I Have Opened A Malware PDF File. What Now?
"Please help!"
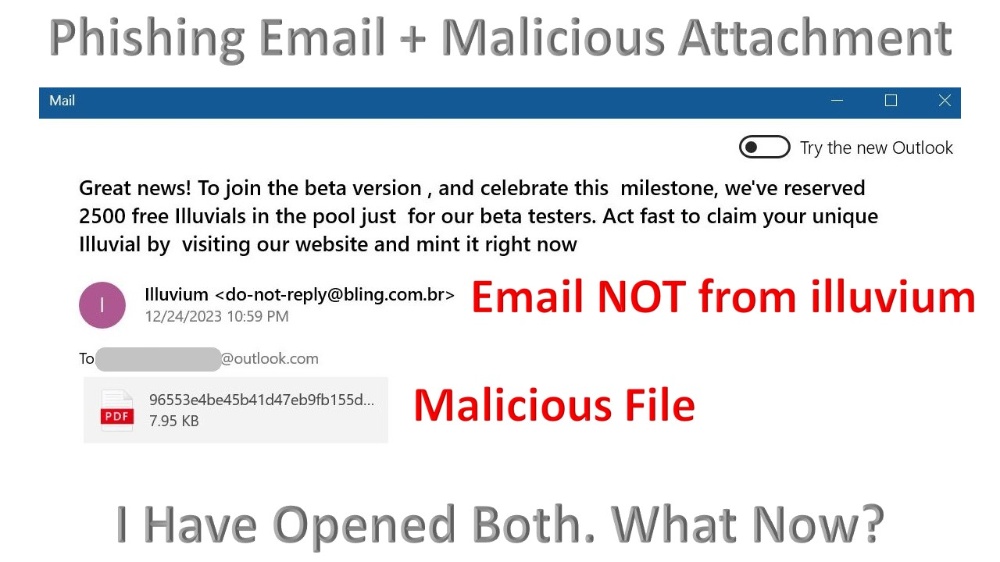
"I was not thinking straight and opened a phishing email. "To make things worse, I have also opened the attached PDF, and the following file has opened."
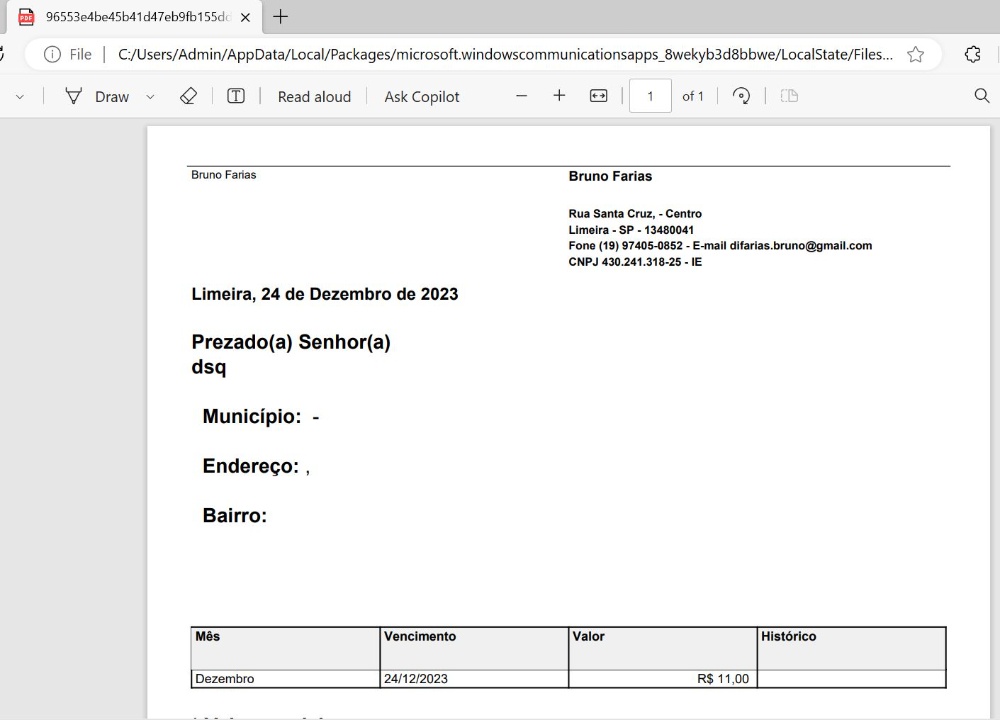
"To make things worse, I have also opened the attached PDF, and the following file has opened." "C:/Users/admin/AppData/... what is happening here?"
