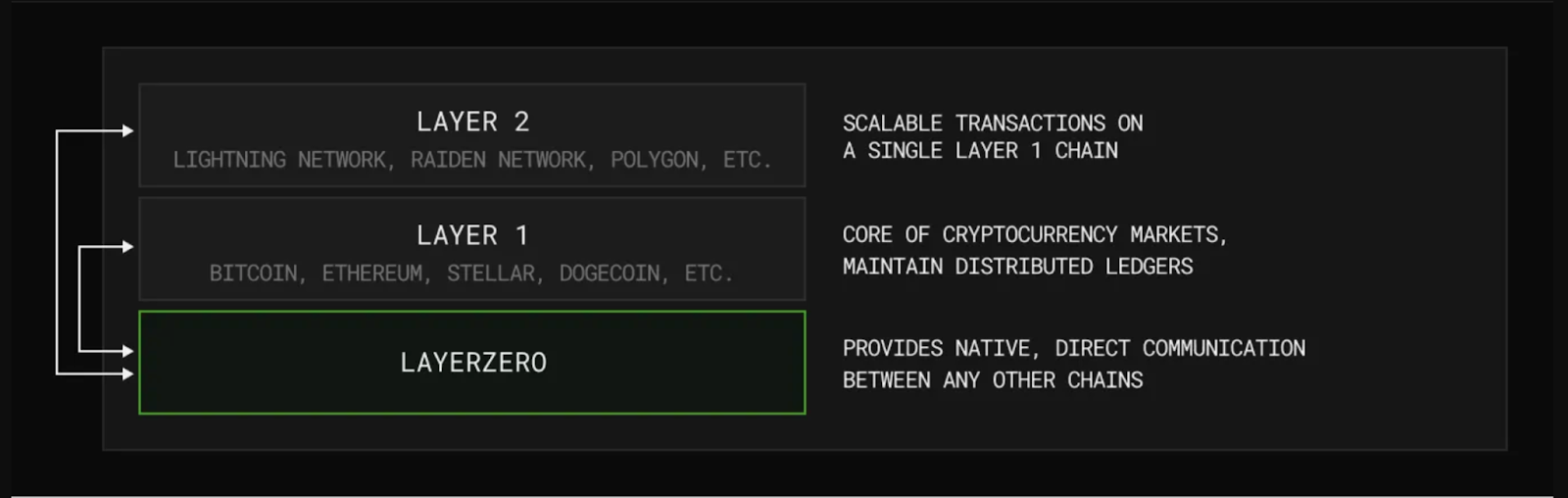
This won’t be a technical deep-dive but a straightforward breakdown to give you an overview of how it works.
LayerZero Architecture- What was
LayerZero V1
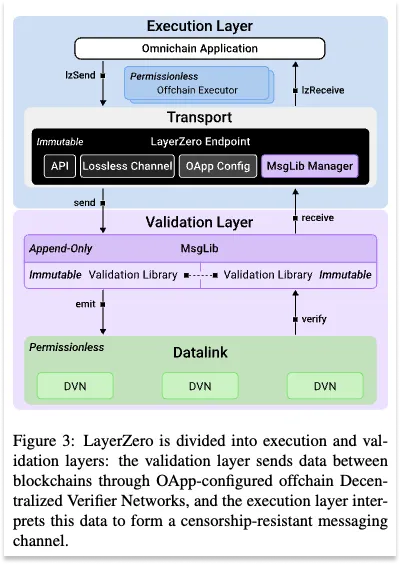
To get a handle on LayerZero’s architecture, we first need to understand its key components. At a high level, LayerZero consists of endpoints, message libraries, oracles, and relayers, each playing a distinct role in making cross-chain communication possible.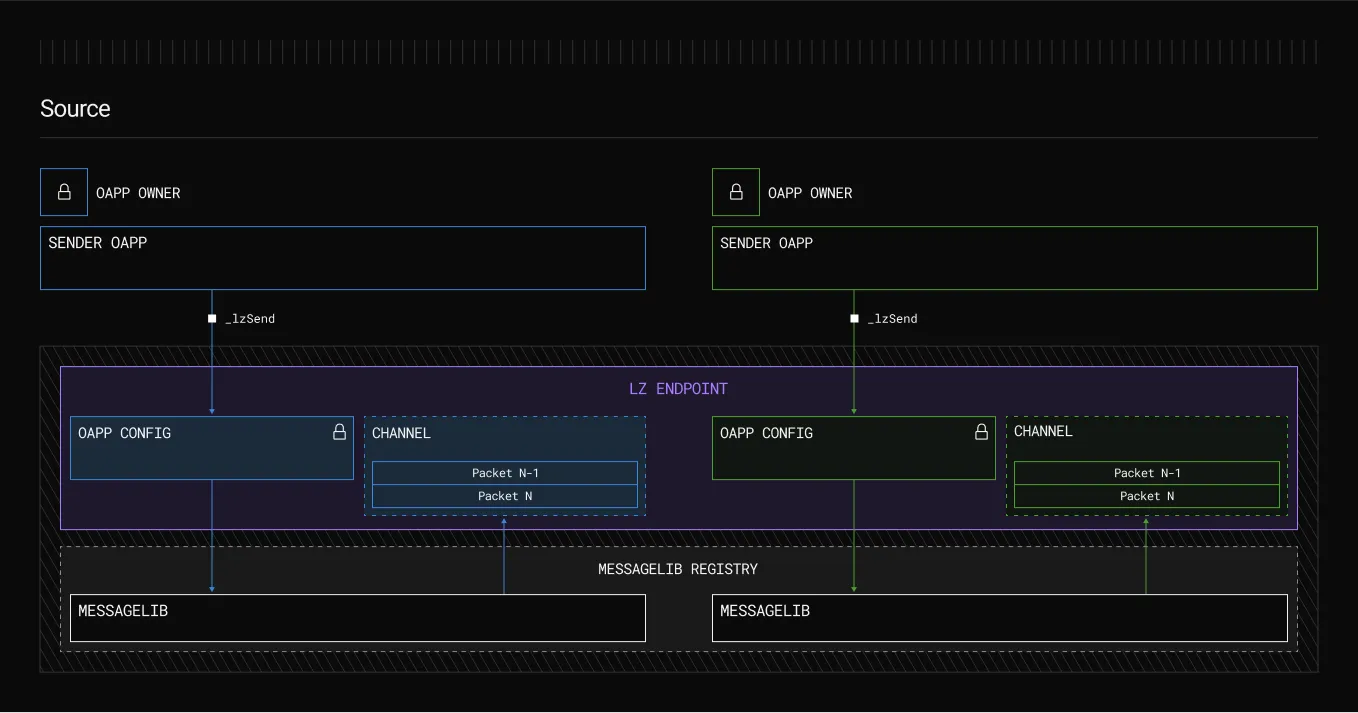
At the core of LayerZero’s architecture are endpoints. Each blockchain connecting to LayerZero hosts an endpoint — a smart contract communicating with LayerZero’s protocol.
Think of endpoints as the entry and exit points on different blockchains. They are the messengers that pass along instructions and data, enabling communication between disparate blockchains.
Message Libraries (Message Libs)
Each Endpoint has a Message Library attached, which manages how messages are sent and verified between different blockchains.
MessageLibs are add-ons that stay permanent once attached, allowing LayerZero to introduce updates without removing old MessageLibs. Developers can still choose whether to use the older or newer MessageLibs, just like apps can stick with older versions of software if they prefer.
Relayers and Oracles: The Off-Chain Components
While endpoints handle on-chain communication, oracles and relayers handle off-chain verification, critical for secure cross-chain transactions. Oracles retrieve essential data, like block headers, while relayers independently verify this data by providing proof of authenticity. This two-step verification prevents tampering, as both entities would need to collude to compromise a message.
