5 Modern Day Computer Viruses
We usually look at historical viruses, today is something different
In our earlier historical articles about computer worms and viruses we’ve taken a historical approach, highlighting variants that were often built by students, researchers or people that were’t often driven by malice. Today’s article will be slightly different as we’ll be looking at modern viruses that have been extremely destructive and were used purely for malicious purposes of some kind. By the end of the article you may also notice a pattern, that helps indicate the changing times we now live in. 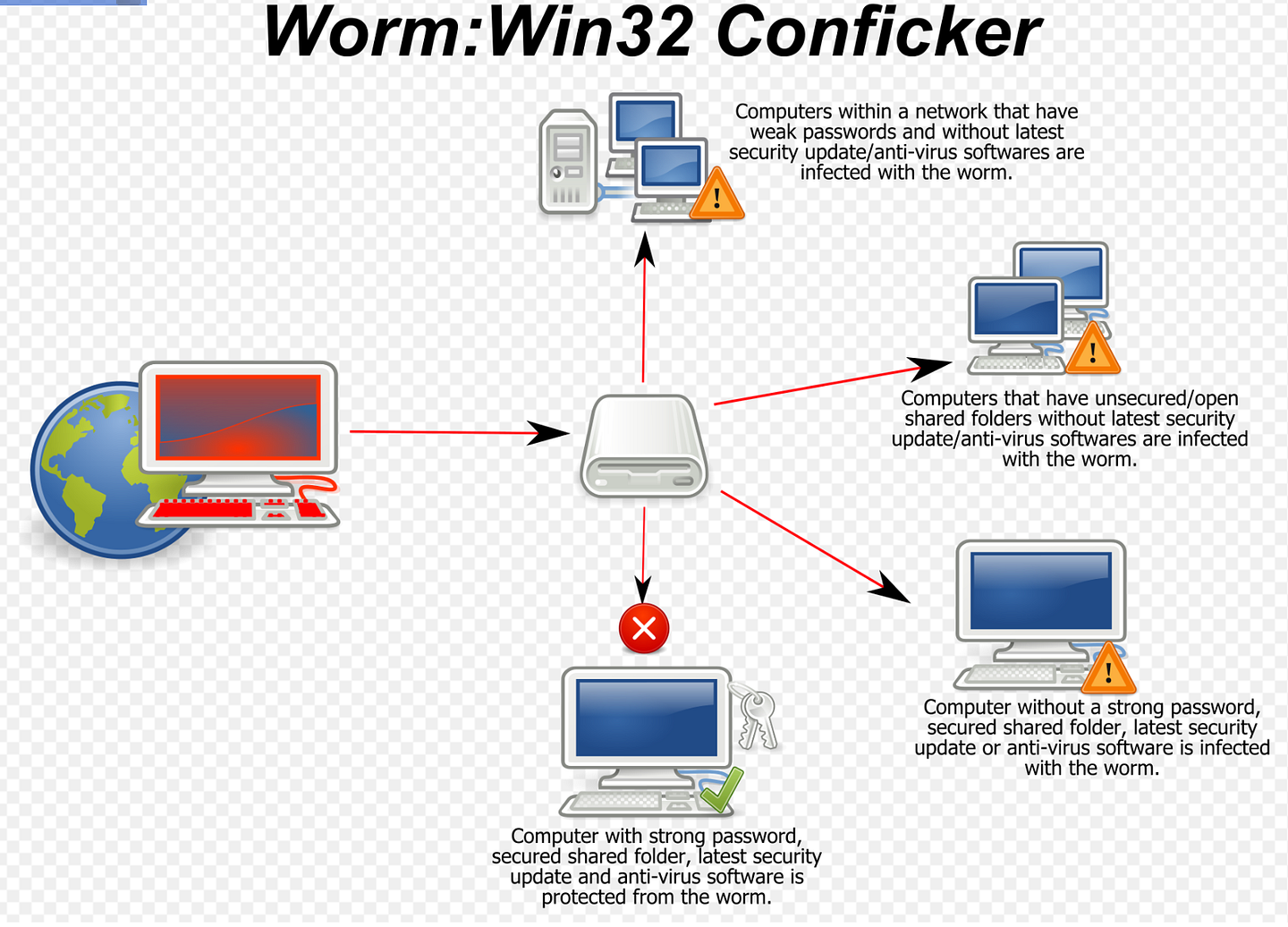
Conficker, (2008, Ukraine)
First appearing in 2008, and targeting Windows machines conficker was a modern computer worm that propagated rapidly. A play on the name configure f**ker, conficker saw 5 different variants post release and was noteworthy due to the impact it had on services and government operations. Conficker grounded French Navy airplanes, wrecked chaos on Royal Navy ships and bases and the German Bundeswehr also suffered a small infection as well.
