Crypto Security: Your Ultimate Guide to Safeguarding Your Digital Assets
In the digital age, safeguarding your assets has become a paramount concern, especially when it comes to cryptocurrencies. Crypto security encompasses the measures and technologies employed to protect your digital assets. In this guide, you'll discover effective strategies to keep your crypto assets secure, enhancing your security measures in an SEO-friendly manner and maximizing the safety of your digital holdings.
When deciding to enter the crypto sector, ensuring the security of your assets becomes one of the most crucial aspects. I will guide you through the best ways to protect your crypto assets. Safeguarding your cryptocurrency is paramount, and I will walk you through effective strategies. Ensuring the security of your assets is vital as you step into the world of crypto.
Seed Phrase
While some individuals may call it a recovery or backup phrase, at Blockchain.com, we specifically term it as your Secret Private Key Recovery Phrase.
What exactly is a Secret Private Key Recovery Phrase?
It's a sequence of 12 or 24 words that grants full access to your Private Key Wallets.
What is its purpose
In the event that you forget your password or face the loss or damage of your device, you can regain access to your account by utilizing your Secret Private Key Recovery Phrase.
Why is the recovery phrase crucial
The significance lies in the fact that anyone possessing your recovery phrase gains unrestricted access to the funds in your Private Key Wallets. They can seamlessly restore access to those wallets through ANY Blockchain.com Wallet account
How to handle your seed phrase
Ensure that your Secret Private Key Recovery Phrase remains... well, a secret.
Some individuals choose to jot down this phrase and secure it in a safe deposit box. Others opt to engrave it onto wood or metal, while some prefer storing it in a dedicated password management tool.
Regardless of your chosen storage method, it's crucial never to disclose your recovery phrase to anyone, including us.If someone requests your code, refrain from sharing it. If there's insistence on screen sharing or sharing access to your recovery phrase, exercise extreme caution and be suspicious.
Private Keys serve as the means to maintain complete control over your crypto assets, yet their security is contingent on your best security practices.If you haven't already secured your funds by backing them up with your Secret Private Key Recovery Phrase, consider taking that crucial step now. Simply launch the Blockchain.com app, tap the Person Icon located in the upper left corner, scroll down to Security, and select Backup Phrase. Follow the steps outlined in the app to ensure the security of your assets.
Enhancing Security: Your Guide to Effective Two-Factor Authentication (2FA)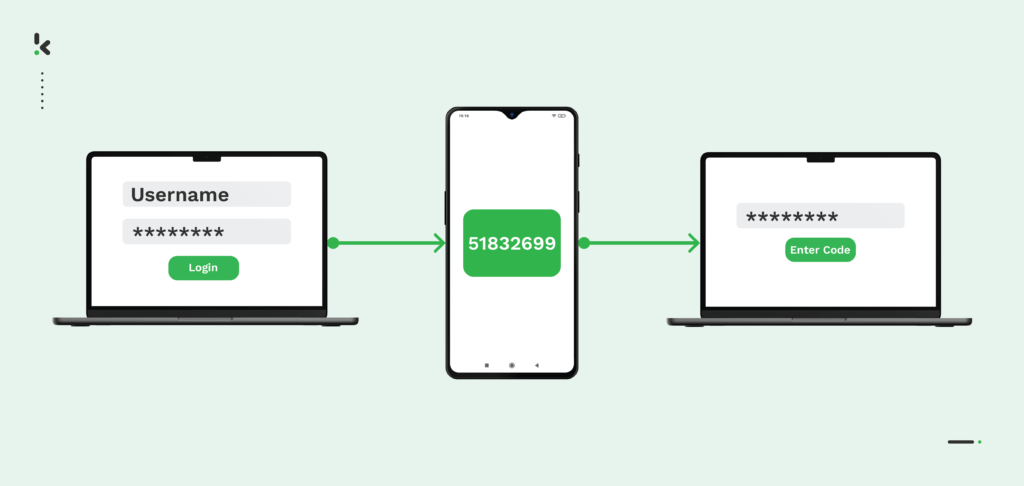
Two Minutes to Security: Activate Two-Factor Authentication (2FA) swiftly to fortify your account. Extend this protective layer to all your applications and digital accounts for enhanced security.
What is 2FA?
Two-Factor Authentication (2FA) serves as an additional layer of security, ensuring that only you can access your account. Even if a hacker obtains your password, gaining entry into the account becomes futile without the one-time passcode.The 'two-factor' concept blends something you know (a knowledge factor) with something you have (a possession factor). This could involve a password paired with an authenticator app or a PIN combined with a hardware security key. Implementing multiple security layers fortifies your account, and the process is seamlessly straightforward.