"C:/Users/admin/AppData/... what is happening here?"
"Have I installed some malware or viruses?"
These are questions that, in one form or another, we come across every so often in forums.
We know that you take your digital safety very seriously, and the good digital practices you follow prevent you from encountering this kind of situation.
But everyone can have a bad day or be in a hurry, become distracted, and take a step that will be regretted.
In this post, we will review the steps you should take if you ever make a similar cybersecurity mistake:
- How to use Hybrid Analysis to analyze a suspicious file
- How to use Virus Total to analyze a suspicious file
- How to use File Scan to analyze a suspicious file
- ... what was the hacker after?
- What to do if you suspect you have installed malware on your device.
Be warned: Curiosity killed the cat.
Before moving ahead, please be careful if you decide to do a phishing email investigation yourself.
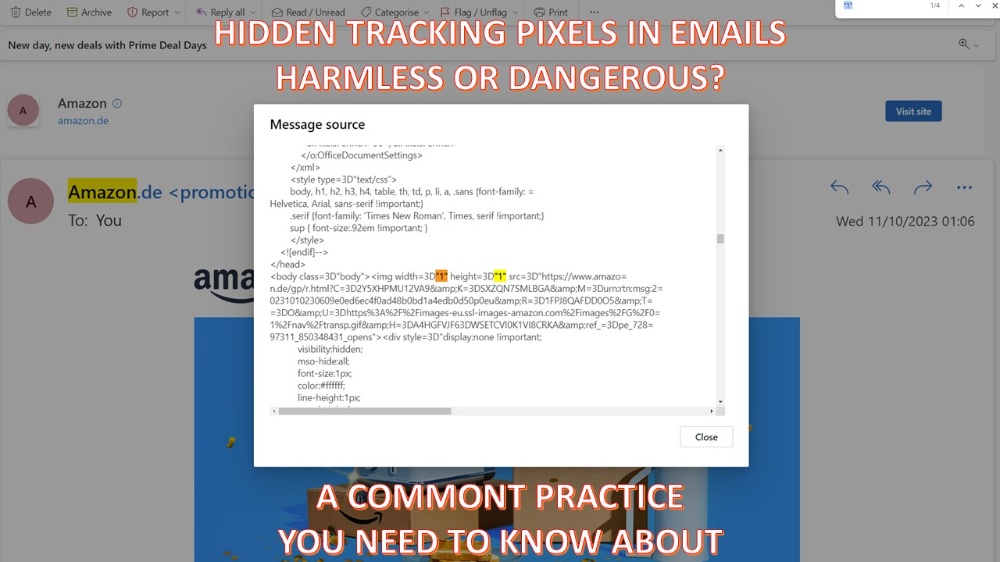
Many emails contain invisible tracking pixels used to collect sensitive data without your awareness.
While many legitimate companies use tracking pixels in your communications, they do not use the collected information for malicious purposes. How this practice invades your privacy may be debatable, though.
But be aware that most phishing emails contain invisible tracking pixels and collect information that can be used to organize further phishing attacks.
Additionally, some emails can contain pernicious malware that can be used to hijack sessions. Out of curiosity, one small mistake can put you at risk.
How to use Hybrid Analysis to analyze a suspicious file
As described in the Hybrid Analysis webpage:
'This is a free malware analysis service for the community that detects and analyzes unknown threats using a unique Hybrid Analysis technology.'
If you have a suspicious file that you want to analyze, you need to drop it, and Hybrid Analysis will analyze it for you.
This is a 5-minute power-up, so we will not do a detailed Hybrid Analysis review. But if you want to learn more, please review the Hybrid Analysis FAQ webpage.
