How To Identify Phishing Websites - 3 Free Tools
In this article, we’ll explore two free but extremely useful and complete online tools for investigating any website for signs of phishing.
Additionally, we’ll introduce two online security browser extensions.
These extensions are valuable tools that even the most experienced web users should consider adopting.
They safeguard against that critical 0.1% that sometimes slips under the radar, identifying potential threats before any harm can occur.
First Tool: The Wayback Machine
The first free tool in the Wayback Machine.
The link to the Wayback Machine is ‘https://archive.org/web/’
Very important: While the Wayback Machine is not a common target for hackers and scammers, we encourage you ALWAYS to verify any link. After all, how do you know a malicious person has not hacked our BULB account and inserted a malicious link to this article?
The Wayback Machine is a tool operated by the Internet Archive that allows users to view archived versions of web pages over time, providing access to historical snapshots of websites.
It serves as a valuable resource for investigating the evolution of web content and can be used to verify the legitimacy of a website by examining its historical state.
To demonstrate the use of the Wayback Machine, we’ll employ Google to search for the authentic Metamask site.
Given that Metamask is a frequent target for malicious activities, including phishing attempts, extra care is essential.
Over the years, numerous cases of deceptive Metamask results in search listings have led to crypto asset theft from unsuspecting individuals.
To ensure the authenticity of the first Metamask search result, we’ll right-click, select ‘Copy Link Address,’ and delve into further investigation.
Then, using the Wayback Machine website, we can paste the link we just copied from the search result and press ‘Browse History’.
The Wayback Machine will display useful historical information about the website we want to investigate.
For example, we can observe that the Wayback Machine took the first metamask.io snapshot in 2016.
This may indicate that metamask.io is legitimate because a quick search informs us that Metamask was released in 2016.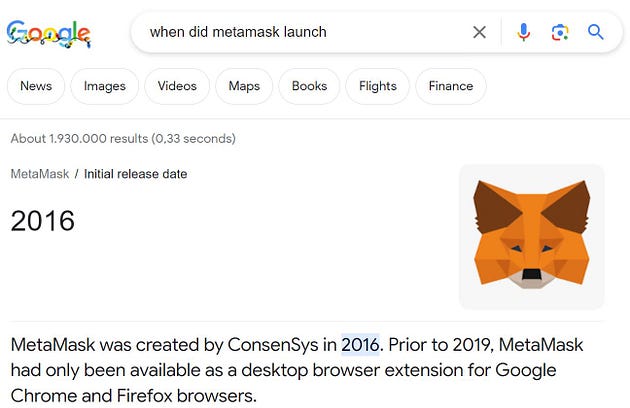
But we will investigate further because the Wayback Machine has stored many snapshots of metamask.io over many years.
And those snapshots can be used to verify that metamask.io has remained consistent over the years: An inconsistent website can indicate that a website has been for sale and maybe used (or is still being used) for nefarious activities.
Next, we choose a year, 2018, and click over a date to access the snapshot.
The Wayback Machine will display that snapshot's content, which, for our date selection, shows how metamask.io looked on July 2, 2018.
At this point, we must use your knowledge and experience to assess the content of the snapshot and decide if the content matches what we expect from the legitimate metamask.io or if it belongs to a phishing website.
Let’s look at a practical example of a phishing website and use the Wayback Machine to investigate the domain to provide some contrast or a reference.
If you own crypto assets, it is likely that, at some point or another, your data has been leaked to the dark web through a data breach, and you are receiving emails like the one displayed below.
The scammers are using some basic dark psychology, an amygdala hijack, to encourage us, the victims, to take quick action.
While ‘Metamask’ is mentioned at the top of the email, the sender's email address, ‘@iinet.net.au,’ has no relation to Metamask. And that should already be a clear indication of a phishing email.
But, for education purposes, we have used one of our disposable laptops to click over the phishing link ‘Recover my wallet’ and check where it leads.
Note that you should neither open suspicious emails nor click over suspicious links because the following scenarios will most likely happen:
- One: The phishing email will probably contain invisible tracking pixels informing the malicious person who sent it that your email address is active and that you are a suitable candidate for further phishing emails. This is because if you have exposed yourself, the information will be sold on the dark web and bombarded with many more phishing emails.
- Two: While most phishing links are ‘relatively’ harmless, some will expose you to advanced hacks that hijack your session without notice. For example, some malicious links can bypass Two-Factor Authentication and take over your accounts.
The malicious ‘Recover my Wallet’ link does lead us to a malicious website that encourages us to enter our Metamask wallet seed phrase.
The malicious website domain ‘ammunitionstore.com’ has nothing to do with Metamask. And that is another clear red flag indicating this is a phishing website.
But a phishing website is not always so obvious, so in case of doubt, we can use the Wayback machine to investigate it.
The results show that the first ‘ammunitiongunstore.com’ snapshot was taken in March 2023.