How to Activate 2FA on Blockchain.com
On Desktop:
- Click on the person icon located in the top right corner.
- Navigate to Security and then click on Enable under Two-Factor Authentication.
- Select your preferred 2FA method and proceed with the setup.
On the App:
- Tap the Person Icon positioned in the top left corner.
- Scroll down to Security and locate 2FA.
- Utilize the toggle switch to enable 2FA.
Strengthen your account security with these simple steps on both desktop and the app
Navigating the Crypto World: Unveiling Common Scams in the Coin Arena
In the dynamic realm of cryptocurrency, opportunities abound, but so do risks. As you venture into the world of coins, it's crucial to be vigilant against common scams that could compromise your investments and security.
1. Phishing Attacks:
One prevalent scam involves phishing attempts where malicious actors pose as legitimate entities, luring users into revealing their private keys or sensitive information. Always verify the authenticity of websites and double-check URLs before entering any personal data.
2. Pump and Dump Schemes:
In the volatile crypto market, pump and dump schemes are all too common. Fraudsters artificially inflate the value of a coin through misleading information, only to sell off their holdings at the peak, leaving unsuspecting investors with significant losses. Research thoroughly and be wary of sudden market hype.
3. Fake ICOs:
Initial Coin Offerings (ICOs) present opportunities for legitimate investment, but fake ICOs are also prevalent. Always scrutinize the project, team, and roadmap before contributing funds. A lack of transparency is a red flag.
4. Ponzi Schemes:
Some schemes promise high returns with little risk, employing funds from new investors to pay existing ones. Recognize the signs of Ponzi schemes, such as unsustainable returns and a lack of clear investment strategies.
5. Impersonation Scams:
Fraudsters often impersonate well-known figures in the crypto space on social media, enticing users to send them funds. Be cautious of unsolicited messages and always verify the identity of individuals or projects making investment claims.
Protecting Yourself:
To safeguard your investments and navigate the crypto space securely:
- Stay Informed: Keep yourself updated on the latest scams and market trends.
- Use Secure Wallets: Opt for reputable wallets with robust security features.
- Enable 2FA: Implement Two-Factor Authentication for an additional layer of account protection.
- Verify Sources: Verify information from multiple reliable sources before making decisions.
By staying vigilant and informed, you can actively protect yourself against common scams prevalent in the coin market. Remember, in the crypto world, knowledge is your strongest defense.
If you're unfamiliar, OpSec is short for 'operational security,' and in the realm of self-custody for crypto assets, it becomes paramount. Taking charge of your assets in self-custody means assuming full responsibility for their safety. However, in the unfortunate event of a security breach, the onus falls squarely on you. Distinguishing effective security measures from mere 'security theater' can be challenging, particularly in the intricate landscape of crypto assets, as pointed out by Bruce Schneier. Security, he notes, is both a feeling and a reality, but aligning the two isn't always straightforward. Feeling secure doesn't guarantee actual safety, and vice versa. The key is to bridge this gap. Celsius investors felt secure, yet faced risks.
Terra investors perceived safety, but faced challenges. FTX investors, despite feeling secure, encountered unexpected issues. Both Celsius and Terra exhibited warning signs, evident in the terms and conditions or the sustainability of Terra UST, visible to those who took the time to investigate. FTX presented a more complex scenario, potentially involving fraud and racketeering, emphasizing the difficulty in protecting against organized, institutional fraud.
In the crypto world, where the stakes are high, understanding the nuances between perceived and actual security becomes crucial. Being informed and discerning is the first line of defense against potential risks in the self-custody landscape.
Understanding Your Risk
On the flip side, centralized exchanges also have a much larger attack surface than you do as an individual. A hacker can easily target an exchange.
However, as an individual, you're a needle in a haystack. It would be almost impossible for hackers to find you. The risk is not a bad actor finding you; it's you finding them.
Malicious Websites
When you opt to self-custody your crypto assets, the primary risk you face is the person staring back at you in the mirror. Fake wallets, spoofed or copy-cat websites, fraudulent airdrops, Telegram and Discord scammers, email phishing, SMS phishing – you name it.
All of them capitalize on greed, incompetence, or both. And they all require users to place their trust in the wrong place.