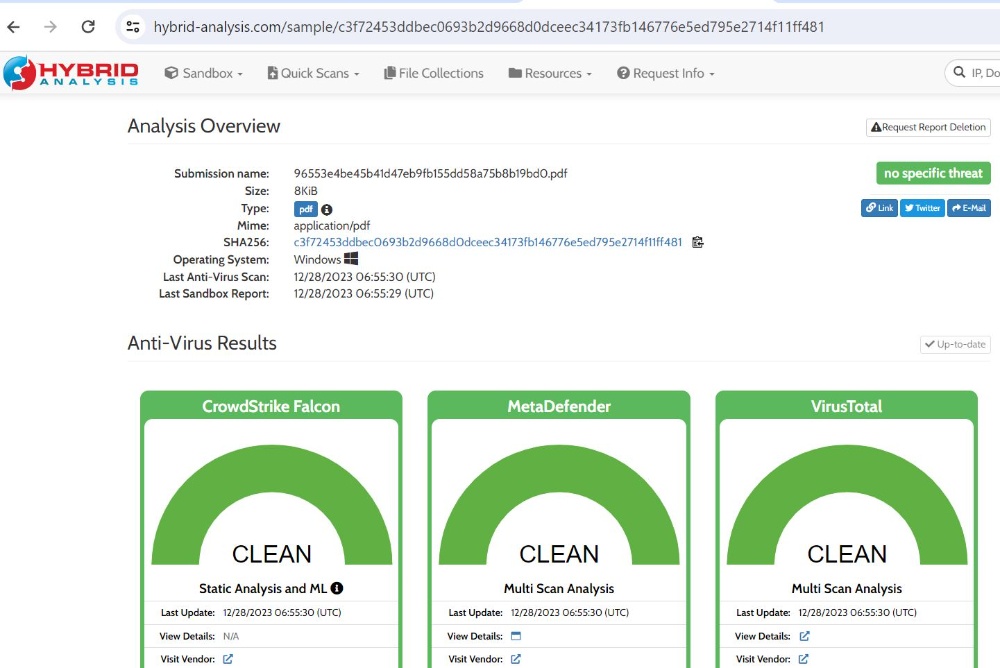
We have dropped our PDF for analysis, and it seems it is deemed safe: CrowdStrike Falcon clean, MetaDefender Clean, and VirusTotal clean.
More on that in the section 'If no malware or virus was installed, what was the hacker after?'.
How to use Virus Total to inspect a suspicious file
As described in the Virus Total webpage:
'Analyse suspicious files, domains, IPs, and URLs to detect malware and other breaches, automatically share them with the security community.'
If you have a suspicious file that you want to analyze, you need to drop it, and Virus Total will analyze it for you.
This is a 5-minute power-up, so we will not do a detailed Virus Total review. But if you want to learn more, please review the Virus Total How It Works webpage.
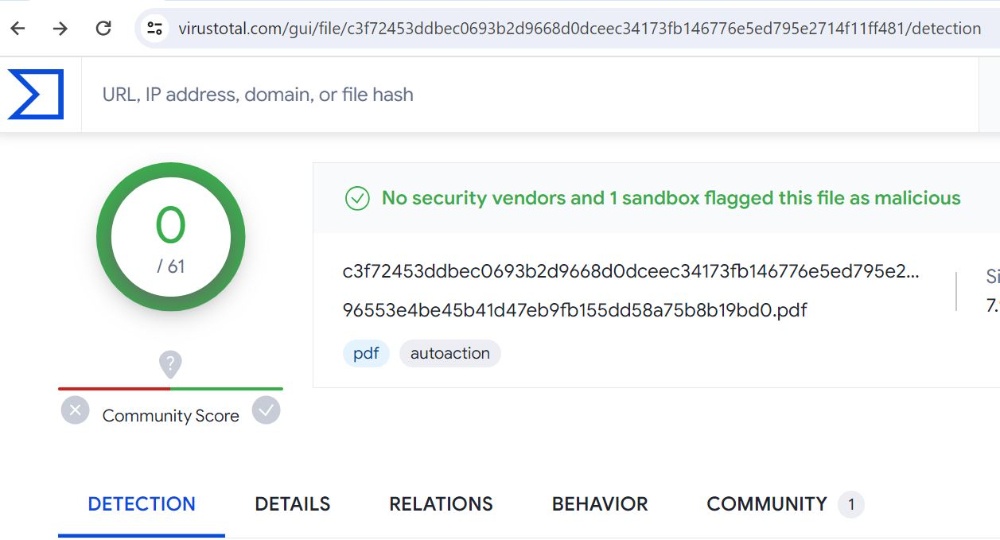
Once again, we have dropped our suspicious file, which has been deemed safe: 'No security vendors and 1 sandbox flagged this file as malicious.'
