Radio Hackers: RFID & Access Control Systems
Sometimes, all you need to get started is an android powered smartphone
If you aren’t a medium member, you can read with no paywall via substack
We strive to provide informative articles, however, it is important for users to ensure their research is both ethical and responsible. Additionally, it is your responsibility to ensure you are compliant with all applicable laws and regulations for your region. The information provided in this article is intended for educational purposes only.
While exploring the radio spectrum, we’ve pointed out some of the essential tools you’ll need to get started. Sometimes, this can include multiple components like transmitters or receivers, and maybe even external antennas or amplifiers to help with signal quality and reception. Often, this can redefine a project, turning it from a simple project to a rather complex project with numerous important parts.
If you’re a beginner you might rightly find this onslaught of information to be a little complex or possibly even a bit overwhelming. And if that’s the case then today's article is just for you. With few complex parts and the only requirement being an Android-powered smartphone, it’s a quick, easy and low-risk way to start exploring the radio spectrum. Let’s get to it!
So, Access Cards You Say?
This could be called more a simple clone rather than a radio hack, however, given we’ll be cloning them in our own lab, with our own devices and they are RF-powered means it fits the bill for today's article. Essentially, we’ll be looking at the security around RFID access systems and looking at simple ways to bypass them using hardware that’s either on hand or easily accessible.
But first, to breach the system we must understand the system so let's start by taking a look at the various types of RFID devices and explore which ones are interesting for our purposes.
Radio Frequency Identification (RFID)
RFID (Radio Frequency Identification) is a technology that uses radio waves to wirelessly identify and track objects or individuals. It consists of two main components: RFID tags and RFID readers. The tags, which are small electronic devices, contain unique identifiers that can be read by RFID readers within a certain range.
RFID technology is utilized in various applications, including access control systems, inventory management, supply chain logistics, and contactless payment systems. Its ability to enable automatic identification and data capture without direct line-of-sight contact has made RFID a popular choice for improving efficiency and security in numerous industries.
Types Of RFID
Like any radio transmitter, we’ll find that the passive RFID systems we’re interested in will often use different operating frequencies. Because of this, one of the most important parts of an assessment such as this is identifying this frequency and ensuring we have the appropriate reader to communicate with our card. Typically we’ll see systems using the following frequencies.
Low Frequency (LF): LF RFID systems typically operate within the frequency range of 125 kHz to 134 kHz. LF tags are known for their relatively short read ranges (typically up to a few feet) and immunity to interference from liquids and metals.
High Frequency (HF): HF RFID systems operate within the frequency range of 13.56 MHz. HF tags usually offer higher data transfer rates and read ranges which can be important in more advanced systems.
Ultra-High Frequency (UHF): UHF RFID systems operate within the frequency range of 860 MHz to 960 MHz. UHF tags offer far greater performance than equivalent systems and will often be seen in environments where range is an important feature.
Types Of Attacks
Like many different types of devices, there’s more than one way to get to the end result. What this means is, that effectively a typical device is often vulnerable to multiple different types of attacks as opposed to just a single form.
While this varies from device to device, we can look at some common attack vectors that are relevant to other areas of cybersecurity as well.
Denial of Service (DoS): Attackers can disrupt RFID systems by jamming or blocking communication between tags and readers, preventing legitimate access or data transmission. A DoS attack could be as simple as a competing signal on the same wavelength that prevents a simple exchange between reader and card.
Replay Attacks: In a replay attack, attackers capture and replay legitimate RFID tag data to gain unauthorized access to a system. By replaying previously captured authentication messages, attackers can trick the system into granting access without proper authorization. A replay attack could use a device such as the Flipper Zero or smartphone to capture the signal for later use.
Tag Cloning: By capturing the data transmitted by legitimate RFID tags, attackers can create counterfeit tags with the same identifiers, allowing them to masquerade as authorized users or items within the system. We should be wary that some high-end systems may have security features that defeat cloning. We’ll be using cloning for today's attempt so we can explore that more later in the article.
Of course, we haven’t discussed Man In The Middle (MITM), Physical access breaches and cryptographic attacks either, however when dealing with RFID devices we’ll often find these types of attacks are less common than the ones we’ve discussed above. Like computers, RFID systems have various features, security and cryptographic variables that will change from system to system. This can be applied on a case-by-case basis using information that’s easily available from online sources.
Let's Do (Clone) This
To get started, you’ll need access to an Android device with an NFC package as well as the ability to download apps from the Play Store. Today we’ll be using the NFC tools package which is easily downloaded and installed on most Android devices.
Our Android device should be equipped to read High Frequency devices operating on 13.56mhz so we’ll need to conduct our testing with a card in that range. Thankfully, we’ve got a mixture of cards ready for testing purposes. NFC Tools comes with a pretty comprehensive set of instructions, which you’ll be able to use for troubleshooting if you need to. Once the App is installed we can look at capturing our card. To do this, we’ll “read” the card so it’s stored on our device.
NFC Tools comes with a pretty comprehensive set of instructions, which you’ll be able to use for troubleshooting if you need to. Once the App is installed we can look at capturing our card. To do this, we’ll “read” the card so it’s stored on our device. Once we’ve read the card, we’ll see the card information displayed on our device. We can then use this information and rewrite it to our fresh duplicate card. The App can store existing information from previously used cards, which may or may not be helpful for your circumstances.