Governments in Europe were also affected, with Britain’s Manchester council incurring over a million pounds worth of damage. Later, the Greater Manchester Police computer network also suffered damage, being brought down by the virus.
While little details are around with regards to the creators, there was a number of people charged in relation to Conficker, with some serving prison sentences.
Conficker makes our list due to the way it propagated and spread, using both Top Level Domains and Ad-Hoc peer to peer networks to spread effectively. 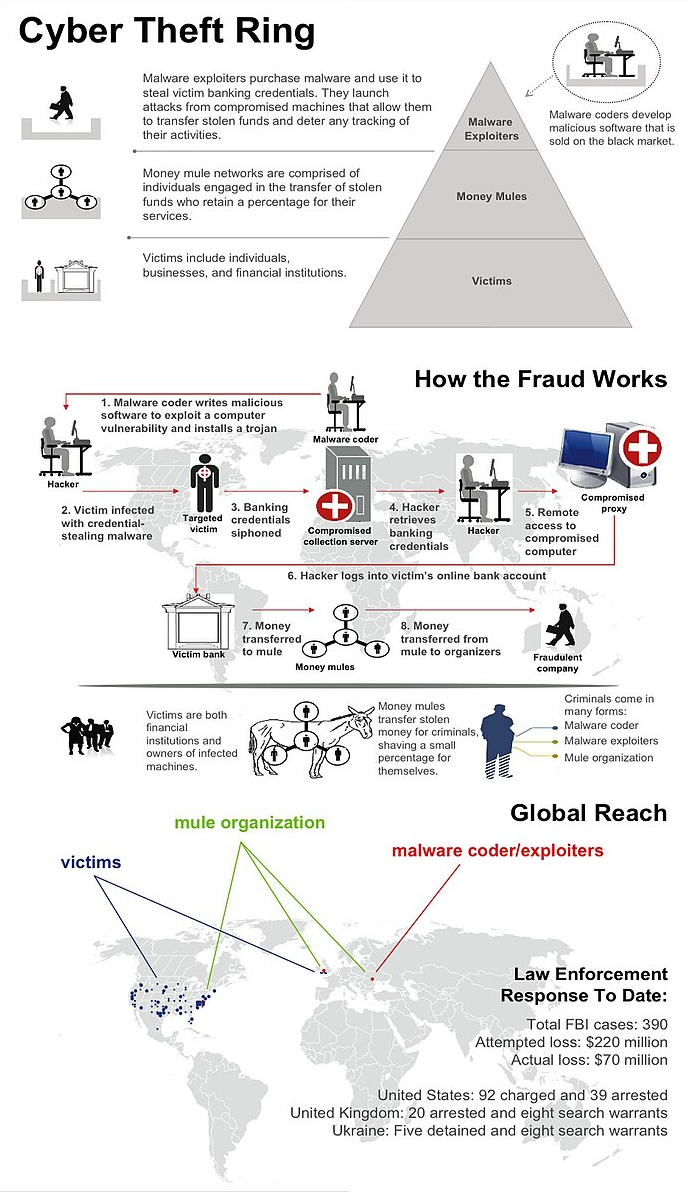
Zeus, AKA Zbot, (2007, Algeria)
Known for it’s sophistication, Zeus appeared in Europe some time in late 2007. A Trojan Horse that targeted Windows based systems, Zeus was extremely destructive and spread rapidly after it’s first sighting in the wild.
Known for being particularly stealthy and difficult to detect, Zeus was responsible for one of the largest botnets in the world at one time and was known for it’s utility by providing key logging, form grabbing and ransomware attacks just to name a few.
The attacks began ramping up into 2010, with the virus giving hackers victim bank information which would then be logged into and drained. Using a sophisticated laundering system, the money was distributed via networks within Europe where “mules” were paid to move it around in an attempt to make it untraceable.
Despite these attempts, more than 100 people were arrested in relation to the laundering, with at least 70 million dollars worth of stolen funds tracked by authorities.
