Ledger vs Trezor — Reviews and Comparisons 2024
This article will compare Ledger vs. Trezor based on multiple criteria and help you decide on the best hardware wallet suited for your need.
What are hardware wallets?
Hardware wallets are physical devices that store cryptocurrencies. They contain private keys in an offline mode and cannot connect to the internet or run complicated apps; hence, they are safe from attacks.
Therefore, they are also known as cold storage (or cold wallets). Hardware wallets are compatible with several interfaces and apps and support multiple cryptocurrencies. They are also compatible with other third-party wallets that act as an interface to manage coins.
Always remember that the more complex the device is, the greater the chance of it getting attacked. These wallets have a minimal and simple design, reducing the overall attack surface.
How do hardware wallets work?
Hardware wallets only sign transactions. Therefore, in order to prepare the transactions and broadcast them to the network, you need to use another device (ex- laptop) that is connected to the internet.
Usually, you need to download a program to interact with the hardware wallet because these wallets allow only specific types of information, such as transaction data.
To start the transaction, we need to enter the pin(password) in the hardware wallet. Always ensure that the transaction we approve on the hardware wallet’s screen is the same as the connected device (Laptop).
You should never forget the seed phrase, which is a 12- 24 words combination given to us to initialize our hardware wallet. Anyone with access to the seed phrase can access your cryptocurrencies, therefore, you must keep them offline in a secure place.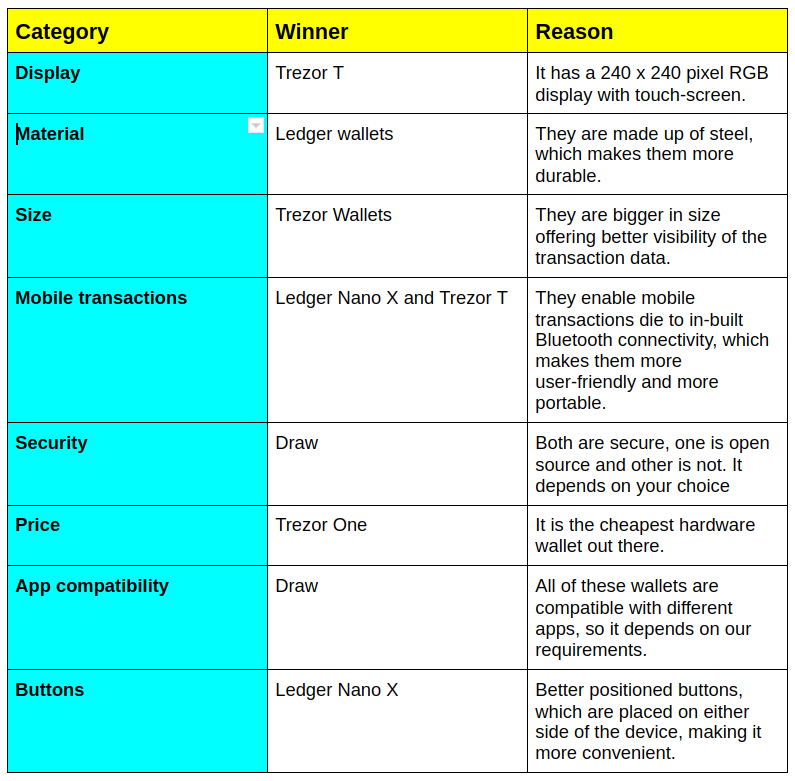 Ledger and Trezor Comparison Table
Ledger and Trezor Comparison Table
Ledger vs. Trezor: Physical Appearance
Display
Both the Trezor and the Ledger wallets have a display screen. They are used to display the seed phrase and send cryptocurrencies. Trezor has a larger display screen compared to Ledger, thus making it more convenient to view. However, Trezor Model T also has a nice color touchscreen.
Material
Trezor wallet is made from plastic, while the Ledger wallet comes with a stainless-steel body. The stainless steel makes the Ledger wallet more durable and portable, giving it a more stylish look.
Buttons
Both devices come with two buttons that are used to manage their software. It is important to note here that Trezor’s buttons are easier to use since they have a good amount of space between them. The buttons in the ledger wallet are very close to each other, increasing the risk of pressing both at once.
