Your Digital Legacy: Managing Your Online Life
Looking at some simple steps to manage your digital life when you’re gone.
If you aren’t a medium member, you can read with no paywall via substack.
Grief, loss and death can be a difficult time. It can usually happen unexpectedly and in today’s world, even when a person is physically gone, their life and digital footprints carry on for some time. Messages arrive, Emails are sent, and even group chats can sometimes still show active members.
Depending on the size of your digital footprint, and the quantity of data you store online, this can often make the situation even more stressful as people will need access to memories, financial information and other essential information as well. And, while this is often an uncomfortable topic for many, tech companies have recognised that steps need to be taken to preserve someone's digital legacy.
In today’s article, we’ll be taking a look at some of the steps you can take to share information and protect your privacy as needed. Despite it being an awkward topic to cover, it’s an essential part of ensuring your legacy is protected when you’re gone and ensuring you’re able to transfer assets to people as needed.
Just Think For A Second
We’d encourage you at this point, to stop and think for a moment about the types of things your digital footprint encompasses. While it’s easy to think about your Apple or Google account, deal with that and call it a day realistically it usually can be a lot more complex than that.
For instance, within our reader group is a large number of cryptocurrency fans and users. This too requires adequate preparation and is part of the reason having a solid backup and recovery plan that others are able to implement is so important. Could your loved ones recover or open your wallet in your absence?
Those who use technology in their professional role might also find that having a suitable strategy for this may prove useful. While many larger corporations and multinationals have dedicated IT departments that are able to deal with this at scale, many smaller businesses and sole traders often have little in the way of cybersecurity preparation at all and often, entire departments or businesses can revolve around the action of a single person.
It’s also worth mentioning that many technology providers won’t always act how you’d expect them to either. Google, for instance, takes the view that preserving the customer's privacy is paramount during this time. So often, you’ll receive little help in the way of data recovery without a clearly nominated strategy. Ensuring that there’s a clear plan that’s able to be implemented in your absence can make a difficult time a little easier for others to process, so let's look at some of the steps we can take to get this sorted. While they won’t be step-by-step tutorials, we will look at some of the options available.
Google Account Manager
Buried deep in the account settings, the inactive account manager is your key to helping Google understand your wishes and what to preserve in the event of an emergency. Using a pre-nominated duration of inactivity, you can set the account manager to both notify someone in your absence and share your data. This data sharing is pretty flexible, so you can share some information while preserving other things should you need to.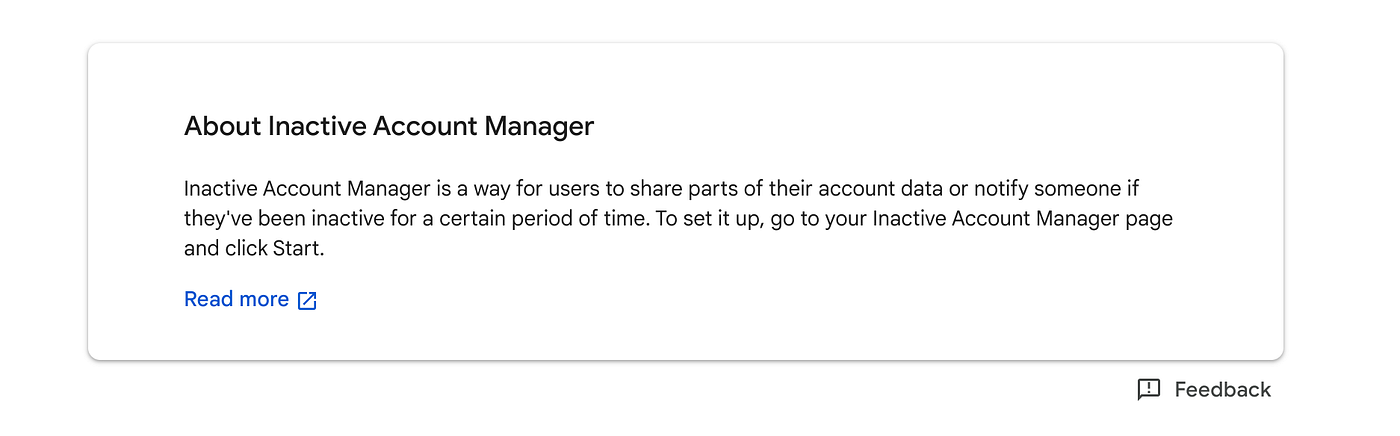