That already indicates that this is a website of recent creation and does not match the information we have already researched about when the Metamask project was started.
Also, ‘ammunitiongunstore.com’ has just a few snapshots. Which is another potential indicator of a phishing website.
Clicking over one of those snapshots shows a very poor and basic website.
While not all phishing websites are as obvious as ‘ammunitiongunstore.com, ' with some knowledge and awareness, anyone should be able to identify 99% of phishing websites using the Wayback machine as a tool.
Second Tool: Who.is
The second free tool is Who.is
The link to the who.is website is ’https://who.is/’
Very important: While Who. is not a common target for hackers and scammers, we encourage you ALWAYS to verify any link. After all, how do you know a malicious person has not hacked our BULB account and inserted a malicious link to this article?
Whois is a database of information related to domain registration.
While Whois may not directly detect phishing websites, it can provide us with valuable information about the domain’s registration details.
Analyzing this information can help us assess the legitimacy of a website.
Here’s how to use Whois to gather information and potentially identify phishing websites.
Once on the legitimate ‘who.is’ website, we can search for the website we want to investigate.
For this example, we again check the link we copied from our Google search.
We copy it to the ‘who.is’ search bar, and we will review that the results match what we expect from the legitimate Metamask domain.
The results show that the metamask.io domain was registered in July 2015, was updated in October 2023, and expires in July 2024.
Additionally, at ‘who.is’, we can access other information like the name of the organization that has registered the domain and the contact information.
The data does match what we could expect from the legitimate Metamask website, and there are no inconsistencies.
Instead, we find barely any information if we investigate ’ammunitiongunstore.com’. This further reassures us that this is just a fake Metamask phishing website.
Third Tool: Online Security Extensions
Using the Wayback Machine or Whois should allow you to identify most if not all, phishing websites.
But we are all humans and prone to human errors. We may have a bad day, be in a hurry, or be distracted, and we may click on a malicious link that leads us to a phishing website.
It may happen to anyone.
Luckily, there are free tools that we can use to compensate for lapses and keep us safe.
Like the web3 antivirus or the wallet guard extensions.
As browser extensions, both Web3 Antivirus and Wallet Guard require downloading and installation.
Therefore, you should exercise extreme caution to install only the authentic extensions.
This article refrains from providing a direct link to Web3 Antivirus due to safety concerns.
Instead, follow a secure process by searching the legitimate Web3 Antivirus and Wallet Guard websites: Utilize tools like the Wayback Machine and Who.is to identify potential phishing sites.
Even the link shown in the image below should be treated with skepticism.
Rather than relying on the link, consider it a reference and conduct thorough research to access the genuine Web3 Antivirus website.
The Web3 Antivirus has many features that would be of special interest to crypto users. But we will not cover them in this article.
However, any online user could benefit from having the Web3 Antivirus browser extension installed because it warns us if a website we are about to access has been identified as phishing.
The Wallet Guard extension also has many useful features for those who own crypto assets and need to interact with DeFi apps or other online cryptocurrency applications.
But, like the Web3 Antivirus, Wallet Guard is a very useful extension to install on your default browser because it warns you if you are about to visit a phishing or recently created website.
While not all recently created websites are phishing, there is a high probability that recently created websites asking you to take urgent actions are malicious. Like the one in the example below.
Now, let’s put both extensions to use.
While doing some research for this article, we were searching for Web3 Antivirus extension information, and we came across the following search results.
Two results will lead you to the legitimate Web3 Antivirus website or browser extension, while one result is from a phishing website.
Before proceeding, can you identify which search result leads to a phishing website?
…
In case of doubt, please research using the Wayback Machine or Who.is tools.
…
The Wallet Guard extension displays the following warning when clicking over the third result.
Similarly, when clicking over the third result, the following warning is displayed by the Web3 Antivirus extension.
We hope this example conveys the importance of researching search results before clicking them.
And, it is worth remarking once again every so often; we all may feel overconfident, or have a bad day, and click over a search result without taking precautions.
In that situation, the online security tools work as a safe net, warning us about the danger.
But it is also worth remembering that we should not blindly trust online security extensions because they may not identify all the threats.
Please consider always doing your research.
We have already reported the malicious website so the competent authorities can evaluate and remove it if deemed unsafe.
If you come across a malicious website, please do the same. For the safety of our fellow web users.
The Most Reliable Tool is Your Knowledge and Experience
We hope this article has been informative and you have learned how to identify and avoid phishing websites.
Because, after all, your knowledge and experience are the best tools to steer away from malicious websites, emails, links, and such threats.
Please consider subscribing to our blog for shorter but more important articles about crypto and digital good practices.
Or, visit us at www.cryptosafetyfirst.com





























































































