API Keys vs Tokens Unraveling the Authentication Puzzle for Enhanced Security
In the ever-evolving landscape of web development and security, the choice between API keys and tokens plays a pivotal role in shaping a robust authentication strategy. This article aims to demystify the complexities surrounding these authentication mechanisms, shedding light on their unique characteristics and best use cases.
Navigating the Naming Conundrum: Unraveling the Distinct Worlds of API Keys and Tokens
In the intricate realm of computer science, they say that the two most challenging problems are cache invalidation and naming things. And, to be honest, they're not wrong. Naming things, in particular, is a formidable task that demands a delicate balance between clarity and conciseness. The essence lies in leaving no room for doubt about the meaning of variables, terms, functions, or classes. If there's ambiguity, it's safe to say that the naming might need a second thought. Recently, I found myself in a discussion where the terms "API keys" and "tokens" were tossed around interchangeably. After about two minutes, it became evident that clarity was missing from the conversation. I had to intervene and pose a crucial question, "Do you realize these are different, right?" To my surprise, they did not. This scenario isn't uncommon. Many individuals struggle to articulate the disparity between API keys and tokens. So, let's untangle the confusion and set the record straight.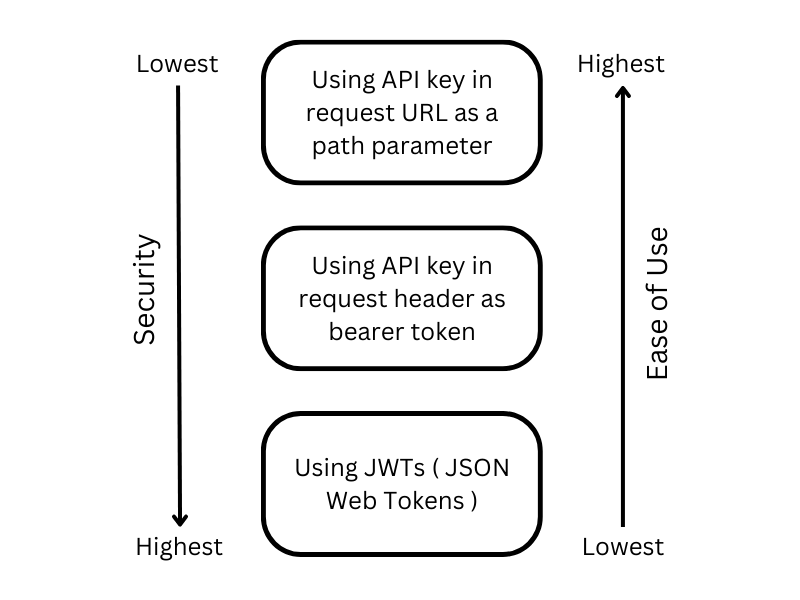
Definition
1. API Keys: The Identifiers
API keys are like digital fingerprints, serving as unique identifiers. They are alphanumeric strings that authenticate and track the usage of a service or application. Think of them as keys to a secure vault, allowing access while also keeping a meticulous record of who's coming and going. However, with great power comes responsibility – mishandling API keys can pose security risks. 2. Tokens: The Versatile Guardians
2. Tokens: The Versatile Guardians
On the other side of the spectrum, tokens are versatile guardians of authentication. In the realm of OAuth and similar authorization protocols, tokens take center stage. These encoded entities carry information about users and their permissions, offering a more sophisticated approach to access control. Unlike API keys, tokens can have a limited lifespan, reducing the risk associated with long-term exposure.
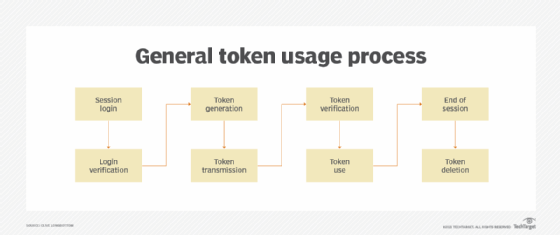 Clearing the Air: Why the Distinction Matters
Clearing the Air: Why the Distinction Matters
Understanding the disparity between API keys and tokens is not just a matter of semantics; it's about fortifying the foundations of secure communication. When these terms are used interchangeably, the potential for confusion and security lapses escalates.
As developers, security enthusiasts, or anyone venturing into the digital landscape, it's imperative to grasp the nuances of API keys and tokens. Precise naming isn't just a coding convention; it's a language that speaks volumes about the robustness of our systems.
So, the next time you find yourself in a conversation about API keys and tokens, remember – clarity in naming is the cornerstone of effective communication and secure practices in the digital realm. Let's embrace precision to navigate the complexities of authentication with confidence and understanding.
API Keys vs Tokens: Understanding Authentication in the Digital Realm
In the ever-evolving landscape of web development and security, the choice between API keys and tokens plays a pivotal role in shaping a robust authentication strategy. This article aims to demystify the complexities surrounding these authentication mechanisms, shedding light on their unique characteristics and best use cases.
1. The Basics: API Keys and Tokens Defined
Explore the fundamental concepts behind API keys and tokens. Understand how API keys act as identifiers and how tokens, with their encoded information, offer a more sophisticated approach to authentication.
2. Security Implications: Balancing Convenience and Risk
Delve into the security aspects of API keys and tokens. Discuss potential vulnerabilities associated with each method and highlight best practices to mitigate risks. Emphasize the importance of adopting security measures without compromising user experience.
3. Practical Implementation: Code Snippets and Examples
Provide practical insights into implementing API keys and tokens in real-world scenarios. Include code snippets to illustrate the step-by-step process, catering to both novice and experienced developers.
4. Lifecycle Management: Key Considerations
Address the lifecycle of API keys and tokens, emphasizing the importance of proper management. Discuss expiration, renewal, and revocation processes to ensure a secure and seamless authentication experience.