Activation is extremely simple. After meeting the criteria for the pre-nominated inactivity time Google will place the account into inactive mode and send an email to up to 10 pre-nominated contacts. You can also choose what data (if any) you’d like to share with them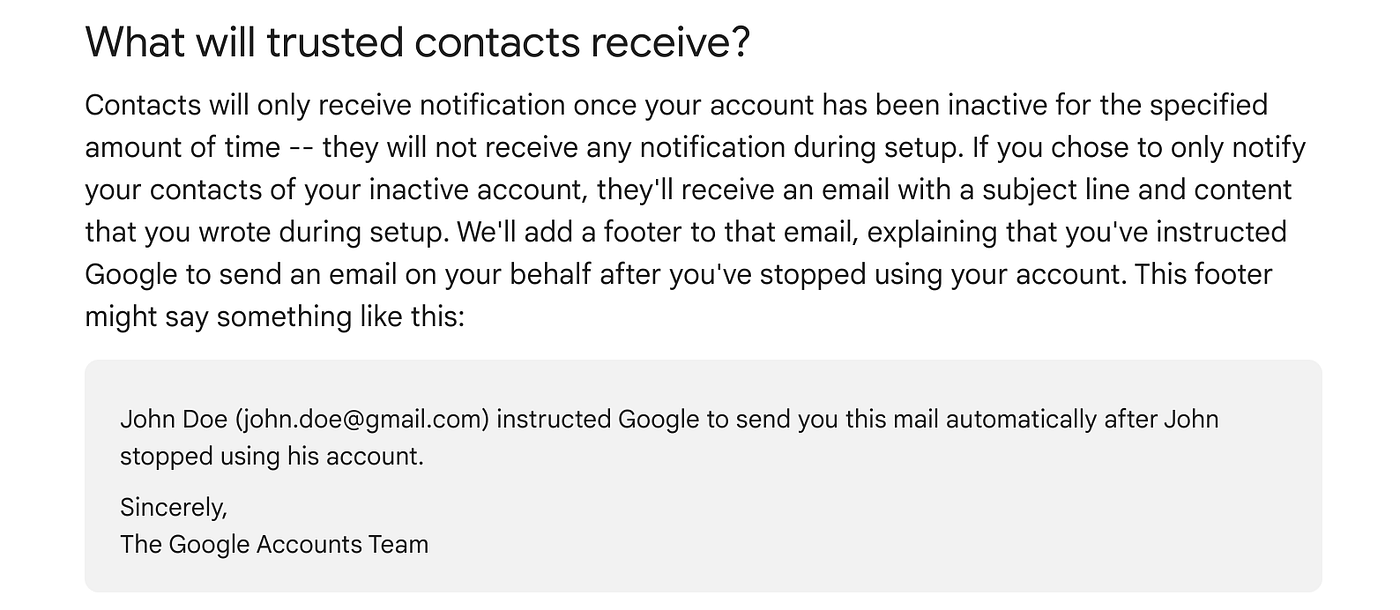
Apple Digital Legacy
Apple also makes provisions for users to nominate contacts to use for legacy management. With this, someone you’ve nominated will be able to access your phone after submitting a request through the Apple support team.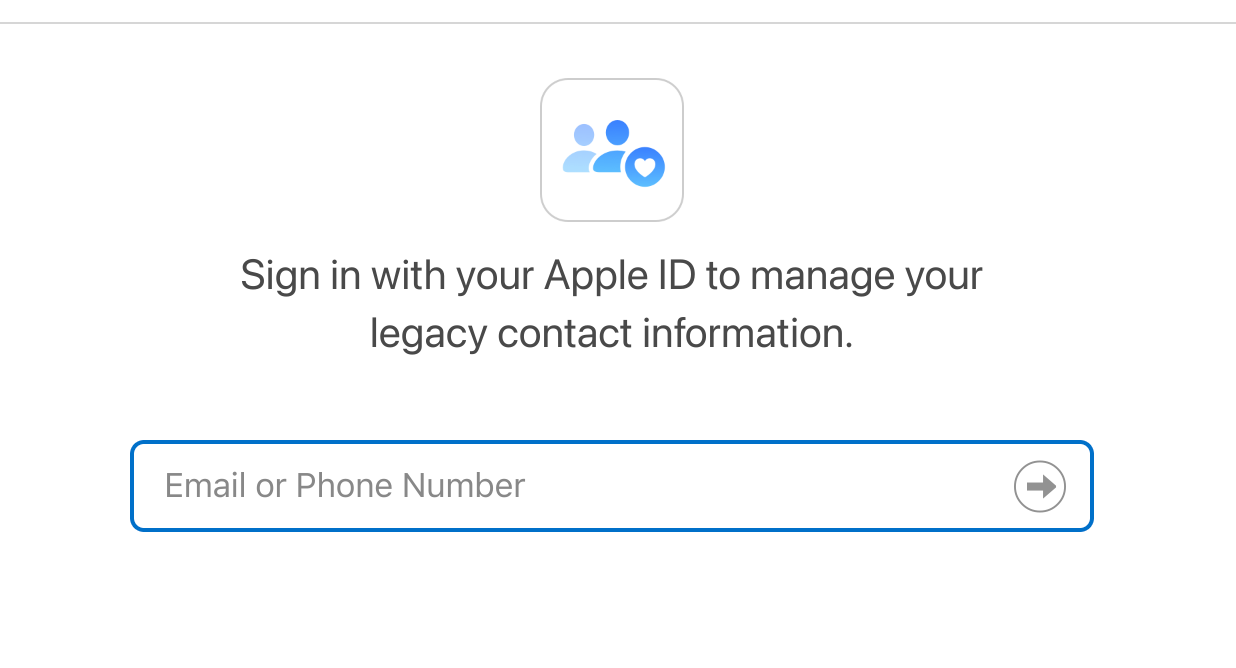
Like Google, Apple makes this pretty easy to manage for users by simply putting the information into the account management section for your Apple account. However, rather than setting up a phone number to use for verification as is the Google way, Apple uses the Legacy Contact key for this. Working in a similar fashion to a PGP key, you’ll give one part of the key to your nominated contact who can then use it to access your account should you even need it.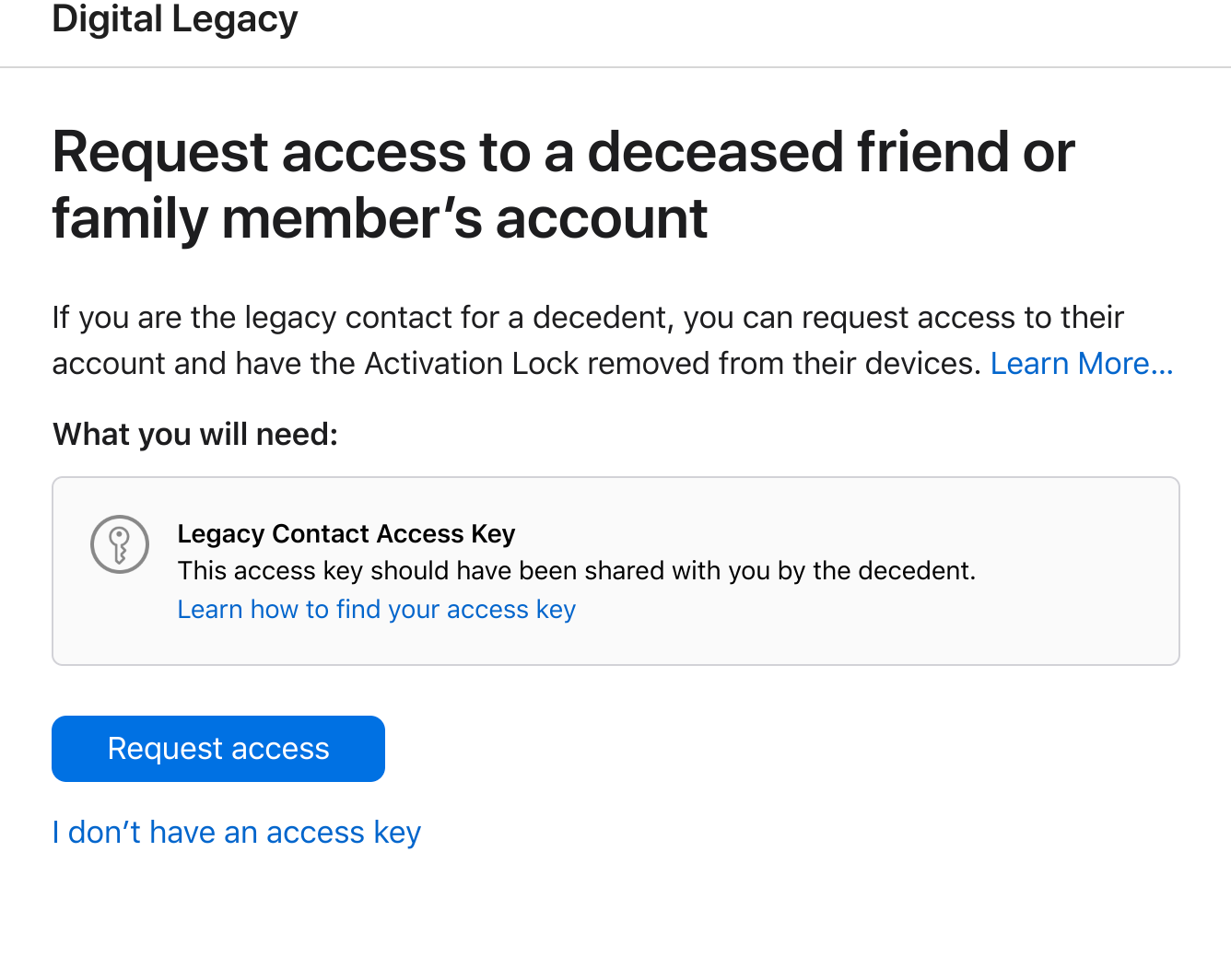
Other Accounts & Considerations
While you’ll typically think of social media and other accounts of that nature when considering these topics, the reality is that our connected world runs far deeper than that. Most countries use an electronic form of communication for many matters of a government nature, nearly everybody uses online banking these days and even things like Vehicle Registrations and Insurance companies have an online component now.
