Historical Hacks: Ashley Madison
Breached data can cause all kinds of long-term issues to user security.
If you aren’t a medium member, you can read with no paywall via substack
When you’re dealing with cybersecurity it’s often true to say that some of the more damaging incidents come from personalised attacks. The success of everything from simple phishing attacks right through to a heavily personalized social engineering approach can be dramatically increased by including personal information and understanding more about your end target. Enhancing legitimacy can often be the difference between an email hitting the spam folder, and a target absent-mindedly clicking a lick or entering personal information into a malicious web portal.
But what happens when you’re dealing with a legitimate website that then happens to breach your information after being hacked??? In today’s historical hack, we’ll be wandering back to 2015 and taking a look at a rather controversial data breach that made the news for all the wrong reasons. It exposed its users to blackmail, extortion and financial manipulation that is still being seen today, albeit on a far lesser scale.
Ashley Who?
Launched in 2002, Ashley Madison was a relatively unknown dating agency in the beginning. However, rather than traditional relationships this agency had a distinctly different flavour. Marketing its services with the caption “Life’s short, Have an Affair”, Ashley Madison directly targeted users in unhappy relationships who were looking for companionship.
Being a dating website, naturally, they held large amounts of information about their users. While this included things like personal identifying information (PII) it also included information on things like sexual orientation, political leanings, financial information as well as other relevant topics you might like to know about a potential partner.
In the time before the hack, Ashley Madison had already faced minor controversy. Not only was their business model clearly provocative, but they also faced accusations of engagement farming, with bots and false profiles permeating the site and creating artificial traffic directed towards its predominantly male user base.
Further attention was drawn to some of its advertising and business practices, with so-called “Guerrilla marketing” strategies used to promote its services and draw attention to the company. However, this wasn’t always successful, with some companies banning the service from conducting advertising and certain countries denying it the right to operate on its territory. Singapore for instance, was the first country to ban Ashley Madison outright for “Promoting adultery and being inconsistent with family values”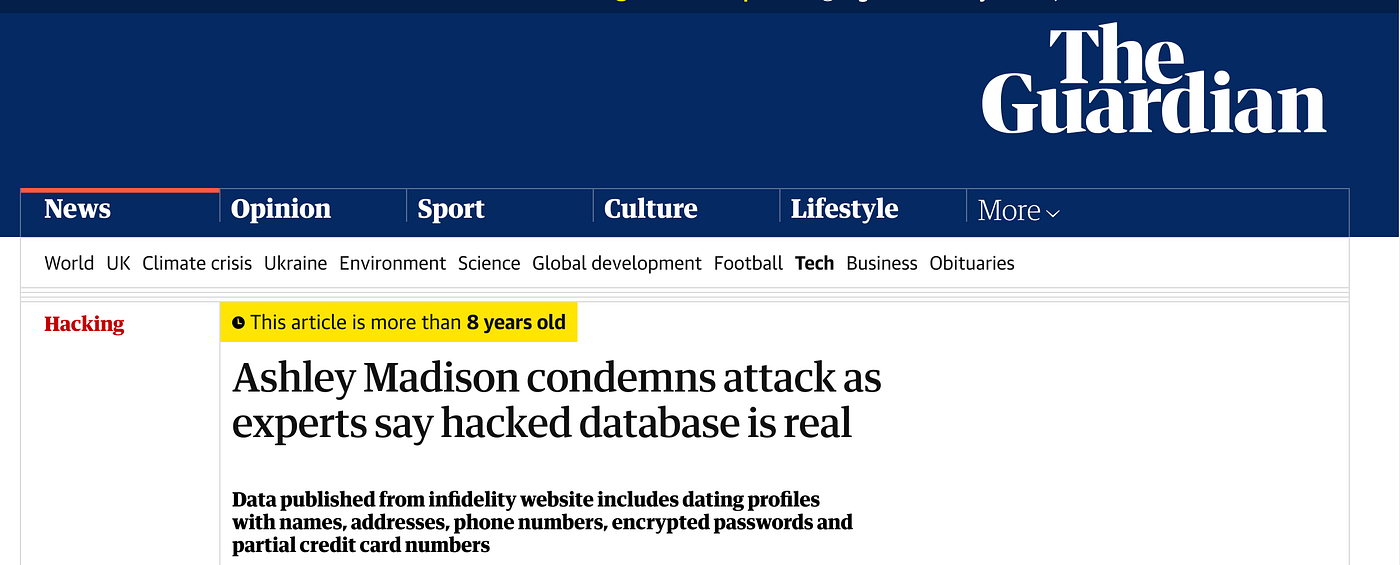
The Hack
By the time the hack occurred in 2015, the company had been operating for a few years and had built up a large database of its users. Along the way though, it had also acquired a few problems around its attitude towards things like cyber hygiene and data management. So, despite the company facing early controversy things were about to get much, much worse.