5. Choosing the Right Approach for Your Application
Guide readers in making informed decisions when selecting between API keys and tokens. Discuss scenarios where one method might be more suitable than the other, considering factors like scalability, user roles, and application architecture.
6. Looking Ahead: Emerging Trends in Authentication
Briefly touch upon emerging trends and advancements in authentication methods. Encourage readers to stay informed about the evolving landscape and adapt their strategies accordingly.
 Briefly;
Briefly;
API keys and tokens are two essential concepts used to facilitate secure and authorized information sharing. Here are the key points explaining the importance of API keys and tokens:
Authentication and Authorization:
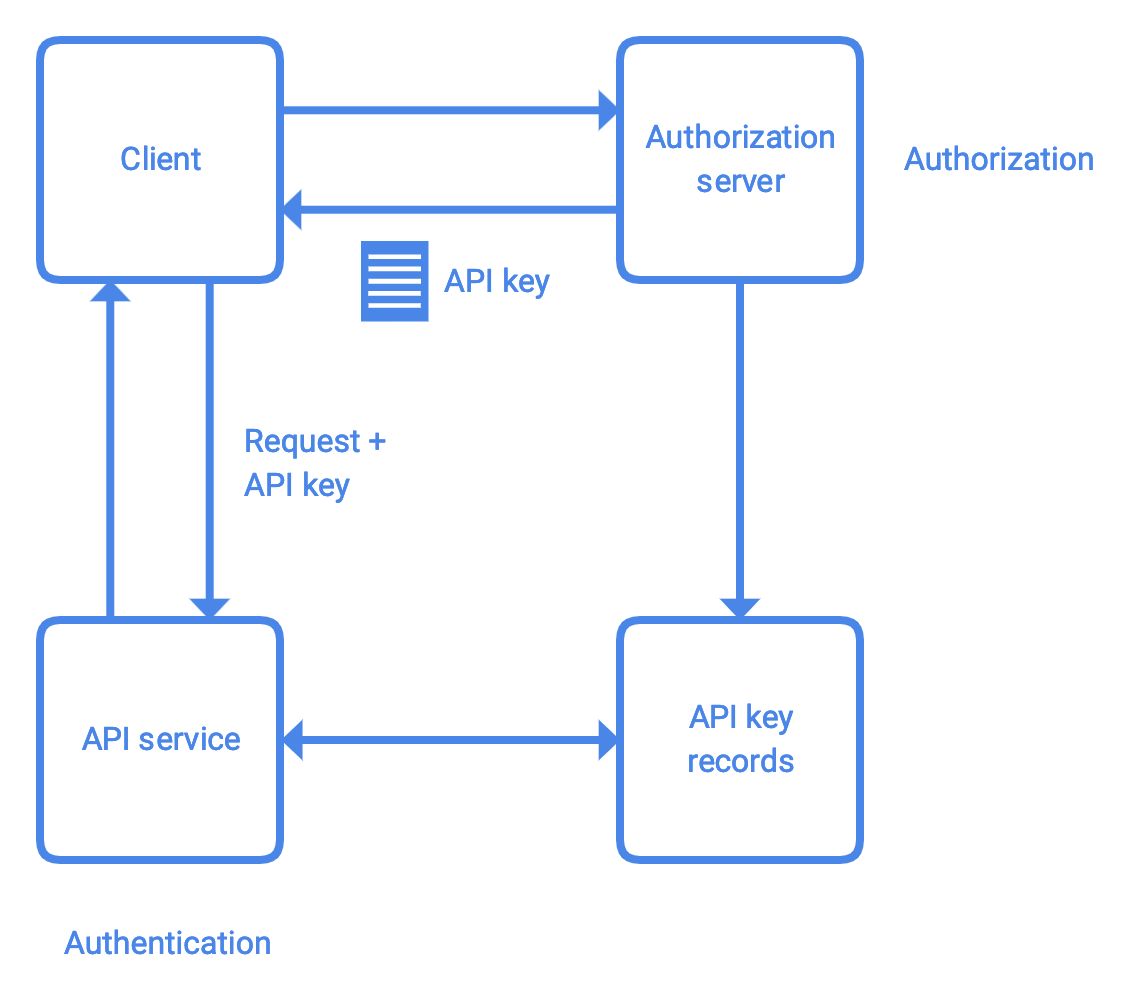
- API Key: An API key is used to authenticate an application or user. It is typically an alphanumeric string that allows the API to recognize and authorize requests from the correct source.
- Token: Tokens are often used in a broader context of authorization, especially in authentication protocols like OAuth. Tokens can contain information such as a user's identity and permissions, enabling more complex authorization scenarios.
 Security:
Security:
- API Key: API keys are often simple alphanumeric strings, making them more sensitive from a security perspective. Improper storage or sharing of keys can pose serious security risks.
- Token: Tokens usually have a more complex and encrypted structure. Additionally, security measures like token expiration and renewal can be implemented for enhanced security.

Monitoring and Analysis:
- API Key: API keys can be used to track how often an application utilizes the API and where the requests originate. This is crucial for usage statistics and monitoring.
- Token: Tokens can be utilized to monitor a user's login status and access permissions, aiding in security audits and tracking user activities.

Integration into the API Ecosystem:
- API Key: API keys provide a quick and straightforward way to access an API, often primarily for authentication purposes.
- Token: Tokens are designed to be used in a broader ecosystem, offering authorization across various services.
![]() API keys and tokens enable the secure, structured, and traceable use of APIs, allowing users, applications, and service providers to manage resources effectively while prioritizing security.
API keys and tokens enable the secure, structured, and traceable use of APIs, allowing users, applications, and service providers to manage resources effectively while prioritizing security.
SCORE


























