In 2013, a hacker known as Bx1 was arrested in Thailand and charged with various crimes in relation to Zeus. Zeus makes our list due to it’s stealthy habits and the large amount of financial damage that the virus was responsible for. 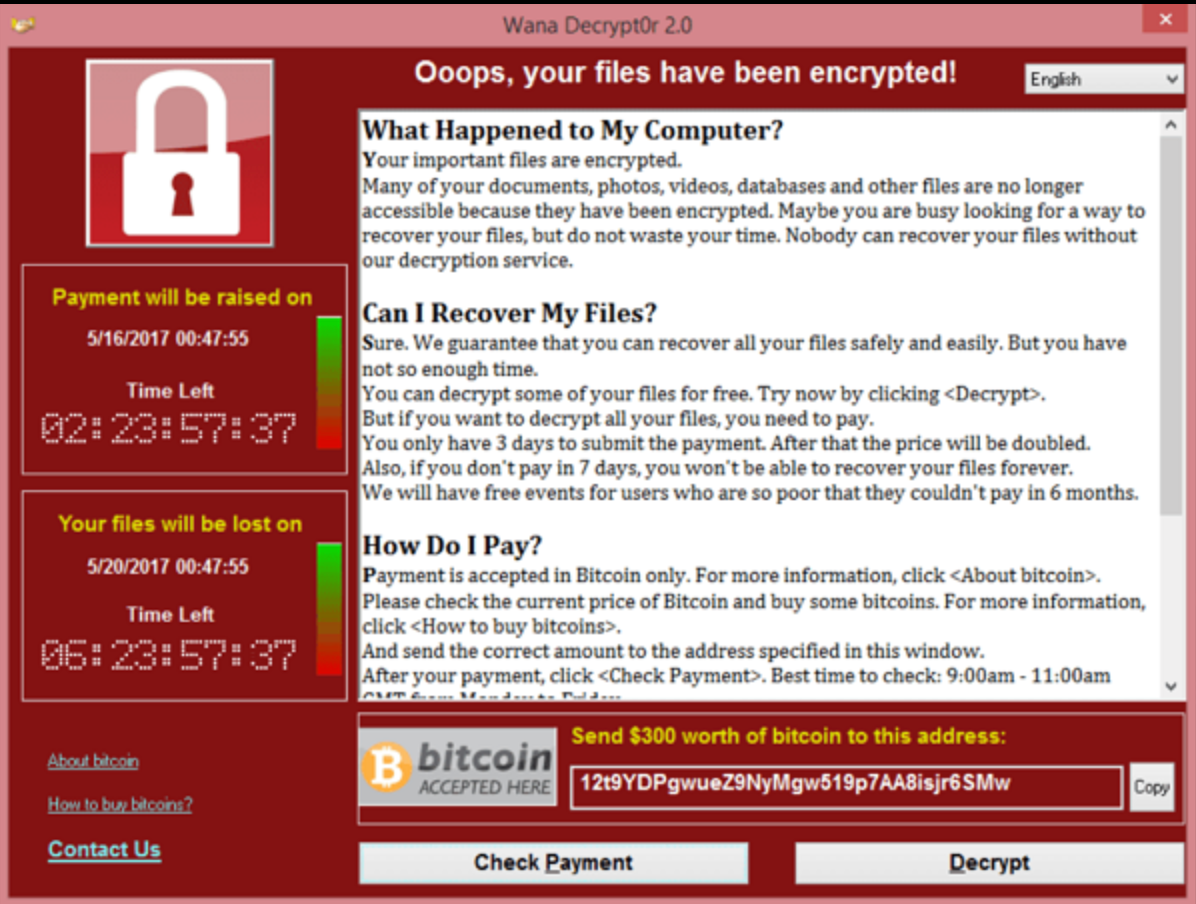
WannaCry (2017, North Korea)
Targeting computers worldwide in 2017, Wanna Cry was deemed to be a state sponsored cyber attack after originating in North Korea. Yet another virus that targeted windows based systems, Wanna Cry was ransomware that would encrypt an infected system and demand a cryptocurrency payment to be unlocked.
Using the Eternal Blue exploit to propagate, WannaCry was extremely destructive due to the fact that if no payment was received, the system would delete the encrypted files causing a loss of all data.
While WannaCry spread extremely rapidly in the early stages, things were contained with the discovery of a kill switch in the code, that enabled researchers to stop the spread of the malware. Despite this kill switch the damage was done, with hundreds of millions of dollars in damages incurred n those early hours, with an estimated 300,000 computers infected.
WannaCry reappeared later in 2018, when a modified variant caused a factory wide shutdown at Taiwan’s TSMC semi-conductor factory. This one makes the list due to it’s destructive nature and it’s state based origins. 
NotPetya (2016, Russia)
Originating in 2016, Petya rocketed to attention in 2017 when a variant was used for a massive cyber attack against Ukraine. Another Windows based piece of Malware, Petya worked similar to WannaCry in the sense that encrypted key file systems and demanded payment in Bitcoin to recover them.
Propagating via the Eternal Blue exploit, Petya is distinct due to it’s two different variants, with one a ransomware and another a wiper. NotPetya is also believed to be a state based attack, with the Russian SandWorm group suspected to be involved. The second variant of Petya was particularly unique as it also targeted power stations, gas plants, airports, banks and other critical infrastructure being used within Ukraine.