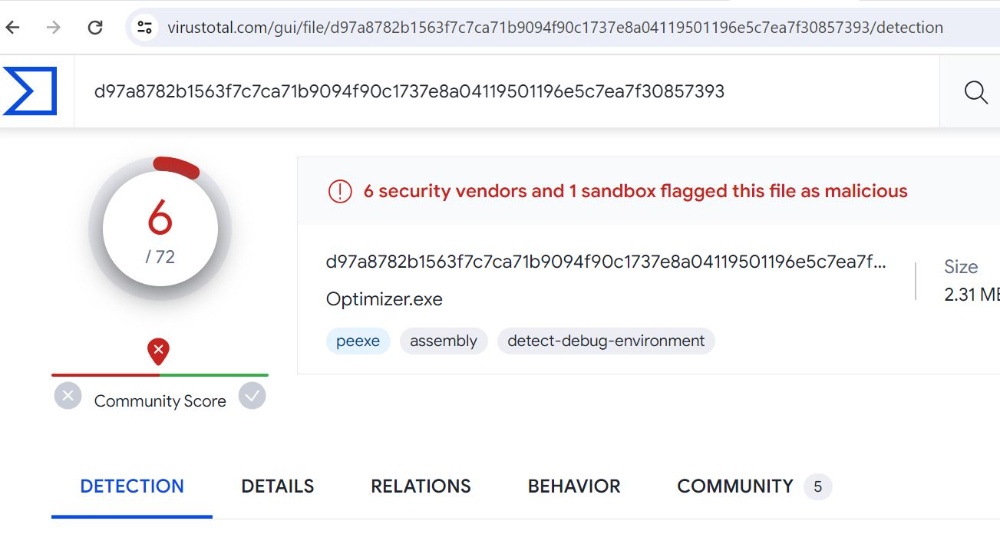
Still, for contrast, see below the assessment of a malicious 'optimizer.exe' file and how '6 security vendors and 1 sandbox flagged this file as malicious.'
How to use File Scan to inspect a suspicious file
Last but not least, as described in the File Scan webpage:
'The free community version of FileScan.IO is powered by OPSWAT Filescan Sandbox that operates 10 times faster than traditional sandboxes and uses 90% fewer resources. It uses adaptive threat analysis technology to detect evasive malware and extract relevant Indicators of Compromise (IOCs). Our threat-agnostic scanning supports a wide variety of files and URLs to identify IOCs swiftly and efficiently.'
Again, this is a 5-minute power-up, so we will not do a detailed File Scan review. But if you want to learn more, please review the File Scan FAQ webpage.
Once again, we have dropped our suspicious file, deemed safe: 'No Threat/100%.'
If no malware or virus was installed, what was the hacker after?
Only a security professional with access to the file could 100% assess if a file contains anything malicious or poses a security threat.
But anyone can investigate and find out what a file without virus or malware can be after.