Size
Trezor is bigger than the Ledger Nano S. Therefore it may be easier to carry the Ledger wallet with you because of its smaller size.Physical appearance of wallets
Ledger vs. Trezor: Cryptocurrency support
It is crucial to know what coins are supported by both wallets. Currently, both Trezor and Ledger wallets support 1000+ coins. Both wallets support all ERC20 tokens on the Ethereum network.
Ledger vs. Trezor: Open source
Ledger
The Ledger wallets run their own custom operating system BOLOS. This means we cannot see what code goes into the device and the firmware it runs on. However, the specifications are completely open and detailed, and all cryptographic operations are deterministic, allowing them to have the required information.
Trezor
The Trezor wallets use open-source firmware and software. Using an open source has both pros and cons. The bugs can be identified easily, but it comes with an attached security risk.
You can learn more about Trezor on its GitHub.
Ledger vs. Trezor: Supported OS
Trezor and Ledger are compatible both with computers and smartphones. The supported operating systems are Windows 10, macOS 10.11, and higher, Linux, and Android OS.
Ledger supports Windows 8+, macOS 10.10+, Linux excluding ARM Processors. It is also compatible with Android 7+ smartphones.
Ledger vs. Trezor: Difference in password encryption
Both Trezor and Ledger wallets have a password function. Each different passphrase unlocks a unique set of accounts. We can use multiple passphrases.
These settings are helpful to have one main account and two or more hidden accounts from the same wallet, with the same 24 words recovery seed. So regardless of whether we have the recovery seed, we need the password to access the corresponding wallet. If you have to forcefully give your password, you can always give the one with fewer assets.
In Trezor wallets, this password is entered via a connected device such as a Laptop, making it vulnerable for attackers to read.
However, in Ledger wallets, the password is linked to another PIN which is entered using the normal keys.
Trezor wallets have a password manager that works with Chrome and cross-platform on your MacOS, Windows, and Linux. We can install the Trezor Password Manager Chrome extension (TPM) and sign in with Google Drive or Dropbox. We can also connect to our Trezor device by entering our PIN and then enabling Password Manager on our Trezor device.
Ledger vs. Trezor: Compatibility with other apps
Ledger
The Ledger wallet is compatible with apps such as Ledger Live, Electrum, MyEtherWallet, Copay, Mycelium, Electron Cash, GreenBits, MyCrypto, Binance, Magnum, etc.
Trezor
The Trezor Wallet is compatible with apps such as MyTrezor, Copay, MultiBitHD, Magnum, GreenBits, Electrum, Mycelium, MyEtherWallet, etc.
Both of the wallets are compatible with a large number of apps and have a lot of those apps in common. So always choose, depending on what you need.
Ledger vs. Trezor: Hardware
Ledger
The ledger wallet has a very distinctive hardware architecture, consisting of a very secure Operating System BOLOS (Blockchain Open Ledger Operating System), and specialized chips known as Secure Elements.
In order to utilize the Secure Element’s unique security capabilities while being able to manage the different peripheral devices, the Secure Element has been provided with a STM32 microcontroller (MCU) which acts as a router between the peripherals and the Secure Element and notifies it whenever new data is to be received.
The Secure Element is responsible for executing all of the applications of the BOLOS environment.
Trezor
CPU: The processor used by a Trezor is an ARM Cortex-M3 processor @ 120 MHz, while the software is custom.
Screen: The screen is an important tool, which enables the users to verify the authenticity of the data entered. The Trezor One uses an OLED screen (128 x 64 pixels); while the Trezor model T uses an LCD touch-screen (240 x 240 pixels). Both of the screens provide ample of space on the screen so as to display the warnings, requests, images, or transaction details. It is also used to display the recovery seed of our private key.
Buttons: Two buttons are used by Trezor One in order to receive confirmation from the user. Physical confirmation is important in order to protect the accounts from attacks.
Trezor model T also uses a Micro-SD card slot and a USB-C Connector.