Relayers and Oracles: Clearing Up the Misnomer
In LayerZero, oracles aren’t involved in tasks like fetching price data or connecting to external systems. Their sole responsibility is retrieving essential transaction details from the source chain. When a user or smart contract initiates a transaction, LayerZero’s oracle securely fetches and forwards this transaction data to the destination chain. However, the oracle doesn’t operate alone — it’s just one part of the verification process.
Relayers, in contrast, are responsible for receiving and submitting transaction proof, essentially verifying that the transaction happened as intended. Rather than just relaying messages, they independently confirm the integrity of the message as it moves across chains. This dual-verification setup, where the oracle delivers the data and the relayer verifies its accuracy, is key to ensuring security.
Now, let’s patch it all together
Here’s how verification works in LayerZero:
- The oracle fetches data from the source chain, like a transaction or event, and delivers it to the destination chain.
- Separately, the relayer sends the cryptographic proof that the transaction data (delivered by the oracle) is valid.
- Once both the oracle’s data and the relayer’s proof arrive at the destination chain, they are compared by the LayerZero endpoint (smart contract) on the destination chain.
The LayerZero endpoint checks:
- If the data from the oracle is consistent with the transaction’s cryptographic proof provided by the relayer.
- If both the oracle and relayer agree on the validity of the transaction, the message is accepted and executed on the destination chain.
While promising in theory, it didn’t quite play out as expected in practice.