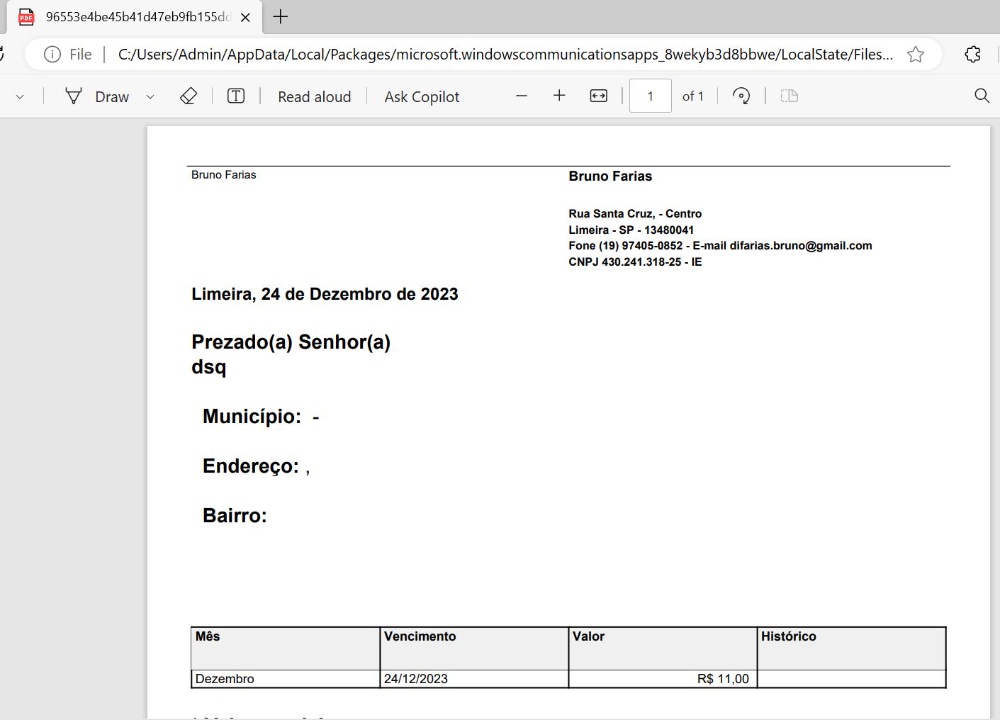
Because it is clear that the victim received a phishing email: the 'do-not-reply@biling.com.br' has nothing to do with Illuvium.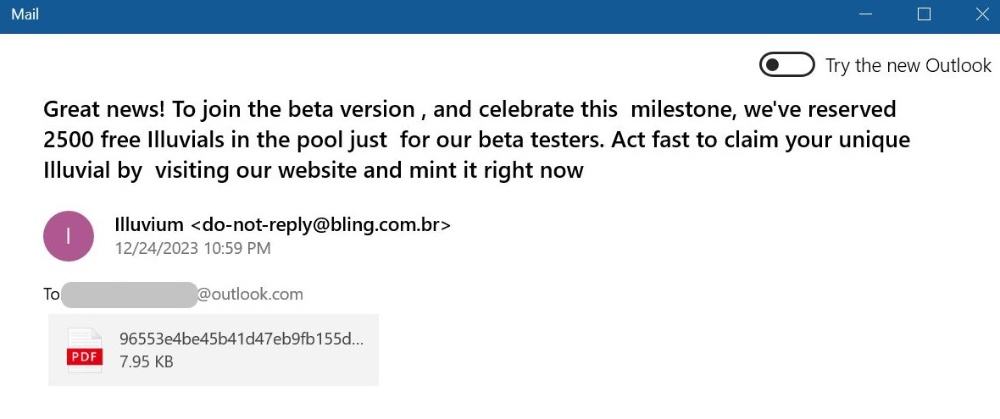
'A decentralised studio building the world’s first Interoperable Blockchain Game (IBG) universe including an open-world exploration game, industrial city builder, and autobattler, all on the Ethereum blockchain.'
So what is the hacker or scammer after?