Ledger vs. Trezor: Security
When considering the security in entering our passwords, in Trezor wallets, the password is entered via the keyboard of the connected device, making it vulnerable for attackers to read it.
However, in Ledger wallets, the password is linked to another PIN which is entered using the normal keys.
How to check if your Trezor or Ledger wallet is tempered?
There are two ways in which the device could be attacked physically. First, it could be compromised before we receive it. To avoid that, the Trezor uses tamper-evident seals. They are sealed using industrial glue, and putting that back again after making changes to the hardware is quite tricky, so we know that the wallet has been compromised if it has a damaged or broken seal.
Ledger uses a trusted computing base which is validated using cryptographic proofs. Users can verify the integrity of the device by performing an attestation check. They also prevent evil maid attacks.
What to do when Trezor or Ledger wallet is stolen?
These devices are protected by a pin, and after three unsuccessful attempts, it wipes off all the contents, self-destructs, and locks the suspicious user out.
Both Trezor and Ledger are, by design, protected from remote attacks. They do not connect to the internet directly; when connected to an internet-enabled device, they only pass necessary information like transaction details.
While both Ledger and Trezor are highly secure in their own ways, Trezor is considered to be a better option as it is more secure because of its open-source feature.
Ledger vs. Trezor: Pricing
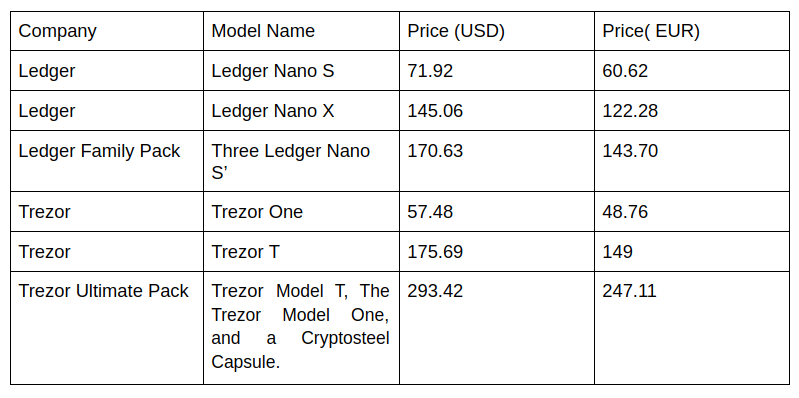
Ledger vs. Trezor: Models
Both Ledger and Trezor come with two models. In this section, we will compare their own models with each other.
Ledger Nano S vs. Ledger Nano X
The Ledger hardware wallet consists of the following models:
Ledger Nano S
The Nano S was the predecessor of Nano X and was developed in 2014. It is made of steel and consists of the ST31H320 Secure Element and the STM32F042K microcontroller chips.
It is a bit lighter and smaller than the Nano X. It consists of a smaller screen with 128 x 32 pixels display and has two buttons on one side of the device.
It does not consist of a battery since it only supports wired transactions and comes with a micro USB Type B.
Ledger Nano S is not exactly devised for mobile transactions but requires computer access to perform transactions. It has a limited amount of storage space and can accommodate up to 10 apps.
Because of its comparably cheaper price, the Nano S still remains a popular choice among cryptocurrency enthusiasts and novice traders.
Ledger Nano X
Ledger Nano X is Nano S’ successor. It is made of steel and consists of the ST33J2M0 Secure Element and the STM32WB55 microcontroller, which are wireless chips and have built-in Bluetooth support.
Nano X is a bit heavier and larger than the Nano S. It has a larger screen than the Nano S with a display size of 128 x 64 pixels and allows for more room for displaying information.
It consists of two buttons that are placed on either side of the device which feels more durable and more convenient to use.
A 100 mAh rechargeable battery supports Ledger Nano X. comes with a USB Type C Connector. It provides us with a lot more storage and can easily accommodate more than 100 apps, each supporting a different crypto currency. Ledger Nano X is a much more popular choice among professionals who need to access their funds anytime and anywhere.
Trezor One vs. Trezor model T
The Trezor hardware wallet consists of the following models:
Trezor One
The Trezor One was the first-ever Trezor hardware wallet developed by SatoshiLabs.