Once we’ve read the card, we’ll see the card information displayed on our device. We can then use this information and rewrite it to our fresh duplicate card. The App can store existing information from previously used cards, which may or may not be helpful for your circumstances.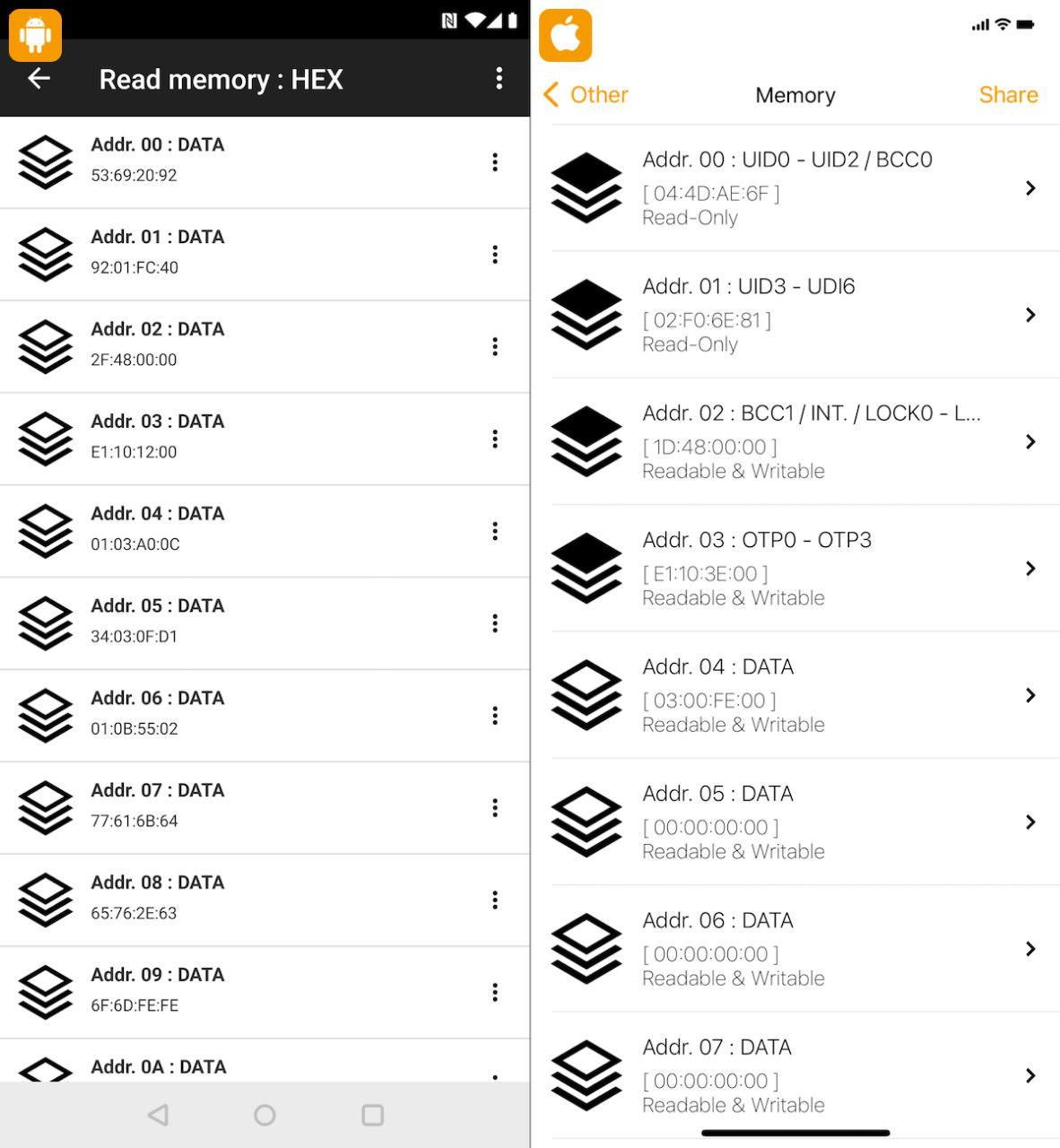 To complete the close, we’ll simply use the write feature within the app to prepare our information. Once the information is set, we’ll simply write it to the card by putting it on to the card reader.
To complete the close, we’ll simply use the write feature within the app to prepare our information. Once the information is set, we’ll simply write it to the card by putting it on to the card reader. Once you’re finished, congratulations! You’ve just finished gaining access to your test system with a self-written card. If you’re interested, you can look at the “Other Tools” section of the app and explore some of the other features that are writable to your RFID card.
Once you’re finished, congratulations! You’ve just finished gaining access to your test system with a self-written card. If you’re interested, you can look at the “Other Tools” section of the app and explore some of the other features that are writable to your RFID card.
Final Words
It’s important to remember that sometimes RFID systems are far more complex than a passive chip talking to a single reader. Often, we’ll see systems that have clone prevention, live access control and other security features that are designed to thwart cheap clones and easy attacks. This is why identifying the system you’re working with is such an important part of the research process, as it means you’ll be able to source and use information that will make your job easier.
While the topic of RF hacking and spoofing can involve high-end hardware with a significant knowledge penalty, projects like this allow the beginner to explore the radio spectrum in a way that isn’t overwhelming in cost or experience.
Any ideas on what you’d like to see next?? Drop a comment and let us know. Tutorial recommendations and requests are always welcomed.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Software Defined Radio & Radio Hacking Pt 1
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates





































