In LayerZero V1, oracles and relayers were intended to be independent, decentralized validators to ensure secure and trustless cross-chain communication.
In theory, any entity could run a relayer, allowing for flexibility and decentralization. However, in practice, almost no one built it. As a result, most applications defaulted to using LayerZero Labs’ relayer and trusted oracles like Chainlink or Google Cloud.
Running a relayer required significant resources, including handling billions of RPC calls per month, managing real-time pricing, and ensuring secure execution. This complexity created a chokepoint: if LayerZero Labs’ relayer went down, the entire system could experience downtime. This operational risk compromised the trustless nature of the protocol, prompting the need for a more robust solution — leading to V2’s Decentralized Verifier Networks (DVNs).
LayerZero V2
What remained?
The underlying infrastructure remains: immutable smart contracts, or endpoints, deployed on each chain LayerZero supports with MessageLibs that are append-only. These layers were built as the core foundation — unchangeable.
What changed?
In V1, the relayer was responsible for both verification and execution. This setup created a single point of potential failure; if the relayer went down, transactions couldn’t be processed, leading to bottlenecks. While this issue wasn’t realized in V1, the structure still presented a theoretical risk. In V2, however, execution is permissionless and operates outside the protocol’s verification process.
Before going further, let’s introduce two new terms: DVNs (Decentralized Verifier Networks) and Executors.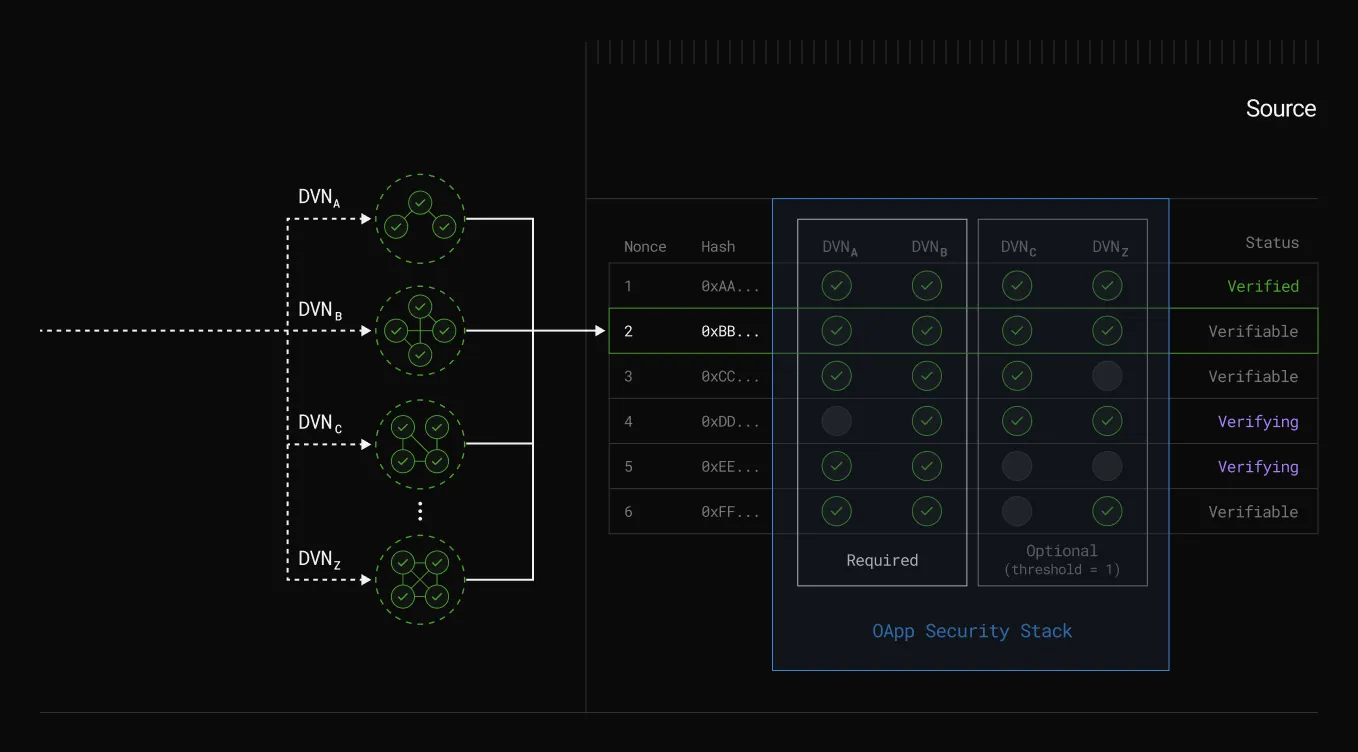
Put simply, DVNs are entities responsible for verifying messages sent across chains by apps using LayerZero. Any entity capable of cross-chain data packet verification — including native bridges, third-party bridges, middle chains, and oracles — can register as a DVN in V2. Additionally, apps can choose a unique combination of DVNs (explained below).