It has two push buttons and a 128 x 64-pixel OLED display rather than a touch-screen. It resembles a keychain and is very compact and lightweight to carry around.
Trezor One is protected by an ABS plastic case, which is impact-resistant and robust and protects against minor physical damages.
It consists of an STM32 F2 microcontroller and the ARM Cortex-M3 processor running at 120 MHz, which provides smooth and secure access to our funds.
The Trezor One as well as the Trezor model T comes without a battery.
Both the Trezor wallets allow various features like Password Manager (which enables us to store, access, and manage login details for various apps) and U2F authentication token (which allows an easy login to various social media sites like Twitter, Github, Google, etc).
It is an ideal choice for a hardware wallet with low-budget conditions.
Trezor Model T
The Trezor T is a second-generation wallet and is the newer, updated, and more secure version of the Trezor One hardware wallet.
It has a newer, faster, and better Operating system and processor. It is protected by an ABS+PCplastic case and consists of a STM32F4 microcontroller and the ARM Cortex-M4 processor running at 168 MHz.
Trezor Model T consists of a 240 x 240 pixel RGB color display with a touch screen and supports a lot more crypto-currencies than Trezor One.
The touch screen provides the user with a more user-friendly experience, better accessibility, and ultimate control of the hardware wallet.
The screen is the only medium to enter the passphrases or PIN, unlock the device, to recover existing wallets, and to confirm other actions, which makes it less prone to cybercrime and more secure during the seed recovery process.
The screen also has a bigger size, making the wallet much more convenient.
The wallet has built-in mobile connectivity, an SD card slot, and a USB Type C Connector, which enables mobile transactions, and is compatible with any mobile device or computer. Rather than using third-party interfaces, the wallet allows us to use its own web-wallet interface for the ERC20 tokens transactions.
Hardware Wallet Advantages
There are multiple advantages of using hardware wallets:
- Hardware wallets are capable of hosting multiple crypto-currencies at the same time in an isolated, offline environment.
- These wallets are more secure and less vulnerable to computer viruses and malware, which ensures a more secure transaction.
- Hardware wallets are protected by an encrypted pin, which we generate. After the three consecutive wrong password entries, the wallet self-destructs and locks out, anybody who tries to forcefully enter by trying different pins. The device would delete the keys in order to keep our funds secure.
- The private key is entered only on our encrypted hardware device, which makes it unexposed to other people and devices and prevents it from getting hacked.
- These wallets do not allow anybody to make any transaction without having access to the device since the hardware wallet itself does the transaction verification. Thus, our data and transactions are safe as long as we are the only ones having access to the hardware wallet.
Hardware Wallet Disadvantages
The disadvantages of hardware wallets are as follows:
- They are not free.
- The wallet could get lost or broken.
- The private key extraction becomes quite difficult.
- Since they are highly secure, they don’t allow us to perform a transaction in just a few clicks, and it is sometimes difficult to set up the wallet.
- Many people and online shopping platforms are involved in manufacturing and selling fake hardware wallets, which could end up emptying our funds.
Ledger vs. Trezor: How to Setup?
Ledger
- You must wait for the device to generate private keys to access your crypto assets.
- You will also have to write down your unique recovery phrase (24 words), which is a backup of your private keys.
- To begin the set-up process, you must connect the device to the computer and wait for the Welcome message.
- After navigating through the instructions, press both buttons simultaneously to start setting up a new device.
- After that, follow the steps to choose a PIN code. After selecting the checkmark, press both buttons to confirm their choice.
- The device will now display the 24-word recovery phrase, which you should write/note down.
Trezor
- You have first to visit trezor.io/start. You will be redirected to wallet.TREZOR.io, where you can install either the TREZOR Bridge or the TREZOR Chrome Extension.
- As no firmware is installed in a new device, you must install it with the latest.
- Follow the instructions to generate the PIN. Trezor uses a grid-based PIN generation system.
- After the PIN has been generated, you should note down the unique combination of 24 words generated.
Ledger vs. Trezor : Staking
Ledger
Ledger wallets allow staking up to seven coins simultaneously in their platform or an external wallet. The cryptocurrencies available for staking include Ethereum, Tezos, Tron, Cosmos, Algorand, and Polkadot.