The first problems were known when an unknown group known as “The Impact Team” made an announcement about holding breach data from the Ashley Madison servers. While damage control was done early and an attempt was made to deny the hack, this later fell apart when a 10GB data file was released on BitTorrent. This proved the existence of the hack as well as the sensitivity & relevance of some of the information that was stolen.
So let’s pause for a second to analyse this. We have a company that's controversial in nature that’s leaked a large bunch of information that its users would prefer never saw the light of day. So, how did the internet react to this? It melted down of course. What else would you expect?!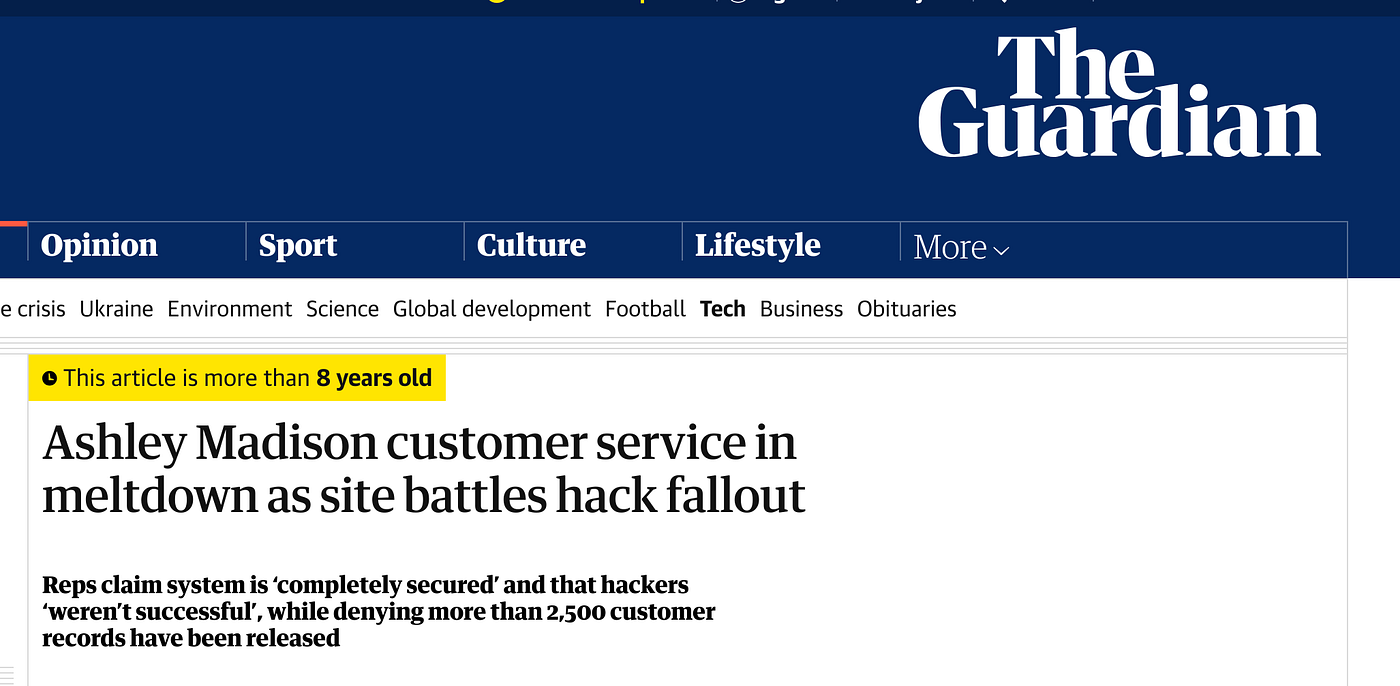
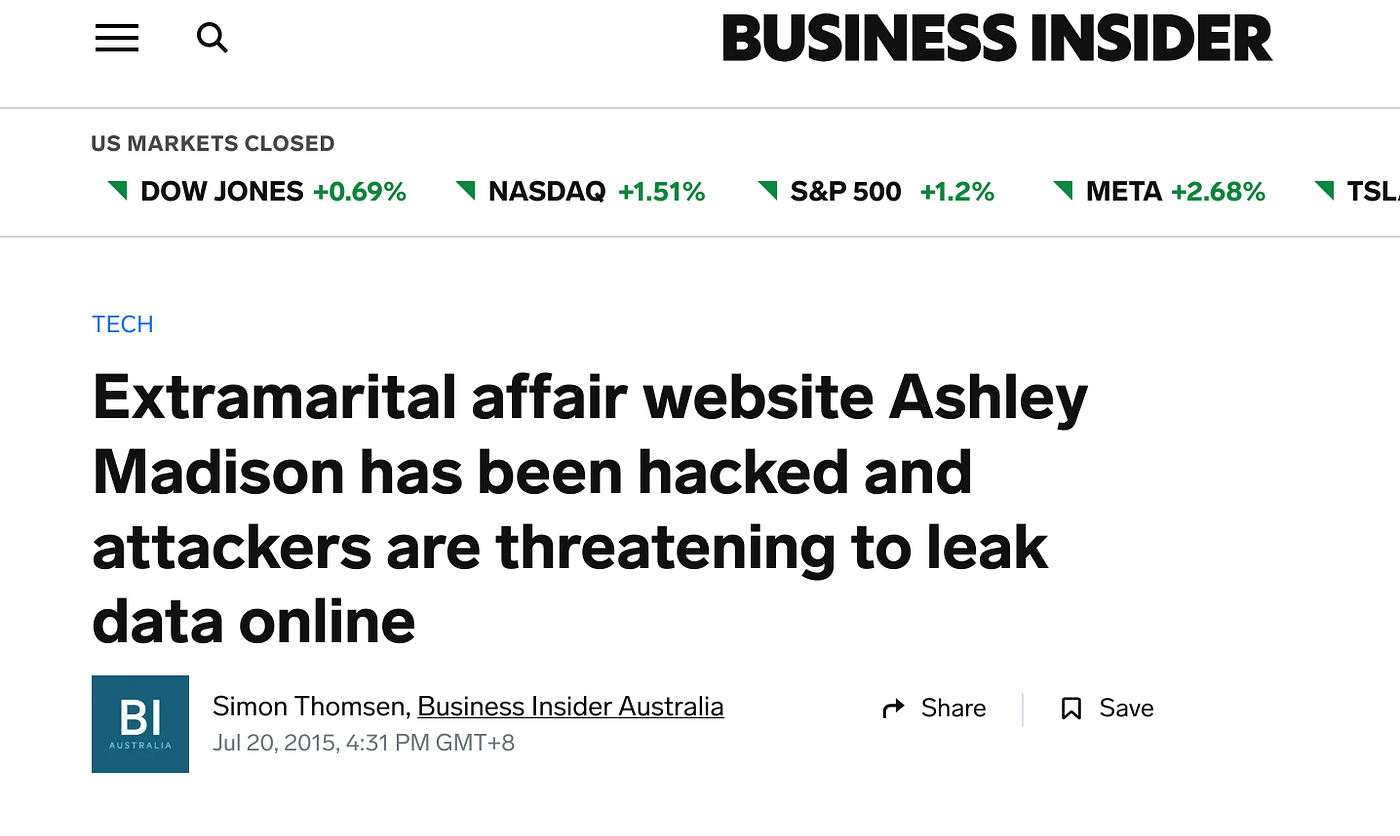
In terms of scale, it was huge. Over 37 million people worldwide were believed to be affected by the hack. Unfortunately, this hack also came with actual, real-world consequences as more than a few doxxed users faced significant consequences due to the release of their personal information.