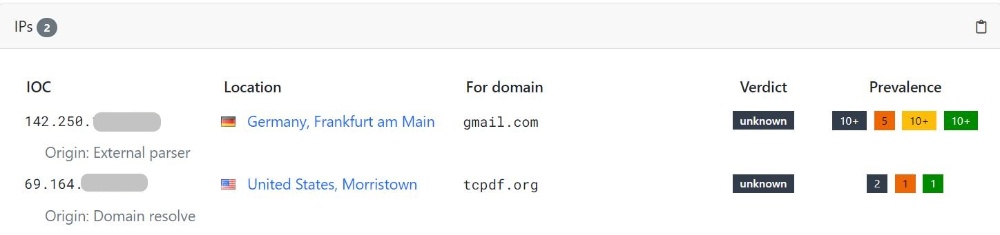
We got the following information from the File Scan analysis, but similar information can also be found in Virus Total or Hybrid Analysis.
The scammer has obtained the victim's IP address, which can be used to determine the victim's approximate location.
If you want to know your IP or the location of any IP, you can use one of the multiple available tools, like iplocation.net
It could be that this information, in combination with other sensitive information, can be used to mount a more sophisticated phishing or hacking attack on the victim.
If you have a Google account, you can easily find out what data has been leaked: Please review this post, How to Maximize Google Security and Safety webpage.
Look at this...
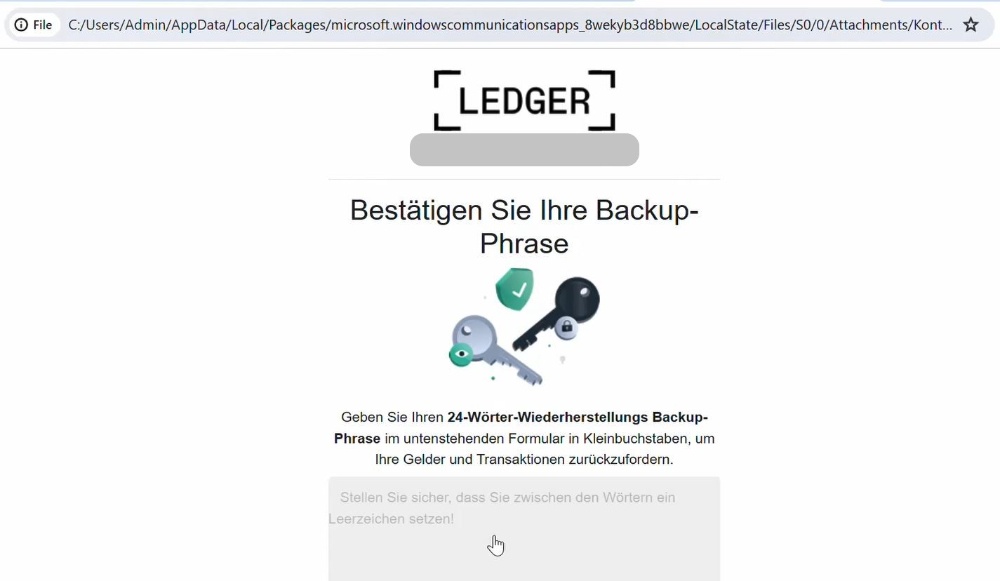
Just a couple of days before releasing this post, the colleague from Crypto Safety First who investigated the Illuvium Phishing email received a Ledger Phishing Email with a link that opens the following URL:
Does the URL look familiar?
We are now creating a new video and post that reviews three Leger Phishing scams and shows in detail the tactics used by scammers to encourage their victims to reveal the seed phrases.
Stay posted; the video and the companion post will be released shortly.
What to do if you suspect you have installed malware on your device
If it comes to the worst, the file contains some virus and malware, and the victim's PC gets infected, the best and most sensible option is to look for professional help.