So, when you’re setting this type of thing up, it can be a good habit to ensure you’re looking at things like banking habits and transport options as well. If you share finances, can your partner access them should they need to? Is the car registered in your name? All these questions and more can be mitigated a lot easier by having some of these discussions ahead of time.
One other thing to consider is the subject of insurance. Many people opt to take out life insurance or funeral insurance to make the time less stressful for those involved. If you’re one of those people, then it’s also good practice to ensure your nominated contact is up to date, and that the person knows the policy exists and is accessible. Dealing with this process can often be a bit of a whirlpool when you’re also dealing with grief, so making this a bit more accessible to your loved ones can often make this process much easier.
Lastly, it’s a good idea to check and set up legacy options on your usual social media accounts as well. While the process will vary from company to company, there are usually ways to establish this via the account management process. Some companies might choose to freeze the account entirely, while others may place it into a legacy mode where it remains partly accessible to some users.
Hold Up. I Like Privacy
While the concept of making your account accessible to others might seem crazy when you consider the concept of privacy alongside it, the reality is by taking appropriate steps you’re actually increasing the chances of protecting your privacy when you’re gone.
The reality is that in some instances, privacy can sometimes disappear simply by presenting a death certificate and being an authorised person like a nominated next of kin. While this isn’t always applicable in the tech world (google with withhold some account data) it’s still worth considering if that’s important to you.
Rather than having your account handed over (or even hacked in the event of your absence), establishing a protocol around handling this information takes little time and can give you substantial piece of mind that things will be handled appropriately.
Although we can’t control everything around this topic, there’s a lot we can do to ease some of the concerns that can be around this process.
Other Options
It’s fair to say that with the proliferation of data breaches in the modern world, some of our readers might not trust some of these larger companies to act in their best interests during these times. And, if you’re one of those people then you might find some comfort in the fact that there are alternate ways of doing this that don’t entail placing your trust in them.
The first thing to consider is what you’d like to share and then make it accessible. For instance, you might choose to have a lock placed on your accounts entirely once the company is notified, assuring you that your data remains secure. You can then choose to place your legacy information into a third-party cloud provider like Dropbox or similar and then arrange to share that information with your next of kin.
One other ingenious but lesser-used option can be a deadman switch. A simple piece of software using a trigger like social media posts, the script can run in the background and be configured to send a simple email containing information in your absence.
While this is similar to the Inactivity checks for a Google account, choosing to run this locally might be a better option for some of the more technical and security-conscious folk.
Or, you might simply choose to involve the services of a legal professional to act on your behalf when required.
Whatever option you decide to choose, we’d encourage you to have these conversations with the people that matter ahead of time. With much of this process being a set-and-forget type system, it really can save a significant amount of stress at a very difficult time.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Software Defined Radio & Radio Hacking Pt 1
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates











![[ℕ𝕖𝕧𝕖𝕣] 𝕊𝕖𝕝𝕝 𝕐𝕠𝕦𝕣 𝔹𝕚𝕥𝕔𝕠𝕚𝕟 - And Now What.... Pray To The God Of Hopium?](https://cdn.bulbapp.io/frontend/images/79e7827b-c644-4853-b048-a9601a8a8da7/1)