While information in the aftermath of the breach became more and more murky as time progressed, it’s believed the attack was conducted via SQL injection. This, paired with weak encryption techniques meant that the sensitive information held by the company wasn’t able to be protected appropriately.
The Aftermath
While databases being breached is usually a pretty significant event, this one was especially so because after the data was breached a large amount of work was carried out by various entities with regards to processing and analysing this effectively.
This included everything from cyber researchers and analysts right through to companies that were claiming to provide data “scrubbing” services that would remove a victim's information from the database for a fee.
However, this conversation was amplified further by the revelation of poor security strategies within Ashley Madison as well as poor handling of the crisis by the company leadership as the crisis unfolded. This meant that in reality, the event became an example of what not to do during a cyber incident.
And, while typically, data breaches are stressful incidents that will most often evoke a sympathetic reaction from members of the public this breach was actually quite different. Due to the nature of its business as well as the demographic of its users, in this breach victims were often outright ridiculed for their involvement. This made mitigation strategies far harder to apply which often exposed the victims to longer lasting consequences.
One other interesting point that came out as a result of the hack was the poor security techniques applied by many of its users. Signing up for a profile didn’t require ID, meaning that theoretically, the 37 million profiles could be fake. However, research showed that not only were a large number of users actually verified in the leak, but they were also significantly involved. This meant passwords, credit card information and more were all part of the breach and when the data nerds were all said and done, one thing that was noteworthy was the poor password management strategies applied by many. Check out that list below.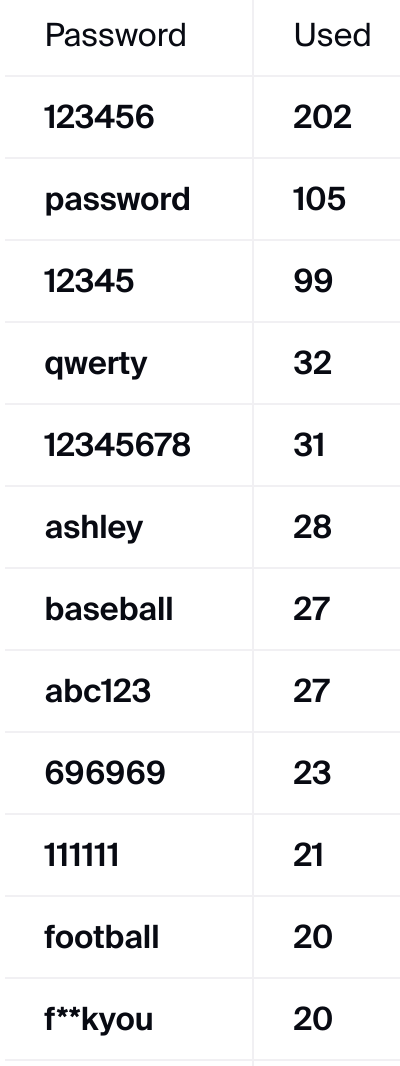
Lessons Learnt
While it's pretty reasonable to assume that most readers won't be having an affair any time soon, believe it or not, there are some points that the everyday reader can take away from this event that can help improve the management of your own digital footprint.
Passwords: While good password management is still a solid strategy, there are now far more options around securing online accounts than ever before, with magic links and hardware-based authentication being just a couple of the ways to provide additional security. While no method is perfect, you can improve your footprint and general security by using unique, strong passwords and considering other methods like this to help safeguard your account.
Cyber Hygiene: The biggest step you can take though is by considering the way you handle your personal information in the digital domain. While this will typically vary according to a user's appetite for risk, things like alias email addresses and services like Cloaked, provide ways for users to apply additional security mitigation techniques to their online lives.
While approaches like this won’t remove the chance of being in a data breach, what it will do is allow you to face such an incident comfortably in the knowledge that mitigation strategies were applied prior to the event occurring. This usually makes the outcome of any given event much easier to manage.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Software Defined Radio & Radio Hacking Pt 1
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates











