Here are a couple of ways to protect yourself from malicious websites:
- Exercise Caution with Links:
- Avoid clicking on links unless they come from a reliable source. Be diligent in confirming the legitimacy of your 'reliable source.' Even a seemingly innocent Google search can lead you to a malicious site.
- Mindful App Installations:
- Refrain from installing apps or wallets that you don't fully comprehend. If you decide to install something, ensure it's from a legitimate and trusted source, such as Google Play or the App Store.
The two most common avenues for falling victim to malicious links involve entering your seed phrase or security key or enabling permissions that empower the site to access and withdraw funds. There is never a legitimate reason to input your seed phrase, password, or security key on a website. If a platform requests such information, consider it a HUGE red flag. Crafty site operators can create pop-ups that mimic the appearance of your wallet – don't be deceived. NEVER disclose your seed phrase, password, or security key. Handling permissions can be more challenging. Legitimate decentralized applications (dApps) like Uniswap may require your permission to access funds for trading. Illegitimate sites, however, can exploit the same permissions to completely deplete your wallet. Remain vigilant and cautious to safeguard your assets.
Every time you grant permissions to access your wallet or funds, you are exposing yourself to potential risks.
If you click on a link and receive a prompt to grant access to your wallet, the best practice is to decline. You can always manually grant access later if necessary.
Even when dealing with legitimate websites or decentralized applications (dApps), it is advisable to revoke permissions after disconnecting, as a standard security measure.
However, in the case of illegitimate sites, revoking permissions becomes extremely crucial and should be done promptly!
Merely disconnecting is not sufficient. The spend permission remains active, even if you're no longer connected to the website.
While there may be a small gas fee associated with revoking permissions, it's a minimal cost compared to the potential loss of your entire wallet.
In summary: refrain from clicking on links, never disclose your seed phrases, and make it a habit to revoke permissions after each session to ensure the utmost security of your assets.
Mobile Security
SIM swaps, also known as port-out scams, pose a significant threat. If your personal information is leaked, particularly in the aftermath of an exchange hack, your cryptocurrency holdings could be in jeopardy.
In the mentioned exchange hack, cybercriminals successfully accessed personally identifiable information, including cell phone numbers and details of customers with substantial balances, highlighting the critical importance of mobile security.
With Great Power Comes Great Responsibility
As an increasing number of crypto investors become aware of the risks associated with trusting third-party vendors, such as centralized exchanges, there's a significant push towards self-custody.
Following the FTX incident, sales of Ledger devices (removable hardware wallets) witnessed a substantial uptick. Generally, I view this as a positive development.
Decentralized money empowers us to bypass the need for intermediaries and regulators. However, this power also comes with the responsibility of safeguarding our own assets.
Given the highly technical nature of the crypto field, I believe that most users lack the knowledge and sophistication to self-custody safely. It doesn't make sense to trade one risk of loss for another simply out of fear.
What does make sense is taking control of what you understand and how you operate. Assuming responsibility for the safekeeping of your crypto assets can be uncomfortable and even intimidating. Yet, if you're navigating a high-risk, highly volatile, and largely unregulated space, it's the least you should be doing.
In the realm of crypto, sensibility is crucial. While it's enticing to dream of 'wen lambo,' the reality is that we are on the frontier of a global tech boom.Being on the frontier of anything carries inherent dangers. Yes, there are potentially incredible rewards for those who endure, but survival must come first. Learning how to safely self-custody your crypto assets is a vital initial step toward being a survivor.
Consider these tips as a guide, but remember, these are solely my opinions. I'm not a financial advisor, this isn't financial advice, and always DYOR (Do Your Own Research). Implementing any of these ideas carries the risk of losing all your money. I am dead serious about that. While I enjoy tinkering with this stuff, I've been on record acting like a total baboon. Invest accordingly.
Until next time, stay safe, stay smart, and always tie the camel.









![[ℕ𝕖𝕧𝕖𝕣] 𝕊𝕖𝕝𝕝 𝕐𝕠𝕦𝕣 𝔹𝕚𝕥𝕔𝕠𝕚𝕟 - Is Trump Dying? Or Only Killing The Market?](https://cdn.bulbapp.io/frontend/images/a129e75e-4fa1-46cc-80b6-04e638877e46/1)






![[FAILED] Engage2Earn: McEwen boost for Rob Mitchell](https://cdn.bulbapp.io/frontend/images/c798d46f-d3b8-4a66-bf48-7e1ef50b4338/1)