Executors
The Executor in LayerZero handles transaction execution on the destination chain, simplifying the process for end-users by taking care of gas fees. It provides a quote for gas fees on the source chain in the local token and then executes the transaction automatically on the destination chain. Similar to selecting a DVN set, applications can configure which Executor/Executors they want to use. LayerZero Labs offers a default Executor, but applications can choose or develop their own. Alternatively, applications can choose to operate without an Executor, allowing end-users to manually trigger transactions via LayerZero Scan. This setup reduces technical requirements, enhances competition, and improves “liveness.” If one Executor fails, another can take over seamlessly, keeping transactions moving without interruption.
A Universal Toolkit for Devs
V2 ensures dev focus more on building unique features and less on adapting code for cross-chain compatibility
- Unified semantics enables a token or app built with LayerZero to behave the same way on all supported blockchains.
- Developers don’t need to rewrite or adapt code each time they want their app to work on a new blockchain.
An Immutable Core with Configurable Layers
Applications on LayerZero have the flexibility to select a unique configuration of DVNs, Executors, and other security settings tailored to their specific needs. This choice forms an application’s unique Security Stack.
V2 is designed to let applications control their security. Rather than enforcing a single verification method, it allows developers to choose the approach that best fits their needs. Thus, adaptability enables security to evolve alongside advancements in research and project growth, without sacrificing long-term security.
This contrasts with most messaging protocols, which often use a shared security model — typically a fixed validator set or middlechain — for all projects. The one-size-fits-all model often leaves projects overpaying for unnecessary security or underpaying for critical protection.
Custom Quorum for Security (X of Y of N)
With the “X of Y of N” model, an application can establish specific approval rules for message validity.
For example, “1 of 3 of 5” means:
- 3 out of 5 DVNs must approve.
- One of these must be a specific DVN, which could even be the app’s own verifier.
This way, the app has the final say on messages, adding a strong security layer against any potential malicious activity.
Case in point
Let’s say, App X is a gaming platform (NFTs<$1) handling thousands of cross-chain transactions per second but isn’t as concerned with ultra-high security for each transaction. It can opt for a 3 of 5 threshold, requiring just 3 out of 5 verifiers to confirm a message. To balance cost and speed, it selects verification nodes from reputable services like AWS, Google Cloud, and Chainlink, plus a few of its own data centers, ensuring adequate security without overpaying for excessive validation.
App Y is a DEX processing high-value cross-chain asset transfers that prioritizes security and redundancy. It can go for a 10 of 15 threshold, meaning it needs 10 verifiers from a pool of 15 to approve every message. It can choose validators like Google Cloud, IBM’s Blockchain Platform, Chainlink, and include competing solutions like Wormhole or Axelar for additional redundancy.
Thus, LayerZero’s Security Stacks eliminate vendor lock-in by giving developers the freedom to choose and customize their security setup. This means apps can adjust, combine, or update verification methods as their needs change, ensuring security that fits their specific requirements.
So coming back to what changed, V2 separates execution from verification. Validation and security remain flexible with DVNs taking over oracles, while Executors replace relayers for efficient execution.
- DVNs ensure message legitimacy, while
- Executors handle delivery independently, without being tied to verification.
Additionally, V2 enables developers the opportunity to execute transactions in order or in whatever way achieves maximum throughput.
By separating these roles, LayerZero ensures messages can’t be tampered with (censorship-resistant), and will always be delivered (maintaining liveness), making it a secure, unstoppable way to connect blockchains.
Conclusion
LayerZero V2’s modularity — through customizable DVNs and Executors — gives developers unmatched control over security and operability, positioning it as a vital infrastructure, and pushing DeFi, NFTs, and Web3 toward a more integrated future.
In truth, this article merely scratches the surface of what LayerZero V2 has to offer. There’s a wealth of groundbreaking technology and innovation in this space that deserves deeper exploration, far beyond what we could cover here. Stay tuned for our next piece.
If you find this helpful, please support us by subscribing and following.
Everythingblockchain — Freethinkers, Writers ✍, Blockchain explorers 🔭
In pursuit of simplifying the different blocks of the chain metaverse
Socials
Twitter, Medium, Youtube, Reddit, Substack
The information provided through this work is intended solely for educational purposes and must not be treated as investment advice. Any lapses in presenting any of the information correctly are ours alone. We disclaim any liability associated with the use of this content.



