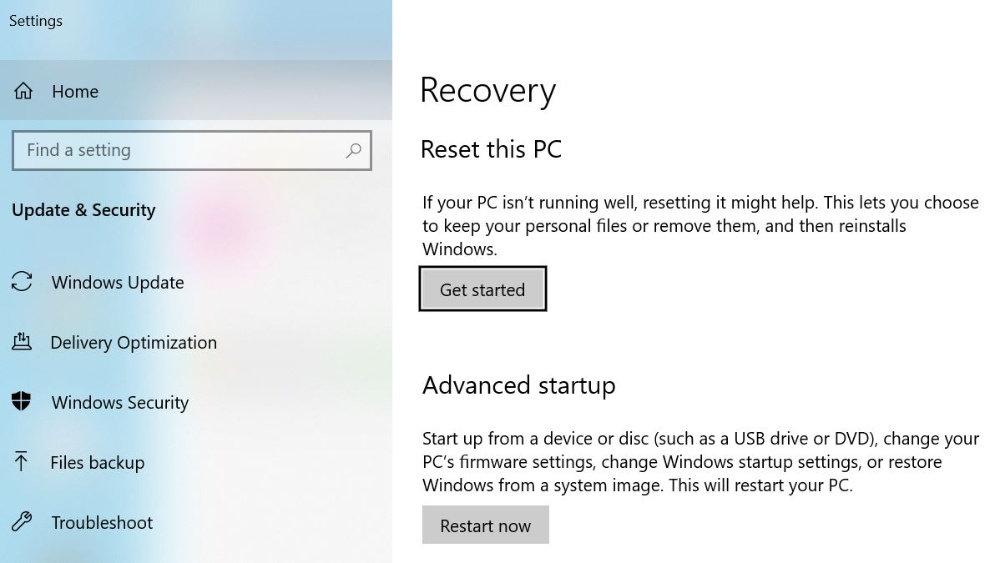
But if this option is not possible, it may be necessary to reset the PC.
We trust that everyone backs up important documents and information, so if this comes to happen, resetting an infected PC does not become a major loss.
If not done yet, you may want to work on system protection for your PC... today.
So, if it comes to the worst, you can restore your PC and eliminate any installed malware or virus.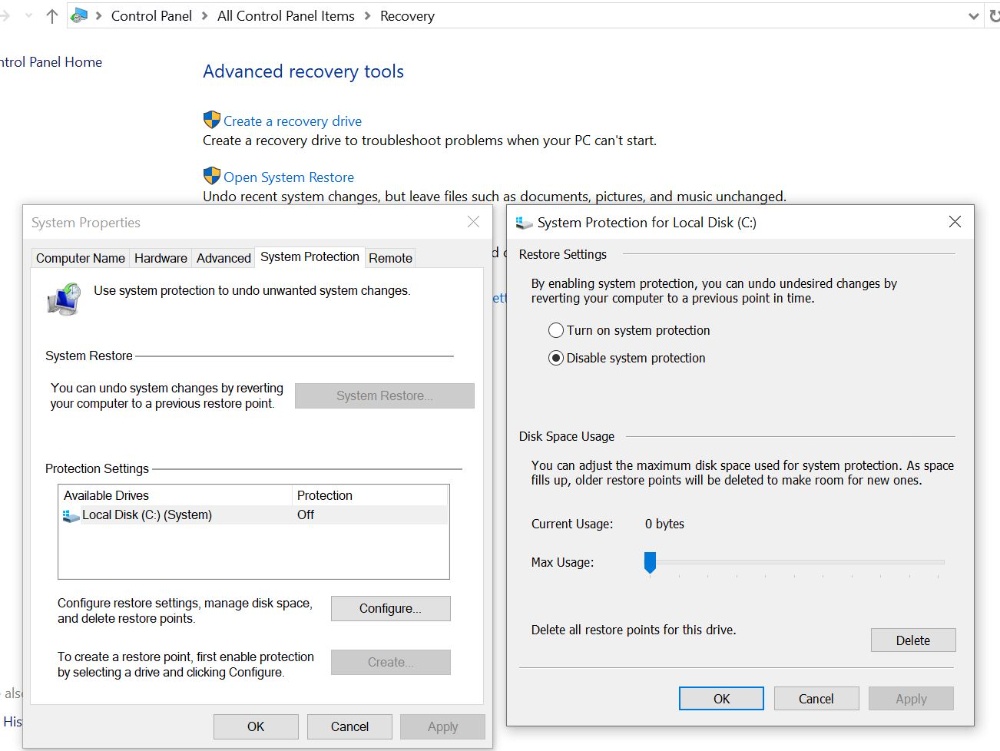
Congratulations on completing this 5-minute digital safety power-up.
We hope this 5 minutes read was worth the time and that you have learned some valuable information.