Trezor
Trezor hardware wallets do not allow cryptocurrency staking. You can link the Trezo Model T or Trezor One wallet to a third-party validator or staking pool. Further, you can also use the Exodus wallet as a staking interface.
Ledger vs. Trezor: Pros and Cons
Ledger
 Ledger Pros and Cons
Ledger Pros and Cons
Trezor
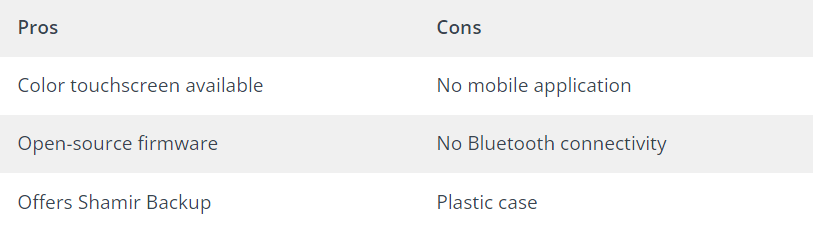 Trezor Pros and Cons
Trezor Pros and Cons
Frequently Asked Questions
How does the ledger wallet work?
Ledger wallets are basically USB storage devices that hold multiple currencies offline. It is capable of storing the user’s private keys on the device and thus, making it difficult for third parties to access the user’s account. Moreover, if the physical device gets stolen, the user can rely on a 24-word password backup recovery to access his/her stored cryptocurrency.
How to set up a Trezor wallet?
- Connect the trezor wallet to your computer.
- Go to trezor.io/start
- Install trezor wallet.
- Install firmware.
- Reconnect Trezor.
- Give the trezor device a name.
- Set up the PIN.
- Note down the recovery seeds
How to exchange cryptocurrency with your Trezor wallet?
- Connect your trezor wallet and sign in.
- Select the relevant type of cryptocurrency from the top left corner of the trezor wallet.
- Select an account from which you want to trade.
- From the main navigation menu, click on “Exchange”.
- Select the type of cryptocurrency you want to buy.
- Click on the “Continue to Exchange”
- Fill in the amount that you wish to sell.
- Finally, select the best trade.
What if I lose my ledger wallet?
You can always just get a new Ledger device, put in your recovery phrase, and you’re back in business. Also, it is recommended to have a backup Ledger device set up with the same recovery phrase for easy access to your funds in case something gets lost or goes wrong.
What is the purpose of a ledger wallet?
Ledger hardware wallets are multicurrency wallets that are used to store private keys for cryptocurrencies offline.
You can read on Ledger Nano S vs X to better compare the two wallets.
Is Trezor a good wallet?
Yes, Trezor is a reliable and trustworthy wallet in the cryptocurrency world. It is a well-known hardware wallet that serves high security and is being used by more than 1 million crypto users globally.
What coins can I store on Trezor?
Trezor hardware wallet supports several major cryptocurrencies. Some of these include ERC 20 tokens, Bitcoin, XRP, Stellar, Tether, Tron, and many more.
Which is the best Ethereum wallet?
Ethereum is among the most valuable cryptocurrency in the world. Some of the best Ethereum wallets include Trezor One, Metamask, and Ledger Nano.
Why are hardware wallets safe?
A hardware wallet stores the user’s private keys very securely by making use of a USB drive device. This keeps the wallets unaffected by viruses that could be on the user’s computer.
Disclaimer — This article contains product affiliate links. We may receive a commission if you make a purchase after clicking on one of these links.























![[ℕ𝕖𝕧𝕖𝕣] 𝕊𝕖𝕝𝕝 𝕐𝕠𝕦𝕣 𝔹𝕚𝕥𝕔𝕠𝕚𝕟 - OM(G) , My Biggest Bag Was A Scam????](https://cdn.bulbapp.io/frontend/images/99de9393-38a8-4e51-a7ab-a2b2c28785bd/1)

