NotPetya makes the list due to it’s state sponsored nature and focus on critical infrastructure. It’s also noteworthy that the wiper variants of Petya were designed to look like basic malware, hiding the intention of their true targets and designed to be passed of as simply yet another piece of bad code rather than a state sponsored cyber attack. Stuxnet targeted Siemens Controllors Stuxnet targeted Siemens Controllors used in industrial operations. Source: Wikipedia
Stuxnet targeted Siemens Controllors Stuxnet targeted Siemens Controllors used in industrial operations. Source: Wikipedia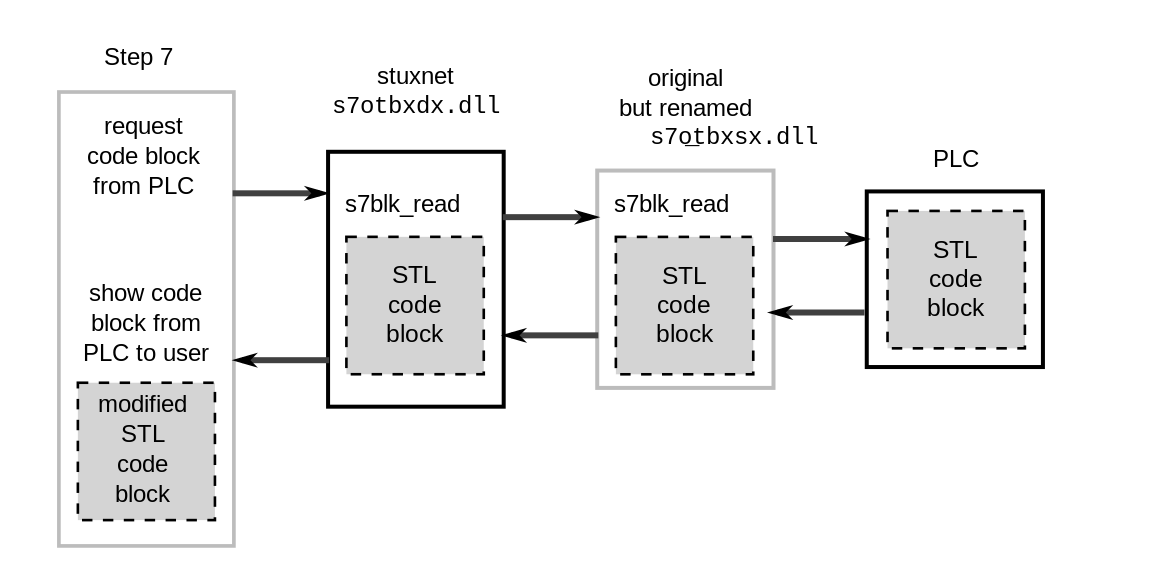 Stuxnet disrupted the code, bringing on a discreet early failure. Source: Wikipedia
Stuxnet disrupted the code, bringing on a discreet early failure. Source: Wikipedia
Stuxnet (2010, United States)
Thought to be developed in 2005, however not appearing until 2010, Stuxnet is number one on today’s list and with good cause. This virus was also state sponsored, targeting industrial control systems with a specific purpose.
Originally surfacing in mid 2010 Stuxnet had a number of features that made it rather interesting to researchers. Firstly, the virus targeted industrial control systems, or SCADA units. These units were often operating with Siemens brand micro controllers which was noted to be a particular target of interest to the virus.
Secondly on the day of it’s release, security research network and mailing groups suffered a coordinated DDOS attack, restricting the critical flow of information in regards to Stuxnet, right at the time it was needed.
Stuxnet was also unique due to it’s propagation nature. The malware would check the infected system and if it did not meet a particular set of requirements it would then focus on spreading rather than doing damage.
It was also observed by researchers that a particular segment of code within Stuxnet was designed to fool factory controllers, allowing damaged Siemens units to continue operating without triggering alerts within the infected factory.
All paths led to Iran and researchers were able to conclude that Stuxnet was released with the specific intention of causing disruption to the nuclear program being ran within Iran at that time.
Because of this, Iran was observed to beef up their security post attack, and even conducted retaliatory attacks against the US under the name Operation Ababil.
One Last Point:
You may have noticed this article varied from the first two, in both the destructive nature of each code and the more malicious intent by the designers. However we’d like to point out that rather than being designed by bored computer science students, that out of today’s list of 5, 3 were confirmed to be state sponsored cyber attacks.
The era of cyber warfare was well and truly established and it’s around this time frame that a renewed focus was applied to both observing and participating in this new digital battlespace.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it as well as hitting the right spot for the new medium algorithm. Thank you.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our Telegram channel for exclusive updates or.
🐦 Follow us on Twitter
🔗 Articles we think you’ll like:
- OSINT Unleashed: 5 Essential Tools for Cyber Investigators
- What the Tech?! GPS Technology
✉️ Want more content like this? Sign up for email updates here




























































